Python(30):非对称加密算法RSA的使用(openssl生成RSA公私钥对)
1、openssl生成RSA公私钥对
1.1、生成RSA公私钥对命令
[root@loaclhost ~]# openssl
OpenSSL> genrsa -out rsa_private_key.pem 1024
Generating RSA private key, 1024 bit long modulus
..++++++
.....++++++
e is 65537 (0x10001)
OpenSSL> pkcs8 -topk8 -inform PEM -in rsa_private_key.pem -outform pem -nocrypt -out rsa_private_key_8.pem
OpenSSL> rsa -in rsa_private_key_8.pem -pubout -out rsa_public_key.pem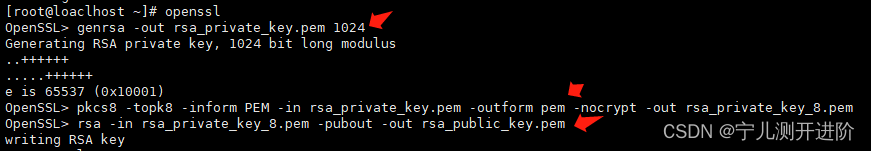
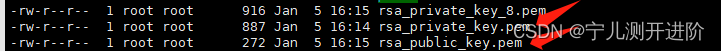
1.2、公钥
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCfNHu9aoeNUTAZH3GCP2CQaSOg
XNx0tImsIaCWBEQK3/fvUx8f17hIOtttCMrrTPWefUdcUxLIZ+xzqeU/eISsz9Ym
kguImd1+bMkGIYiHBKmF5Uww2jGSU738c+AUuRKpixZP+VPekLY+KbOH7NkE2U/L
XGbDeMXeiqQ22UmOSQIDAQAB
-----END PUBLIC KEY-----
1.3、私钥
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQCfNHu9aoeNUTAZH3GCP2CQaSOgXNx0tImsIaCWBEQK3/fvUx8f
17hIOtttCMrrTPWefUdcUxLIZ+xzqeU/eISsz9YmkguImd1+bMkGIYiHBKmF5Uww
2jGSU738c+AUuRKpixZP+VPekLY+KbOH7NkE2U/LXGbDeMXeiqQ22UmOSQIDAQAB
AoGACXx2Fw4+73Oz+vs9pzYhidlJ7yc5V5beUSxbxjSQ3VkFC/SW+S3AZEVlh7Sr
aqPWStBKLT0h9GEE3Mt1xndm6FEVUebboPxDekNU46NnzmF82olzOZbDQuK3LIZT
rKoGMmUD6SlYo9B7DpP3gCYTOb9c6OzHRjcJuHPNWdlyH4UCQQDOrBUupe9vyC4D
iOHIym7dcVj5+O459OzhnXli1WvMhhYpr9QwVC7cRVJk6ZsQgSj+3NmZBx0S0DzC
Ux1fUnOTAkEAxTQZX+M3OrRSIMzUSEI0prZe/B+ZSwXMUpcWu830Zlz0MbhrDSAg
Y67vHE1cAfLIFQOLUWwr+6Fb7hcrhJZYMwJAGB1uL04/XPyvmcv8BHDSdNZH+or4
SRzyEvVL96NNe8TdiymwCZ+ZBCy2i33SkR9xCCP+4+M3mj1gCZCnKbs2LwJBAJ/I
d+reoohZRNY4wKQPqLOPvuSQAdfsycH9k7j1xloOZPnIUEzhQ/0g57LJ54vYmE+W
gJKnj/ehpWgDtAoI+0sCQCXMKPQb2yt2Ca5Ew7R8W2mFo3AyuiYa/FWyeBHZ3x6h
Lqd69roKtGGkB1/rNrPze6/Kqkyjas2urie8cqbzw0A=
-----END RSA PRIVATE KEY-----
2、Python调用RSA加解密
2.1、Python代码
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5 as PKCS1_cipher
import base64
def rsa_encrypt(public_key_str,plain_data):
#pubkey = RSA.import_key(public_key_str)
pubkey = RSA.importKey(public_key_str) #读入公钥
rsa = PKCS1_cipher.new(pubkey) #生成对象
## 通过生成的对象加密明文,注意,在python3中加密的数据必须是bytes类型的数据,不能是str类型的数据
cipher_text = base64.b64encode(rsa.encrypt(bytes(plain_data.encode('utf-8'))))
cipher_data=cipher_text.decode('utf-8')
return cipher_data
def rsa_decrypt(private_key_str, cipher_data):
pri_key = RSA.importKey(private_key_str) #导入私钥
cipher = PKCS1_cipher.new(pri_key) #生成对象
# 将密文解密成明文,返回的是一个bytes类型数据,需要自己转换成str
plain = cipher.decrypt(base64.b64decode(cipher_data.encode("utf8")), 0)
plain_data = plain.decode('utf-8')
return plain_data
public_key ="-----BEGIN PUBLIC KEY-----\n"+"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCfNHu9aoeNUTAZH3GCP2CQaSOgXNx0tImsIaCWBEQK3/fvUx8f17hIOtttCMrrTPWefUdcUxLIZ+xzqeU/eISsz9YmkguImd1+bMkGIYiHBKmF5Uww2jGSU738c+AUuRKpixZP+VPekLY+KbOH7NkE2U/LXGbDeMXeiqQ22UmOSQIDAQAB"+"\n-----END PUBLIC KEY-----\n"
plain_text="Hello World!"
cipher_text =rsa_encrypt(public_key, plain_text)
print(cipher_text)
private_key ="-----BEGIN RSA PRIVATE KEY-----\n"+"MIICXAIBAAKBgQCfNHu9aoeNUTAZH3GCP2CQaSOgXNx0tImsIaCWBEQK3/fvUx8f17hIOtttCMrrTPWefUdcUxLIZ+xzqeU/eISsz9YmkguImd1+bMkGIYiHBKmF5Uww2jGSU738c+AUuRKpixZP+VPekLY+KbOH7NkE2U/LXGbDeMXeiqQ22UmOSQIDAQABAoGACXx2Fw4+73Oz+vs9pzYhidlJ7yc5V5beUSxbxjSQ3VkFC/SW+S3AZEVlh7SraqPWStBKLT0h9GEE3Mt1xndm6FEVUebboPxDekNU46NnzmF82olzOZbDQuK3LIZTrKoGMmUD6SlYo9B7DpP3gCYTOb9c6OzHRjcJuHPNWdlyH4UCQQDOrBUupe9vyC4DiOHIym7dcVj5+O459OzhnXli1WvMhhYpr9QwVC7cRVJk6ZsQgSj+3NmZBx0S0DzCUx1fUnOTAkEAxTQZX+M3OrRSIMzUSEI0prZe/B+ZSwXMUpcWu830Zlz0MbhrDSAgY67vHE1cAfLIFQOLUWwr+6Fb7hcrhJZYMwJAGB1uL04/XPyvmcv8BHDSdNZH+or4SRzyEvVL96NNe8TdiymwCZ+ZBCy2i33SkR9xCCP+4+M3mj1gCZCnKbs2LwJBAJ/Id+reoohZRNY4wKQPqLOPvuSQAdfsycH9k7j1xloOZPnIUEzhQ/0g57LJ54vYmE+WgJKnj/ehpWgDtAoI+0sCQCXMKPQb2yt2Ca5Ew7R8W2mFo3AyuiYa/FWyeBHZ3x6hLqd69roKtGGkB1/rNrPze6/Kqkyjas2urie8cqbzw0A="+"\n-----END RSA PRIVATE KEY-----\n"
decrypt_data =rsa_decrypt(private_key,cipher_text)
print(decrypt_data)2.2、执行结果
"D:\Program Files\Python386\python.exe" D:/python_project/apiTest/venv/src/common/common.py
MNkriQhmq7Y1L4fGQ5zdAuoxpvRJHrBIRjRZDhTebxTVPoJ1UJqIGekZVi36W+lJkd57az9tj3HpRZS2WLd52CvKpnCyv5yhQcxduCPMrekINwz1mUj1ZaNVFiRPdE6aj5P+jVPPZWkd8GNu346PU6pQb4mq49RejfevnN8xT8E=
Hello World!
Process finished with exit code 0
参考:https://blog.csdn.net/qq_62789540/article/details/124400910



























![[SwiftUI]工程最低适配iOS13](https://img-blog.csdnimg.cn/direct/a90dd7f61c2740aaac7ce95fb680d91b.png)