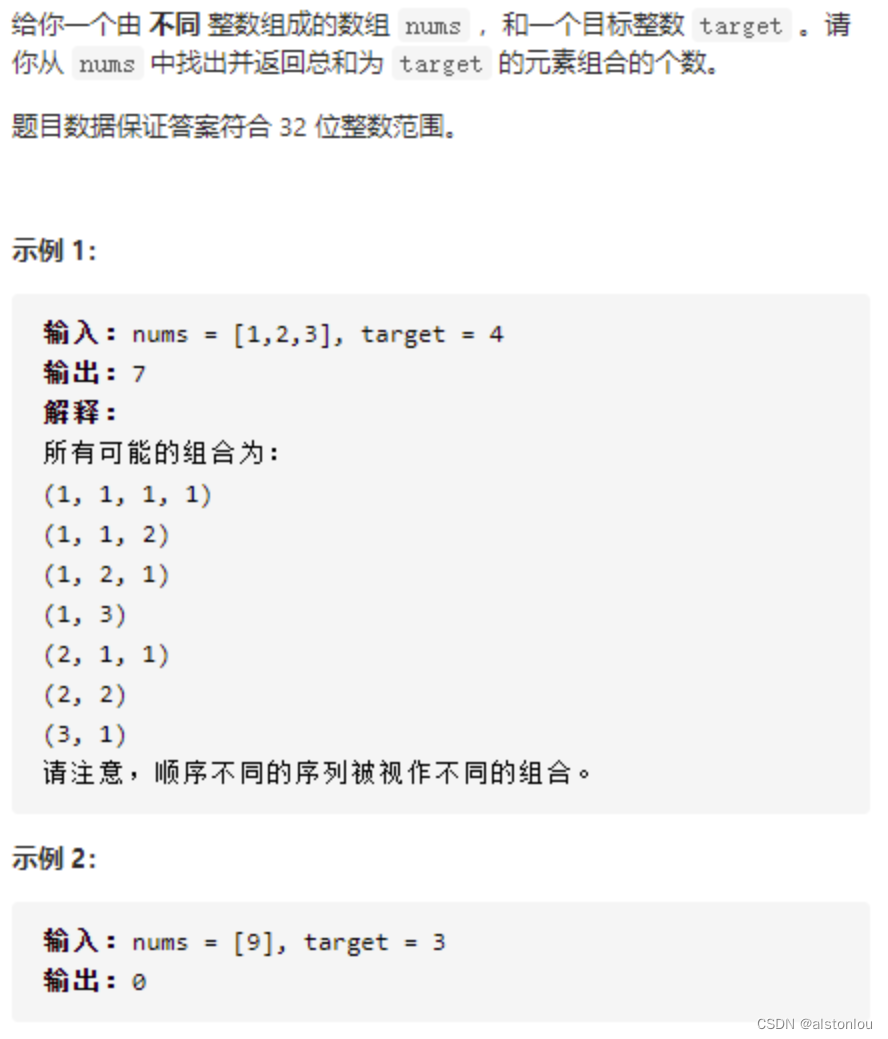
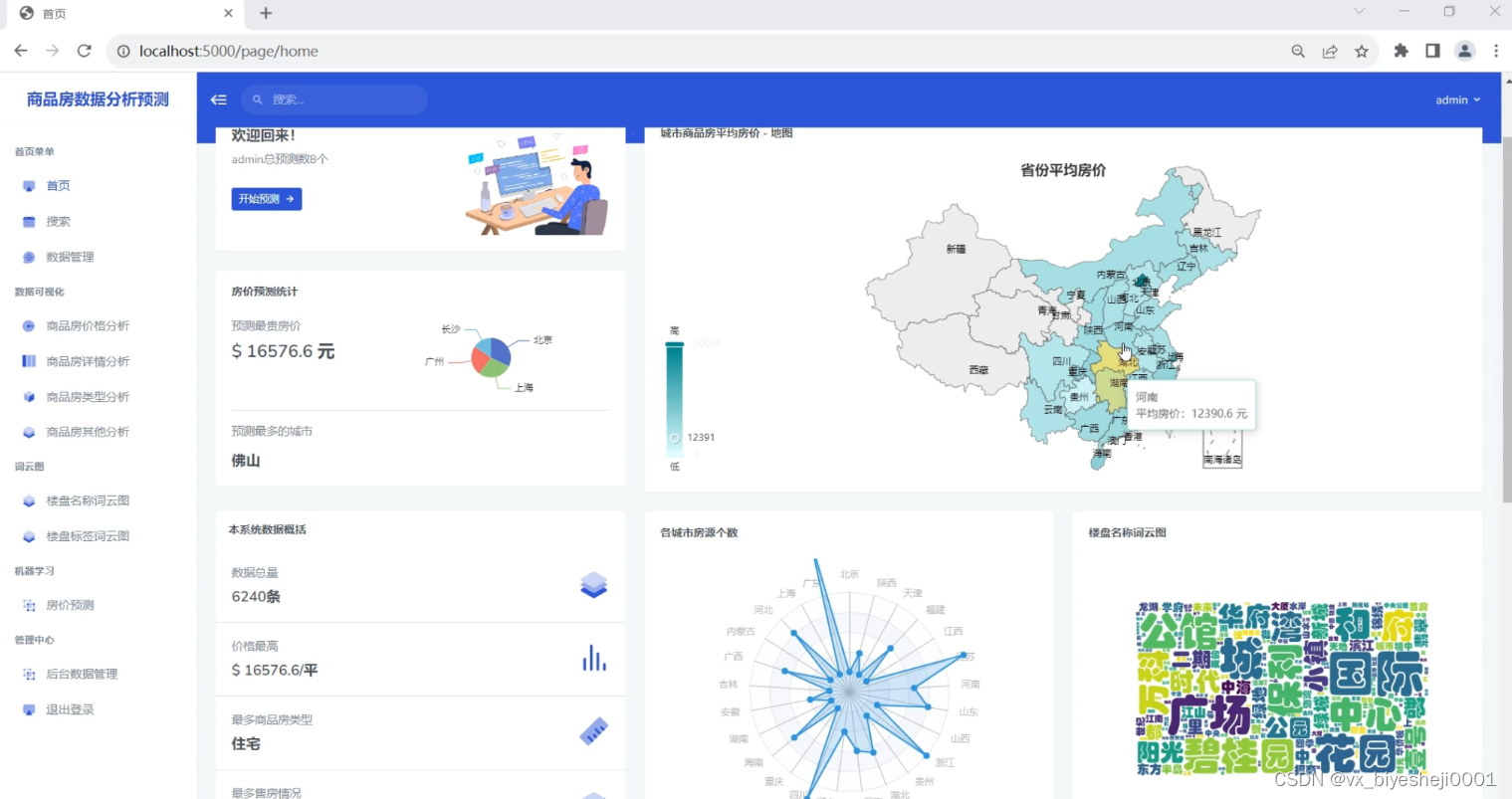
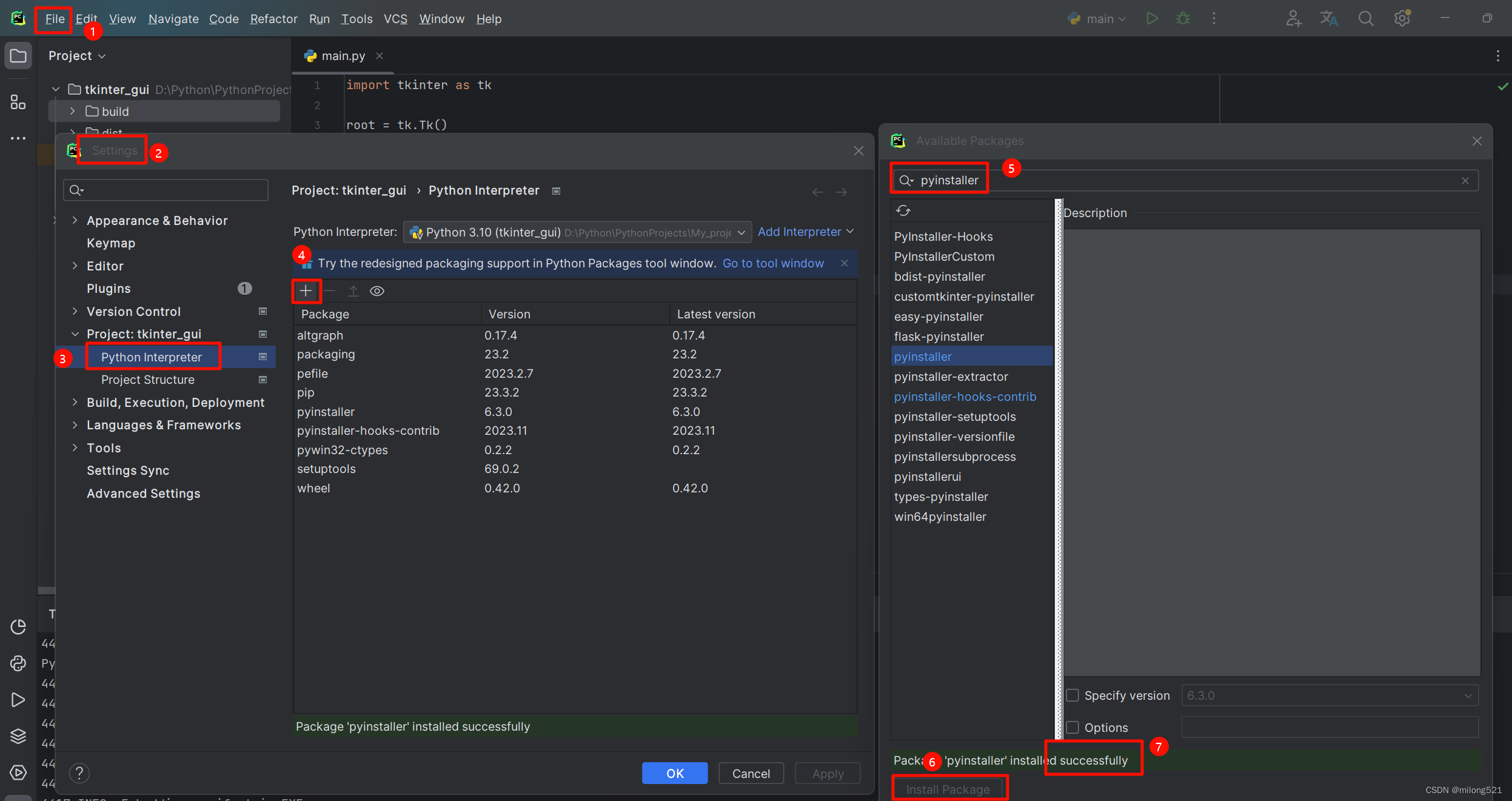
使用Azure Powershell 设置 Rule Collection Group, 首先需要创建 Firewall policy。
在创建完firewall policy后,通过Azure Portal页面添加 Rule Collection Group。
然后就可以使用 Set-AzFirewallPolicyRuleCollectionGroup命令在Firewall policy中添加Rule Collection Group了。
以下是一个简单例子,通过Azure Powershell在Rule Collection Group中添加Rule Collection和Rules。
$resourceGroup = "test_rg"
$fprg = $resourceGroup
$targetfp = Get-AzFirewallPolicy -Name "testFWpolicy" -ResourceGroupName $fprg //获取Firewall Policy对象
$targetrcg = Get-AzFirewallPolicyRuleCollectionGroup -AzureFirewallPolicyName "vincentFWpolicy" -Name "network-segmentation-local" -ResourceGroupName $resourceGroup //获取Rule Collection Group对象
$rules = @()
$RuleParameter = @{
Name = "net-pde-to-external-prod-allowasdfajsdlflklkajlkfd"
Protocol = "Any"
sourceAddress = "*"
DestinationAddress = "*"
DestinationPort = "*"
}
$rule = New-AzFirewallPolicyNetworkRule @RuleParameter
$NetworkRuleCollection = @{
Name = "src-azure-network-rules-segmentation-allow"
Priority = "666"
ActionType = "Allow"
Rule = $rules += $rule
} //在第一个Rule Collection中添加Rule
$NetworkRuleCategoryCollection = New-AzFirewallPolicyFilterRuleCollection @NetworkRuleCollection
$rules = @()
$RuleParameter = @{
Name = "net-pde-to-external-prod-allow-all2"
Protocol = "Any"
sourceAddress = "*"
DestinationAddress = "*"
DestinationPort = "*"
}
$rule = New-AzFirewallPolicyNetworkRule @RuleParameter
$NetworkRuleCollection2 = @{
Name = "src-azure-network-rules-segmentation-allowasdfasdf2"
Priority = "888"
ActionType = "Allow"
Rule = $rules += $rule
} //在第二个Rule Collection中添加Rule
$NetworkRuleCategoryCollection2 = New-AzFirewallPolicyFilterRuleCollection @NetworkRuleCollection2
//将以上创建的两个Rule Collection加入Rule Collection Group对象
$targetrcg.Properties.RuleCollection.Add($NetworkRuleCategoryCollection)
$targetrcg.Properties.RuleCollection.Add($NetworkRuleCategoryCollection2)
//设置保存Rule Collection Group并使其生效
Set-AzFirewallPolicyRuleCollectionGroup -FirewallPolicyName testFWpolicy -Name $targetrcg.Name -Priority 112 -ResourceGroupName test_rg -RuleCollection $targetrcg.Properties.RuleCollection
需要注意的问题:
Set-AzFirewallPolicyRuleCollectionGroup这个命令执行的是Overwrite操作,它会保存命令中的多个Rule Collection。同时会覆盖掉之前的配置,如果保存之前在Rule Collection Group中存在其他的Rule Collection,那么这些没有在命令中被写入的Rule Collection就会被擦除。所以如果想一次在Rule Collection Group中设置多个Rule Collection。需要在参数中指定多个Rule Collection的数组。
参考文档:
Set-AzFirewallPolicyRuleCollectionGroup (Az.Network) | Microsoft Learn