Conference:Network and Distributed System Security Symposium (NDSS)
CCF level:CCF A
Categories:network and information security
Year:2024
Number of acceptances:7
1
Title:
Front-running Attack in Sharded Blockchains and Fair Cross-shard Consensus
分片区块链中的抢先攻击和公平的跨分片共识
Authors:
Jianting Zhang (Purdue University), Wuhui Chen (Sun Yat-sen University), Sifu Luo (Sun Yat-sen University), Tiantian Gong (Purdue University), Zicong Hong (The Hong Kong Polytechnic University), Aniket Kate (Purdue University)
Key words:
None
Abstract:
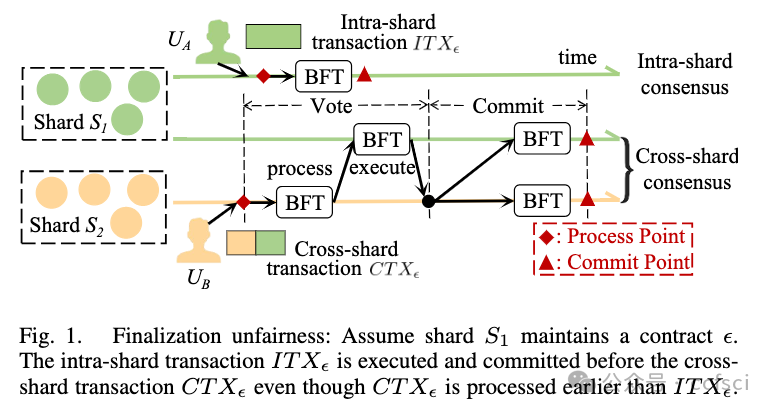
Sharding is a prominent technique for scaling blockchains. By dividing the network into smaller components known as shards, a sharded blockchain can process transactions in parallel without introducing inconsistencies through the coordination of intra-shard and cross-shard consensus protocols. However, we observe a critical security issue with sharded systems: transaction ordering manipulations can occur when coordinating intra-shard and cross-shard consensus protocols, leaving the system vulnerable to attack. Specifically, we identify a novel security issue known as finalization fairness, which can be exploited through a front-running attack. This attack allows an attacker to manipulate the execution order of transactions, even if the victim's transaction has already been processed and added to the blockchain by a fair intra-shard consensus.
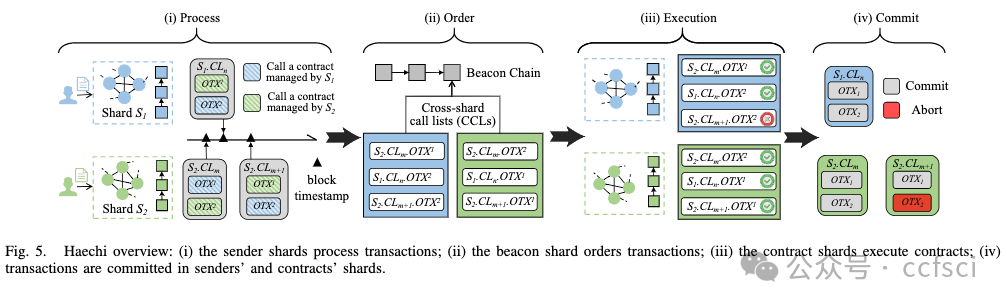
To address the issue, we offer Haechi, a novel cross-shard protocol that is immune to front-running attacks. Haechi introduces an ordering phase between transaction processing and execution, ensuring that the execution order of transactions is the same as the processing order and achieving finalization fairness. To accommodate different consensus speeds among shards, Haechi incorporates a finalization fairness algorithm to achieve a globally fair order with minimal performance loss. By providing a global order, Haechi ensures strong consistency among shards, enabling better parallelism in handling conflicting transactions across shards. These features make Haechi a promising solution for supporting popular smart contracts in the real world. To evaluate Haechi's performance and effectiveness in preventing the attack, we implemented the protocol using Tendermint and conducted extensive experiments on a geo-distributed AWS environment. Our results demonstrate that Haechi can effectively prevent the presented front-running attack with little performance sacrifice compared to existing cross-shard consensus protocols.
分片是扩展区块链的一项重要技术。通过将网络划分为更小的组件(称为分片),分片区块链可以并行处理交易,通过分片内和跨分片共识协议的协作不会引入不一致。然而,我们观察到分片系统存在一个关键的安全问题:协调分片内和跨分片共识协议时可能会发生交易排序操作,从而使系统容易受到攻击。具体来说,我们发现了一个称为最终公平性的新安全问题,可以通过抢先交易攻击来利用该问题。这种攻击允许攻击者操纵交易的执行顺序,即使受害者的交易已经通过公平的分片内共识处理并添加到区块链中。
为了解决这个问题,我们提供了 Haechi,一种新颖的跨分片协议,可以免受抢先交易攻击。Haechi在交易处理和执行之间引入了排序阶段,保证交易的执行顺序与处理顺序相同,实现最终公平。为了适应分片之间不同的共识速度,Haechi 采用了最终公平算法,以最小的性能损失实现全局公平秩序。通过提供全局顺序,Haechi 确保了分片之间的强一致性,从而在处理跨分片的冲突事务时实现更好的并行性。这些功能使 Haechi 成为支持现实世界中流行的智能合约的有前途的解决方案。为了评估 Haechi 在防止攻击方面的性能和有效性,我们使用 Tendermint 实施该协议,并在地理分布式 AWS 环境中进行了广泛的实验。我们的结果表明,与现有的跨分片共识协议相比,Haechi 可以有效防止所提出的抢先交易攻击,而几乎没有牺牲性能。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-197-paper.pdf
2
Title:
A Two-Layer Blockchain Sharding Protocol Leveraging Safety and Liveness for Enhanced Performance
利用安全性和活性来增强性能的两层区块链分片协议
Authors:
Yibin Xu (University of Copenhagen), Jingyi Zheng (University of Copenhagen), Boris Düdder (University of Copenhagen), Tijs Slaats (University of Copenhagen), Yongluan Zhou (University of Copenhagen)
Key words:
None
Abstract:
Sharding is a critical technique that enhances the scalability of blockchain technology. However, existing protocols often assume adversarial nodes in a general term without considering the different types of attacks, which limits transaction throughput at runtime because attacks on liveness could be mitigated. There have been attempts to increase transaction throughput by separately handling the attacks; however, they have security vulnerabilities. This paper introduces Reticulum, a novel sharding protocol that overcomes these limitations and achieves enhanced scalability in a blockchain network without security vulnerabilities.
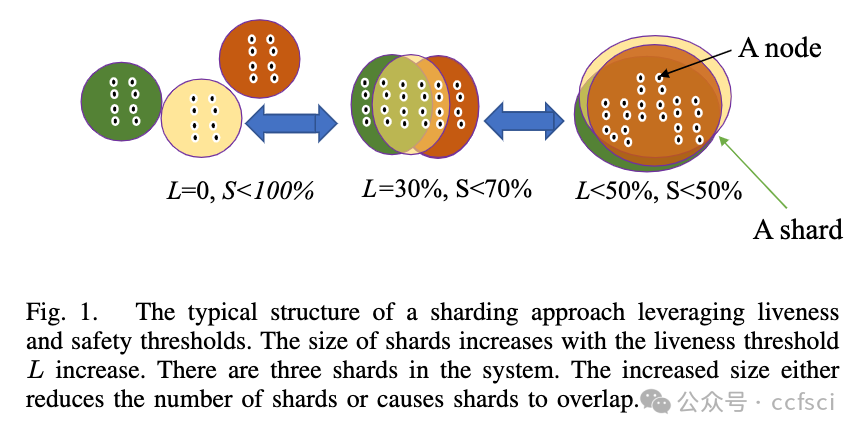
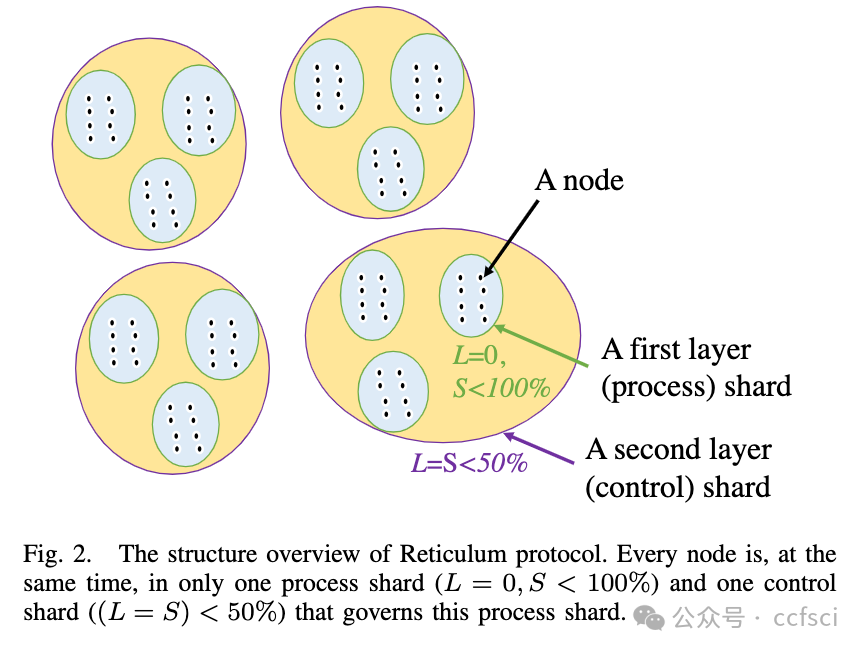
Reticulum employs a two-phase design that dynamically adjusts transaction throughput based on runtime adversarial attacks on either or both liveness and safety. It consists of ‘control’ and ‘process’ shards in two layers corresponding to the two phases. Process shards are subsets of control shards, with each process shard expected to contain at least one honest node with high confidence. Conversely, control shards are expected to have a majority of honest nodes with high confidence. Reticulum leverages unanimous voting in the first phase to involve fewer nodes in accepting/rejecting a block, allowing more parallel process shards. The control shard finalizes the decision made in the first phase and serves as a lifeline to resolve disputes when they surface.
Experiments demonstrate that the unique design of Reticulum empowers high transaction throughput and robustness in the face of different types of attacks in the network, making it superior to existing sharding protocols for blockchain networks.
分片是增强区块链技术可扩展性的关键技术。然而,现有协议通常笼统地假设对抗性节点,而不考虑不同类型的攻击,这限制了运行时的事务吞吐量,因为可以减轻对活性的攻击。已经尝试通过单独处理攻击来提高交易吞吐量;然而,它们存在安全漏洞。本文介绍了 Reticulum,一种新颖的分片协议,它克服了这些限制,并在没有安全漏洞的情况下在区块链网络中实现了增强的可扩展性。
Reticulum 采用两阶段设计,根据对活性和安全性中的一个或两个的运行时对抗性攻击动态调整交易吞吐量。它由对应两个阶段的两层“控制”和“过程”分片组成。 过程分片是控制分片的子集,每个过程分片预计包含至少一个具有高置信度的诚实节点。相反,控制分片预计拥有大多数具有高置信度的诚实节点。Reticulum 在第一阶段利用一致投票来减少接受/拒绝区块的节点,从而允许更多的并行进程分片。控制分片最终确定第一阶段做出的决定,并作为解决争议出现的生命线。
实验表明,Reticulum 的独特设计在面对网络中不同类型的攻击时具有高交易吞吐量和鲁棒性,使其优于现有的区块链网络分片协议。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-6-paper.pdf
3
Title:
Proof of Backhaul: Trustfree Measurement of Broadband Bandwidth
回程证明:宽带带宽的无信任测量
Authors:
Peiyao Sheng (Kaleidoscope Blockchain Inc.), Nikita Yadav (Indian Institute of Science), Vishal Sevani (Kaleidoscope Blockchain Inc.), Arun Babu (Kaleidoscope Blockchain Inc.), Anand Svr (Kaleidoscope Blockchain Inc.), Himanshu Tyagi (Indian Institute of Science), Pramod Viswanath (Kaleidoscope Blockchain Inc.)
Key words:
None
Abstract:
Recent years have seen the emergence of decentralized wireless networks consisting of nodes hosted by many individuals and small enterprises, reawakening the decades-old dream of open networking. These networks have been deployed in an organic, distributed manner and are driven by new economic models resting on performance-based incentives. A critical requirement for the incentives to scale is the ability to prove network performance in a decentralized ``trustfree" manner, i.e., a Byzantine fault tolerant network telemetry system.
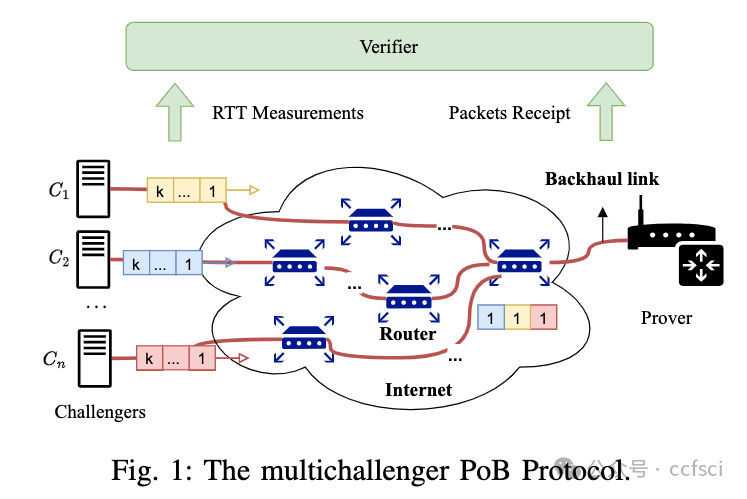
In this paper, we present a Proof of Backhaul (PoB) protocol which measures the bandwidth of the (broadband) backhaul link of a wireless access point, termed prover, in a decentralized and trustfree manner. In particular, our proposed protocol is the first to satisfy the following two properties:
(1) Trustfree. Bandwidth measurement is secure against Byzantine attacks by collusion of challenge servers and the prover.
(2) Open. The barrier-to-entry for being a challenge server is low; there is no requirement of having a low latency and high throughput path to the measured link.
At a high-level, our protocol aggregates the challenge traffic from multiple challenge servers and uses cryptographic primitives to ensure that a subset of challengers or, even challengers and provers, cannot maliciously modify results in their favor. A formal security model allows us to establish guarantees of accurate bandwidth measurement as a function of the maximum fraction of malicious actors.
We implement our protocol with challengers spread across geographical locations and release the code~cite{multichallenger-pob}. Our evaluation shows that our PoB protocol can verify backhaul bandwidth of up to 1000 Mbps with less than 10% error using measurements lasting only 100 ms. The measurement accuracy is not affected in the presence of corrupted challengers. Importantly, the basic verification protocol lends itself to a minor modification that can measure available bandwidth even in the presence of cross-traffic.
Finally, the security guarantees of our PoB protocol output are naturally composable with ``commitments" on blockchain ledgers, which are commonly used for decentralized networks.
近年来,由许多个人和小型企业托管的节点组成的去中心化无线网络的出现,重新唤醒了数十年来开放网络的梦想。这些网络以有机、分布式的方式部署,并由基于绩效激励的新经济模型驱动。规模激励的一个关键要求是能够以去中心化的“无信任”方式证明网络性能,即拜占庭容错网络遥测系统。
在本文中,我们提出了一种回程证明(PoB)协议,它以去中心化和免信任的方式测量无线接入点(宽带)回程链路的带宽,称为证明者。特别是,我们提出的协议是第一个满足以下两个属性的协议:
(1) 无需信任。通过挑战服务器和证明者的串通,带宽测量可以抵御拜占庭攻击。
(2)开放。成为挑战服务器的门槛较低;不要求被测链路具有低延迟和高吞吐量的路径。
在高层,我们的协议聚合来自多个挑战服务器的挑战流量,并使用加密原语来确保挑战者的子集,甚至挑战者和证明者,不能恶意修改结果以利于他们。正式的安全模型使我们能够根据恶意行为者的最大比例来保证准确的带宽测量。
我们与分布在各个地理位置的挑战者一起实施我们的协议,并发布代码~cite{multichallenger-pob}。我们的评估表明,我们的 PoB 协议可以使用仅持续 100 毫秒的测量来验证高达 1000 Mbps 的回程带宽,且误差低于 10%。在存在损坏的挑战者的情况下,测量精度不会受到影响。重要的是,基本验证协议可以进行微小的修改,即使存在交叉流量也可以测量可用带宽。
最后,我们的 PoB 协议输出的安全保证自然可以与区块链分类账上的“承诺”组合,这通常用于去中心化网络。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-764-paper.pdf
4
Title:
Security-Performance Tradeoff in DAG-based Proof-of-Work Blockchain Protocols
基于 DAG 的工作量证明区块链协议的安全性与性能权衡
Authors:
Shichen Wu (1. School of Cyber Science and Technology, Shandong University 2. Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education), Puwen Wei (1. School of Cyber Science and Technology, Shandong University 2. Quancheng Laboratory 3. Key Laboratory of Cryptologic Technology and Information Security, Ministry of Education), Ren Zhang (Cryptape Co. Ltd. and…
Key words:
None
Abstract:
Proof-of-work (PoW) blockchain protocols based on directed acyclic graphs (DAGs) have demonstrated superior transaction confirmation performance compared to their chain-based predecessors. However, it is uncertain whether their security deteriorates in high-throughput settings similar to their predecessors, because their acceptance of simultaneous blocks and complex block dependencies presents challenges for rigorous security analysis.
We address these challenges by analyzing DAG-based protocols via a congestible blockchain model (CBM), a general model that allows case-by-case upper bounds on the block propagation delay, rather than a uniform upper bound as in most previous analyses. CBM allows us to capture two key phenomena of high-throughput settings: (1) simultaneous blocks increase each other's propagation delay, and (2) a block can be processed only after receiving all the blocks it refers to. We further devise a reasonable adversarial block propagation strategy in CBM, called the late-predecessor attack, which exploits block dependencies to delay the processing of honest blocks. We then evaluate the security and performance of Prism and OHIE, two DAG-based protocols that aim to break the security-performance tradeoff, in the presence of an attacker capable of launching the late predecessor attack. Our results show that these protocols suffer from reduced security and extended latency in high-throughput settings similar to their chain-based predecessors.
与基于链的前辈相比,基于有向无环图 (DAG) 的工作量证明 (PoW) 区块链协议已展现出卓越的交易确认性能。然而,不确定它们的安全性是否会像其前身那样在高吞吐量设置中恶化,因为它们对同时块和复杂块依赖性的接受给严格的安全分析带来了挑战。
我们通过拥塞区块链模型(CBM)分析基于 DAG 的协议来解决这些挑战,CBM 是一种通用模型,允许根据具体情况确定块传播延迟的上限,而不是像之前大多数分析那样采用统一的上限。CBM 使我们能够捕获高吞吐量设置的两个关键现象:(1)同时出现的块会增加彼此的传播延迟,(2)一个块只有在接收到它所引用的所有块后才能被处理。我们进一步在 CBM 中设计了一种合理的对抗性区块传播策略,称为后前驱攻击,它利用区块依赖性来延迟诚实区块的处理。然后,我们评估 Prism 和 OHIE(两种基于 DAG 的协议)的安全性和性能,旨在在存在能够发起后期前驱攻击的攻击者的情况下打破安全性与性能的权衡。我们的结果表明,与基于链的前身类似,这些协议在高吞吐量设置中面临安全性降低和延迟延长的问题。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-685-paper.pdf
5
Title:
Abusing the Ethereum Smart Contract Verification Services for Fun and Profit
滥用以太坊智能合约验证服务来获取乐趣和利润
Authors:
Pengxiang Ma (Huazhong University of Science and Technology), Ningyu He (Peking University), Yuhua Huang (Huazhong University of Science and Technology), Haoyu Wang (Huazhong University of Science and Technology), Xiapu Luo (The Hong Kong Polytechnic University)
Key words:
permissioned blockchains, throughput, latency
许可区块链、吞吐量、延迟
Abstract:
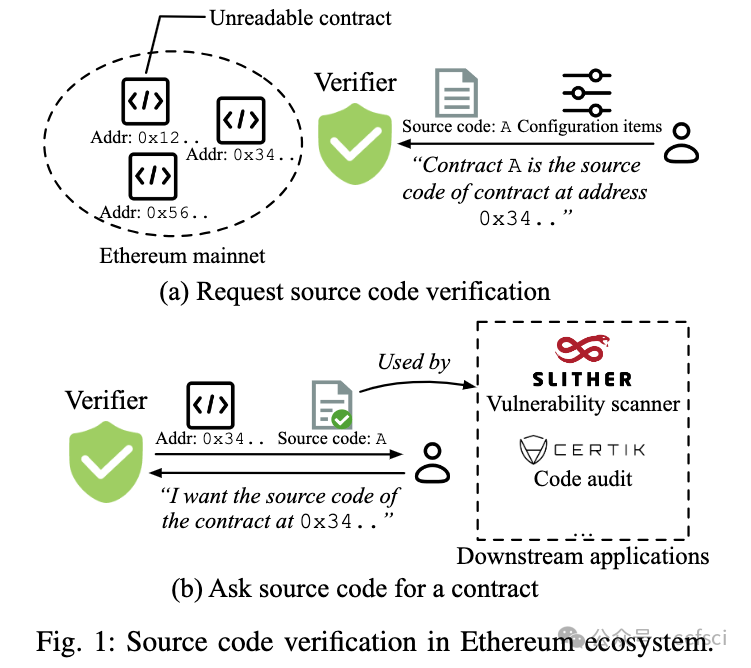
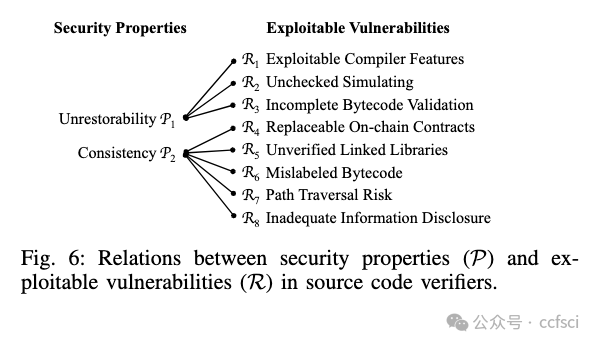
Smart contracts play a vital role in the Ethereum ecosystem. Due to the prevalence of kinds of security issues in smart contracts, the smart contract verification is urgently needed, which is the process of matching a smart contract’s source code to its on-chain bytecode for gaining mutual trust between smart contract developers and users. Although smart contract verification services are embedded in both popular Ethereum browsers (e.g., Etherscan and Blockscout) and official platforms (i.e., Sourcify), and gain great popularity in the ecosystem, their security and trustworthiness remain unclear. To fill the void, we present the first comprehensive security analysis of smart contract verification services in the wild. By diving into the detailed workflow of existing verifiers, we have summarized the key security properties that should be met, and observed eight types of vulnerabilities that can break the verification. Further, we propose a series of detection and exploitation methods to reveal the presence of vulnerabilities in the most popular services, and uncover 19 exploitable vulnerabilities in total. All the studied smart contract verification services can be abused to help spread malicious smart contracts, and we have already observed the presence of using this kind of tricks for scamming by attackers. It is hence urgent for our community to take actions to detect and mitigate security issues related to smart contract verification, a key component of the Ethereum smart contract ecosystem.
智能合约在以太坊生态系统中发挥着至关重要的作用。由于智能合约中各种安全问题的普遍存在,迫切需要进行智能合约验证,即将智能合约的源代码与其链上字节码进行匹配,以获得智能合约开发者和用户之间的相互信任的过程。尽管智能合约验证服务已嵌入流行的以太坊浏览器(例如 Etherscan 和 Blockscout)和官方平台(例如 Sourcify)中,并在生态系统中广受欢迎,但其安全性和可信度仍不清楚。为了填补这一空白,我们首次对智能合约验证服务进行了全面的安全分析。通过深入研究现有验证器的详细工作流程,我们总结了应满足的关键安全属性,并观察到了八种可能破坏验证的漏洞。此外,我们提出了一系列检测和利用方法来揭示最流行的服务中是否存在漏洞,总共发现了 19 个可利用的漏洞。所有研究过的智能合约验证服务都可以被滥用来帮助传播恶意智能合约,并且我们已经观察到攻击者使用此类技巧进行诈骗的情况。因此,我们的社区迫切需要采取行动来检测和减轻与智能合约验证相关的安全问题,智能合约验证是以太坊智能合约生态系统的关键组成部分。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-992-paper.pdf
6
Title:
Separation is Good: A Faster Order-Fairness Byzantine Consensus
分离是好事:更快的排序公平拜占庭共识
Authors:
Ke Mu (Southern University of Science and Technology, China), Bo Yin (Changsha University of Science and Technology, China), Alia Asheralieva (Loughborough University, UK), Xuetao Wei (Southern University of Science and Technology, China & Guangdong Provincial Key Laboratory of Brain-inspired Intelligent Computation, SUSTech, China)
Key words:
None
Abstract:
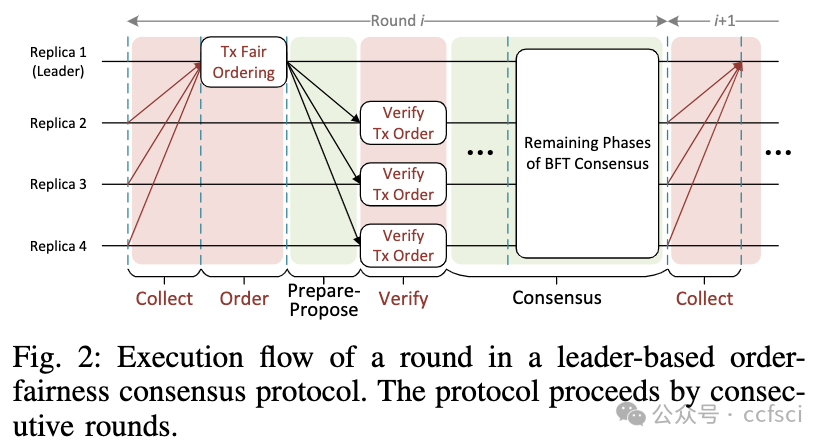
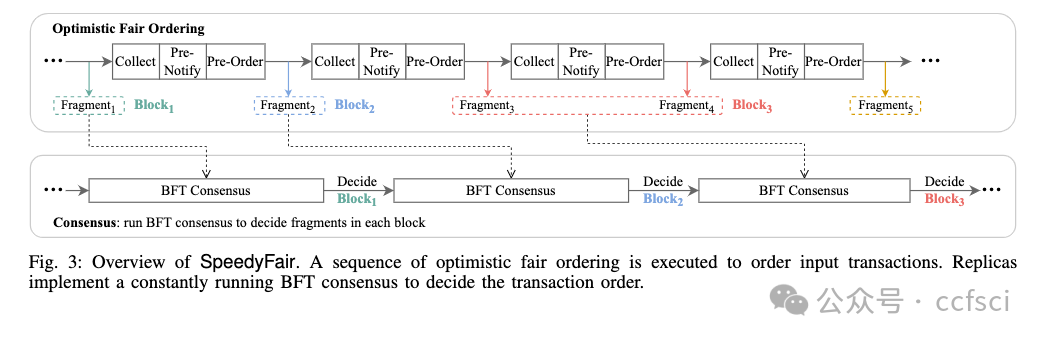
Order-fairness has been introduced recently as a new property for Byzantine Fault-Tolerant (BFT) consensus protocol to prevent unilaterally deciding the final order of transactions, which allows mitigating the threat of adversarial transaction order manipulation attacks (e.g., front-running) in blockchain networks and decentralized finance (DeFi). However, existing leader-based order-fairness protocols (which do not rely on synchronized clocks) still suffer from poor performance since they strongly couple fair ordering with consensus processes. In this paper, we propose SpeedyFair, a high-performance order-fairness consensus protocol, which is motivated by our insight that the ordering of transactions does not rely on the execution results of transactions in previous proposals (after consensus). SpeedyFair achieves its efficiency through a decoupled design that performs fair ordering individually and consecutively, separating from consensus. In addition, by decoupling fair ordering from consensus, SpeedyFair enables parallelizing the order/verify mode that was originally executed serially in the consensus process, which further speeds up the performance. We implement a prototype of SpeedyFair on the top of the Hotstuff protocol. Extensive experimental results demonstrate that SpeedyFair significantly outperforms the state-of-the-art order-fairness protocol (i.e., Themis), which achieves a throughput of 1.5×-2.45× greater than Themis while reducing latency by 35%-59%.
最近引入了排序公平作为拜占庭容错(BFT)共识协议的新属性,以防止单方面决定交易的最终顺序,从而减轻对抗性交易顺序操纵攻击(例如抢先交易)的威胁区块链网络和去中心化金融(DeFi)。然而,现有的基于领导者的排序公平协议(不依赖于同步时钟)仍然存在性能不佳的问题,因为它们将公平排序与共识过程紧密结合在一起。在本文中,我们提出了 SpeedyFair,一种高性能的排序公平共识协议,其动机是我们认为交易的排序不依赖于先前提案(共识后)中交易的执行结果。SpeedyFair 通过解耦设计实现其效率,该设计独立且连续地执行公平排序,与共识分离。此外,通过将公平排序与共识解耦,SpeedyFair能够将原本在共识过程中串行执行的排序/验证模式并行化,从而进一步加快性能。我们在 Hotstuff 协议之上实现了 SpeedyFair 的原型。大量的实验结果表明,SpeedyFair 显着优于最先进的订单公平协议(即 Themis),其吞吐量比 Themis 高 1.5×-2.45×,同时延迟减少了 35%-59%。
Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/2024-693-paper.pdf
7
Title:
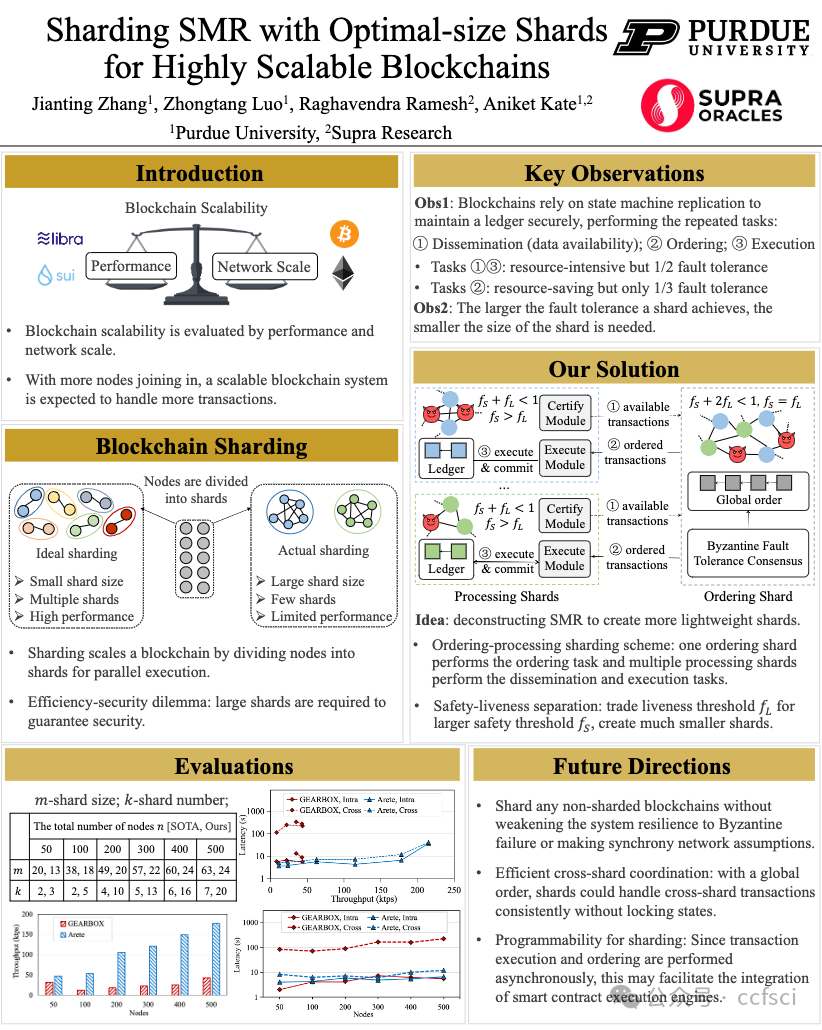
Poster: Sharding SMR with Optimal-size Shards for Highly Scalable Blockchains
海报:使用最佳大小的分片对 SMR 进行分片以实现高度可扩展的区块链
Authors:

Pdf link:
https://www.ndss-symposium.org/wp-content/uploads/ndss24-posters-25.pdf

关注我们,持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends