IPSec的隧道嵌套
公网上架设多层隧道,整合不同隧道的优点,弥补缺点
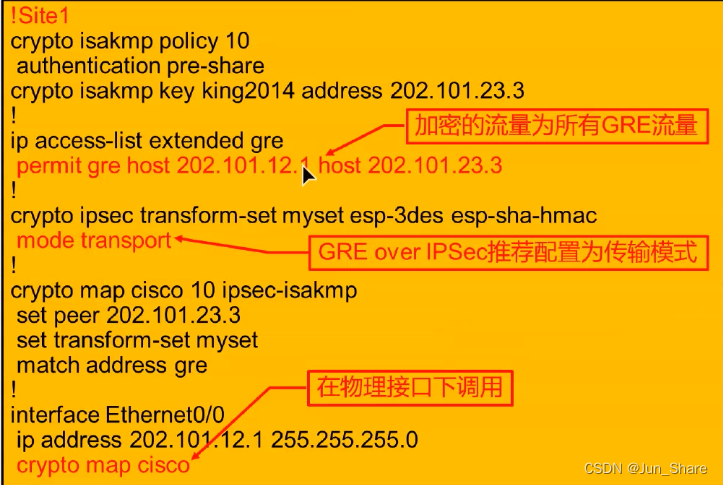
1、GRE over IPSec VPN
1)特点
通过GRE隧道运行的路由协议、组播等功能
通过IPSec提供数据的机密性、完整性检查、源认证
IPSec是保护GRE上面的所有流量(动态路由协议、ICMP、TCP/UDP)
封装模式采用传输模式,可以减少20字节的报文大小
先进行GRE的封装在进行IPSec的封装
2)IPSec Profile :
将二阶段的策略关联到隧道接口上
3)封装格式:
IPH(公)+IPSec+GRE+IPH(私)+DATA
配置:
crypto isakmp policy 10
encr 3des
authentication pre-share
group 5
crypto isakmp key 123 address 202.101.23.3
crypto ipsec transform-set cjj esp-3des esp-sha-hmac
mode transport --- 建议为传输模式
crypto ipsec profile cjj
set transform-set cjj
interface Tunnel1
tunnel protection ipsec profile cjj
华三:
#
ipsec transform-set HQ --- 二阶段的转换集
encapsulation-mode transport
protocol esp
esp encryption-algorithm 3des-cbc --- 加密
esp authentication-algorithm md5
#总部
ike proposal 1
encryption-algorithm 3des-cbc --- 加密
dh group5
authentication-algorithm md5 --- 完整性检查
#
ike keychain HQ
pre-shared-key hostname BR1 key cipher $c$3$aL2IbBi5F12wGpWsxjvOjwkUi+l7Dw==
#
ike keychain QH
pre-shared-key hostname BR2 key cipher $c$3$cRejsSLmF15105X6g39qJelzDOlbUg==
#
ike profile BR1
keychain HQ --- 预共享密钥
exchange-mode aggressive --- 模式:野蛮模式
match remote identity fqdn BR1 --- 对方的标识:主机名
proposal 1
#
ike profile BR2
keychain QH
exchange-mode aggressive
match remote identity fqdn BR2 --- 对等体
proposal 1
#
ipsec policy-template BR1 10 --- 关联一二阶段
transform-set HQ
ike-profile BR1
#
ipsec policy-template BR2 10 --- 关联一二阶段
transform-set HQ
ike-profile BR2
#
ipsec policy BR 1 isakmp template BR1
#
ipsec policy BR 2 isakmp template BR2
#
ike identity fqdn HQ
#
[HQ]dis cur int Tunnel 1
#
interface Tunnel1 mode gre
ip address 10.1.1.1 255.255.255.0
source GigabitEthernet0/0
destination 202.101.2.1
#
[HQ]dis cur int Tunnel 2
#
interface Tunnel2 mode gre
ip address 20.1.1.1 255.255.255.0
source GigabitEthernet0/0
destination 202.101.3.1
#
[HQ]dis cur int g0/0
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 202.101.1.1 255.255.255.0
ipsec apply policy BR
分部
#
ike proposal 1
encryption-algorithm 3des-cbc
dh group5
authentication-algorithm md5
#
ike keychain BR1
pre-shared-key address 202.101.1.1 255.255.255.255 key cipher $c$3$kCwhGhHKUDhkg3y519CgaeoHz6h10g==
#
ike profile HQ
keychain BR1
exchange-mode aggressive
match remote identity address 202.101.1.1 255.255.255.255
proposal 1
#
ipsec transform-set BR1
encapsulation-mode transport
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy BR1 10 isakmp
transform-set BR1
security acl 3000
remote-address 202.101.1.1
ike-profile HQ
#
ike identity fqdn BR1
interface Tunnel1 mode gre
ip address 10.1.1.2 255.255.255.0
source GigabitEthernet0/0
destination 202.101.1.1
#
interface GigabitEthernet0/0
port link-mode route
combo enable copper
ip address 202.101.2.1 255.255.255.0
ipsec apply policy BR1
2、IPSec over GRE VPN
1)特点
先进行IPSEC封装再进行GRE的封装
IPSEC保护的流量只是内网的流量,对OSPF、TCP等不做保护(ACL)
VPN的对等体不是物理接口,是隧道接口的IP
二阶段采用隧道模式
2)配置
华三:公用一个tunnel口
[BR1]ike proposal 1
[BR1-ike-proposal-1]quit
[BR1]ike keychain BR1
[BR1-ike-keychain-BR1]pre-shared-key address 192.168.13.1 key simple h3c
[BR1-ike-keychain-BR1]quit
[BR1]ike profile myprofile
[BR1-ike-profile-myprofile]local-identity address 192.168.13.3
[BR1-ike-profile-myprofile]match remote identity address 192.168.13.1
[BR1-ike-profile-myprofile]proposal 1
[BR1-ike-profile-myprofile]keychain BR1
[BR1-ike-profile-myprofile]quit
[BR1]ipsec transform-set myset
[BR1-ipsec-transform-set-myset]encapsulation-mode tunnel
[BR1-ipsec-transform-set-myset]protocol esp
[BR1-ipsec-transform-set-myset]esp encryption-algorithm 3des
[BR1-ipsec-transform-set-myset]esp authentication-algorithm sha1
[BR1-ipsec-transform-set-myset]quit
[BR1]acl advanced 3001
[BR1-acl-ipv4-adv-3001]rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
[BR1-acl-ipv4-adv-3001]quit
[BR1]ipsec policy mypolicy 1 isakmp
[BR1-ipsec-policy-isakmp-mypolicy-1]security acl 3001
[BR1-ipsec-policy-isakmp-mypolicy-1]transform-set myset
[BR1-ipsec-policy-isakmp-mypolicy-1]ike-profile myprofile
[BR1-ipsec-policy-isakmp-mypolicy-1]remote-address 192.168.13.1
[BR1-ipsec-policy-isakmp-mypolicy-1]quit
华为:两个隧道口(IPSec、GRE)
思科同华为
3)封装格式
封装格式:IPH(公)+GRE+IP(隧道)+IPSec+IPH(私)+DATA
3、L2TP over IPSec VPN
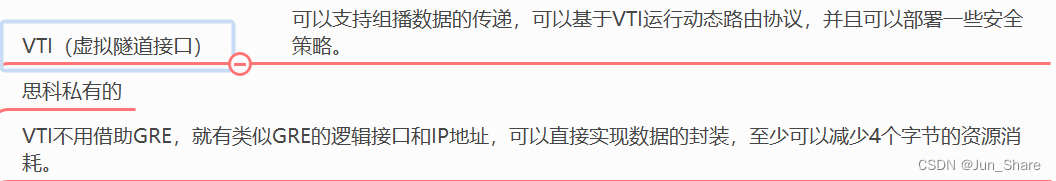
4、IPSec VTI
隧道的一种模式,可以像GRE一样运行路由协议、组播,但是没有GRE字段。减少报文的大小
可以部署QoS、防火墙等
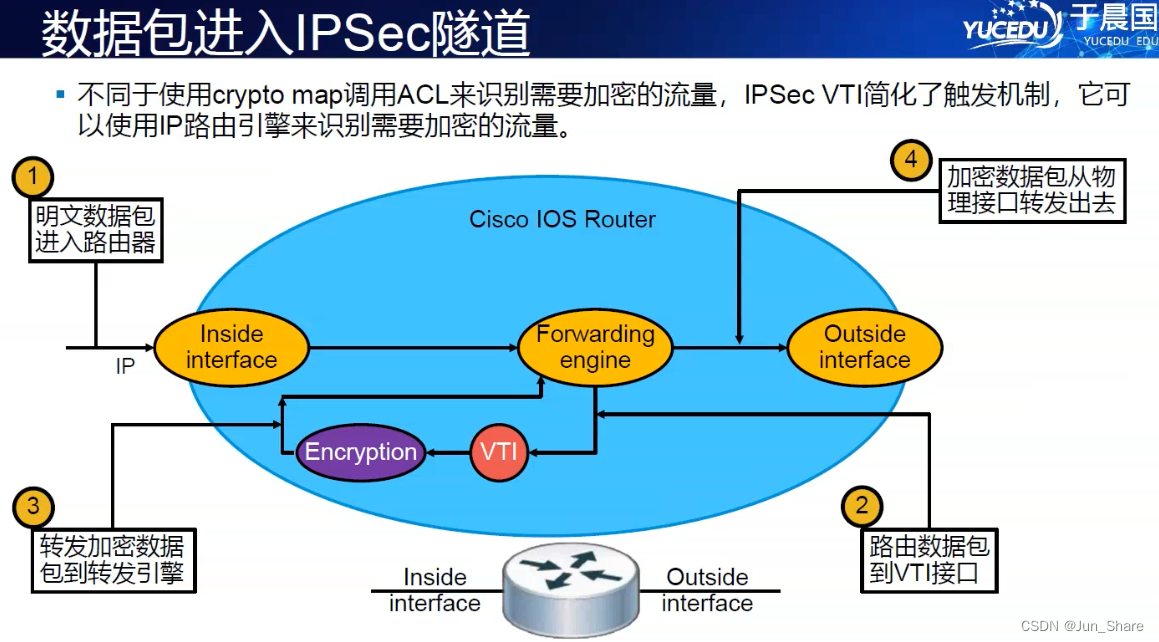
1)分类
【1】SVTI
一对一的场景
配置:
1、创建VTI
r3(config)#int tunnel13
r3(config-if)#ip add 192.168.13.3 255.255.255.0
r3(config-if)#tunnel source e0/0
r3(config-if)#tunnel destination 202.101.12.1
r3(config-if)#tunnel mode ipsec ipv4
//设置tunnel的模式为ipsec
2、设置ispec策略
r3(config)#crypto isakmp policy 10
r3(config-isakmp)#authentication pre-share
r3(config-isakmp)#ex
r3(config)#crypto isakmp key abc123 address 202.101.12.1
r3(config)#crypto ipsec transform-set myset esp-3des esp-sha-hmac
r3(cfg-crypto-trans)#mode tunnel
//设置封装模式为隧道模式(VTI没有额外新的一个头部)
r3(config)#crypto ipsec profile mypro
r3(ipsec-profile)#set transform-set myset
r3(config)#int tunnel13
r3(config-if)#tunnel protection ipsec profile mypro
3、启用ospf
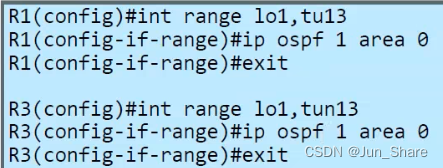
【2】DVTI
主要运用总部→分部的架构
如果采用GRE或者SVTI,当总部和分部需要建立VPN时,总部需要创建多个隧道
总部跟分部建立VPN时,总部只需要创建一个隧道接口
分支与分支之间互访需要经过总部中转
总部-分部的架构→DMVPN(动态多点VPN)
配置:
-----------------------------总部----------------------------------------------
crypto keyring Hub
pre-shared-key address 0.0.0.0 0.0.0.0 key cisco123
crypto isakmp profile zwh
keyring Hub
match identity address 0.0.0.0
virtual-template 1
crypto ipsec transform-set zwh esp-3des esp-sha-hmac
mode tunnel
crypto ipsec profile zwh
set transform-set zwh
set isakmp-profile zwh
interface Virtual-Template1 type tunnel
ip address 10.1.1.1 255.255.255.0
ip ospf 110 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile zwh
----------------------------分部---------------------------------------
crypto keyring R2
pre-shared-key address 202.101.1.1 key cisco123
crypto isakmp profile zwh
keyring R2
match identity address 202.101.1.1 255.255.255.255
crypto ipsec transform-set zwh esp-3des esp-sha-hmac
mode tunnel
crypto ipsec profile zwh
set transform-set zwh
set isakmp-profile zwh
interface Tunnel1
ip address 10.1.1.2 255.255.255.0
ip ospf 110 area 0
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination 202.101.1.1
tunnel protection ipsec profile zwh
5、高可用性
1)冗余性VPN
设置总部双VPN对等体,提高冗余性
如何检测主故障?
如何实现主、备切换?
2)IKE存活消息
当VPN的对等体之间失去IP可达性时,阶段一和阶段二状态依旧正常,这样会产生黑洞
在VPN对等体之间交换状态通告(密文),如果超过3次未确认,则删除相关的SA
配置:
R1(config)#crypto isakmp keepalive 10 3
10S周期发,超过3次就检测失败
如果存在多个分支,所有分支大量的IKE存活消息,总部路由器会消耗过多的CPU处理消息
3)DPD
失效对等体检测(对IK存活消息的优化)
检测方式:
①周期--- R1(config)#crypto isakmp keepalive 10 3 periodic
②按需--- crypto isakmp keepalive 10 3 on-demand
(当需要使用VPN时,先发送探测报文,检查VPN是否正常)
③超过五次认为失败
4)idle time
当IPSec SA处于闲置状态时,使能该机制,超过一定时间没有使用,IPSec SA删除
全局配置:
R2(config)#crypto ipsec security-association idle-time 60
crymap下的配置:
R2(config-crypto-map)#set security-association idle-time 60
5)RRI
反向路由注入
VPN设备根据数据包的源IP在路由表生成一条静态路由
当IPsec SA不存在时,静态也消失,但是可以通过增加“static”参数,保持静态路由一致有效
crypto map mymap 10 ipsec-isakmp
reverse-route //开启RRI
set reverse-route tag 10 //对注入进来的静态路由打上标记10
6)default peer configuration
当主VPN外网故障切换到备用VPN
配置:
crypto map xcie 10 ipsec-isakmp
set peer 202.101.2.1 default 设置为主
set peer 202.101.3.1
优化:内网故障切换到备用VPN
解决方案:(EEM检测)
event manager applet ospf_down
event syslog pattern "%OSPF-5-ADJCHG: Process 110, Nbr202.101.24.4 on Ethernet0/1 from FULL to DOWN"
action 1.0 cli command "enable"
action 2.0 cli command "configure terminal"
action 3.0 cli command "interface ethernet 0/0"
action 4.0 cli command "shutdown"
event manager applet ospf_up
event syslog pattern "%OSPF-5-ADJCHG: Process 110, Nbr3.3.3.3 on Ethernet0/1 from LOADING to FULL"
action 1.0 cli command "enable"
action 2.0 cli command "configure terminal"
action 3.0 cli command "interface ethernet 0/0"
action 4.0 cli command "no shutdown"
6、NAT对IPsecVPN的影响
1)VPN和NAT在同一台设备上
现象:VPN失败,NAT成功
原因:接口配置了NAT和VPN,先执行NAT再执行VPN
NAT将VPN流量的源IP转换为外网口
转换后的数据包无法匹配VPN的ACL,就无法触发VPN封装数据包的动作
路由器直接将访问其他站点的内网流量发送到外网,外网就直接丢包
解决方法:根因:NAT将VPN的流量转换了IP(不转)
NAT的ACL不转换VPN的流量
access-list 101 deny ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 剔除VPN的流量
access-list 101 permit ip 192.168.10.0 0.0.0.255 any NAT转换192.168.10.0访问其他的流量
顺序:由内到外---先NAT再VPN
由外到内---先VPN再NAT
2)VPN和NAT不在同一台设备上
IPsec的NAT穿越:NAT-T
问题:VPN的IP属于内网IP,其他站点对该IP缺乏路由可达性
希望能够访问外网IP映射到内网VPN的IP→静态NAT
当其他站点访问公网IP,通过NAT的映射关系将VPN发送到内网,实现VPN建立
现象:解决了VPN的建立即可通信,NAT与VPN现象均正常
抓包发现ESP封装正在UDP之上端口为4500,NAT转化表中也有相同记录
PAT需要端口号,但是ESP基于IP协议,没有端口号无法NAT转换
为了让VPN流量能够穿越NAT,那么就会产生ESP在UDP下4500的端口号,方便NAT转换

























![[C#]OpenCvSharp使用HoughCircles霍夫圆检测算法找出圆位置并计数](https://img-blog.csdnimg.cn/direct/ba115db096aa461c8b13aa453312a5ed.jpeg)