Conference:International Conference on Software Engineering (ICSE)
CCF level:CCF A
Categories:Software Engineering/System Software/Programming Languages
Year:2024
Num:13
1
Title:
Smart Contract and DeFi Security Tools: Do They Meet the Needs of Practitioners?
智能合约和 DeFi 安全工具:它们能满足从业者的需求吗?
Authors:

Abstract:
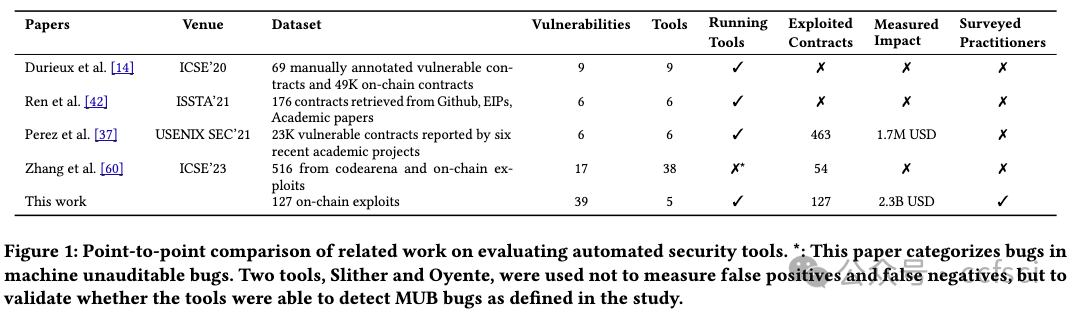
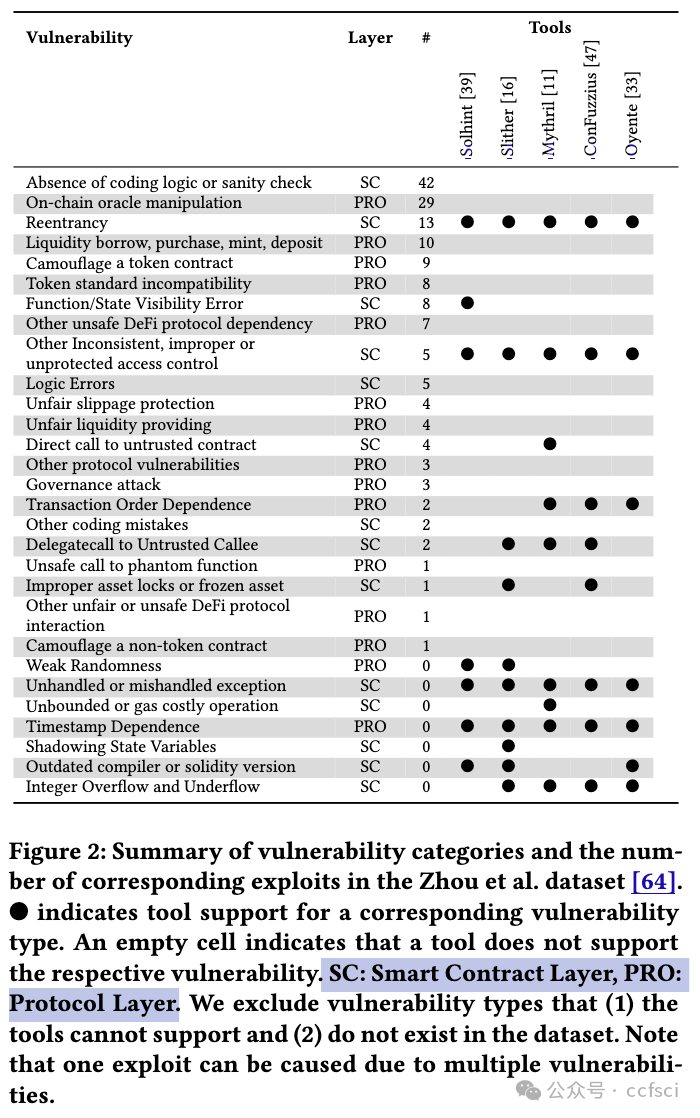
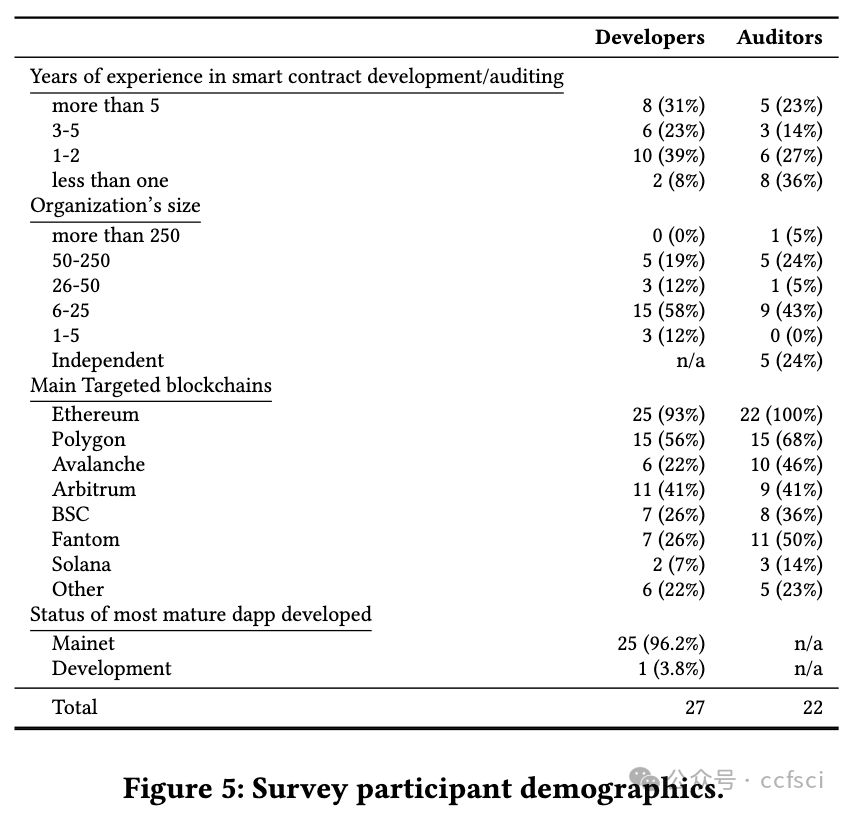
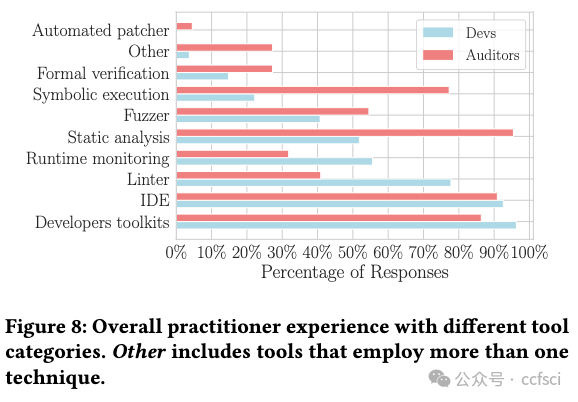
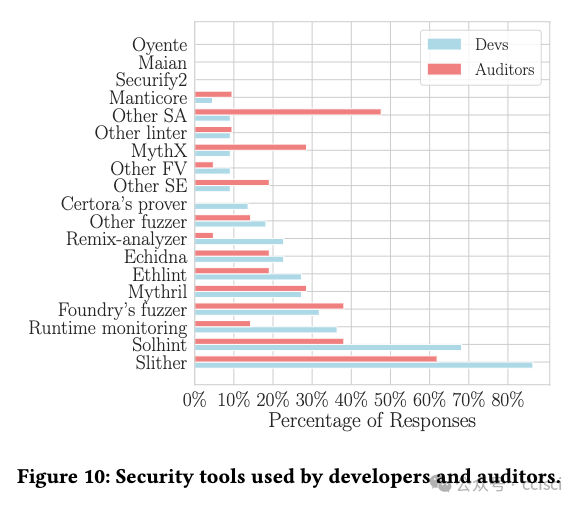
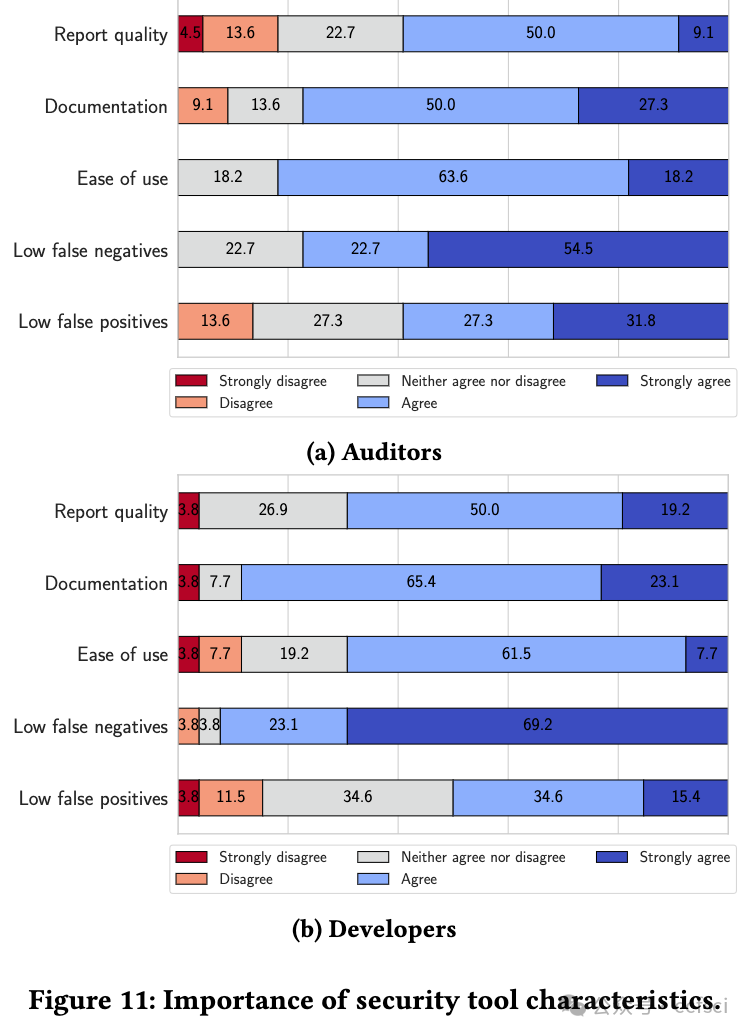
The growth of the decentralized finance (DeFi) ecosystem built on blockchain technology and smart contracts has led to an increased demand for secure and reliable smart contract development. However, attacks targeting smart contracts are increasing, causing an estimated $6.45 billion in financial losses. Researchers have proposed various automated security tools to detect vulnerabilities, but their real-world impact remains uncertain. In this paper, we aim to shed light on the effectiveness of automated security tools in identifying vulnerabilities that can lead to high-profile attacks, and their overall usage within the industry. Our comprehensive study encompasses an evaluation of five SoTA automated security tools, an analysis of 127 high-impact real-world attacks resulting in $2.3 billion in losses, and a survey of 49 developers and auditors working in leading DeFi protocols. Our findings reveal a stark reality: the tools could have prevented a mere 8% of the attacks in our dataset, amounting to $149 million out of the $2.3 billion in losses. Notably, all preventable attacks were related to reentrancy vulnerabilities. Furthermore, practitioners distinguish logic-related bugs and protocol layer vulnerabilities as significant threats that are not adequately addressed by existing security tools. Our results emphasize the need to develop specialized tools catering to the distinct demands and expectations of developers and auditors. Further, our study highlights the necessity for continuous advancements in security tools to effectively tackle the ever-evolving challenges confronting the DeFi ecosystem.
建立在区块链技术和智能合约基础上的去中心化金融(DeFi)生态系统的发展,导致对安全可靠的智能合约开发的需求增加。然而,针对智能合约的攻击正在增加,估计造成了 64.5 亿美元的经济损失。研究人员提出了各种自动安全工具来检测漏洞,但它们在现实世界中的影响仍不确定。在本文中,我们旨在阐明自动安全工具在识别可能导致重大攻击的漏洞方面的有效性,以及它们在行业内的总体使用情况。我们的综合研究包括对五种 SoTA 自动安全工具的评估、对 127 次造成 23 亿美元损失的高影响真实攻击的分析,以及对 49 名在主要 DeFi 协议中工作的开发人员和审计人员的调查。我们的研究结果揭示了一个严酷的现实:在我们的数据集中,这些工具仅能阻止 8% 的攻击,在 23 亿美元的损失中仅占 1.49 亿美元。值得注意的是,所有可预防的攻击都与重入性漏洞有关。此外,从业人员将与逻辑相关的漏洞和协议层漏洞视为现有安全工具无法充分解决的重大威胁。我们的研究结果表明,有必要开发专门的工具,以满足开发人员和审计人员的不同需求和期望。此外,我们的研究还强调了不断改进安全工具以有效应对 DeFi 生态系统所面临的不断变化的挑战的必要性。



Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3623302
2
Title:
Revealing Hidden Threats: An Empirical Study of Library Misuse in Smart Contracts
揭示隐藏的威胁:智能合约中库滥用的实证研究
Authors:

Abstract:
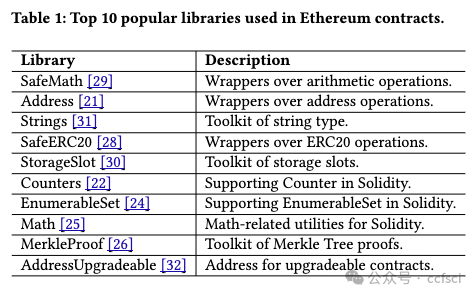
Smart contracts are Turing-complete programs that execute on the blockchain. Developers can implement complex contracts, such as auctions and lending, on Ethereum using the Solidity programming language. As an object-oriented language, Solidity provides libraries within its syntax to facilitate code reusability and reduce development complexity. Library misuse refers to the incorrect writing or usage of libraries, resulting in unexpected results, such as introducing vulnerabilities during library development or incorporating an unsafe library during contract development. Library misuse could lead to contract defects that cause financial losses. Currently, there is a lack of research on library misuse. To fill this gap, we collected more than 500 audit reports from the official websites of five audit companies and 223,336 real-world smart contracts from Etherscan to measure library popularity and library misuse. Then, we defined eight general patterns for library misuse; three of them occurring during library development and five during library utilization, which covers the entire library lifecycle. To validate the practicality of these patterns, we manually analyzed 1,018 real-world smart contracts and publicized our dataset. We identified 905 misuse cases across 456 contracts, indicating that library misuse is a widespread issue. Three patterns of misuse are found in more than 50 contracts, primarily due to developers lacking security awareness or underestimating negative impacts. Additionally, our research revealed that vulnerable libraries on Ethereum continue to be employed even after they have been deprecated or patched. Our findings can assist contract developers in preventing library misuse and ensuring the safe use of libraries.
智能合约是执行在区块链上的图灵完备程序。开发者可以使用 Solidity 编程语言在以太坊上实现复杂的合约,例如拍卖和借贷。作为面向对象的语言,Solidity 在其语法中提供了库,以促进代码可重用性并降低开发复杂性。库滥用是指库的编写或使用不正确,导致意想不到的结果,例如在库开发过程中引入漏洞或在合约开发过程中合并不安全的库。库滥用可能导致合约缺陷,从而造成财务损失。目前,对库滥用的研究还很缺乏。为了填补这一空白,我们从五家审计公司的官方网站收集了 500 多份审计报告,从 Etherscan 收集了 223,336 个现实世界的智能合约,以衡量库的流行度和库滥用。然后,我们定义了库滥用的八种一般模式;其中三种发生在库开发期间,五种发生在库使用期间,涵盖了整个库生命周期。为了验证这些模式的实用性,我们手动分析了 1,018 个现实世界的智能合约并公布了我们的数据集。我们在 456 份合约中发现了 905 起滥用案例,表明库滥用是一个普遍存在的问题。在 50 多个合约中发现了三种滥用模式,主要是由于开发人员缺乏安全意识或低估了负面影响。此外,我们的研究还发现,以太坊上的易受攻击的库即使在被弃用或修补后仍会继续使用。我们的研究结果可以帮助合约开发人员防止库滥用并确保库的安全使用。
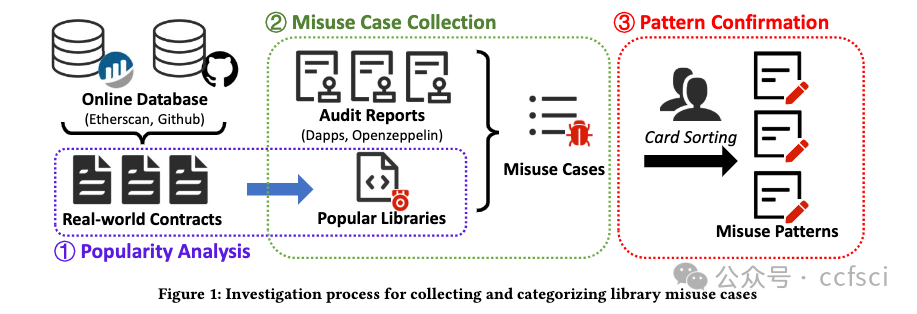
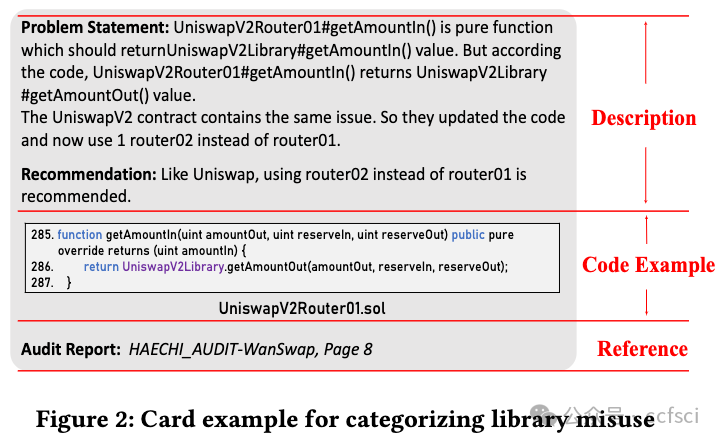
LIBRARY MISUSE PATTERNS
P1: Invalid Wrapper Check in Library
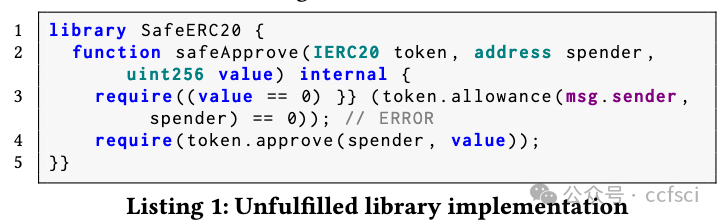
P2: Unhandled Exceptions in Library
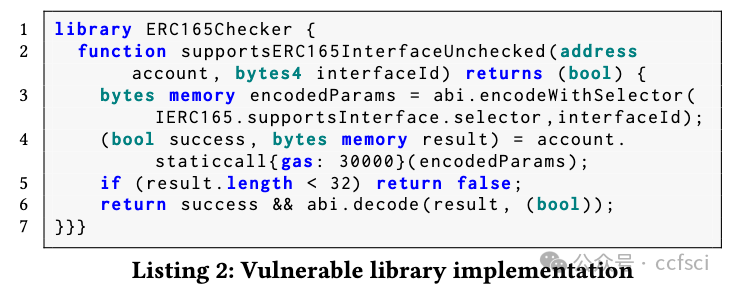
P3: Inappropriate Library Extension
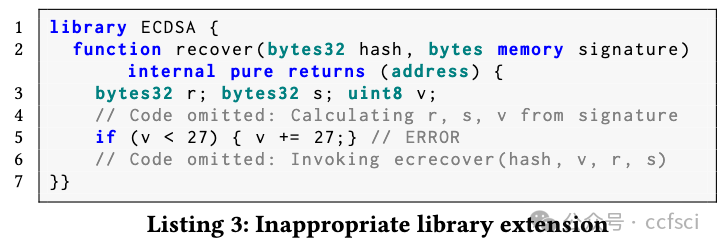
P4: Inappropriate Using For
P5: Incomplete Function Replacement

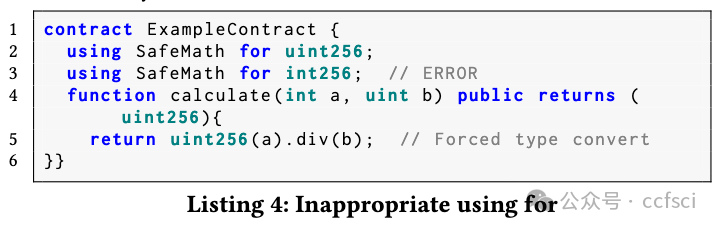
P6: Overestimated Library Capability

P7: Underestimated Library Capability
P8: Unnecessary Library Using
Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3623335
3
Title:
PonziGuard: Detecting Ponzi Schemes on Ethereum with Contract Runtime Behavior Graph (CRBG)
PonziGuard:使用合约运行时行为图(CRBG)检测以太坊上的庞氏骗局
Authors:

Key words:
Smart Contract, Ponzi Scheme, Flow Analysis, Graph Neural Networks
智能合约、庞氏骗局、流量分析、图神经网络
Abstract:
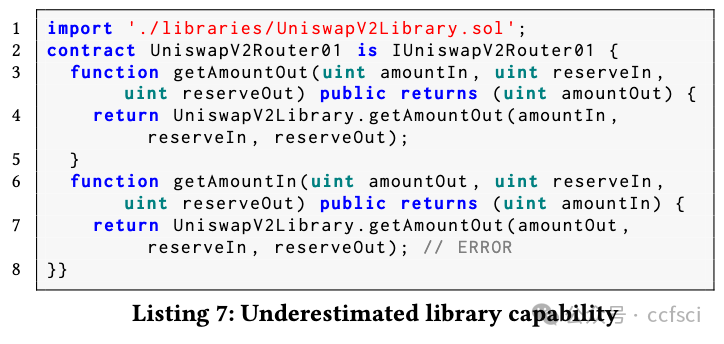
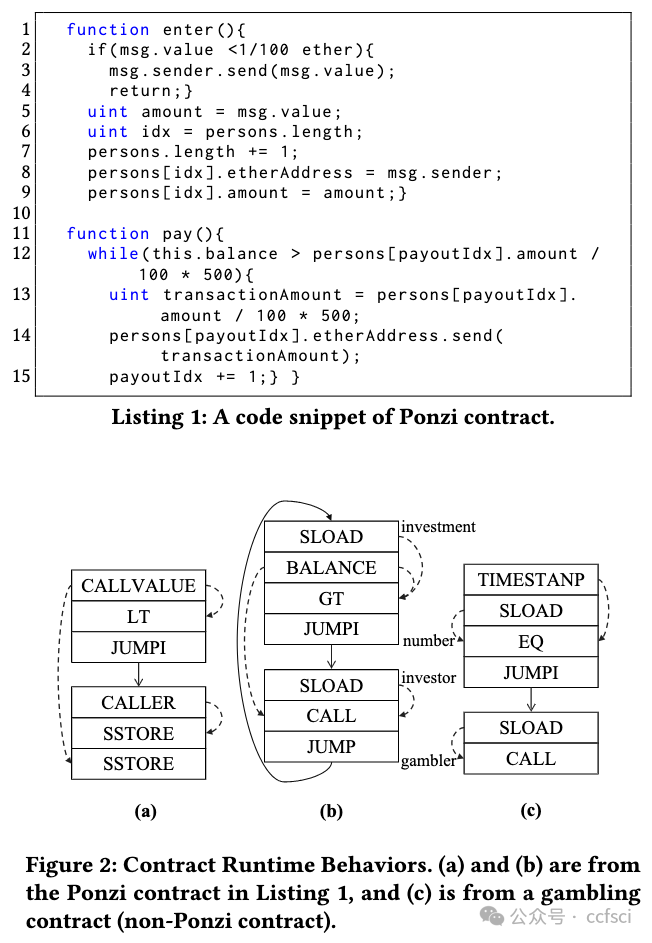
Ponzi schemes, a form of scam, have been discovered in Ethereum smart contracts in recent years, causing massive financial losses. Rule-based detection approaches rely on pre-defined rules with limited capabilities and domain knowledge dependency. Additionally, using static information like opcodes and transactions for machine learning models fails to effectively characterize the Ponzi contracts, resulting in poor reliability and interpretability. In this paper, we propose PonziGuard, an efficient Ponzi scheme detection approach based on contract runtime behavior. Inspired by the observation that a contract's runtime behavior is more effective in disguising Ponzi contracts from the innocent contracts, PonziGuard establishes a comprehensive graph representation called contract runtime behavior graph (CRBG), to accurately depict the behavior of Ponzi contracts. Furthermore, it formulates the detection process as a graph classification task, enhancing its overall effectiveness. We conducted comparative experiments on a ground-truth dataset and applied PonziGuard to Ethereum Mainnet. The results show that PonziGuard outperforms the current state-of-the-art approaches and is also effective in open environments. Using PonziGuard, we have identified 805 Ponzi contracts on Ethereum Mainnet, which have resulted in an estimated economic loss of 281,700 Ether or approximately $500 million USD.
近年来,庞氏骗局在以太坊智能合约中被发现,造成了巨大的经济损失。基于规则的检测方法依赖于功能有限且依赖领域知识的预定义规则。此外,使用操作码和交易等静态信息进行机器学习模型无法有效表征庞氏合约,导致可靠性和可解释性较差。在本文中,我们提出了一种基于合约运行时行为的高效庞氏骗局检测方法 PonziGuard。受合约运行时行为更有效地将庞氏合约与无辜合约区分开来的启发,PonziGuard 建立了一种称为合约运行时行为图 (CRBG) 的综合图形表示,以准确描述庞氏合约的行为。此外,它将检测过程制定为图形分类任务,从而提高了其整体有效性。我们在真实数据集上进行了比较实验,并将 PonziGuard 应用于以太坊主网。结果表明,PonziGuard 优于目前最先进的方法,并且在开放环境中也有效。使用 PonziGuard,我们在以太坊主网上发现了 805 个庞氏骗局合约,这些合约造成的经济损失估计为 281,700 以太币,约合 5 亿美元。
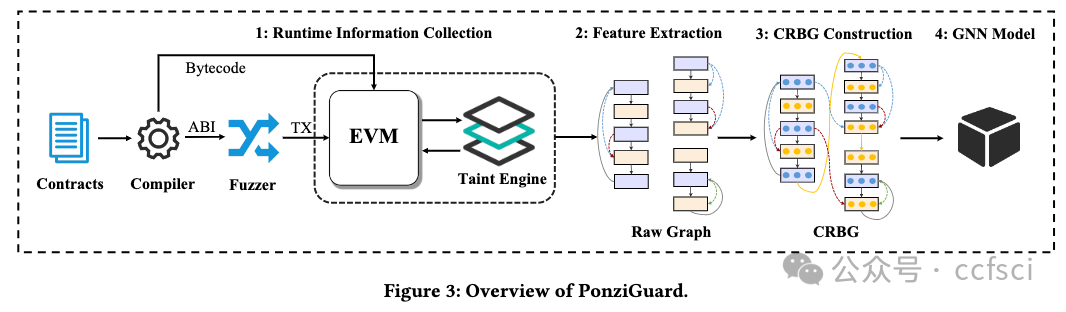


Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3623318
4
Title:
Are We There Yet? Unraveling the State-of-the-Art Smart Contract Fuzzers
我们到了吗?揭秘最先进的智能合约模糊测试器
Authors:

Key words:
Smart Contract, Fuzzing, Evaluation
智能合约,模糊测试,评估
Abstract:
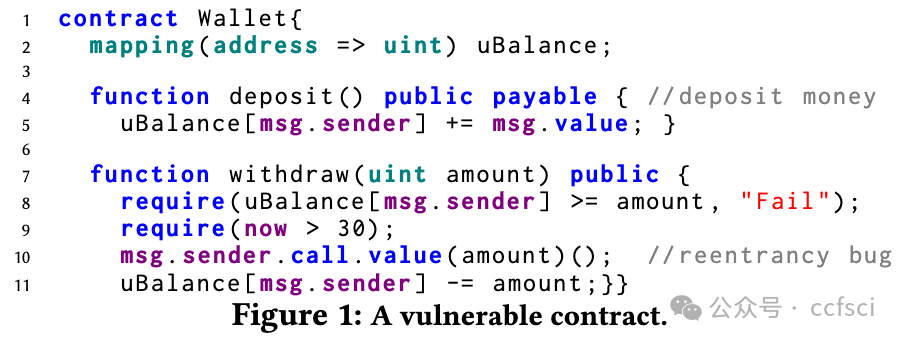
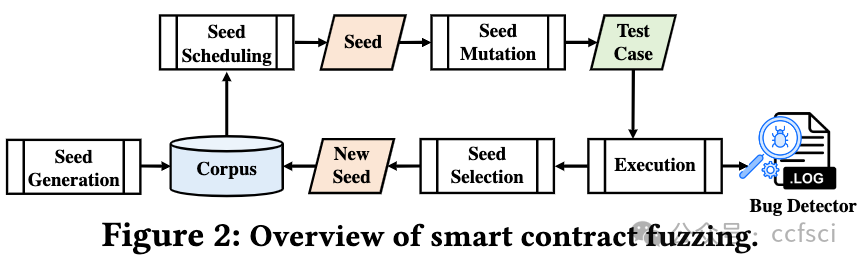
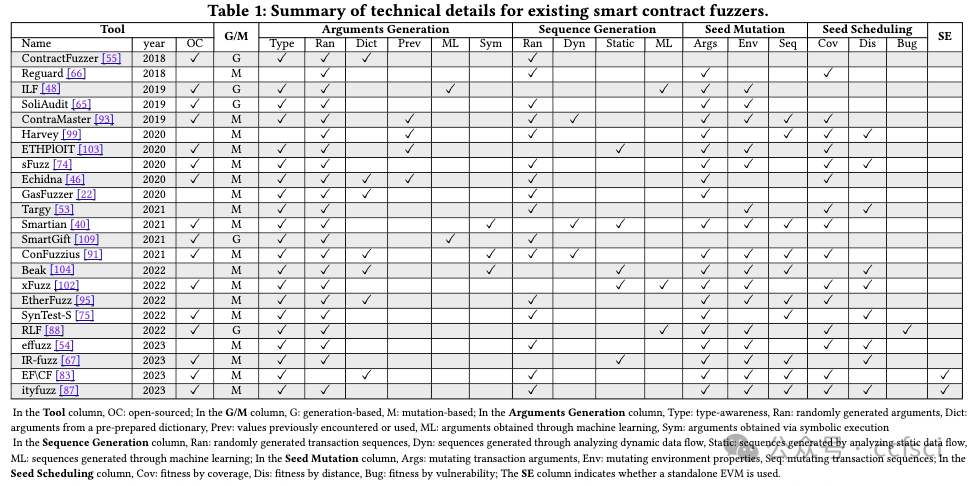
Given the growing importance of smart contracts in various applications, ensuring their security and reliability is critical. Fuzzing, an effective vulnerability detection technique, has recently been widely applied to smart contracts. Despite numerous studies, a systematic investigation of smart contract fuzzing techniques remains lacking. In this paper, we fill this gap by: 1) providing a comprehensive review of current research in contract fuzzing, and 2) conducting an in-depth empirical study to evaluate state-of-the-art contract fuzzers' usability. To guarantee a fair evaluation, we employ a carefully-labeled benchmark and introduce a set of pragmatic performance metrics, evaluating fuzzers from five complementary perspectives. Based on our findings, we provide direction for the future research and development of contract fuzzers.
鉴于智能合约在各种应用中的重要性日益增加,确保其安全性和可靠性至关重要。模糊测试是一种有效的漏洞检测技术,最近已广泛应用于智能合约。尽管有大量研究,但对智能合约模糊测试技术的系统研究仍然缺乏。在本文中,我们通过以下方式填补了这一空白:1)全面回顾合约模糊测试的当前研究;2)进行深入的实证研究以评估最先进的合约模糊测试器的可用性。为了保证公平的评估,我们采用了精心标记的基准并引入了一组实用的性能指标,从五个互补的角度评估模糊测试器。根据我们的研究结果,我们为合约模糊测试器的未来研究和开发提供了方向。
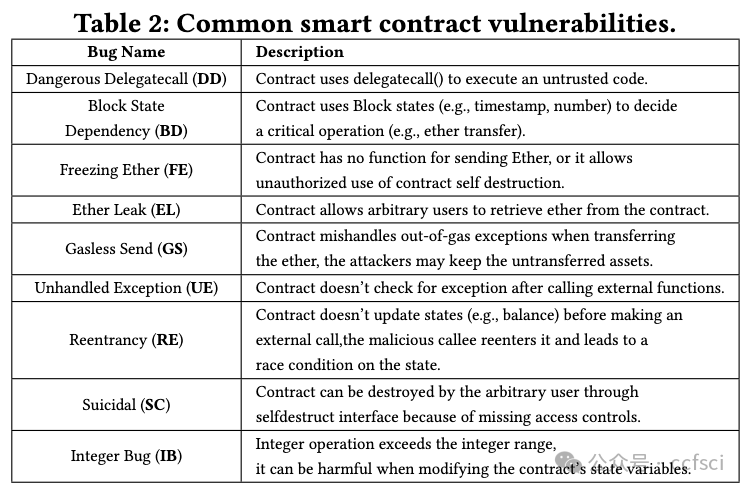
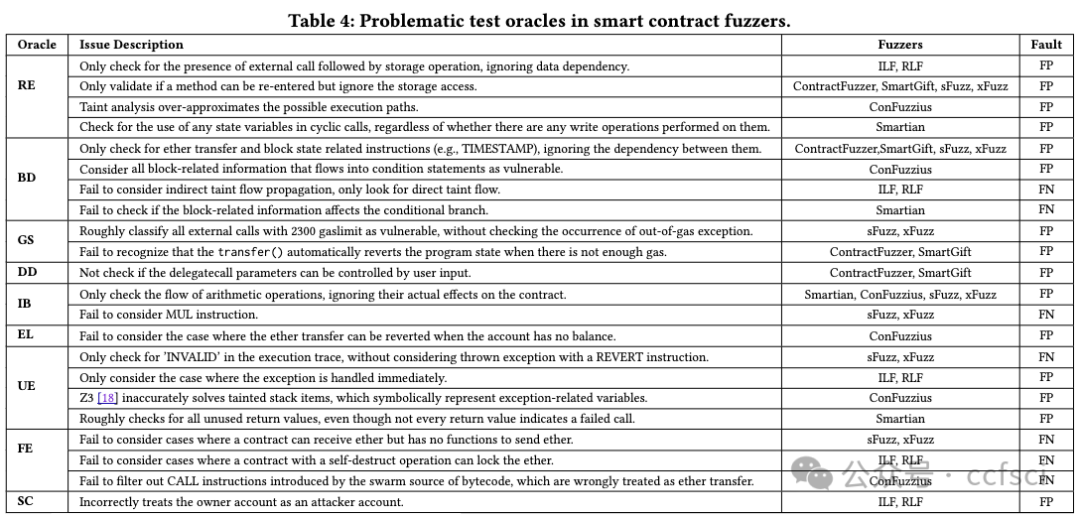
Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639152
5
Title:
Uncover the Premeditated Attacks: Detecting Exploitable Reentrancy Vulnerabilities by Identifying Attacker Contracts
发现有预谋的攻击:通过识别攻击者合约来检测可利用的重入漏洞
Authors:

Key words:
Smart Contract; Dataflow Analysis; Reentrancy; Attacker Identification; Ethereum
智能合约;数据流分析;重入性;攻击者识别;以太坊
Abstract:
Reentrancy, a notorious vulnerability in smart contracts, has led to millions of dollars in financial loss. However, current smart contract vulnerability detection tools suffer from a high false positive rate in identifying contracts with reentrancy vulnerabilities. Moreover, only a small portion of the detected reentrant contracts can actually be exploited by hackers, making these tools less effective in securing the Ethereum ecosystem in practice. In this paper, we propose BlockWatchdog, a tool that focuses on detecting reentrancy vulnerabilities by identifying attacker contracts. These attacker contracts are deployed by hackers to exploit vulnerable contracts automatically. By focusing on attacker contracts, BlockWatchdog effectively detects truly exploitable reentrancy vulnerabilities by identifying reentrant call flow. Additionally, BlockWatchdog is capable of detecting new types of reentrancy vulnerabilities caused by poor designs when using ERC tokens or user-defined interfaces, which cannot be detected by current rule-based tools. We implement BlockWatchdog using cross-contract static dataflow techniques based on attack logic obtained from an empirical study that analyzes attacker contracts from 281 attack incidents. BlockWatchdog is evaluated on 421,889 Ethereum contract bytecodes and identifies 113 attacker contracts that target 159 victim contracts, leading to the theft of Ether and tokens valued at approximately 908.6 million USD. Notably, only 18 of the identified 159 victim contracts can be reported by current reentrancy detection tools.
重入漏洞是智能合约中一个臭名昭著的漏洞,已导致数百万美元的财务损失。然而,目前的智能合约漏洞检测工具在识别具有重入漏洞的合约时存在较高的误报率。此外,检测到的重入合约中只有一小部分可以被黑客利用,这使得这些工具在实践中无法有效地保护以太坊生态系统。在本文中,我们提出了 BlockWatchdog,这是一种专注于通过识别攻击者合约来检测重入漏洞的工具。黑客部署这些攻击者合约来自动利用易受攻击的合约。通过专注于攻击者合约,BlockWatchdog 可以通过识别重入调用流有效地检测出真正可利用的重入漏洞。此外,BlockWatchdog 能够检测使用 ERC 代币或用户定义接口时因设计不良而导致的新型重入漏洞,而目前的基于规则的工具无法检测到这些漏洞。我们使用跨合约静态数据流技术实现 BlockWatchdog,该技术基于从实证研究中获得的攻击逻辑,该研究分析了 281 起攻击事件中的攻击者合约。BlockWatchdog 对 421,889 个以太坊合约字节码进行了评估,并识别出 113 个攻击者合约,这些合约针对 159 个受害者合约,导致价值约 9.086 亿美元的 Ether 和代币被盗。值得注意的是,在已识别的 159 个受害者合约中,目前的重入检测工具只能报告 18 个。
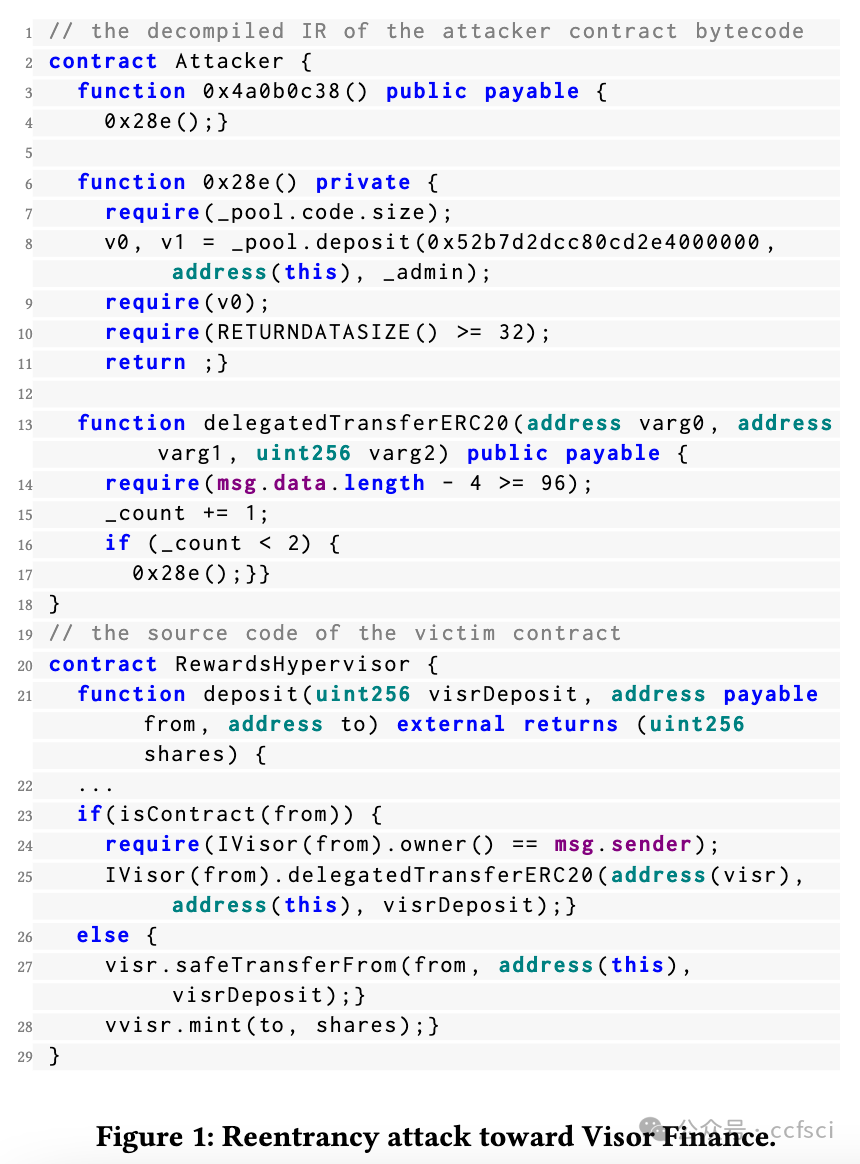
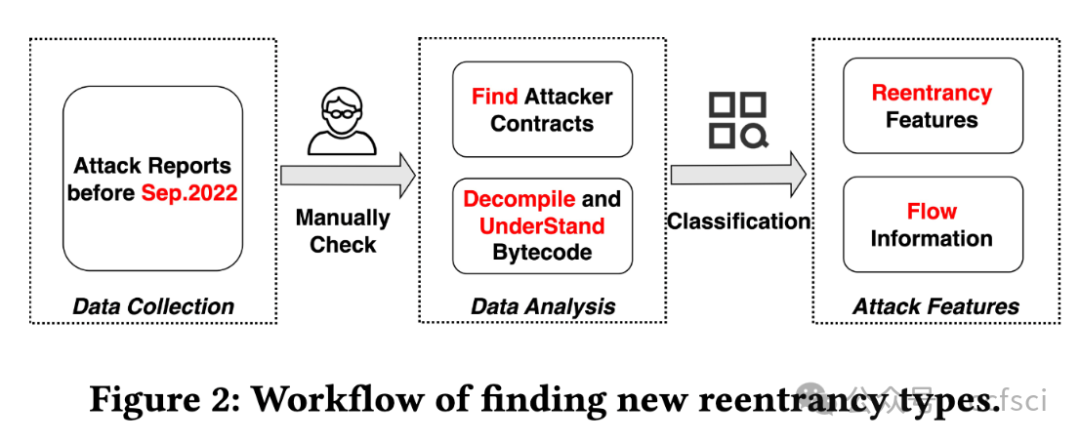

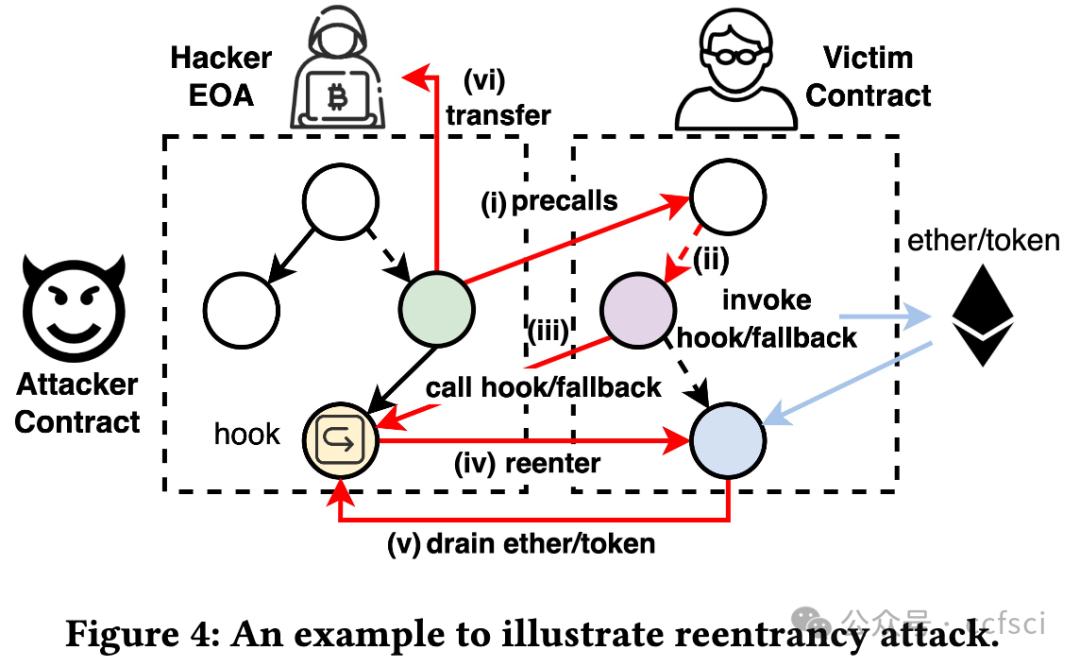
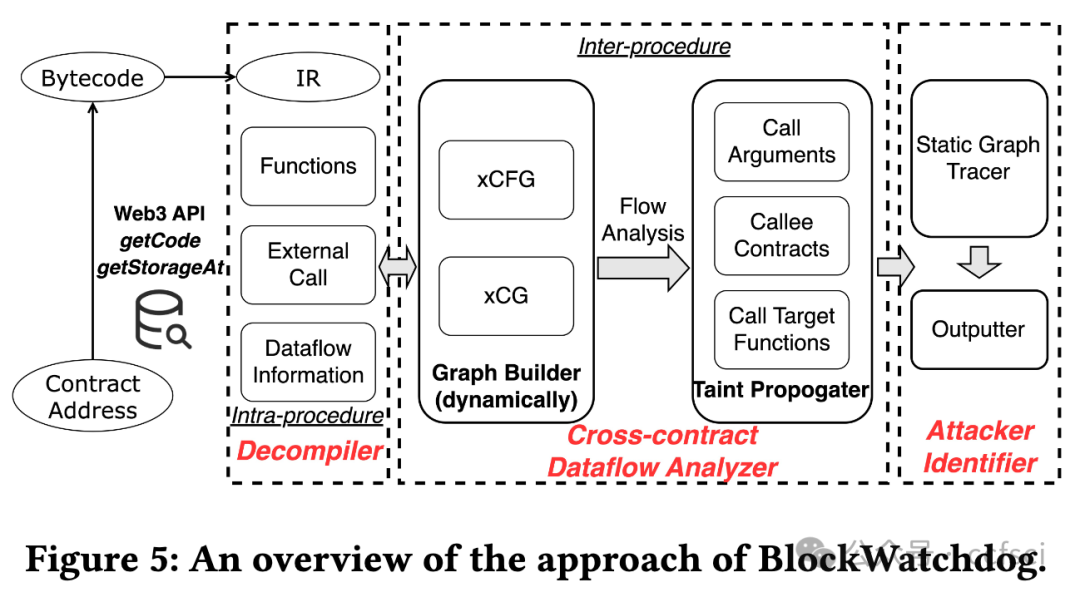
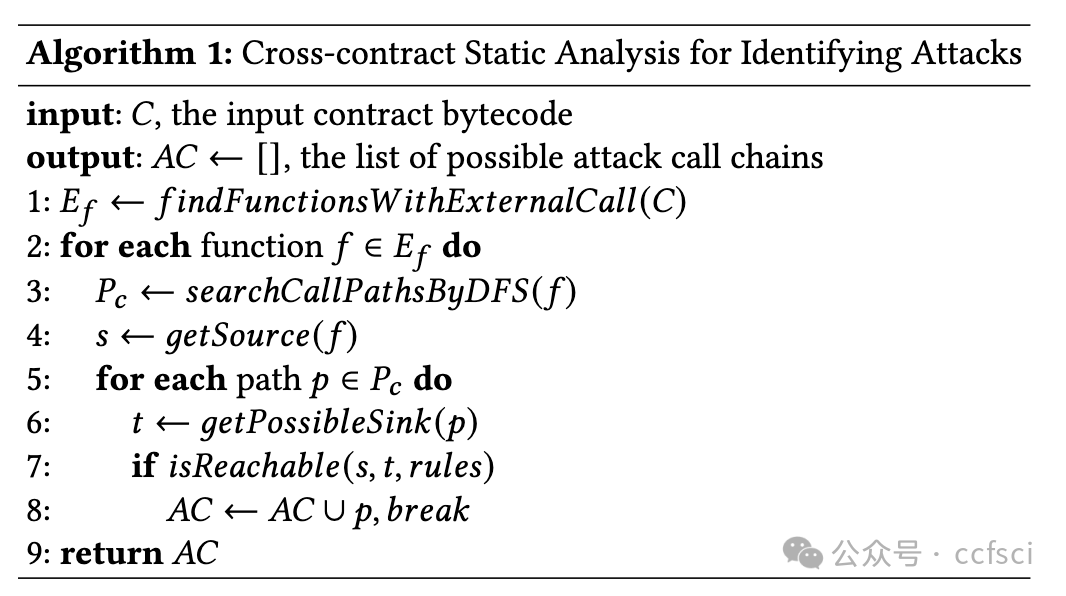
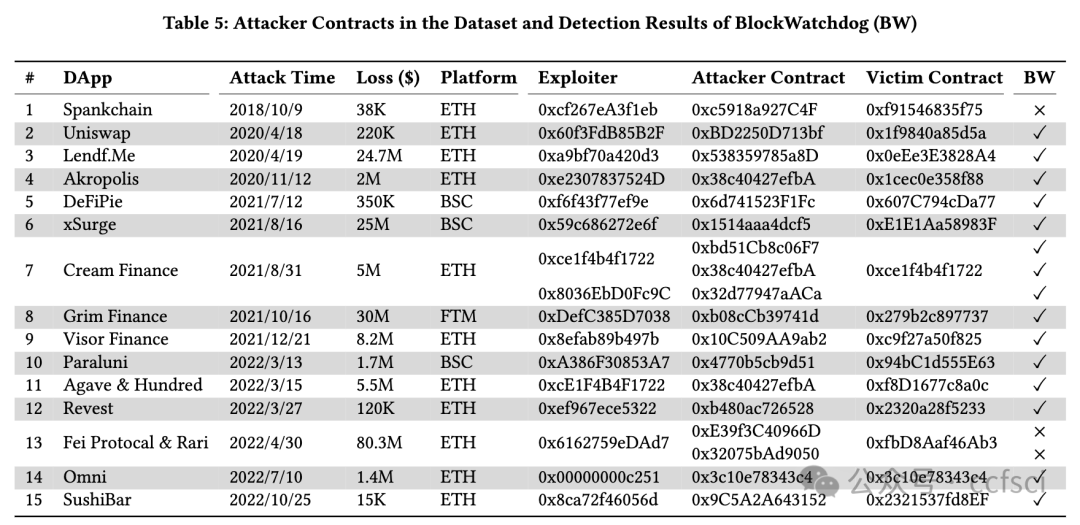
Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639153
6
Title:
Towards Finding Accounting Errors in Smart Contracts
寻找智能合约中的会计错误
Authors:

Key words:
Blockchain, Smart Contract, Accounting Error, Type Checking
区块链、智能合约、会计错误、类型检查
Abstract:
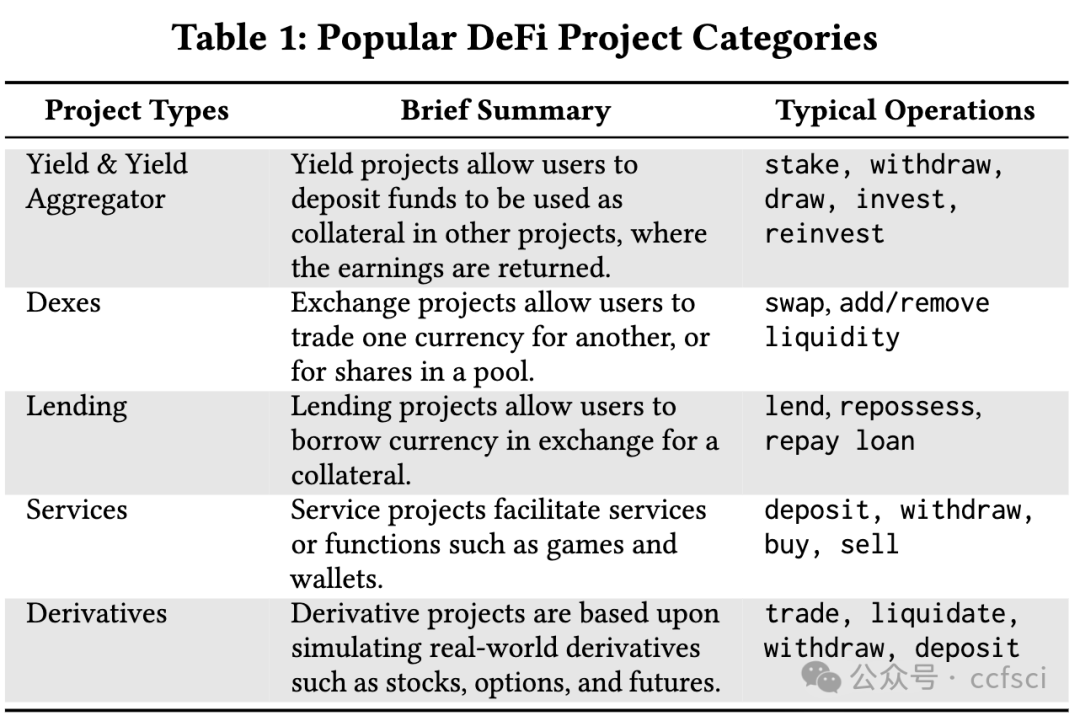
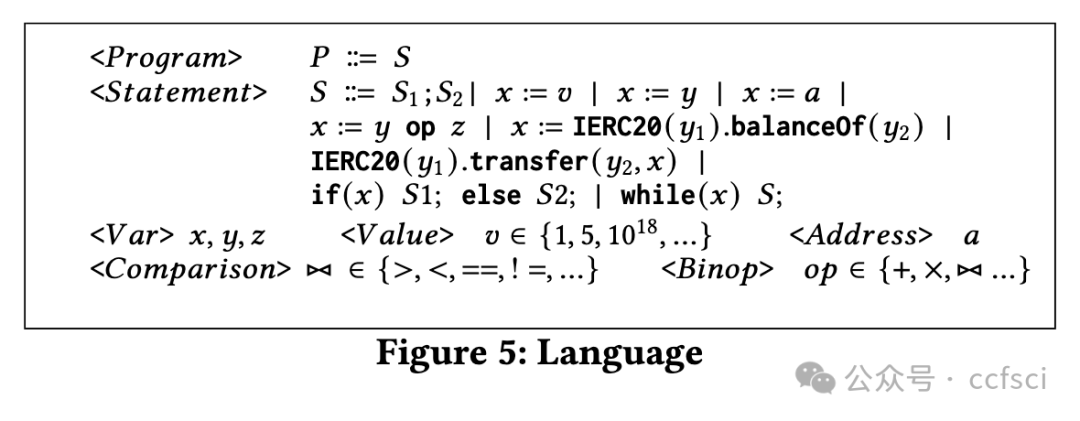
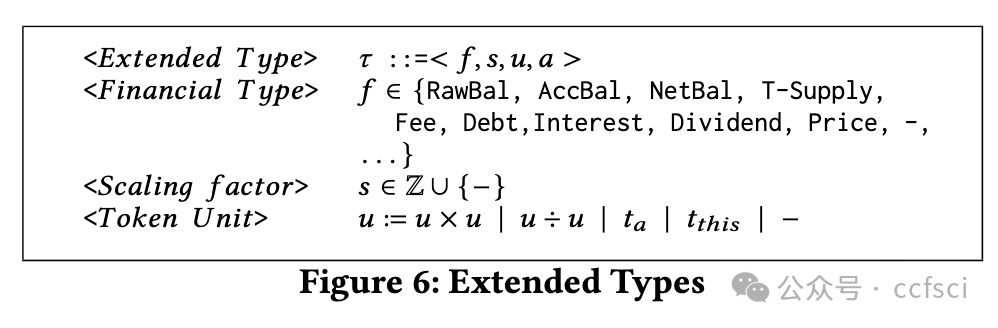
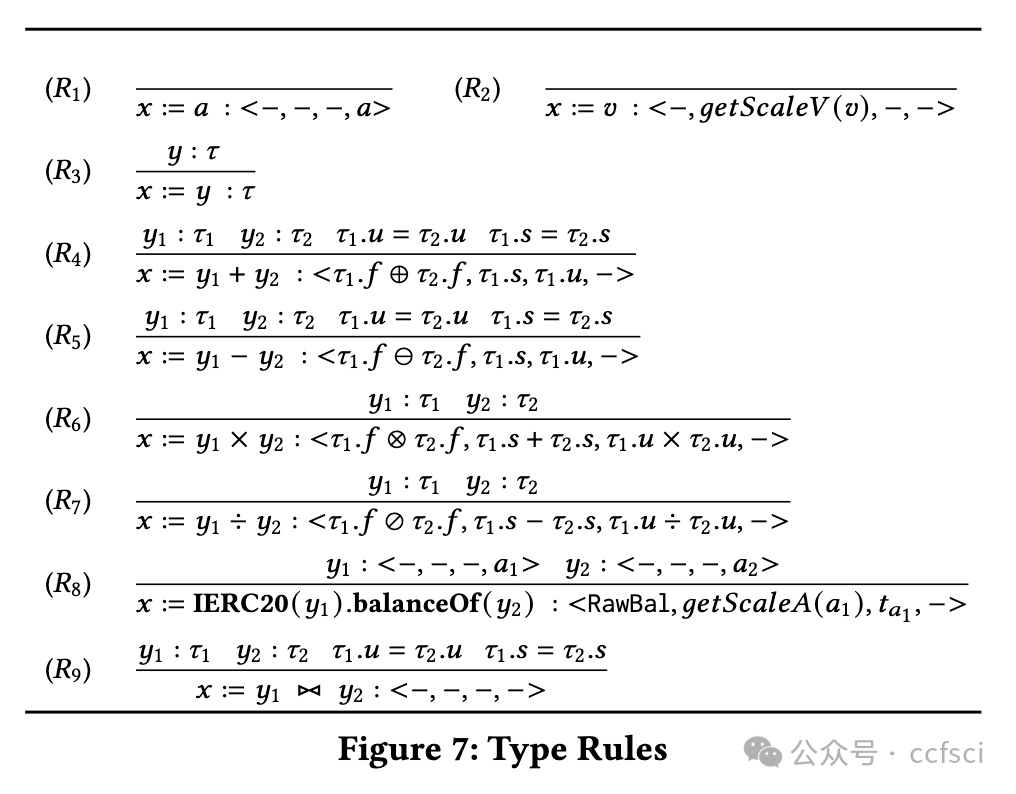
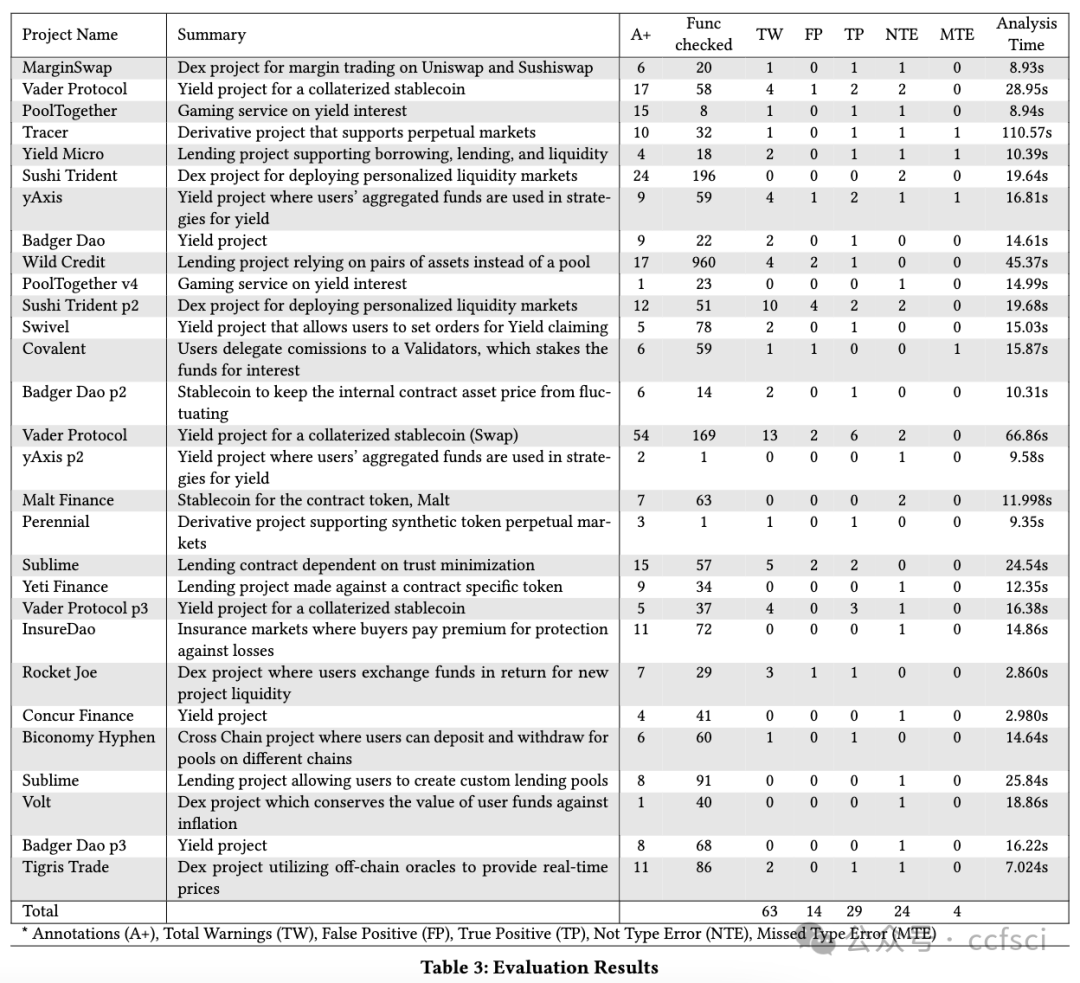
Bugs in smart contracts may have devastating effects as they tend to cause financial loss. According to a recent study, accounting bugs are the most common kind of bugs in smart contracts that are beyond automated tools during pre-deployment auditing. The reason lies in that these bugs are usually in the core business logic and hence contract-specific. They are analogous to functional bugs in traditional software, which are largely beyond automated bug finding tools whose effectiveness hinges on uniform and machine checkable characteristics of bugs. It was also reported that accounting bugs are the second-most difficult to find through manual auditing, due to the need of understanding underlying business models. We observe that a large part of business logic in smart contracts can be modeled by a few primitive operations like those in a bank, such as deposit, withdraw, loan, and pay-off, or by their combinations. The properties of these operations can be clearly defined and checked by an abstract type system that models high-order information such as token units, scaling factors, and financial types. We hence develop a novel type propagation and checking system with the aim of identifying accounting bugs. Our evaluation on a large set of 57 existing accounting bugs in 29 real-world projects shows that 58% of the accounting bugs are type errors. Our system catches 87.9% of these type errors. In addition, applying our technique to auditing a large project in a very recent auditing contest has yielded the identification of 6 zero-day accounting bugs with 4 leading to direct fund loss.
智能合约中的错误可能会造成毁灭性的影响,因为它们往往会造成财务损失。根据最近的一项研究,会计错误是智能合约中最常见的错误类型,在部署前审计期间,这些错误超出了自动化工具的范围。原因在于这些错误通常存在于核心业务逻辑中,因此特定于合约。它们类似于传统软件中的功能性错误,这些错误在很大程度上超出了自动化错误查找工具的范围,而自动化错误查找工具的有效性取决于错误的统一和机器可检查的特征。据报道,由于需要了解底层业务模型,会计错误是通过人工审计发现的第二难的问题。我们观察到,智能合约中的大部分业务逻辑可以通过一些原始操作(如银行中的操作)或它们的组合来建模,例如存款、取款、贷款和还款,或者通过它们的组合来建模。这些操作的属性可以通过抽象类型系统明确定义和检查,该系统对高阶信息(如代币单位、缩放因子和财务类型)进行建模。因此,我们开发了一种新型类型传播和检查系统,旨在识别会计错误。我们对 29 个实际项目中的 57 个现有会计漏洞进行了评估,结果表明 58% 的会计漏洞是类型错误。我们的系统可以捕获 87.9% 的此类错误。此外,在最近的一次审计竞赛中,我们将技术应用于审计一个大型项目,发现了 6 个零日会计漏洞,其中 4 个直接导致资金损失。

Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639128
7
Title:
Improving Smart Contract Security with Contrastive Learning-based Vulnerability Detection
使用基于对比学习的漏洞检测提高智能合约安全性
Authors:
Key words:
Smart contract, Vulnerability detection, Deep learning, Contrastive learning
智能合约、漏洞检测、深度学习、对比学习
Abstract:
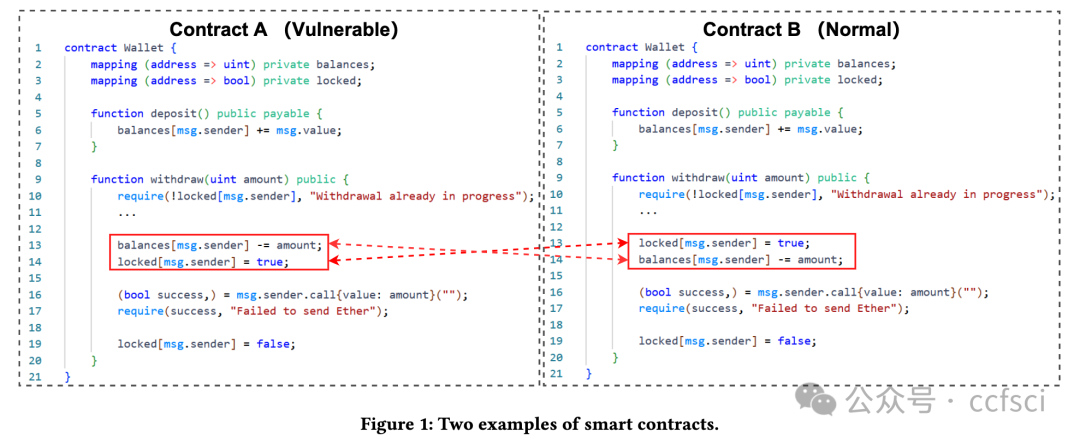
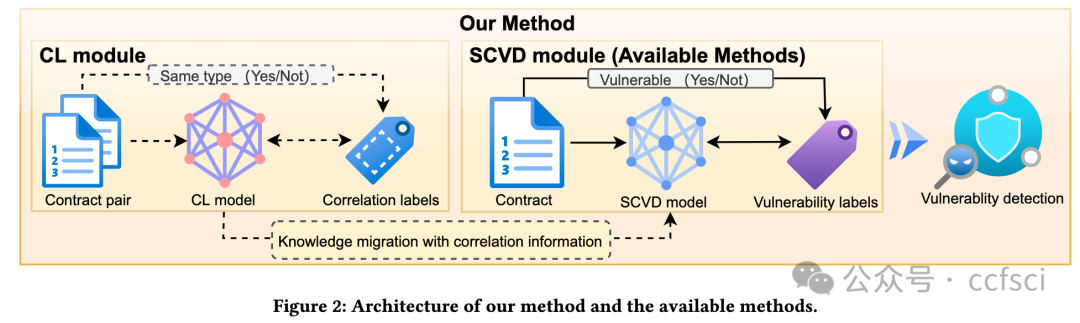
Currently, smart contract vulnerabilities (SCVs) have emerged as a major factor threatening the transaction security of blockchain. Existing state-of-the-art methods rely on deep learning to mitigate this threat. They treat each input contract as an independent entity and feed it into a deep learning model to learn vulnerability patterns by fitting vulnerability labels. It is a pity that they disregard the correlation between contracts, failing to consider the commonalities between contracts of the same type and the differences among contracts of different types. As a result, the performance of these methods falls short of the desired level. To tackle this problem, we propose a novel Contrastive Learning Enhanced Automated Recognition Approach for Smart Contract Vulnerabilities, named Clear. In particular, Clear employs a contrastive learning (CL) model to capture the fine-grained correlation information among contracts and generates correlation labels based on the relationships between contracts to guide the training process of the CL model. Finally, it combines the correlation and the semantic information of the contract to detect SCVs. Through an empirical evaluation of a large-scale real-world dataset of over 40K smart contracts and compare 13 state-of-the-art baseline methods. We show that Clear achieves (1) optimal performance over all baseline methods; (2) 9.73%-39.99% higher F1-score than existing deep learning methods.
当前,智能合约漏洞已成为威胁区块链交易安全的主要因素。现有的先进方法依靠深度学习来缓解这一威胁。他们将每个输入合约视为一个独立的实体,并将其输入到深度学习模型中,通过拟合漏洞标签来学习漏洞模式。遗憾的是,它们忽略了合约之间的相关性,没有考虑同一类型合约之间的共性以及不同类型合约之间的差异。因此,这些方法的性能达不到预期水平。针对这一问题,我们提出了一种新的对比学习增强的智能合约漏洞自动识别方法,称为 Clear。具体而言,Clear 采用对比学习 (CL) 模型来捕获合约之间的细粒度相关性信息,并根据合约之间的关系生成相关性标签来指导 CL 模型的训练过程。最后,它结合相关性和合约的语义信息来检测 SCV。通过对超过 40,000 个智能合约的大规模真实世界数据集进行实证评估,并比较了 13 种最先进的基线方法。我们表明 Clear 实现了 (1) 优于所有基线方法的最佳性能;(2) F1 分数比现有的深度学习方法高 9.73%-39.99%。

Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639173
篇幅有限,下篇文章将继续分享剩余论文

持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends