一、漏洞描述
近⽇,互联⽹安全监测发现XZ Utilѕ ⼯具库恶意后⻔植⼊漏洞(CVE-2024-3094),3⽉29⽇有开发⼈员发帖称发现了涉及XZ包中的供应链攻击,进⼀步溯源发现SSH使⽤的上游liblzma库被植⼊了后⻔代码,主要存在于 5.6.0 到5.6.1版本之间;从 5.6.0 版开始,发现该恶意代码修改了liblzma代码中的函数,通过一系列复杂的混淆处理,liblzma 编译过程从源代码中存在的伪装测试文件中提取了一个预编译对象文件,然后用来修改 liblzma 代码中的特定函数。这样就产生了一个经过修改的 liblzma 库,任何与该库链接的软件都可以使用它,拦截并修改与该库交互的数据。攻击者可能利用这一漏洞在受影响的系统上绕过SSH的认证获得未授权访问权限,执行任意代码,进行后门远程未经授权访问整个系统。

XZ是⼀种⾼压缩⽐的数据压缩格式,它帮助将⼤⽂件格式压缩为更⼩、更易管理的⼤⼩,以便通过⽂件传输进⾏共享。liblzma是⼀个⽤于处理XZ压缩格式的开源软件库。xz由Tukaani项⽬开发,⼏乎存在于每个Linux发⾏版中,⽆论是社区项⽬还是商业产品发⾏版,此漏洞影响范围较⼤,目前的调查表明,这些呗恶意代码修改的包只存在于Red Hat社区生态系统中的Fedora 40和Fedora Rawhide中。因该恶意代码是在编译过程引入的,目前该恶意代码还不存在于XZ的Git发行版中,相关项目已经紧急下线,目前仅存在于完整的下载包中。

影响范围:xz == 5.6.0、xz == 5.6.1、liblzma == 5.6.0、liblzma == 5.6.1及使⽤了受影响版本XZ的操作系统或软件如openSUSE、Fedora 41、Liblzma、Debian⾮稳定的测试版(SID) 5.5.1alpha-0.1 到 5.6.1-1;更多参考影响列表
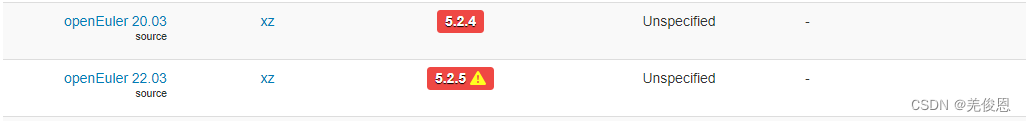
处理:请立即停止使用 Fedora 41 或 Fedora Rawhide ,以及Debian相关测试版,使用了受影响版本的XZ Util需降级到5.4.6(XZ Utils 5.4.6稳定版)及以下,可参考:OS对应默认版本,其中5.2.5涉及CVE-2020-22916漏洞;

二、排查处理
1、⽐对影响范围中的组件类型及版本,看是否涉及以上版本;如果存在⼿动安装xz项⽬的情况,可通过如下命
令查看系统本地是否安装了受影响的XZ,如果输出为 5.6.0 或 5.6.1 ,说明您的系统可能已被
植⼊后⻔: xz --version;
2、如果确实正中受影响版本,利用以下脚本查看是否漏洞被利用:
#! /bin/bash
set -eu
# find path to liblzma used by sshd
path="$(ldd $(which sshd) | grep liblzma | grep -o '/[^ ]*')"
# does it even exist?
if [ "$path" == "" ]
then
echo probably not vulnerable
exit
fi
# check for function signature
if hexdump -ve '1/1 "%.2x"' "$path" | grep -q
f30f1efa554889f54c89ce5389fb81e7000000804883ec28488954241848894c2410
then
echo probably vulnerable
else
echo probably not vulnerable
fi
另外一个来自 Baroni Fabio写的检查脚本,如下所示,执行前请先试读了解脚本执行过程:
#!/bin/bash
# CVE-2024-3094-checker.sh
# Quick and dirty PoC for checking whether a vulnerable version of xz-utils is installed
# https://nvd.nist.gov/vuln/detail/CVE-2024-3094
# Author Baroni Fabio
# This shell script is provided as-is and without warranty of any kind, express or implied.
# By executing this script, you acknowledge that you do so at your own risk.
# The author(s) of this script shall not be liable for any damages or issues that may arise from its use, including but not limited to data loss, system instability, or any other unintended consequences.
# It is recommended to review the script and understand its functionality before running it, and to ensure that appropriate backups are in place.
# Use of this script implies your acceptance of these terms.
# Detect package manager
if command -v apt-get &>/dev/null; then
PKG_MANAGER="apt-get"
elif command -v yum &>/dev/null; then
PKG_MANAGER="yum"
elif command -v zypper &>/dev/null; then
PKG_MANAGER="zypper"
else
echo "Unsupported package manager. Exiting."
exit 1
fi
if [ "$PKG_MANAGER" = "zypper" ]; then
version=$(rpm -q xz)
if [[ $version =~ (5\.6\.(0|1)) && ! $version =~ revertto ]]; then
echo "It seems you have a vulnerable version of the xz package installed on your system"
echo "OpenSuse has released a patched version that avoids this CVE, running zypper to update the xz package..."
sudo zypper refresh
sudo zypper update xz
if [ $? -eq 0 ]; then
echo "xz package updated successfully. Now it is advisable to reboot"
else
echo "xz package update failed"
fi
if lsb_release -d | grep -q "Tumbleweed"; then
echo "OpenSuse recommends openSUSE Tumbleweed users where SSH is exposed to the internet to make a fresh installation of the system and change credentials, as it’s unknown if the backdoor has been exploited."
echo "Due to the sophisticated nature of the backdoor an on-system detection of a breach is likely not possible."
echo "Also rotation of any credentials that could have been fetched from the system is highly recommended."
fi
else
echo "Your OpenSuse installation is probably safe."
fi
elif [ "$PKG_MANAGER" = "apt-get" ]; then
version=$(dpkg -l | grep "xz-utils" | awk '{print $3}')
if [[ "$version" == *"5.6.0"* || "$version" == *"5.6.1"* ]]; then
echo "Vulnerable version of xz-utils found: $version"
read -p "Do you want to attempt installing the stable uncompromised xz-utils 5.4.6 version from source? (y/n): " choice
if [[ "$choice" == "y" || "$choice" == "Y" ]]; then
echo "Downloading xz-utils 5.4.6 from source..."
wget https://github.com/tukaani-project/xz/releases/download/v5.4.6/xz-5.4.6.tar.gz
tar -zxvf xz-5.4.6.tar.gz
cd xz-5.4.6
echo "Configuring xz-utils..."
./configure
echo "Compiling xz-utils..."
make
echo "Installing xz-utils..."
sudo make install
echo "xz-utils 5.4.6 installed successfully."
else
echo "You chose not to install the package automatically. Install manually if needed. Exiting."
fi
else
echo "You appear to be safe."
fi
fi
脚本示例3:
#检查系统安装了哪个版本的XZ
for xz_p in $(type -a xz | awk '{print $NF}' | uniq);
do
strings "$xz_p" | grep "xz (XZ utils)" || echo "No match found for $xz_p";
done
3、处置建议
⽬前 GitHub 已经关停了整个xz项⽬。xz项⽬⽬前官⽅尚⽆最新版本,需对软件版本进⾏降级⾄5.4.6,但有人在社区爆料,攻击者可能已补发5.4.6的恶意版本,故可选5.4更低的版本,完成后进行漏洞扫描检测;Fedora Linux 40 ⽤户需 xz 回退到 5.4.x 版本可参考Fedora Linux 40 Beta、openSUSE:Factory / xz、perl-Compress-Raw-Lzma
软件下载:https://jaist.dl.sourceforge.net/project/lzmautils/xz-5.4.6.tar.gz
SHA1:a8262cf6e4ecf878955e236cea09ad5dc80c3fb8
MD5:08a6d92f44bf3a28fd5c61695101dd22
yum list installed|grep xz
yum info xz*|grep 5.*
yumdownloader xz-5.2.4
rpm -ivh xz-utils-5.2.4-1.el7.x86_64.rpm
rpm -q xz
#或,对于具有依赖关系的包,YUM降级困难,YUM降级不会自动解决依赖关系,因此必须手动完成
yum downgrade xz-5.2.4-2.el7_9.x86_64
yum downgrade xz xz-libs xz-devel xz-compat-libs xz-lzma-compat