实验条件
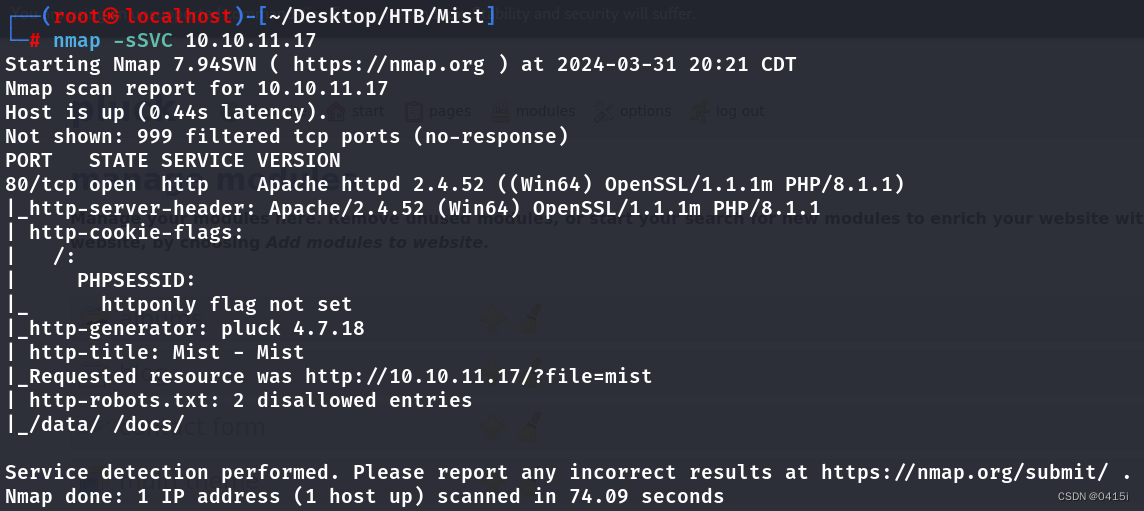
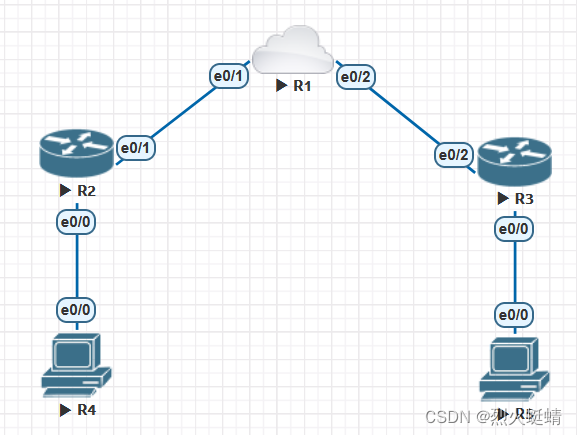
网络拓朴
实验目的
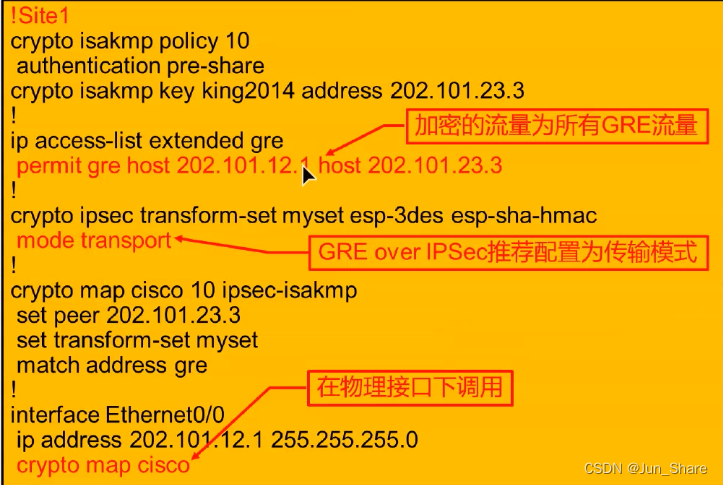
为R2和R3建立IPSec VPN
R4可以ping通R5
开始配置
R2:模拟需要远程访问网络的网关
R4:模拟需要远程访问网络内的目标主机
R3:本地网络上网的网关
R5:移动办公用户,需要去访问远程网络的个人设备
1. R2 Ping R3确定基础网络是通的
R2#show ip int br
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 192.168.1.254 YES TFTP up up
Ethernet0/1 12.1.1.2 YES TFTP up up
Ethernet0/2 unassigned YES TFTP administratively down down
Ethernet0/3 unassigned YES TFTP administratively down down
NVI0 192.168.1.254 YES unset up up
R2#ping 13.1.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 13.1.1.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R2#ping 192.168.2.254
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.254, timeout is 2 seconds:
U.U.U
Success rate is 0 percent (0/5)
2. 配置R2
第一阶段:协商秘钥参数
R2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#crypto isakmp policy 10
R2(config-isakmp)#encryption aes 256
R2(config-isakmp)#hash sha256
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#group 5
R2(config-isakmp)#lifetime 3600
第一阶段:配置预共享秘钥用于身份认证,由于R3是模拟任意公网路由器,其公网IP应该在现实中不知道的,所以这里的对端peer address为0.0.0.0,表示任意
R2(config-isakmp)#crypto isakmp key CISCO address 0.0.0.0
第二阶段:配置IPsec转换集
R2(config)#crypto ipsec transform-set mySET esp-aes 256 esp-sha256-hmac
R2(cfg-crypto-trans)#mode tunnel
R2(cfg-crypto-trans)#exit
配置dynamic crypto map:由于R2作为目标网络出口网关,其IP地址固定;但是
移动办公用户接入的出口路由器是任意的(这里是R3),所以无法指对端peer具体地址,同时也没有办法做到主动去匹配感兴趣流,只能被动响应
R2(config)#crypto dynamic-map MOBILE_USER 10
R2(config-crypto-map)#set transform-set mySET
R2(config-crypto-map)#exit
将动态crypto map与静态crypto map做关联: 因为dynamic crypto map 无法直接在接口下调用,只能关联后通过调用静态crypto map来间接关联动态的crypto map
R2(config)#crypto map myMAP 10 ipsec-isakmp dynamic MOBILE_USER
R2(config)#interface e0/1
R2(config-if)#crypto map myMAP
3. 配置R5
R5#CONF T
Enter configuration commands, one per line. End with CNTL/Z.
R5(config)#crypto isakmp policy 10
R5(config-isakmp)# encr aes 256
R5(config-isakmp)# hash sha256
R5(config-isakmp)# authentication pre-share
R5(config-isakmp)# group 5
R5(config-isakmp)# lifetime 3600
这里要指目标网络出口网关的地址
R5(config-isakmp)#crypto isakmp key CISCO address 12.1.1.2
第二阶段:转换集设置
R5(config)#crypto ipsec transform-set mySET esp-aes 256 esp-sha256-hmac
R5(cfg-crypto-trans)# mode tunnel
R5(cfg-crypto-trans)# exit
crypto map映射
R5(config)#crypto map myMAP 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R5(config-crypto-map)# set peer 12.1.1.2
R5(config-crypto-map)# match address 101
// 要配置转换集。不然会导致无法协商成功
R5(config-crypto-map)# set transform-set mySET
R5(config-crypto-map)# exit
定义感兴趣流量
R5(config)# access-list 101 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
R5-e0/0接口下调用
R5(config)# interface Ethernet0/0
R5(config-if)# crypto map myMAP
3. 验证
R2#show crypto session
Crypto session current status
Interface: Ethernet0/1
Session status: UP-ACTIVE
Peer: 13.1.1.3 port 4500
Session ID: 0
IKEv1 SA: local 12.1.1.2/4500 remote 13.1.1.3/4500 Active
IPSEC FLOW: permit ip 192.168.1.0/255.255.255.0 192.168.2.0/255.255.255.0
Active SAs: 2, origin: dynamic crypto map
R2#
R5#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 5/5/6 ms
R5#show crypto session
Crypto session current status
Interface: Ethernet0/0
Session status: UP-ACTIVE
Peer: 12.1.1.2 port 4500
Session ID: 0
IKEv1 SA: local 192.168.2.1/4500 remote 12.1.1.2/4500 Active
IPSEC FLOW: permit ip 192.168.2.0/255.255.255.0 192.168.1.0/255.255.255.0
Active SAs: 2, origin: crypto map
R4#ping 192.168.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
R4#
目标网络无法知道对端是何人来访问,所以R2是无法主动发起的,需要移动办公用户端主动发起流星触发IPSec, 触发之后,R4才可以再访问R5