目录
2.Client1访问FTP服务器:client1截图,会话表截图
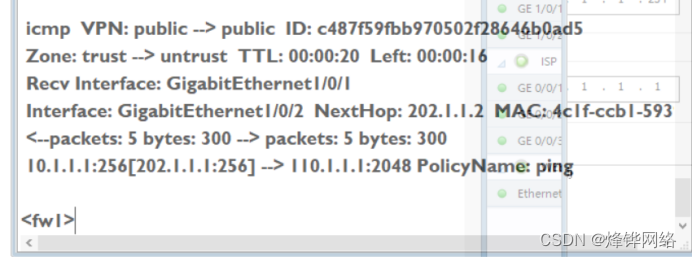
4.Client1访问client2,ping截图,会话表截图
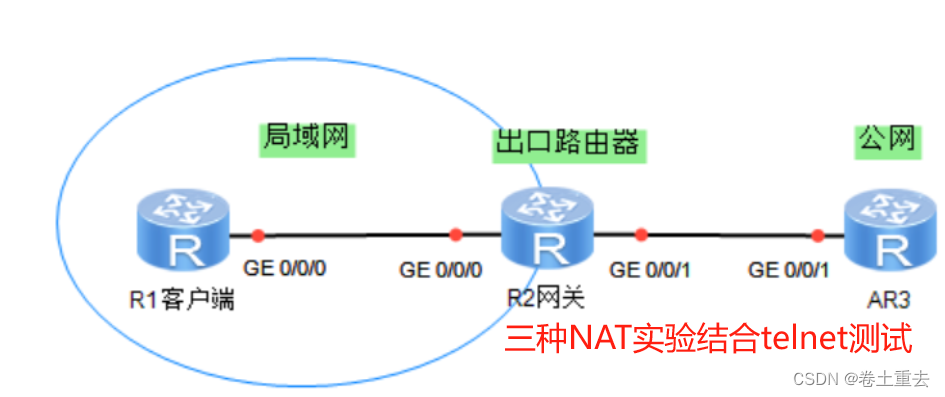
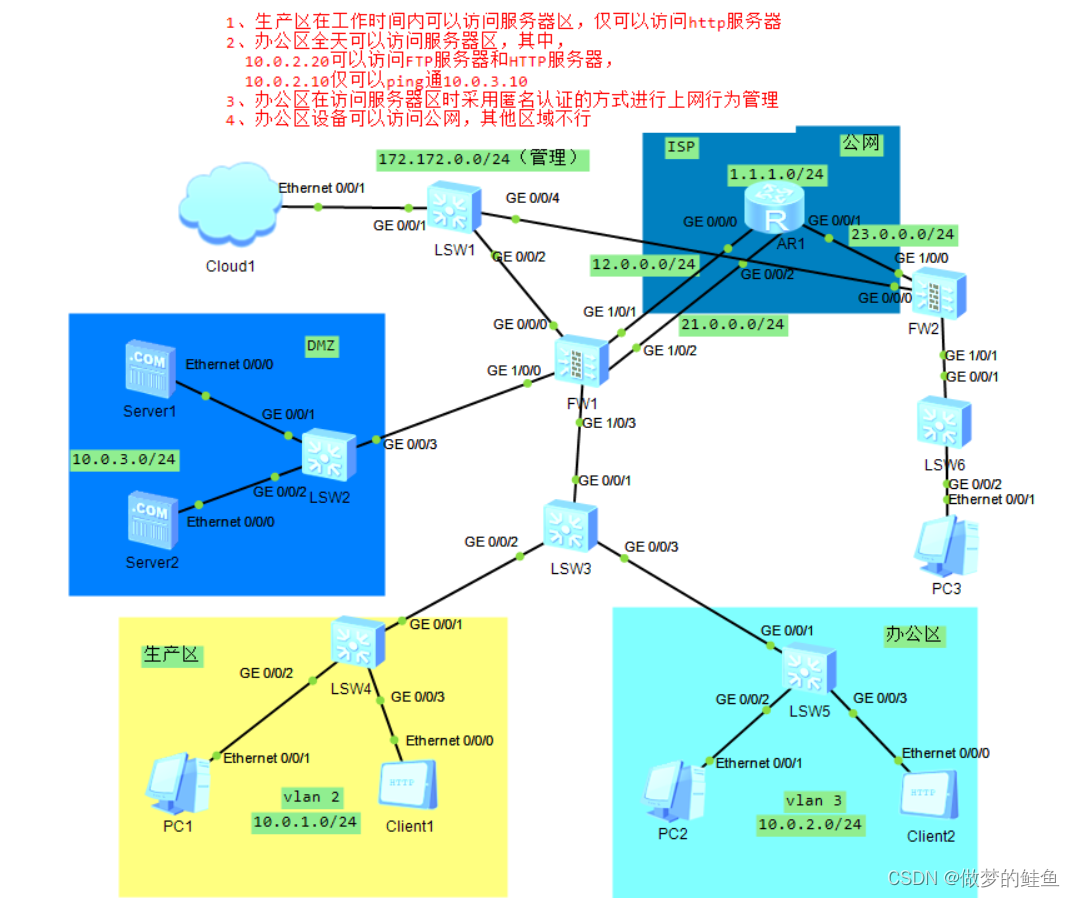
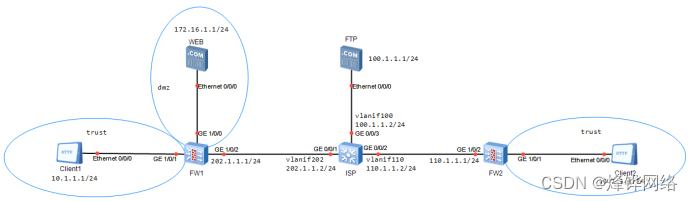
一.实验要求
1. WEB服务器对外的IP地址为202.1.1.100
2. 所有客户端都可通过公网IP访问WEB服务器
3. 所有客户端访问FTP服务器
3.1 client1 使用NAPT方式转换地址,地址池:202.1.1.10
3.2 client2 使用Easy-ip方式转换地址
4. 实现client互访
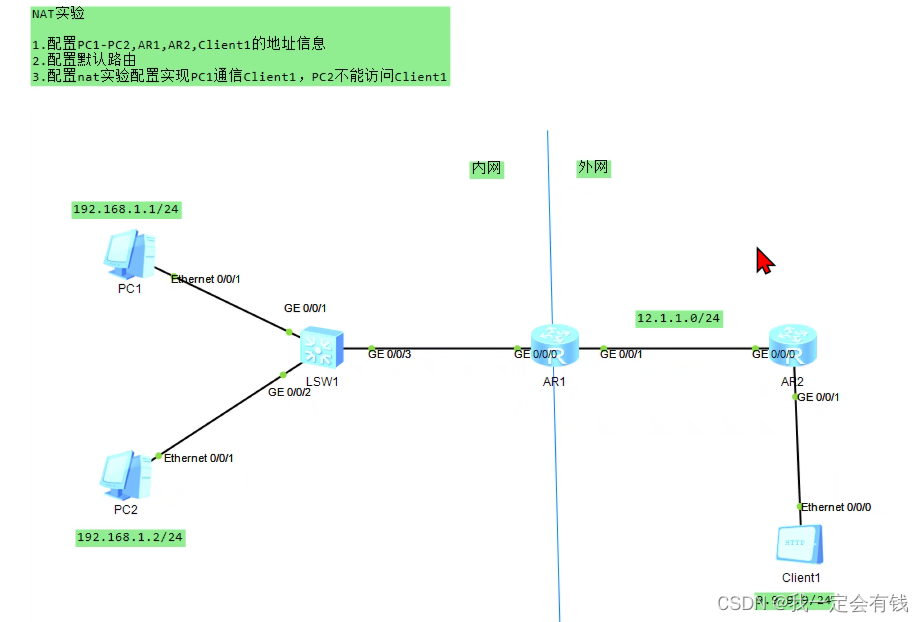
二.配置
1.设备接口ip配置
配置设备接口ip地址
配置防火墙FW1
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 172.16.1.254 255.255.255.0
interface GigabitEthernet1/0/2
undo shutdown
ip address 202.1.1.1 255.255.255.0
interface GigabitEthernet1/0/2
undo shutdown
ip address 202.1.1.1 255.255.255.0
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.254 255.255.255.0配置防火墙二
interface GigabitEthernet1/0/2
undo shutdown
ip address 110.1.1.1 255.255.255.0
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.254 255.255.255.0配置isp
vlan batch 202 110 100
inter vlanif202
ip add 202.1.1.2 24
inter vlanif100
ip add 100.1.1.2 24
inter vlanif110
ip add 110.1.1.2 242.配置防火墙安全区域
FW1配置
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/0FW2配置
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/1
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/2
#
firewall zone dmz
set priority 503.配置路由
这里在FW1配置ospf路由,这里由于ospf在防火墙上的配置,如果不配置安全策略让ospf能从local区域发送ospf到其他区域,ospf会无法运行,这里在端口配置成p2p可以解决问题。
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 202.1.1.0 0.0.0.255
interface GigabitEthernet1/0/2
undo shutdown
ip address 202.1.1.1 255.255.255.0
ospf network-type p2p在fw2配置ospf路由
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 110.1.1.0 0.0.0.255
interface GigabitEthernet1/0/2
undo shutdown
ip address 202.1.1.1 255.255.255.0
ospf network-type p2p在ISP设备配置ospf路由
ospf 1 router-id 10.10.10.10
area 0.0.0.0
network 202.1.1.0 0.0.0.255
network 100.1.1.0 0.0.0.255
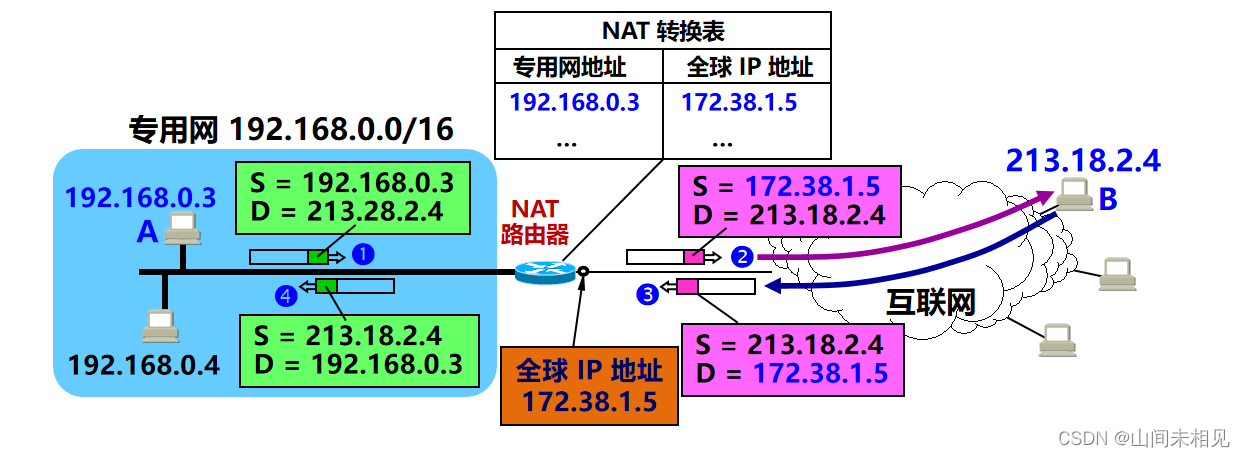
network 110.1.1.0 0.0.0.2554.配置NAT SERVER
FW1
nat server http protocol tcp global 202.1.1.100 inside 172.16.1.1
nat server 1 global 202.1.1.1 inside 10.1.1.1FW2
nat server 0 global 110.1.1.1 inside 10.1.1.15.配置NAPT
FW1
nat address-group zuo 0
mode pat
section 0 202.1.1.10 202.1.1.10
nat-policy
rule name napt
source-zone trust
destination-zone dmz
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
action source-nat address-group zuo6.配置Easy-ip
FW2
nat address-group zuo 0
mode pat
section 0 202.1.1.10 202.1.1.10
nat-policy
rule name napt
source-zone trust
destination-zone dmz
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
action source-nat address-group zuo7.配置安全策略
FW1
security-policy
rule name http
source-zone trust
source-zone untrust
destination-zone dmz
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
source-address 110.1.1.0 mask 255.255.255.0
destination-address 100.1.1.0 mask 255.255.255.0
destination-address 172.16.1.1 mask 255.255.255.255
service ftp
service http
action permit
rule name ping
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
source-address 110.1.1.1 mask 255.255.255.255
destination-address 10.1.1.1 mask 255.255.255.255
destination-address 110.1.1.1 mask 255.255.255.255
service icmp
action permitFW2
security-policy
rule name http_ftp
source-zone trust
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
destination-address 100.1.1.1 mask 255.255.255.255
destination-address 202.1.1.100 mask 255.255.255.255
service ftp
service http
action permit
rule name ping
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.1 mask 255.255.255.255
source-address 202.1.1.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 202.1.1.0 mask 255.255.255.0
destination-address 202.1.1.1 mask 255.255.255.255
service icmp
action permit三.测试结果
1.Client2访问WEB服务器


2.Client1访问FTP服务器:client1截图,会话表截图


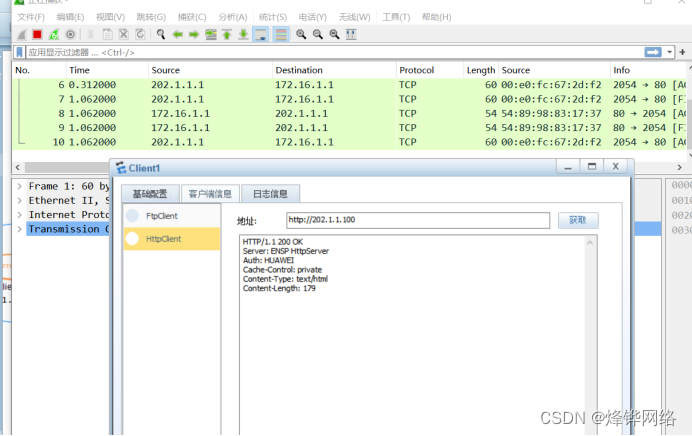
3.Client1访问WEB服务器

4.Client1访问client2,ping截图,会话表截图